-
 By
Yehuda Gelb
By
Yehuda Gelb
- March 4, 2024

Key Points
- Widespread Malware Distribution on GitHub: Recent discoveries, including Apiiro's report on over 100,000 infected GitHub repositories, highlight a growing trend of using GitHub for malicious purposes.
- Diverse Attack Methods: GitHub-based cyber threats employ various sophisticated strategies, including attacks on legitimate repos, social engineering, and exploiting GitHub actions. This variety in attack vectors signifies the adaptability and ingenuity of cyber attackers in exploiting GitHub's functionalities.
- Critical Role of Continuous Monitoring in Cybersecurity: The evolving nature of threats on platforms like GitHub underscores the imperative for robust, continuous monitoring solutions.
- Checkmarx's Proactive Defense Against Supply Chain Cyber Threats: Checkmarx's Supply Chain Security solution vigilantly monitors malicious activities, swiftly identifying and alerting on suspicious actions in the open source ecosystem to effectively counteract these cyber threats.
Malicious Repo Confusion Campaign
In light of a recent blog released by Apiiro, the cybersecurity landscape is yet again reminded of the innovative ways attackers exploit platforms like GitHub to host and spread malware. Apiiro's findings reveal a large-scale malicious repo confusion campaign impacting over 100,000 GitHub repositories, shedding light on the evolving tactics of cybercriminals. Interestingly, part of the attackers' strategy involved creating fake forks to make their repositories seem legitimate, a tactic we have discussed extensively in relation to repository spoofing.
The attacker took the following steps: they first cloned existing repos and infected them with malware loaders. Next, they uploaded them back to GitHub under identical names, automatically forking each one thousands of times. Finally, they covertly promoted them across the web via forums, discord, etc.
This is not an isolated case. The use of GitHub for malicious purposes has been a recurring theme, as evidenced by several incidents in the past.
Attacks on Legitimate Repos
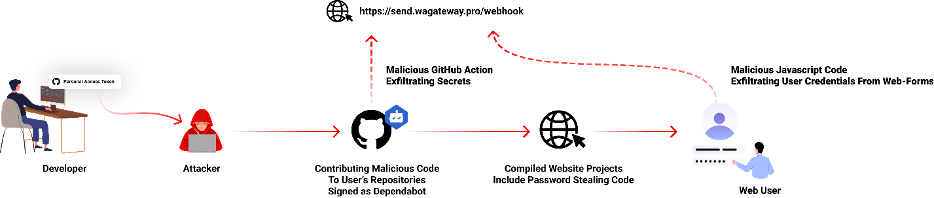
A notable method of exploiting GitHub involves attacking legitimate repos. A prime example is an incident in mid-2023where attackers, leveraging stolen GitHub personal access tokens, impersonated Dependabot, a well-known dependency update helper tool. These tokens bypassed two-factor authentication, allowing malicious code to be committed under the guise of Dependabot. This code aimed to extract sensitive information and inject malware into JavaScript files.
Nation-State Social Engineering Using GitHub
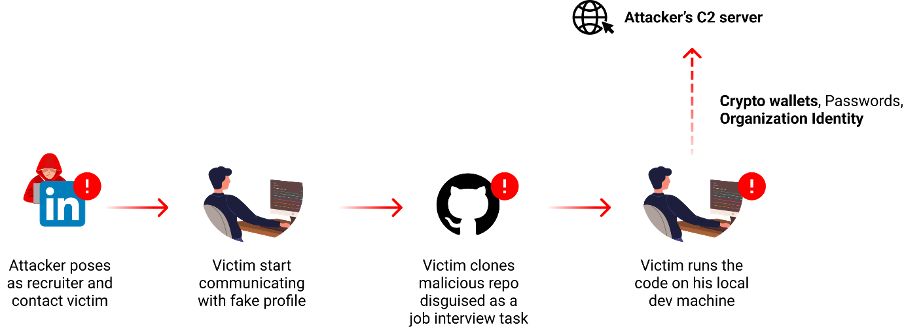
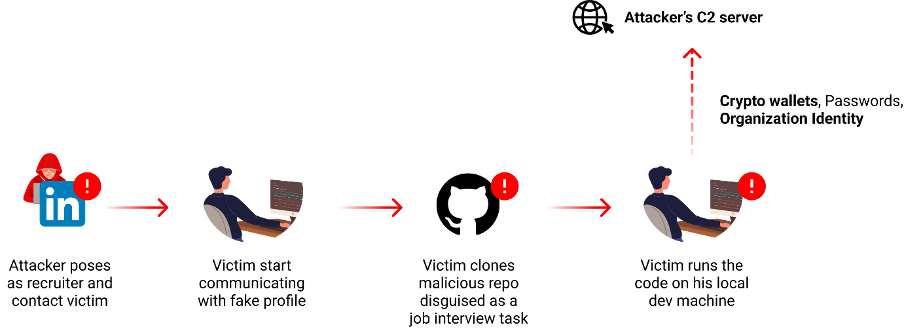
Another tactic is the use of social engineering. In contrast to the scrutiny typically given to public open-source repositories, GitHub's private repositories provide a more concealed avenue for attackers. A recent discoveryrevealed how North Korean state actors were using these malicious repos to then integrate into software through social engineering, targeting specific organizations or individuals.
Attacking GitHub Actions for Public Repos
In mid-2023, GitHub user account, pastramahodu, forked nearly 2,000 repositories, with 319,191 total stars combined, as part of a widespread bug bounty hunt attempt for finding misconfigurations in popular project’s CI pipelines. The procedure was most likely automated and created Pull Requests which in some projects triggered the project’s CI pipeline and executed the custom commands. This highlighted the increasing focus on pipeline security as an entry point for supply chain attacks.
Conclusion
The recurring theme across these examples is clear: GitHub, a platform integral to the development community, has become a focal point for cybercriminals looking to exploit the software supply chain. The sophistication and variety of these attacks demonstrate the evolving and persistent nature of these threats. As part of the Checkmarx Supply Chain Security solution, we continuously monitor and detect suspicious activities in the open-source software ecosystem, such as these. We track and flag “signals” that may indicate foul play and promptly alert our customers to help protect them. In the face of these sophisticated attacks, it is more important than ever for developers and organizations to stay alert, regularly review code sources, even from trusted platforms like GitHub, and implement robust security measures.
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
![]()
Yehuda Gelb
Yehuda is a security researcher at Checkmarx and has a passion for making cyberspace a safer place to live and work. Prior to Checkmarx, he served as an information system security officer for the Lockheed Martin F-35 program, and assisted in developing the Cyber Defense strategy for Israel’s Air Force, the IAF. Yehuda currently holds numerous cyber certifications including CISSP and CCSP. During his free time he also employs his expertise to help people and non-profit organizations share their stories with the world through audio and visuals. Yehuda’s hobbies include creating music, producing films, traveling, and strategy board games.
Never miss an update. Subscribe today!
By submitting my information to Checkmarx, I hereby consent to the terms and conditions found in the Checkmarx Privacy Policy and to
the
processing of my personal data as described therein. By clicking submit below, you consent to allow Checkmarx
to store and process the personal
information submitted above to provide you the content requested.
More Resources to Consider
如有侵权请联系:admin#unsafe.sh