2024-3-7 17:44:6 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
Introduction
In the ever-changing world of Kubernetes security, it’s crucial to stay ahead of threats while maintaining operational efficiency. That’s why we’re excited to introduce our latest feature: Auto-Generated Kubernetes Network Policy, based on application runtime behavior, powered by eBPF (extended Berkeley Packet Filter) technology. With this addition, organizations can easily apply native Kubernetes network rules without worrying about disrupting their production systems.
What are the challenges when adopting a Network Policy?
- Visibility: Understanding which workloads have network policy in place.
- Application behavior: The network traffic patterns within a Kubernetes cluster can be convoluted, making it difficult to define effective policies without comprehensive visibility.
- Complexity: Implementing network policies can be complex due to the diverse nature of containerized environments and the need to balance security with accessibility.
- Policy Conflicts: Configuring policies that align with the requirements of more than one application, while maintaining overall security can lead to conflicts and inconsistencies.
- Policy Management: Managing network policies across multiple clusters or environments requires careful coordination and may become unmanageable as the infrastructure scales.
- Impact on Applications: Implementing restrictive policies without thorough testing can inadvertently disrupt application functionality, leading to downtime or performance issues.
- Continuous Progression: Network policies need to evolve alongside application changes and updates, requiring ongoing monitoring and adjustments to remain effective.
Addressing these challenges requires a combination of careful planning, robust tooling, and continuous monitoring to ensure that Kubernetes network policies effectively balance security and operational requirements.
ARMO Platform’s Kubernetes Network Policy
As organizations embrace cloud-native architectures and Kubernetes for container orchestration, ensuring robust network security becomes increasingly hard. Manual creation and management of Kubernetes network policies can be time-consuming and error-prone, often leading to misconfigurations and security gaps. Our new feature addresses these challenges by automating the generation of network policies based on workload behavior, leveraging the power of eBPF to provide insights and enable the control you need.
Key features
- Identify all the workloads missing network policies
- Auto-generated Kubernetes network policies based on workload behavior
- Network policies visualization – simple and intuitive network policy graph
- Smart IP Enrichment enables identifying IP addresses associated with cloud providers according to CIDR range. Thus, enabling efficient routing and defining firewalls based on CIDR range.
Key benefits
- Streamlined Security: By automatically generating network policies based on application runtime, organizations can effortlessly apply fine-grained security controls without the need for manual intervention. This streamlines security tasks and reduces the risk of misconfigurations.
- Enhanced Efficiency: With auto-generated network policies, security teams can focus their time and resources on strategic initiatives rather than mundane policy management tasks. This increases operational efficiency and agility, allowing teams to adapt quickly to changing security requirements.
- Seamless Integration: Our feature seamlessly integrates with native Kubernetes environments, ensuring compatibility and ease of deployment. Whether you’re running microservices, monolithic applications, or hybrid workloads, ARMO Platform provides consistent security across the board.
- Real-time Insights: Leveraging eBPF technology, ARMO Platform offers real-time insights into workload behavior and network traffic patterns. This granular visibility enables proactive threat detection and response, empowering organizations to stay one step ahead of cyber threats.
How it works
ARMO Platform’s auto-generated Kubernetes network policy feature analyzes workload behavior and communication patterns within the Kubernetes cluster. Based on this analysis, it automatically generates network policies to regulate traffic flows between pods and services. Whether it’s enforcing segmentation, access control, or traffic encryption, ARMO Platform adapts dynamically to the evolving needs of the environment.
