2024-2-21 15:55:53 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
One of the biggest security weaknesses organizations face is their own employees. This isn’t pleasant, but it is a reality we must accept. When they make mistakes, they open the door to attackers. This is even more true when dealing with the user accounts of previous employees.
It’s a common misconception that the primary risk associated with former employees’ accounts lies in the potential for disgruntled ex-workers to use their credentials maliciously. Even though insider threats pose a significant risk, there is another danger that often goes unnoticed: external attackers compromising unmonitored accounts.
In many cases, these accounts become forgotten relics of past employment, left unchecked and unmonitored as employees move on to new opportunities. It is precisely this neglect that makes them such attractive targets for cybercriminals.
Common Challenges and Risks of Ex-Employee Accounts
Attackers are aware that these inactive accounts or stale user accounts, commonly known as ‘leavers’, are often overlooked by organizational security measures. Most IT teams will remove these account privileges and access to critical resources, but this is not always the case.
Even though we would never want to imagine that our employees are capable of malicious actions, failure to revoke a leaver’s access can leave the door open for sensitive company information to be misused and leaked. It is also important to note that lingering accounts pose a risk in terms of password usage. If an active leaver’s account uses a duplicate or insecure password, third parties may have easy access to your organization.
Since the former employee may still possess high privilege access and permissions due to their tenure, attackers have an attractive target to help them gain a foothold in an environment. Whether it is accessing sensitive data, infiltrating critical systems, or initiating lateral movement within the network, compromising these overlooked accounts has the potential to cause significant damage.
The most common example would be the case of a super admin who is let go. Their user account has access to most critical resources, yet IT does not disconnect the account or remove its privileged access.
Real-Life Example: Threat Actors Leveraged Ex-Employee Accounts to Breach State Government Systems
According to the Cybersecurity and Infrastructure Security Agency (CISA), a threat actor gained access to a US government organization’s network using a former employee’s administrative login credentials. By using compromised credentials, the attackers were able to access an internal VPN and the on-prem environment and execute LDAP queries on a domain controller.
The organization, which CISA has not named, failed to remove the former employee’s account, which allowed the threat actor to analyze the environment and its resources. The credentials allowed access to two virtualized servers, SharePoint and the employee’s workstation. A second employee’s credentials were extracted from the SharePoint server and used to authenticate to the on-prem Active Directory and Entra ID (Azure AD), thereby gaining administrative access.
Both virtualized servers have been taken offline and the user account has been disabled. In addition to changing the credentials for the second compromised account, the victim organization also removed its administrative privileges. Additionally, CISA noted that neither of the administrative accounts had MFA enabled.
As this example illustrates, even following best practices throughout your IT security strategy is not sufficient when dealing with attackers. Instead of assuming you have done enough to secure the accounts of former employees, it is best to add more concrete identity security controls that deny access as a means of ensuring the safety of these accounts.
How Silverfort Secures Former Employee Accounts
Silverfort enables Identity teams to easily discover former employee accounts in their environments and either delete them or remove their permissions. Silverfort classifies accounts that have not been used for a year or more as “stale users”. With Silverfort you can gain complete and continuous visibility into stale users and apply appropriate security measures, such as enforcing block access policies to these user accounts.
Let’s see exactly how this is done in Silverfort’s console:
Visibility Into Stale Users
Silverfort automatically discovers all accounts in your environment, including stale user accounts, and provides real-time visibility into all user activity. This enables you to detect and respond to potential security threats — including blocking the access of any accounts that display anomalous behavior.
