
Non-human identities (NHI) are digital, automated and programmable access credentials that play a crucial role in securing systems, managing access, and ensuring the integrity of digital environments. NHIs come in the form of API keys, OAuth tokens, service accounts, and secrets, and are created daily by employees as they delegate access to external entities to automate tasks and increase business efficiency. Unlike human access, or user access, that are rigorously protected with Identity Access Management (IAM) policies and tools like multi-factor authentication (MFA) and single sign-on (SSO), NHI’s are more difficult to secure due to lack of visibility, monitoring, and governance.
What’s the difference between human and non-human identities?
Human identities have security protocols that are easily tracked, monitored and have immense oversight as they are protected with policies and tools like MFA, IP restrictions, etc. On the contrary, non-human identities – tokens, secrets, and other machine credentials – are not given sufficient security measures. Compounding the issue, these credentials often lack expiration dates and are excessively permissive. While expiration and proper scoping can mitigate some risks, the absence of security protocols remains a glaring gap. For instance, if a token is compromised, it grants attackers unrestricted access and can evade detection effectively.
What are the common drivers of non-human identities?
Automation is the most frequent driver in the creation of non-human identities in order to streamline repetitive tasks and workflows, reducing human intervention and increasing operational efficiency. Here are two other factors that continue to push the ungoverned creation of non-human identities:
- Consent fatigue: End users have become so accustomed to window prompts, clicking “allow” or “next” to grant permissions and access to third party apps so the user can fulfill a business goal. As end users integrate applications into the business environment, it consequently increases connections, as well as, ungoverned human access.
- Permissions: Non-human access is naturally over-permissive – so much so that Astrix has found 23% of apps connected to Google Workspace environments have very wide access permissions to the organization’s most sensitive data. Security teams could restrict end users from adding these integrations all together, or opt for manual processes – but due to the rate of automation and cloud adoption, this is not commonly practiced.

How do NHIs operate?
Take an OAuth application, for example, which is one of the most common types of non-human access credentials. Once an OAuth app establishes a connection with another application, the user authorizes access via a consent screen. Then the connected application generates an authorization code, which the OAuth app exchanges for an access token. This token serves as a secure credential, granting the OAuth app permission to access designated resources or execute authorized tasks within the connected application on behalf of the user. It’s crucial to recognize that there are no usage restrictions, and the credential remains accessible to the application’s owner indefinitely.

Why are non-human identities the biggest blindspot?
Managing non-human identities is a critical aspect of cybersecurity governance, as they represent potential points of vulnerability if not properly managed and secured. For instance, the sprawl of third party non-human access to enterprise environments like Salesforce, GitHub and Microsoft365 create a largely ungoverned attack surface. Adding to this plethora of ungoverned access, developers also create secrets that connect internal services and resources to automate processes and improve business efficiency. However, these secrets are sprinkled throughout the organization, often owned and operated by different managers, proving it even more difficult to see each NHI.
Astrix research shows that there are about 10,000 non-human connections for every 1,000 users. As the amount of NHI’s continues to grow, so do the potential risks. Regardless of the size of an organization, anyone can be targeted. There have been a number of NHI-related attacks, from conglomerates like Microsoft, Okta, and Slack.
Are security teams falling short in preventing NHI breaches?
Yes, and no. Attackers are hyper focused on the supply chain because of the vast array of sensitive data they are given access to if they successfully breach an organization. Security teams have certainly realized supply chain attacks are more common than not, but the struggle is finding how to prevent them from happening in the first place. And if they already happened – IR efforts of finding everything that can be accessed by the breached vendor are a huge task as well.
According to Gartner, “Software supply chain attacks have added a new dimension to software security problems because the software delivery pipelines and the tools used to build and deploy software are the new attack vectors.” For instance, in October 2023 Okta’s support ticket system was breached using a compromised service account, which led to another breach from Cloudflare, where their entire Atlassian suite was hacked due to the same leaked credentials. These vendor attacks create a ripple effect into the technology supply chain, which creates even more of a challenge for security teams to protect the business against a potential breach.
