2024-2-25 22:31:42 Author: www.kelacyber.com(查看原文) 阅读量:26 收藏
It has been two years since Russian forces invaded Ukraine. The war is not only being fought on the ground, but also in cyberspace. Russian state-sponsored APT groups have been observed targeting Ukrainian entities, including government organizations and telecommunication companies. Moreover, the Ukrainian government has also been observed claiming to have conducted attacks against Russian organizations.
The Russia Ukraine war gained widespread attention and resulted in the creation of a new wave of hacktivism, with hacktivist groups conducting attacks in support of either side of the conflict. Ukraine raised a volunteer “IT Army”, which, together with hacktivist organizations from across the world, began targeting Russian companies and organizations. On the other side, numerous pro-Russian hacktivist groups emerged conducting attacks on Ukraine and its allies. Due to their beliefs and actions closely aligning with the Russian government, it is believed that some of these groups are state-affiliated. However, various groups have denied their affiliation with the Russian government.
Attacks by pro-Russian groups gained significant media attention. These groups, whilst not the most technically skilled, have claimed attacks on high profile organizations from around the world, including governments from various countries.
In this blog, KELA examines the current state of Russian hacktivist activity, specifically looking at whether this activity has continued or whether these groups have lost momentum.
State of affairs: decreased but steady activity
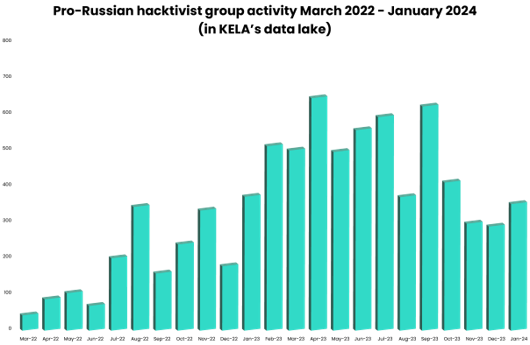
Pro-Russian groups continue to conduct attacks against Ukraine and its allies, including denial of service attacks, website defacements and data leak attacks. Whilst pro-Russian groups continue to claim attacks on their Telegram channels, KELA observed that the amount of posts related to claimed DDoS attacks at the end of 2023 and into 2024 had decreased compared to activity earlier in the year.
KELA chose to focus on claimed DDoS activity alone rather than total number of posts in their channels because total number of posts is not indicative of the activity (groups have a lot of messages in their channels not related to the actual attacks). Of note, the number of posts on the graphs below is not equal to the number of the victims, since one post can claim multiple victims, for example, in the same country.

Pro-Russian hacktivist group activity related to claimed DDoS attacks in March 2022 – January 2024 (in KELA’s data lake)
More specifically, KELA examined the activity of five most active groups that emerged shortly following the start of the war and were active for most of the war: Killnet, NoName057(16), Anonymous Russia, Phoenix, and People’s Cyber Army (possibly linked to APT28). These groups’ activity in the second half of 2023 and early part of 2024 is significantly lower compared to their activity in the first half of 2023.

DDoS activity of 5 most active pro-Russian groups (Killnet, NoName057(16), Anonymous Russia, Phoenix, and People’s Cyber Army) in March 2022— January 2024 (in KELA’s data lake)
NoName057(16) has been conducting attacks since March 2022 and is the most active pro-Russian hacktivist group, however, they do appear to have claimed less posts related to DDoS attacks since July 2023, consistent with the overall trend. Since the start of 2024, NoName057(16) has been observed claiming to have conducted distributed denial of service attacks against organizations from multiple countries, including: Ukraine, Spain, France, Italy, Finland, Germany, Lithuania, Netherlands, Greece, Poland, Romania, Estonia, Latvia, Switzerland, and the UK.