Network Policy generation
Generating Network policy involves five steps, as described in the following sections:
- Set the scope and generate policy
- Review the detected communications and topology graph
- Download the resulting file(s)
- Apply the network policy in your dev environment and run tests
- Deploy to the production environment
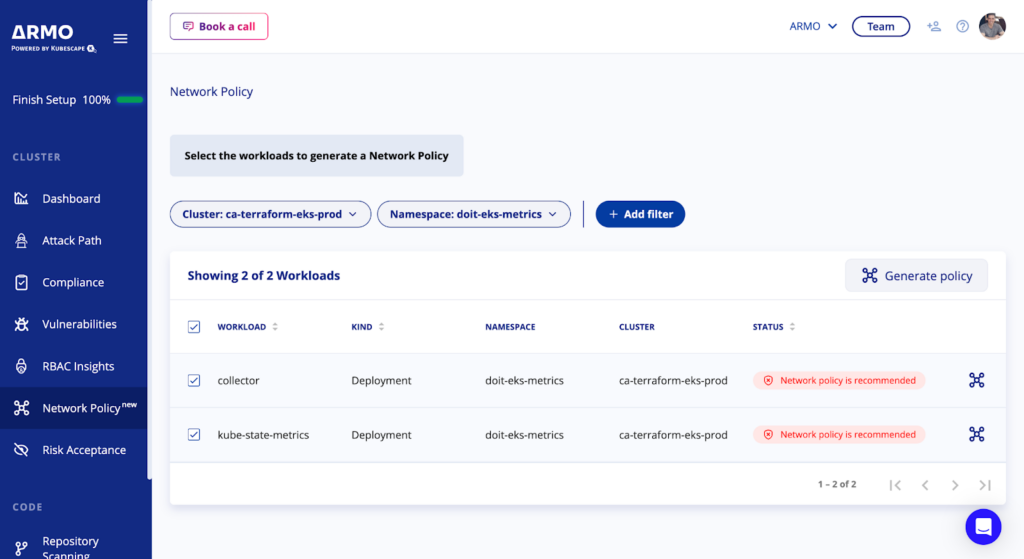
Set the scope and generate policy
- Choose Cluster and Namespace from the drop-down filters.
- Filter by the status, and select Network policy is recommended.
- Select the workloads for which you want to create a policy.
- Click on Generate policy.
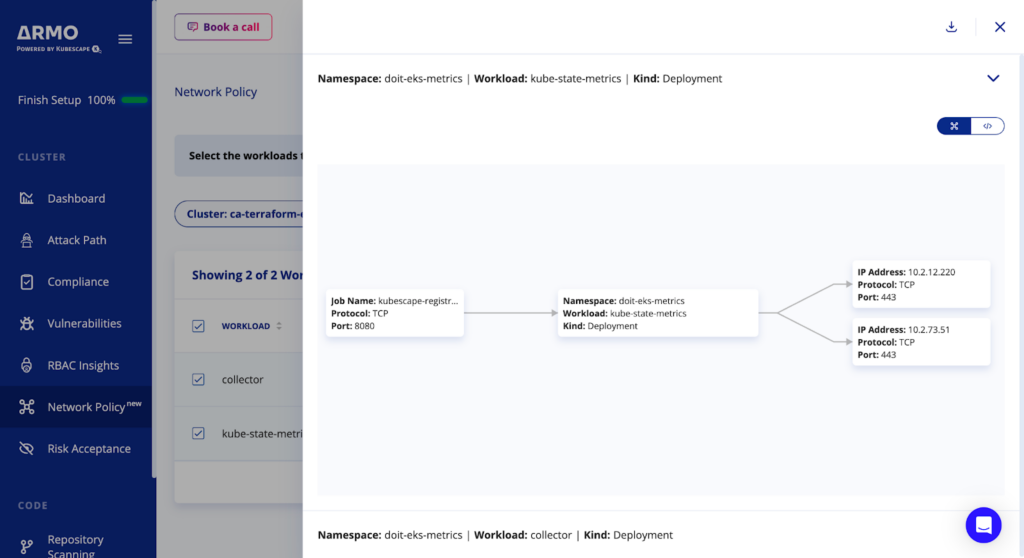
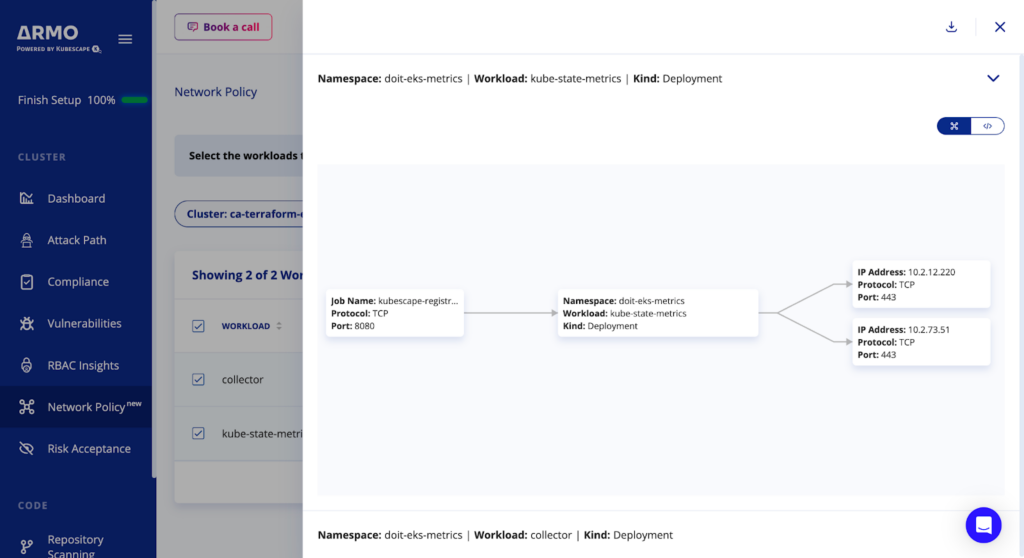
Review the detected communications and topology graph
Use the graph view to visually validate if this is the policy you want, or if something should be changed.
