
2024-3-21 00:30:0 Author: www.tenable.com(查看原文) 阅读量:6 收藏

Explore how Tenable One for OT/IoT helps organizations stay ahead in today's evolving threat landscape with end-to-end visibility and cyber risk prioritization across IT, OT and IoT.
Visibility serves as the cornerstone of security, offering organizations the means to monitor, analyze, and safeguard their digital infrastructure effectively. By maintaining a comprehensive inventory of IT, OT and IoT devices, organizations can gain insights into their network topology, identify potential weak points and ensure adherence to security policies. Moreover, real-time visibility enables security teams to proactively mitigate threats before they can escalate into a full-blown crisis.
However, achieving visibility over IT and OT domains presents a challenge, exacerbated by the diverse nature of these devices and their disparate systems. Traditional security measures designed for IT environments fall short when applied to the unique characteristics of OT and IoT ecosystems. This creates the need for specialized solutions tailored to specific enterprise requirements. In the first and second posts of this three-part blog series, we highlighted key challenges that limit the modern enterprise’s ability to protect its OT and IoT assets. In this post, we dive deeper into four strategies to gain complete IT, OT and IoT asset visibility, and how Tenable’s exposure management platform can improve your security posture.
1. Discover assets and monitor risks
OT and IoT environments comprise a diverse range of devices with varying management methods and communication protocols. To address these unique requirements, a blend of passive and active discovery and monitoring approaches should be applied to achieve an accurate and up-to-date inventory, and to identify asset-related risks, such as misconfigurations and vulnerabilities.
However, OT and IoT devices have unique characteristics, so if you try to discover them using detection tools designed for IT assets you may end up with errors, memory overload and unexpected downtime. For this reason, you should use tools designed to discover OT and IoT assets in order to maintain uptime and reliability.
For example,passive discovery techniques that listen to network traffic can be used to safely identify OT and IoT assets. This method listens to network communications and analyzes patterns to determine the presence of devices. Passive discovery has the added benefit of detecting new devices as they are added to the network, as well as assets that may come and go periodically that also pose a risk. Passive listening can also identify some of the unique characteristics of assets, which can be used to identify them and to populate a subset of asset details.
With a baseline understanding of the IoT and OT assets in the network, and of their identifying characteristics, we can apply native communications – those designed specifically to interact with a specific asset – to actively discover additional asset details, such as firmware version and configuration, as well as asset risks, including vulnerabilities, misconfigurations and changes in configuration.