Ways to address the non-human identity challenge and growing threat vector
As non-human access continues to spread, so do the amount of teams that need to align in order to create a successful non-human identity security strategy. Privacy, third party risk management (TPRM), security teams, developers, etc. – they all contribute to these newly created access points across CRM tools, development pipelines, GenAI tools, and more. By collaborating across all business disciplines, security strategies can be enhanced – identifying third-party digital fingerprints and permission changes so if the organization is hacked, all teams have an understanding of the potential impact and how best to respond.
How Astrix is paving the way for businesses to (securely) leverage non-human access
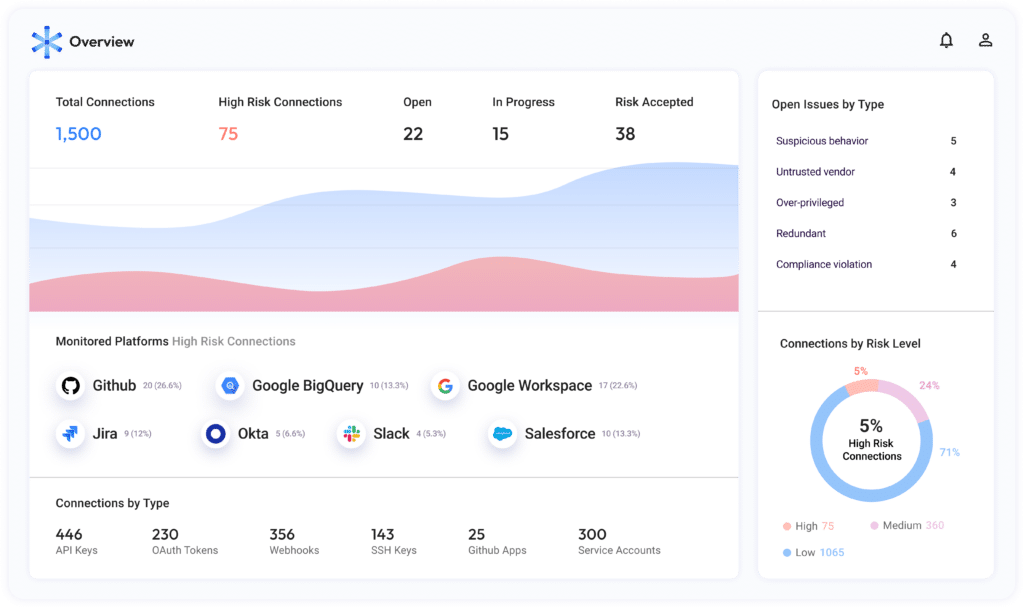
Astrix has engineered a solution precisely tailored to meet all of the needs mentioned above. By automatically compiling a registry of non-human entities accessing enterprise settings – including engineering or business platforms like GitHub, Salesforce, and Microsoft365 – then identifying over privileged, redundant, or malevolent integrations, organizations can uncover and address supply chain vulnerabilities. This can be achieved without impeding the capability of business users to deploy necessary integrations for sustained productivity.
Utilizing an agentless methodology, Astrix furnishes exhaustive insight into non-human entities spanning all SaaS, PaaS, and IaaS environments. The Astrix Security platform empowers businesses to pinpoint non-human access, recognize potential risks, rectify deficiencies, and oversee the entire lifecycle of non-human identities to preempt new or potential risks.
Astrix truly allows, and ensures, that businesses can harness the full potential of automation and connectivity while upholding robust security measures.
The post What are non-human identities? appeared first on Astrix Security.
*** This is a Security Bloggers Network syndicated blog from Astrix Security authored by Danielle Guetta. Read the original post at: https://astrix.security/what-are-non-human-identities/
如有侵权请联系:admin#unsafe.sh