
2024-3-12 22:0:0 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
Accurate and timely threat intelligence is critical for successful security operations centers. In simple terms, threat intelligence can be defined as evidence-based knowledge, including context, indicators, implications, mechanisms, and actionable advice that is related to current or emerging threats to assets. Check out this Automating Threat Intelligence Enrichment blog to learn more about what threat intelligence automation is, why it is important, and common challenges associated with it.
Artificial Intelligence and Threat Intelligence
Much like automation, generative artificial intelligence (AI) is an innovative technology that brings speed and simplicity to any process that it is applied to. Threat detection, intelligence, and prevention are a few of the many cybersecurity functions that are enhanced by the combination of AI and automation.
Swimlane Turbine, the low-code security automation platform, brings this combination to life with the recent introduction of its collection of AI innovations, known as Hero AI. One of the founding HeroAI features is a Text-to-Code ChatBot that uses AI to simplify automation development. Keep reading this blog to dive deep into a practical Threat Intelligence use case that showcases the effectiveness of Hero AI Text-to-Code capability.
3 Steps to Automating Threat Intelligence with AI
Step 1: Determine if the threat is benign or malicious
Automating threat intelligence begins with data from a threat intelligence tool that provides a numerical score. Once the SOC analyst has this score, their goal is to ascertain the nature of the threat, whether it is malicious or benign.
To accomplish this task, the first step is to submit a query to Hero AI. The query should ask the Text-to-Code assistant something like “evaluate the score; designate it as ‘malicious’ if score exceeds 50, and as ‘benign’ if score falls below 50.”

With a single click, the chat assistant auto-generates the required Python code snippet. The user can seamlessly copy the snippet to the clipboard and even test it directly within the Python action script to explore their outcomes before applying it in playbooks in Turbine. This pre-action testing feature accelerates the building process and eliminates the requirement for manual trial and error.
Step 2: Automate Email Filtering
From there, the SOC analyst should possess a list of objects representing emails, each comprising ‘subject’ and ‘body’ fields. Now, the objective is to streamline the list by excluding emails that do not contain specific keywords in the subject. For example, the individual may wish to retain only those emails where the term ‘spam’ is present in the subject.
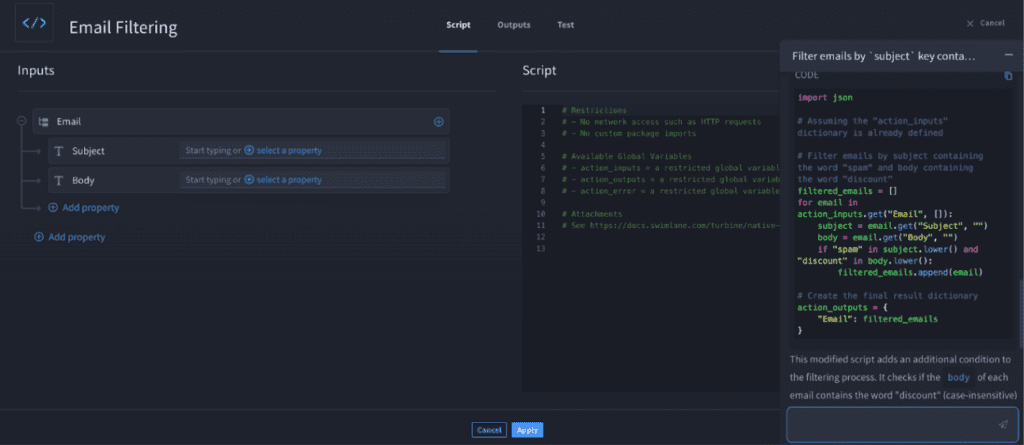
To accomplish this task, query the HeroAI Text-to-Code assistant with a message like “Filter emails by ’subject’ key containing word ‘spam’.”

Step 3: Refine Threat Intelligence Filters as Needed
In the previous example, which filtered emails by a subject containing the word ‘spam’, the chat assistant provided a ready-to-copy script for the Python script action. Now, there is an additional requirement: filtering emails to include the word ‘discount’’ in the body. The chat assistant can generate a script for this purpose as well. This allows for seamless integration of both the ‘spam’ and ‘discount’ filters into a single code block as shown above.
This process of refining the script can continue with additional follow-up questions to the extent needed for the specific threat intelligence use cases. It just takes a few seconds for Hero AI to incorporate a new bit of logic into the previously generated code.
The Results: 50% Time Savings
Numerous Swimlane customers have tested this threat intelligence use case with the help of Hero AI Text-to-Code. They experience that the Python scripts are generated, debugged, and tested faster than previously possible with Swimlane Turbine Hero AI capabilities. On average, customers have reported 50% time savings. They are now able to build complete end-to-end use cases in 25 minutes vs 56 minutes.

For a more detailed walkthrough of how to automate threat intelligence with Swimlane Turbine, request a demo here.
Request a demo
If you haven’t had the chance to explore Swimlane Turbine yet, request a demo.
如有侵权请联系:admin#unsafe.sh