2024-2-20 09:46:15 Author: therecord.media(查看原文) 阅读量:9 收藏
LockBit — the most prolific ransomware group in the world — had its website seized Monday as part of an international law enforcement operation that involved the U.K.’s National Crime Agency, the FBI, Europol and several international police agencies.
“This site is now under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos’,” a seizure notice on the group’s website said. "We can confirm that Lockbit's services have been disrupted as a result of International Law Enforcement action — this is an ongoing and developing operation.”
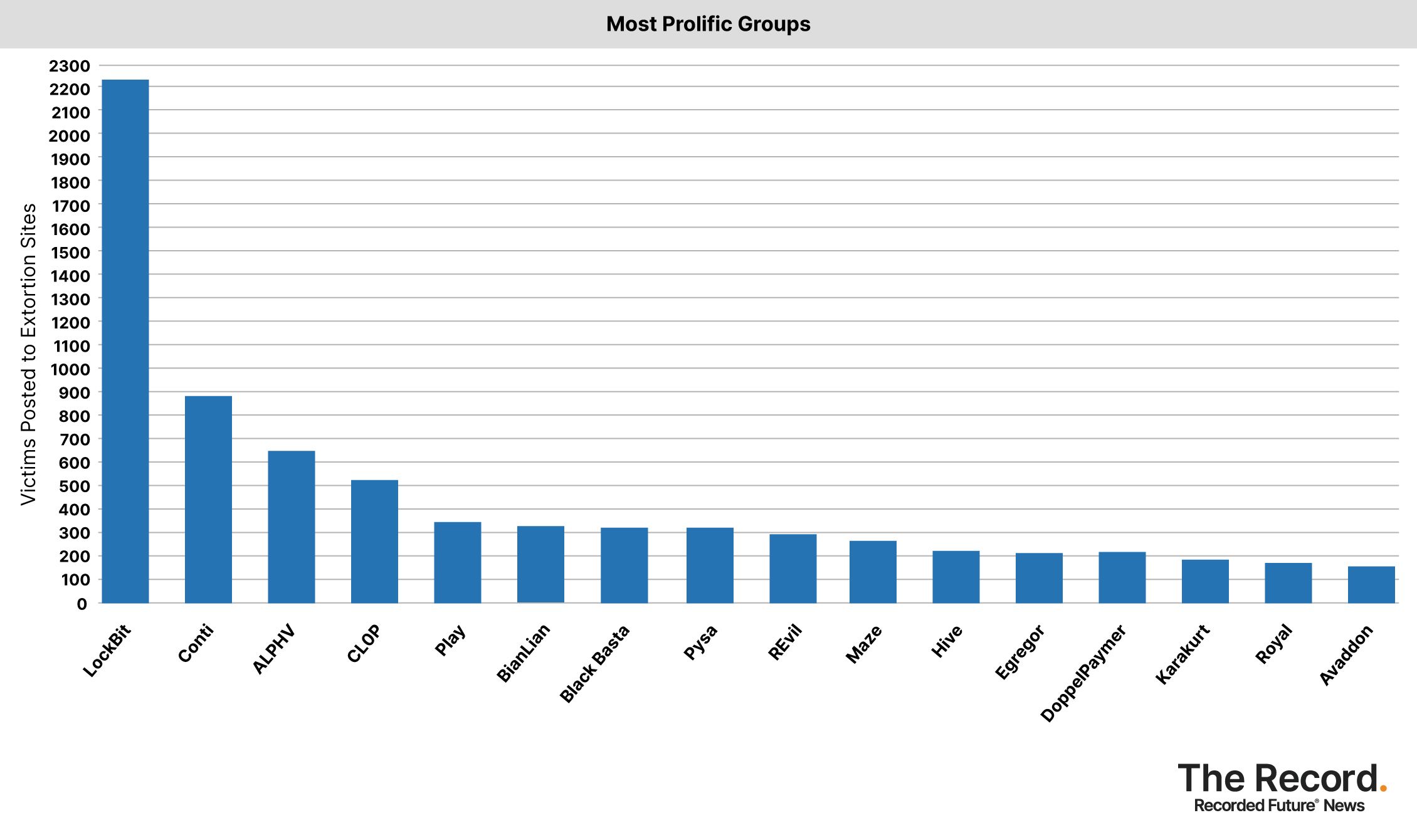
The group has far outpaced other ransomware gangs since it emerged in late 2019, with researchers at Recorded Future attributing nearly 2,300 attacks to the group. Conti — the second most active group — has only been publicly linked to 883 attacks.
![]()
But LockBit has also gained a reputation for the damage it has caused and the organizations it has targeted. Although the group previously claimed to have rules prohibiting attacks on hospitals, it hit Canada’s largest children’s hospital during the 2022 Christmas season, as well as multiple healthcare facilities in the U.S. and abroad. Last month, the group said it was behind a November attack on a hospital system that forced multiple facilities in Pennsylvania and New Jersey to cancel appointments.
“In a highly competitive and cutthroat marketplace, LockBit rose to become the most prolific and dominant ransomware operator,” said Don Smith, vice president of threat research at Secureworks CTU. “It approached ransomware as a global business opportunity and aligned its operations, accordingly, scaling through affiliates at a rate that simply dwarfed other operations.”
The takedown is just the latest in a series of law enforcement actions targeting ransomware gangs — late last year, the FBI and other agencies took down sites and infrastructure belonging to Qakbot, Rangar Locker and other groups.
“This has been a year of action for the Justice Department in our efforts to pivot to a strategy of disruption,” Deputy Attorney General Lisa Monaco said Friday at the Munich Cyber Security Conference. “You’re going to continue to see that same tempo of prevention-focused, disruption-focused, victim-centered action, and I would say ‘stay tuned.’”
Monaco added that the DOJ would also target cryptocurrency platforms and other operations that help ransomware groups monetize their crimes.
Allan Liska, who helps track and analyze data on ransomware groups for Recorded Future, said the takedown will have a disruptive effect on the ransomware ecosystem, even if it is only temporary.
“More importantly, this is a hugely symbolic win. The group behind LockBit has spent the last couple of years laughing at and mocking law enforcement, at one point even paying people to get LockBit tattoos. They’ve built up a cult following in certain circles,” he said. “But this operation shows that no matter how much money you claim to have or how many fans on Twitter you have, law enforcement will catch up to you.”
“Undoubtedly, LockBit leaders will be discussing their plans to change to a new ransomware by the time this story runs, but whatever their new ransomware is, it will be far diminished compared to LockBit and there will be an extreme lack of trust among affiliates for the new offering,” he added.
Law enforcement agencies involved in the LockBit takedown are expected to make additional announcements about the operation on Tuesday.
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Adam Janofsky
Adam Janofsky is the founding editor-in-chief of The Record from Recorded Future News. He previously was the cybersecurity and privacy reporter for Protocol, and prior to that covered cybersecurity, AI, and other emerging technology for The Wall Street Journal.
如有侵权请联系:admin#unsafe.sh
