2024-2-19 01:16:25 Author: stalkphish.com(查看原文) 阅读量:49 收藏
This phishing kit impersonates Caisse D’Epargne, a French bank, of BPCE Group. This kit was downloaded at the beginning of December 2023, by our phishing detection and investigation tool StalkPhish.io.
About the phishing kit
The configuration files contained in the downloaded ZIP archive were edited between November 30 and December 1, 2023:

This phishing kit – we called it “CaisseEpargne_don“, name of the presumed author – contains a great deal of dead code due to the probable reuse of a previous kit developed to impersonate Societe Generale (another French bank), traces of which can be found in a multitude of files, and without these files being observed to be called up during dynamic analysis.
Most of the pages appear to be an aspiration of the site dating back to March 2021 based on the dates of the .download files generated by the site copy tool:

Exfiltration vectors
The aim of this phishing kit is, as is often the case, to steal access to the victim’s bank account management portal, as well as credit card information. Although it was observed in a static analysis that the original kit was developed to send the stolen data to another server via HTTP POST, but it is no more used in this phishing kit copycat:

This modified version uses only a Telegram bot to exfiltrate the stolen information, as well as writing it into TXT files on the server, as we can observer in the ccf.php file:

Targeted data
The information targeted by the scammer is, initially, as follows:
- login to the victim’s bank portal
- account password


Once this initial information has been stolen, it is then exfiltrated on the Telegram channel configured in the kit, via the Telegram bot belonging to the scammer:

Theft of 2FA code
These days, login/password information alone is no longer sufficient to access a banking portal (or you’ll have to change bank), and it is now necessary to validate this access using a second authentication factor (2FA), often the customer’s cell phone or a text message.

On this page, we can point out several things:
- a 3-minute timer, designed to generate stress and influence the victim to take urgent action
- a request for the SMS code to be received by the victim to enable the scammer to connect to the bank
- the reference to a potential voice server call on the victim’s phone to enter the connection validation code.
Once entered, the second factor is also sent to the scammer’s Telegram channel, giving them all the information they need to connect to the bank account, pretending to be the victim being scammed.

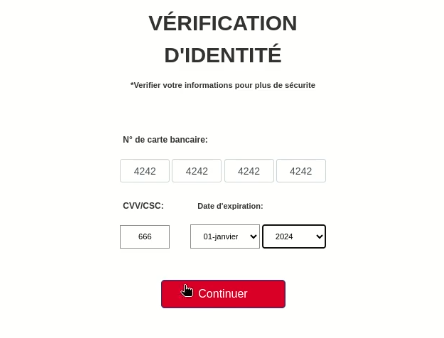
In a second step, under the guise of “identity verification”, the victim is asked to enter their bank card details:
- credit card number
- CVV/CSC code
- card expiry date

As well as a new verification code, enabling the scammer to proceed with a valid remote payment. Once again, this information is sent over the Telegram channel to the scammer.

Once these operations have been completed, the victim is redirected to the bank’s official and legitimate website.
View this kit in action
See how this kit works, in action, on our Youtube page as part of our collection entitled “Phishing Stories”
Some advice
If you receive a message (e-mail, SMS, WhatsApp communication, etc.) claiming a fraudulent operation, payment of a fine or other, and asking you to click on a link provided: don’t click (unless you know what you’re doing), there’s a good chance you’ll be redirected to a phishing page. Instead, go to the official site by opening your browser and searching for the portal in question on your favorite search engine.
Watch where you put your digital feet: does the URL (the site address) resemble that of your bank? Does it really? If in doubt, follow the first recommendation.
Don’t enter any personal information when in doubt, and certainly not on a site you don’t know, or check the means of communication usually used by the portal in question: don’t hesitate to read the alerts on official sites, which very often inform you of the methods of communication usually used.
If you have any other recommendations, please let us know in the comments.
IOC
SHA256 of the zip file: b478ef5489bc53f77a4431325bf35f22e14253c12278b7339f42dccc73899ed1
Name of the zip file: Caisseepagne.zip
PhishingKit-Yara-Rule: PK_CaisseEpargne_don.yar
Telegram Bot token: 5800018105:AAErrOzBn4__BdaBV0jeHeBu4rip6Jtxguc
Telegram channel ID: -869679353
email header: “From:Trnswise [email protected]“
About StalkPhish
We propose free, open source and downloadable tools, mainly focused on anti-phishing and brand identity theft (StalkPhish OSS, PhishingKit-Yara-Rules, PhishingKitHunter), check our dedicated page.
We provide enriched data related to these massive phishing campaigns, through our StalkPhish.io REST API, dedicated to digital detection and investigation of actors and their infrastructures.
Also, we regularly share knowledge and analysis of phishing kits on our StalkPhish.com (this) blog.
You can contact us for more information via our contact page.
About the “StalkPhish’s Phishing Stories” project
The Stalkphish Phishing Stories project aims to show how phishing sites work and what sort of clever tricks are used to lure victims. The aim is to inform the general public of the risks involved and the tricks used to detect these scam pages.
Disclaimer: The Stalkphish Phishing Stories project, offered by StalkPhish.com, is for information purposes only. StalkPhish does not practice or use phishing and phishing kits for illegal activities.
如有侵权请联系:admin#unsafe.sh