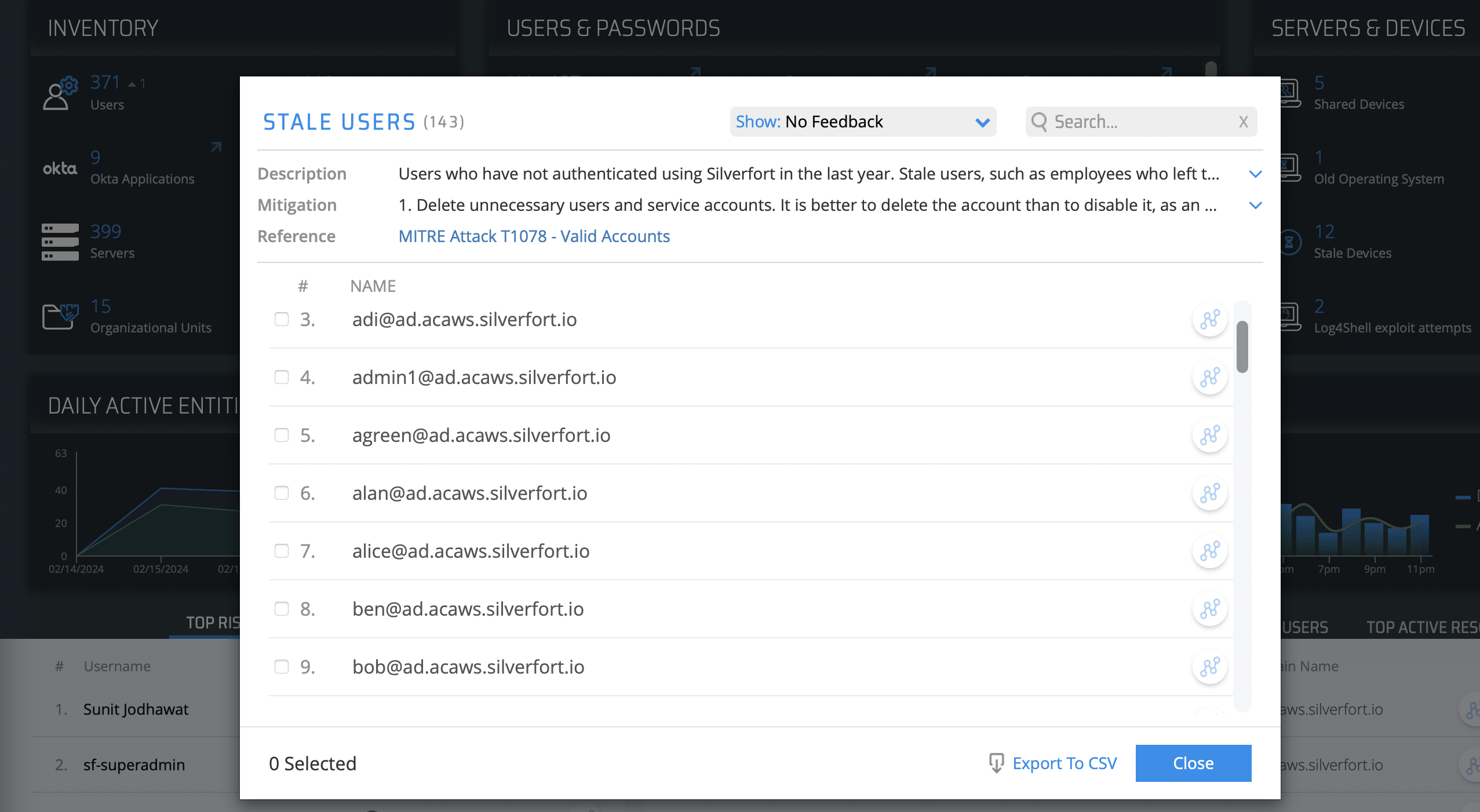
In Silverfort’s Insights screen, you will see an in-depth identity inventory that displays the types of users and resources in your environment as well as weaknesses in your security. Under Users & Passwords, you can find the entire list of stale users in your environment. Silverfort detects and categorizes these accounts by common attributes of stale user accounts.
