Always be wary of opening unsolicited attachments – they might harbour malware.
That’s a message that is being strongly underlined once again, following the discovery of a cybercrime campaign that is using the cover of travel service providers.
Security researchers at Forcepoint say that they have uncovered evidence that malicious hackers are sending out poisoned PDF files, designed to infect recipients’ PCs.
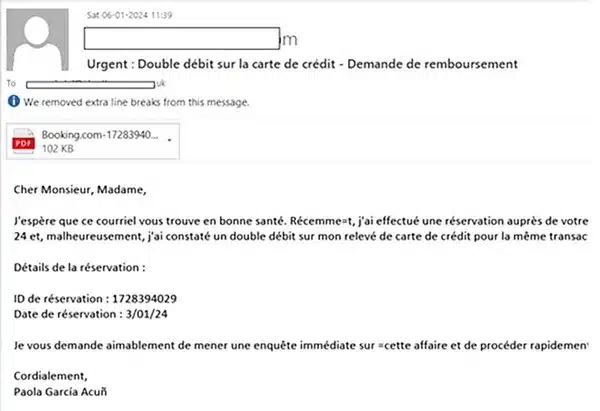
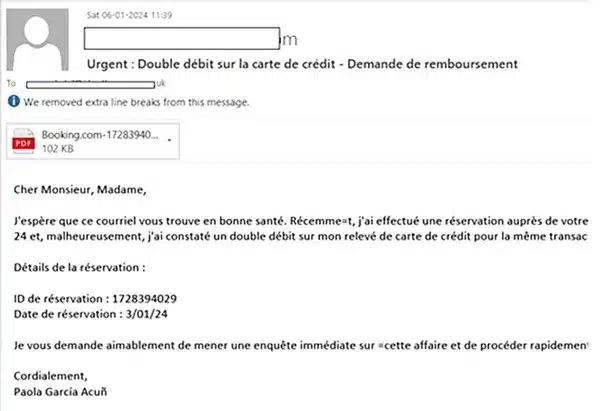
The emails claim that the sender’s credit card has been mistaken charged twice for a hotel reservation – and asked for the matter to be investigated.
However, if the .PDF attachment (which, in the above example, has a filename referencing travel website Booking.com) is opened, malware is downloaded that ultimately deploys the Agent Tesla remote access trojan.
As researchers Mayur Sewani and Prashant Kumar explain, the remote access trojan (RAT) allows remote hackers to log keypresses, steal passwords and other data, and run commands on the infected PC.
Although the example given by Forcepoint uses the disguise of a booking reservation related to Booking.com, it could just as easily pretend to be in connection with another travel service.
One danger is that a hotel receiving such an email might be tricked into opening the boobytrapped file, and give remote hackers an opportunity to break into the hotel’s reservation system – potentially opening opportunities for yet more fraud.
In October last year I described how fraudsters had hacked into hotels Booking.com accounts in order to target guests.
And I should know – I was one of those guests who was targeted.
For more discussion of how hotels were having their Booking.com accounts hacked, be sure to listen to this episode of the “Smashing Security’ podcast.