By continuously monitoring the network through passive listening and periodically conducting active queries, organizations can adapt their security measures to the evolving threat landscape and changes in the network environment.
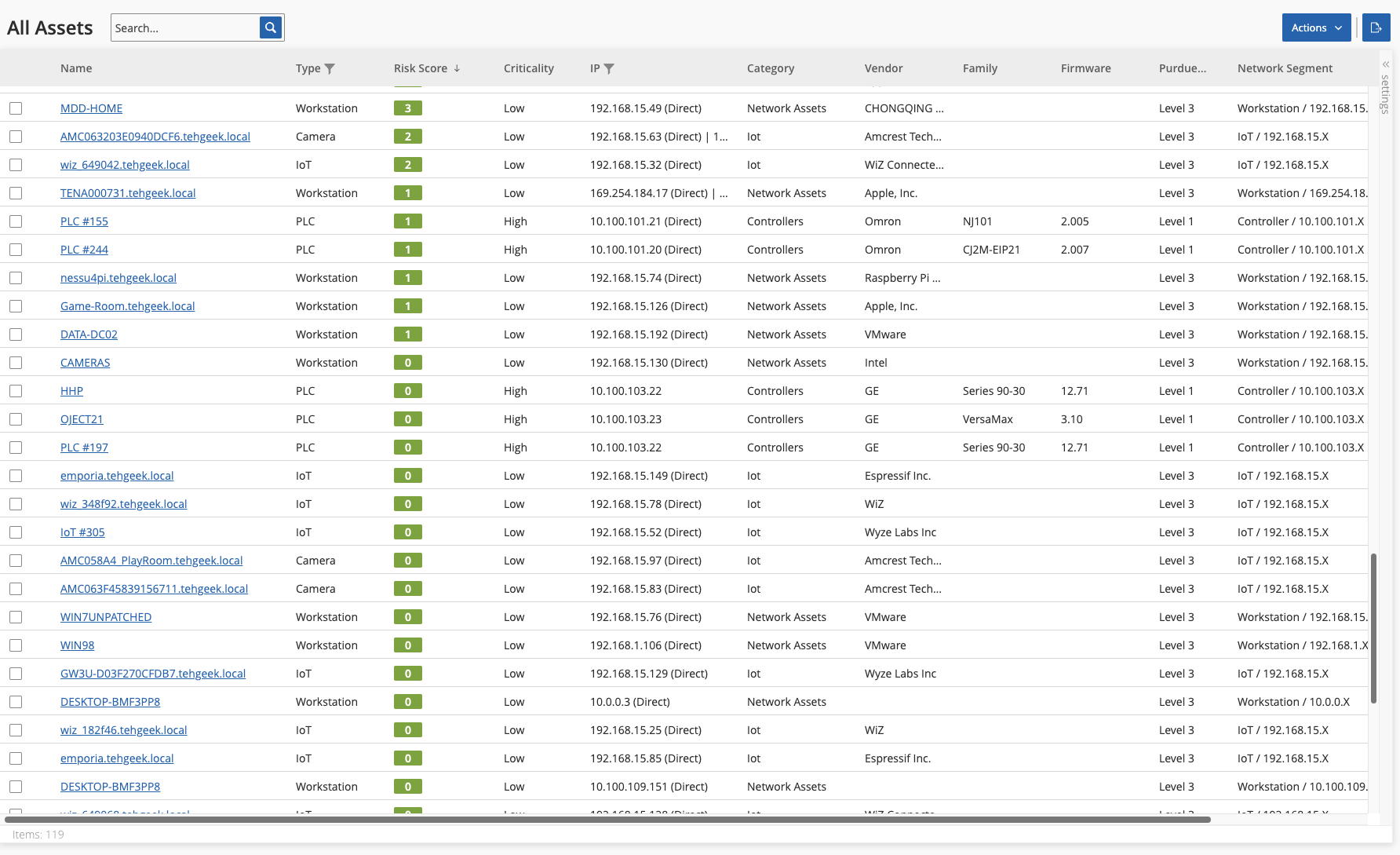
2. Maintain an inventory of assets and risk details
Asset details play a key role in supporting various functions across the organization, but are vital to effectively scale prioritization and remediation of security risks. We explore some of the key attributes below and their relevance to security.
Device Information
- Device type: Identifying the type of device (e.g., PLC, SCADA system, sensor, IoT device) provides insights into its functionality and purpose within the network.
- Make and model: Knowing the make and model of the device helps in understanding its specifications, capabilities, and potential vulnerabilities.
- Firmware/software Version: Tracking firmware or software versions is essential for identifying known vulnerabilities and ensuring that devices are up-to-date with security patches.
- Serial number: Assigning unique identifiers to devices facilitates asset tracking, identification of asset owner, and management.
Network Connectivity
- IP address: Recording IP addresses enables network mapping and facilitates monitoring and management of device connectivity.
- MAC address: MAC addresses aid in uniquely identifying devices on the network and can be used for access control and security purposes.
- Port configuration: Understanding which ports your devices are utilizing helps in assessing potential attack vectors and securing network access points.
- Network segmentation: Identifying which network segments your devices belong to assists in implementing appropriate security controls and isolation measures.
Configuration and Settings
- Default credentials: Identifying devices with default or weak credentials helps mitigate the risk of unauthorized access and credential-based attacks.
- Configuration parameters: Documenting device configurations, such as communication protocols, encryption settings and access controls, ensures consistency and facilitates security auditing.
- Access controls: Understanding who has access to configure or interact with devices, and the level of permissions they possess, is crucial for enforcing security policies and preventing unauthorized changes.
Operational Data
- Operational status: Monitoring the operational status of devices provides insights into their health, performance and availability.
- Sensor data: For IoT devices, capturing sensor data such as temperature, humidity, or pressure readings may be critical for operational monitoring and decision-making.
- Data flow: Understanding how data is collected, processed, and transmitted by devices helps in assessing data security risks and compliance requirements.