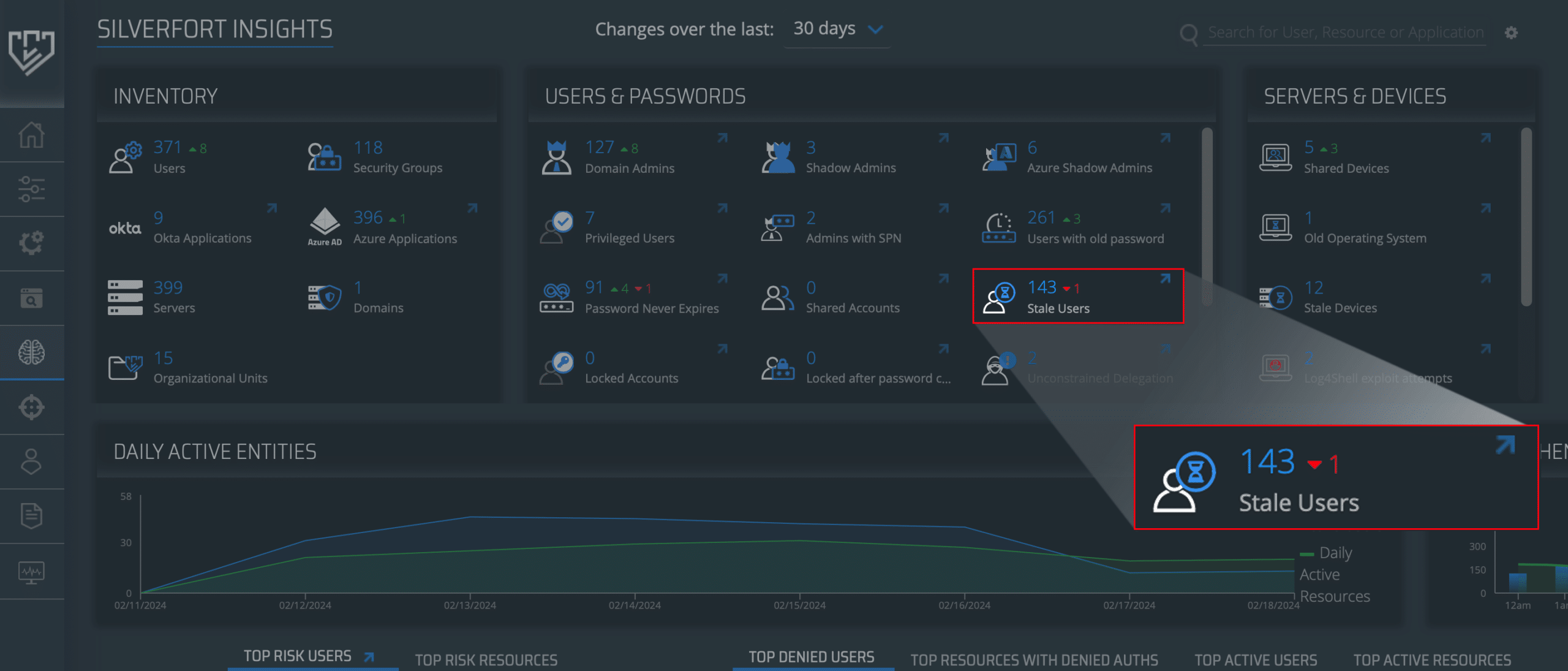


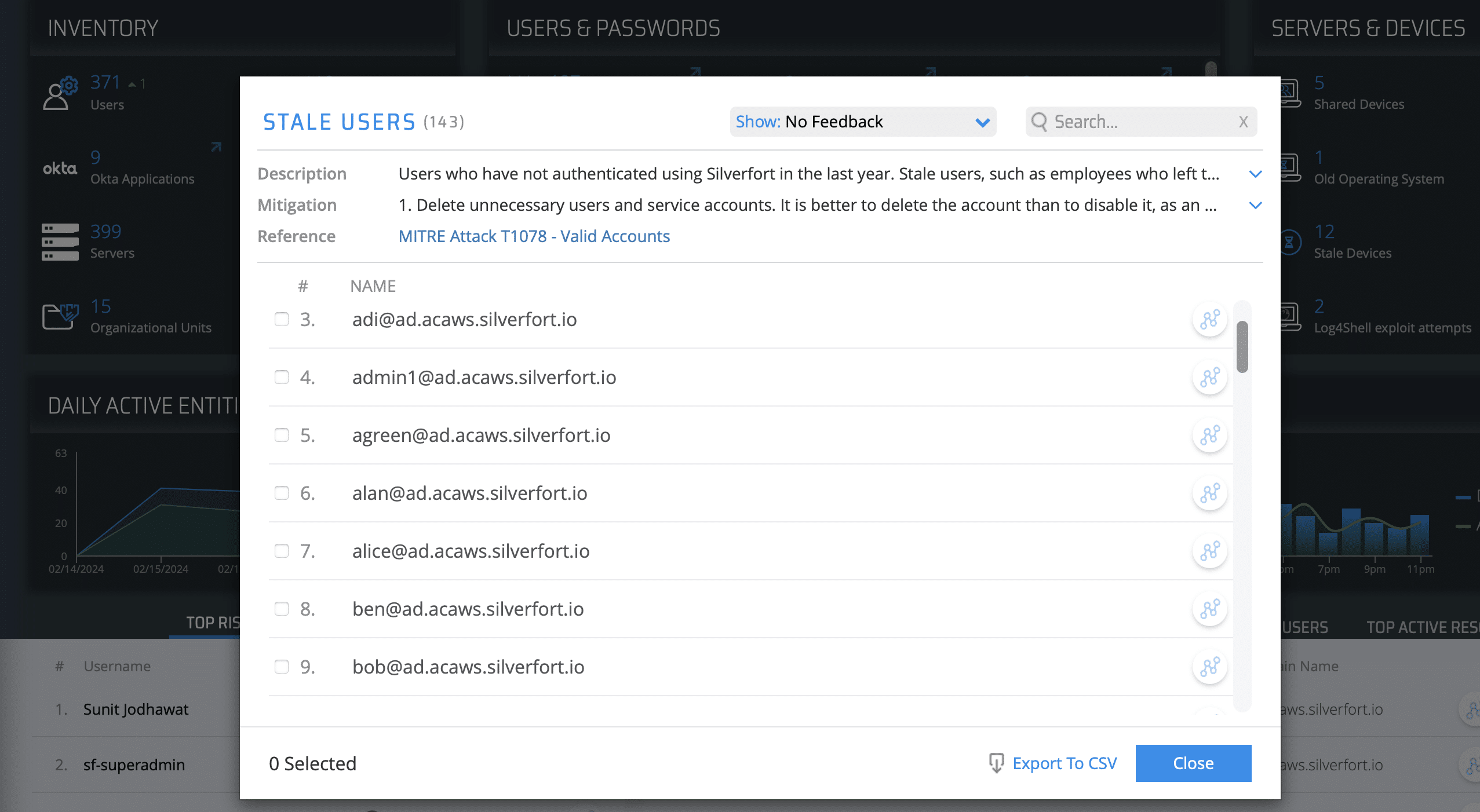
Clicking on the Stale Users space opens a window that shows you full details on these accounts. Now that you have the names of these stale users, you can locate them in its IdP and either remove their permissions, delete them altogether, or apply a deny access policy to the user account.


The Power of Deny
To take a more proactive approach to preventing ex-employee user accounts from creating any more security risks, it’s recommended that you create a ‘Leavers’ deny access policy. This will ensure that if a malicious actor comprises a stale account to gain access to anything in your environment, they will be automatically denied access.
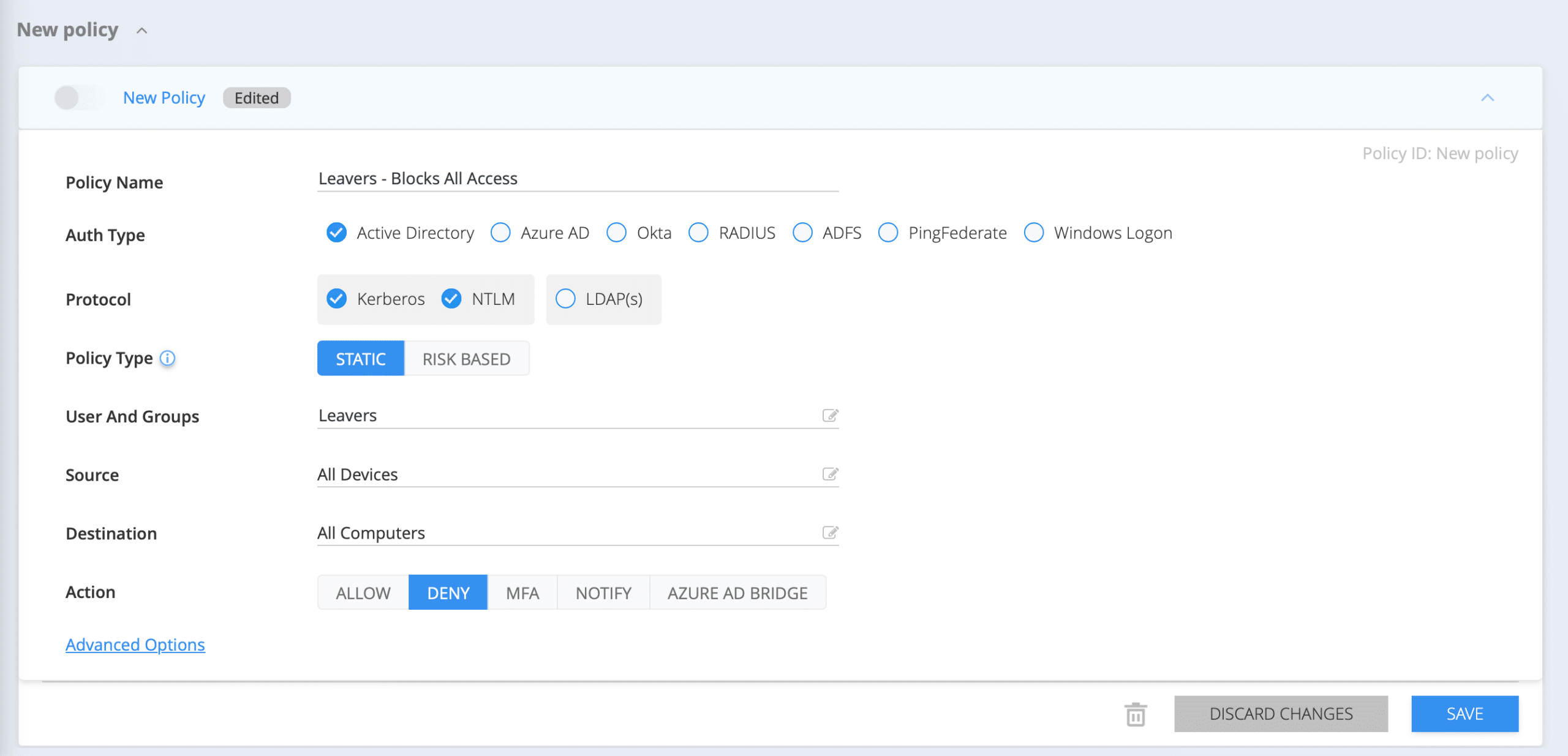


In Silverfort’s Policies screen, create a new policy. Check your IdP as the Auth Type, then check either Kerberos/NTLM or LDAP, depending on your needs. Choose Static Based for the policy type and for User and Group, it should be assigned to the Leavers group or a similar name you have for employees who are leaving or have left. Next, under Action, choose Deny.
Once enabled, this policy will automatically deny access to any account to whom this policy is assigned. If this account was compromised, this policy would deprive an adversary of the ability to use it for malicious access.
Real-Time Visibility and Protection are Critical to Mitigating the Risks of Former Employee Accounts
Many types of security threats can endanger your organization in today’s hybrid environment, so comprehensive security requires complete visibility, monitoring, and protection. The visibility of stale users and the blocking of any access requests are important for ensuring attackers will not use these accounts to gain access to other parts of the environment.
By applying continuous monitoring and active policy enforcement to every form of employee accounts, Silverfort can both automate the discovery of stale users as well as deliver real-time protection against their abuse.
Looking to solve identity protection challenges in your environment? Reach out to one of our experts here.
The post Mitigating the Identity Risks of Ex-Employees’ Accounts appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Silverfort Blog - Cyber Security News authored by Zev Brodsky. Read the original post at: https://www.silverfort.com/blog/identity-risks-of-stale-user-accounts/
如有侵权请联系:admin#unsafe.sh