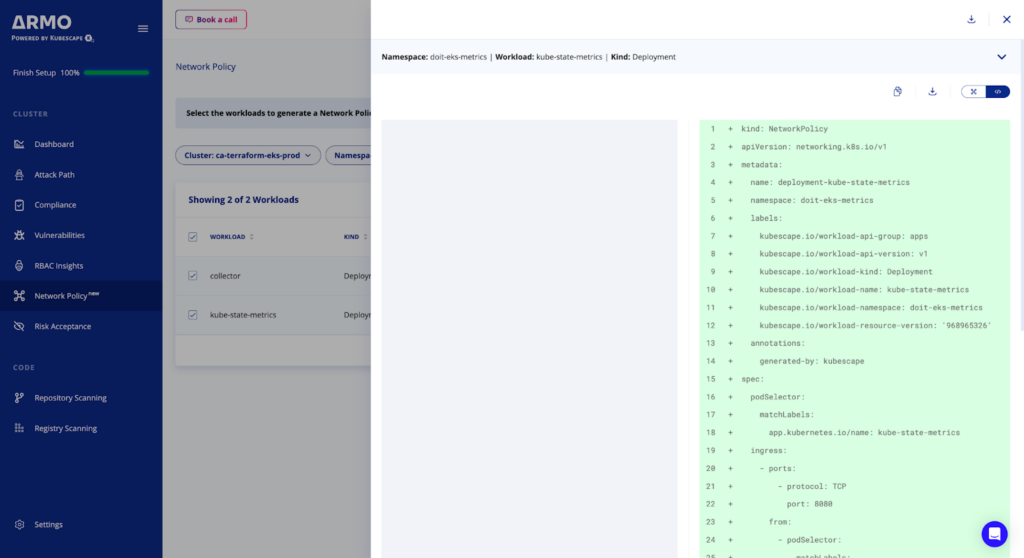
Toggle on the code View to see the raw YAML output of the network policy recommended for that workload.
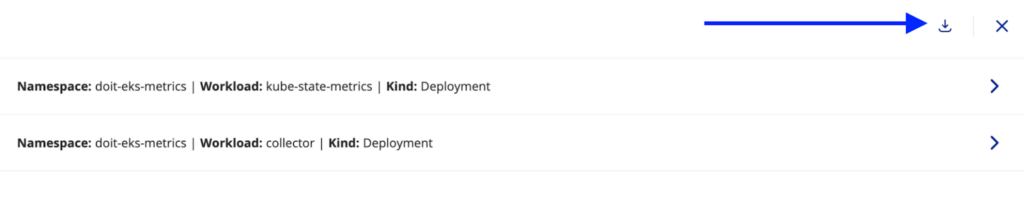
Download the resulting file(s)
After reviewing the generated network policies, click on the Download button to download all the policies, or you can select to download the selected policy:
Applying the Network Policy
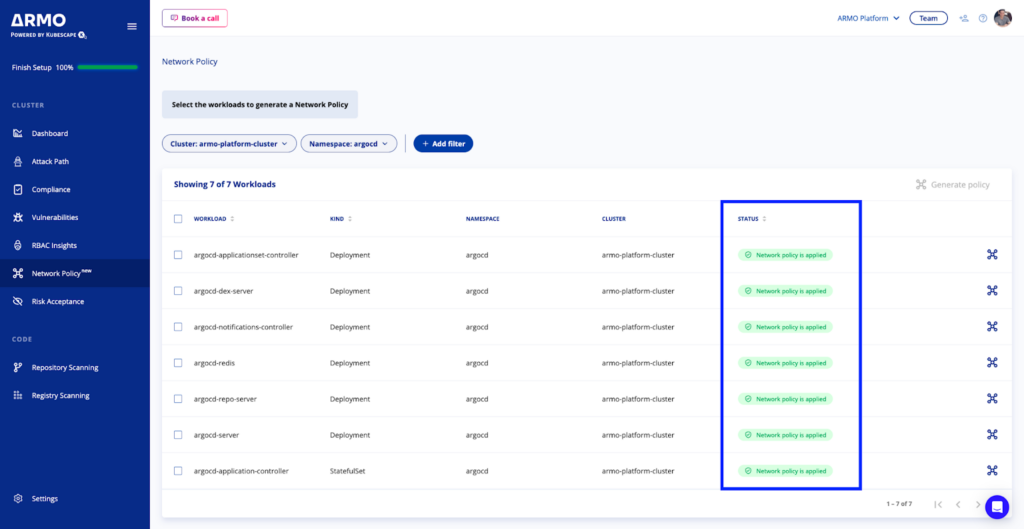
Once you’ve applied the network policy, ARMO Platform identifies, and updates the status automatically to ‘Network policy is applied’
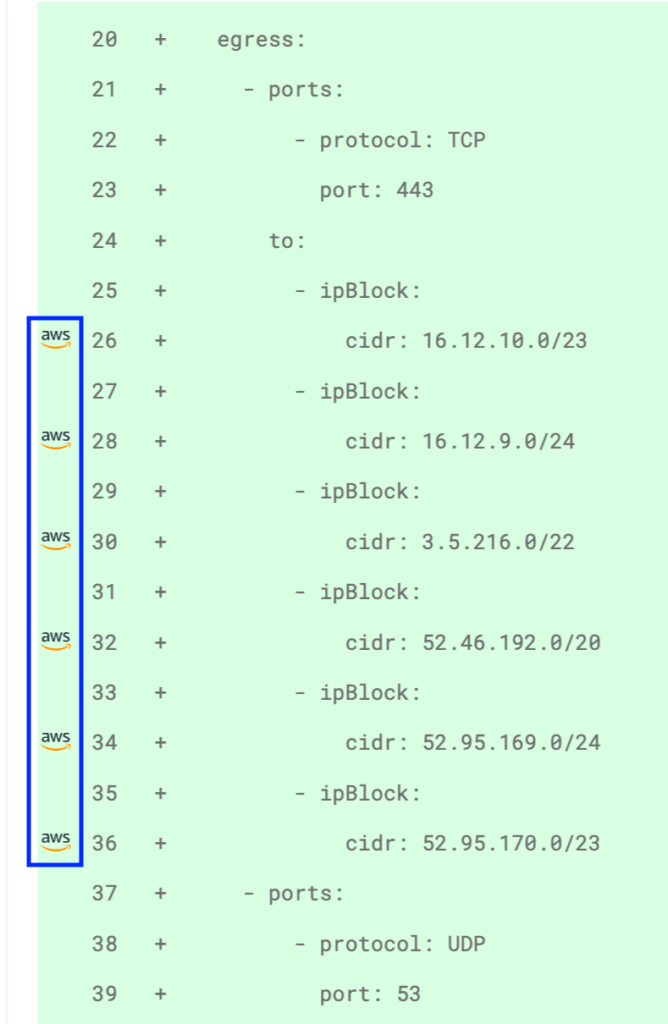
Smart IP Enrichment
Highlights the CIDR range an IP address belongs to (e.g. a cloud provider) enabling efficient routing and defining firewalls based on CIDR ranges.
Future plans
Looking ahead, we’re committed to enhancing the ARMO Platform’s network policy capabilities by adding support for additional CNIs such as Calico, Cilium, and Istio. By extending compatibility with these popular networking solutions, we aim to bring all network policy generation and maintenance to one, security-aware, place.
Conclusion
It’s important to keep Kubernetes environments protected from threats. ARMO Platform’s Auto-Generated Kubernetes Network Policy feature, powered by eBPF technology, offers unique automation, efficiency, and control. With this innovative solution, organizations can achieve seamless security without compromising operational agility, empowering them to confidently embrace cloud-native architectures.
Experience the future of Kubernetes security with our auto-generated network policy feature. Get started today and unlock a new level of protection for your containerized workloads.

Actionable, contextual, end-to-end
{Kubernetes-native security}
From code to cluster, helm to node, we’ve got your Kubernetes covered:
Cut the CVE noise by significantly reducing CVE-related work by over 90%
Automatic Kubernetes compliance for CIS, NSA, Mitre, SOC2, PCI, and more
Manage Kubernetes role-based-access control (RBAC) visually
The post The Future of Kubernetes Network Policy appeared first on ARMO.
*** This is a Security Bloggers Network syndicated blog from ARMO authored by Yossi Ben Naim. Read the original post at: https://www.armosec.io/blog/kubernetes-network-policy-future/
如有侵权请联系:admin#unsafe.sh