Physical Location
- Geographical location: Knowing the physical location of devices assists in asset tracking, maintenance planning and responding to physical security incidents.
- Environmental conditions: Documenting environmental factors such as temperature, humidity and exposure to hazardous conditions helps in assessing device reliability and lifespan.
Lifecycle Information
- Installation date: Tracking when devices were installed provides insights into their lifecycle and helps in planning maintenance and replacement schedules.
- End-of-life/support date: Identifying devices approaching end-of-life or end-of-support enables proactive measures to mitigate risks associated with outdated technology.
Risk and Activity Monitoring:
- Vulnerabilities: Identifying known vulnerabilities in assets is useful to determine the Vulnerability Priority Rating (VPR).
- Network Activity: Identifying traffic source, type, destination and volume is useful in identifying anomalous communications, such as those with external destinations.
- Conversations: Identifying conversations detected in the network, with details about the time they occurred, and involved assets is useful in asset mapping.
3. Visualize attack paths to prioritize risk
Asset details, risk information and communications are also vital for network mapping and prioritization of risk. All too often, breaches in OT and IoT environments originate with vulnerable IT assets, which when compromised give hackers elevated privileges and allow them to carry out attacks, such as ransomware. An understanding of asset relationships is vital to map and visualize attack vectors or paths which are at high risk of exploitation. To identify the most critical attack vector, it’s necessary to factor in multiple parameters and use a risk-based approach. When mapped, factors such as asset risk level, attack path length, communication methods, and external vs internal connectivity allow for improved prioritization and remediation. That way you can, for example, minimize or reduce access to external networks, or close ports and remove services that are not vital, which contribute to higher risk exposure.
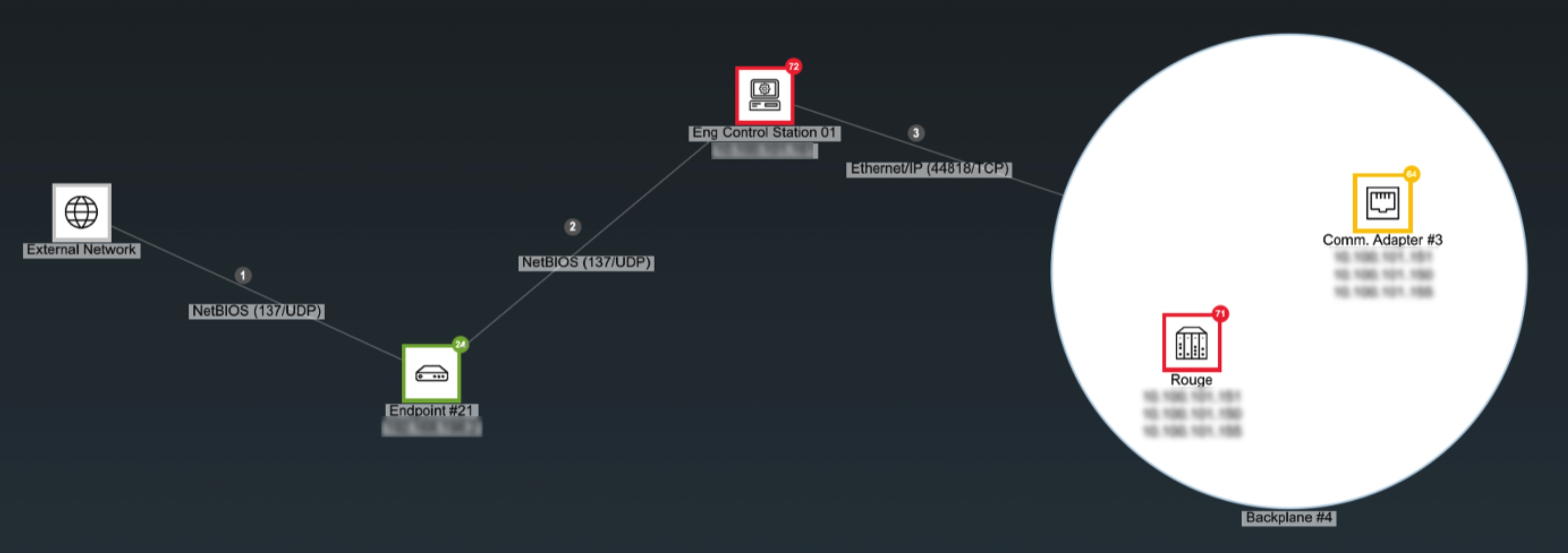
While technically all identities are assets that must be managed, it is important to call out that most domain-specific security tools lack discovery and visibility into identities and their associated risks. For example, these tools typically don’t identify misconfigurations that can lead to excessive permissions, or that can leave identities vulnerable to exploitation, such as weak passwords.