Translated post on NoName057(16)’s Telegram channel on attacks they conducted against Finland (auto-translated through KELA’s platform)
KELA is aware of numerous groups that appear to have stopped conducting attacks. For instance, Bloodnet is a group that emerged in January 2023 and has been claiming new DDoS attacks each few days, both independently and in collaboration with other prominent groups. The group had more than 1000 followers in their Telegram channel. However, Bloodnet has not claimed an attack since October 2023, though the channel is still accessible. Another group that appears to have become inactive is From Russia with Love who has not been observed claiming an attack since December 2022, though the channel had some occasional posts not related to attacks. The channel is still active and has more than 2000 followers.
Nevertheless, despite the apparent decrease in activity and some groups disappearing from the scene, pro-Russian hacktivist activity has continued.
Restructuring of groups
Since their formation, certain pro-Russian hacktivist groups have undergone certain forms of restructuring. For instance, groups have changed their leadership, and some appear to have attempted to fund themselves through financially motivated cyber activities.
Killnet has undergone various changes since the start of the war. Most recently, in December 2023, it was announced that Killmilk, the founder and leader of the group, was retiring and that the new owner of Killnet would be Deanon Club, a hacker community which is fighting against sites that sell drugs. According to Deanon Club’s founder, Killnet will distance itself from politics and will focus on commercial orders. Since Deanon Club purchased the Killnet Telegram channel, KELA has only identified one claim of an attack on Ukraine – the attack on Kyivstar (although, it should be noted that it is unlikely Killnet is behind this attack).
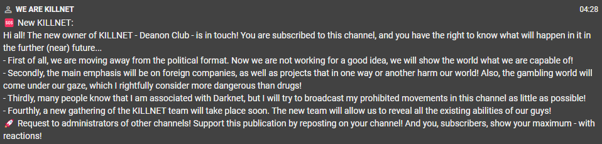
Figure 4: Translation of post in which Deanon Club announces on Killnet Telegram channel that Killnet will move away from “the political format” and that the focus would be on foreign companies or projects that “in one way or another harm our world” (auto-translated through KELA’s platform)
Anonymous Russia has been undergoing leadership change several times, and some of them influenced the group’s funding methods. For example, in April 2023, ‘Radis’ was made leader of the group after the previous leader ‘Raty’ was arrested. After Radis’ takeover of Anonymous Russia, the group moved away from asking for donations from their supporters and instead, launched several paid-for services/products, most notably Tesla-Botnet, a botnet developed by Radis, which has been advertised on Anonymous Russia’s Telegram channel. Now Anonymous Russia is again “on reorganization.”
New groups continue to emerge
Even though the war has been ongoing for a significant period of time, this has not stopped new pro-Russian hacktivist groups from emerging to join the cause. For instance, following the sale of Killnet, a new Telegram channel called “Killnet2.0” emerged in January 2024. The group describes themselves as an “international decentralized group of hacktivists”. Several groups have joined Killnet 2.0, including Anonymous Russia and some groups that have supported Palestine following the outbreak of the war with Israel.
Another example is a new pro-Russian group called “JUST EVIL” that emerged at the end of January 2024. The group, which is believed to have been created by the former leader of Killnet, Killmilk, has already claimed attacks on organizations from the US, Lithuania, and Poland. JUST EVIL appears to be at least partially financially motivated – they were observed demanding a ransom from one of their victims as well as selling data and access to corporate systems on their Telegram channel.
The constant emergence of the new groups appears to affect the threat landscape and contribute to the steady amount of the malicious activity.
Cross-conflict activity: engagement in other geo-political conflicts
Pro-Russian hacktivist groups do not necessarily exclusively conduct attacks in support of Russia. For example, Anonymous Sudan emerged in January 2023, with the purpose of proving “to all countries that Sudan has people who will protect it on the Internet” and to “attack anyone who opposes Islam.” The group, which is not affiliated to the wider Anonymous collective, is believed by some researchers to be linked to Russia. Anonymous Sudan became a member of Killnet in February 2023 and conducted attacks in support of Russia. Anonymous Sudan continues to claim attacks against Ukraine and its supporters, as well as conducting attacks in response to other, non-related events for example in relation to the Israel Hamas war.
Following the start of the Israel Hamas war, some pro-Russian groups were observed participating in attacks in support of Palestine, including attacking Israeli organizations as well as countries seen to be supporting Israel. Groups that have been observed claiming attacks include UserSec, Server Killers, Bluenet, and Anonymous Sudan.
Furthermore, Ancient Dragon is a new hacktivist group that was identified in February 2024. They state that the “group is ready to support the interests of Russia, and we are also ready to support our beloved Muslim brothers.” The group has stated that they will target Ukraine, Israel and the US.
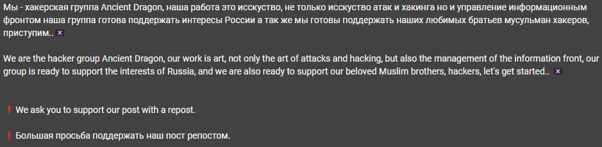
Figure 5: Announcement of Ancient Dragon hacker group (screenshot taken from KELA’s platform)
Summary
Whilst pro-Russian hacktivist activity has decreased compared to levels observed in 2023, these groups do still continue to claim attacks on Ukraine and its allies. Not only does KELA see familiar names continuing to conduct attacks, but KELA continues to identify the emergence of new groups. KELA assesses that DDoS and defacement, with occasional data-theft attacks, are expected to persist as the main tactics of hacktivists in 2024. Organizations in Ukraine and in countries that support Ukraine, for instance NATO countries, will continue to be targets of pro-Russian groups.
如有侵权请联系:admin#unsafe.sh