In the world of OT in particular, the implications of visibility gaps for identities and risk can be great because asset downtime can have a high cost and sometimes lead to unsafe working conditions or even loss of life. OT/IoT security tools, and identity security tools that can integrate with a holistic exposure management platform, can be of great value, because they can feed all relevant asset information needed to do cross-domain attack path analysis. For more insights on this, read this blog series’ second post “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform: The Importance of Contextual Prioritization.”
4. Quantify business exposure with asset tagging
As we explained in that second blog, the ability to logically group and tag assets within Tenable One for OT/IoT is an important element for defining an Asset Criticality Rating (ACR). Device type, make and model, physical location, and network segment can all be used to group and tag assets that are associated with mission critical OT and IoT environments. For example, network segmentation that indicates a cooling system is part of a manufacturing plant floor, as opposed to part of a cafeteria, can be used to elevate the ACR. Similarly, a workstation on the production plant can do more damage than a personal laptop in a guest network.
Asset tags in Tenable One for OT/IoT can also be used to aggregate multiple asset groups to create exposure cards aligned to critical business functions and to determine an overall Cyber Exposure Score (CES) for a business function. Similarly, human and machine identities with access to the same network segments as OT and IoT assets can be aligned to the same exposure card. In this way, total risk can be considered and used for prioritization of resources and investments.
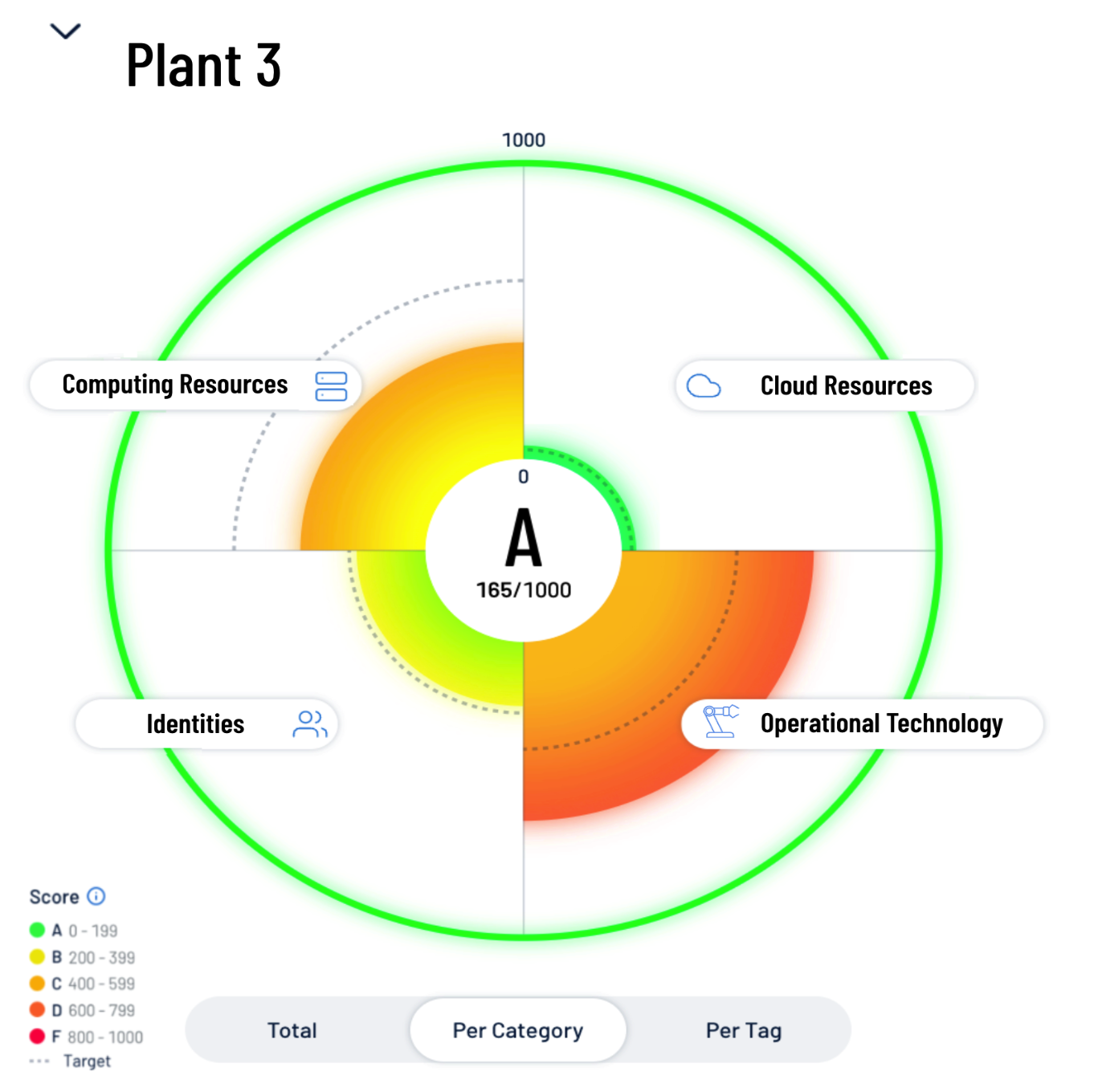
Gain complete visibility across the entire attack surface
Tenable One for OT/IoT helps organizations gain visibility across the modern attack surface – IT, OT and IoT assets; focus efforts to prevent likely attacks; and accurately communicate cyber risk to support optimal business performance. The platform combines the broadest vulnerability coverage spanning IT assets, cloud resources, containers, web apps, identity systems, and OT and IoT assets, builds on the speed and breadth of vulnerability coverage from Tenable Research, and adds comprehensive analytics to prioritize actions and communicate cyber risk.
Tenable One for OT/IoT enables organizations to:
- Get comprehensive visibility of all assets and their vulnerabilities, whether on-premises or in the cloud, and understand where the assets are exposed to risk.
- Anticipate threats and prioritize efforts to prevent attacks by using generative AI and the industry's largest data set of vulnerability and exposure context.
- Communicate exposure risk to business leaders and stakeholders with clear KPIs, benchmarks and actionable insights.
- Leverage the broadest vulnerability coverage spanning IT assets, cloud resources, containers, web apps and identity systems.
- Integrate with third-party data sources and tools for enhanced exposure analysis and remediation.
Tenable One for OT/IoT moves organizations past point solutions and organizational silos to achieve complete visibility and an accurate inventory of IT assets across the entire modern attack surface, including OT and IoT devices.
Schedule a free consultation and demo
Want to see what Tenable One for OT/IoT can do for your organization? Schedule a free consultation to receive a quick technical demo and to discuss how we can help improve your security program and results.
For more information about Tenable One for OT/IoT, visit tenable.com/products/tenable-one and sign up for our webinar “The Invisible Bridge: Recognizing The Risk Posed by Interconnected IT, OT and IoT Environments” for a deep dive on the topics covered in this post.
Learn more
- How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform (blog)
- How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform: The Importance of Contextual Prioritization (blog)
- Tenable Introduces Groundbreaking Visibility Across IT, OT and IoT Domains to Fully Illuminate Attack Vectors and Risks (press release)
- The Invisible Bridge: Recognizing The Risk Posed by Interconnected IT, OT and IoT Environments (webinar)

Jeff Rotberg
In his role as Director of Business Development at Tenable, Jeff Rotberg leads partnerships and strategy for Tenable OT Security. Jeff has over 10 years of experience working in industrial automation and OT environments. Previously, he held multiple sales and technology roles at Rockwell Automation, a leading industrial automation original equipment manufacturer (OEM). Jeff holds a bachelor of science in electrical engineering from UNC Charlotte.
Related Articles
- Exposure Management
- OT Security
- SCADA
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh