2024-3-25 21:59:51 Author: securityaffairs.com(查看原文) 阅读量:13 收藏
Iran-Linked APT TA450 embeds malicious links in PDF attachments

In recent campaigns, Iran-linked APT group MuddyWater used a legitimate Remote Monitoring and Management (RMM) solution called Atera.
Proofpoint researchers observed the Iran-linked APT group MuddyWater (aka SeedWorm, TEMP.Zagros, TA450, and Static Kitten) was behind a new phishing campaign in March 2024 that attempted to drop a legitimate Remote Monitoring and Management (RMM) solution called Atera on the target systems.
The campaign targeted Israeli employees of large multinational organizations with a pay-related social engineering lure.
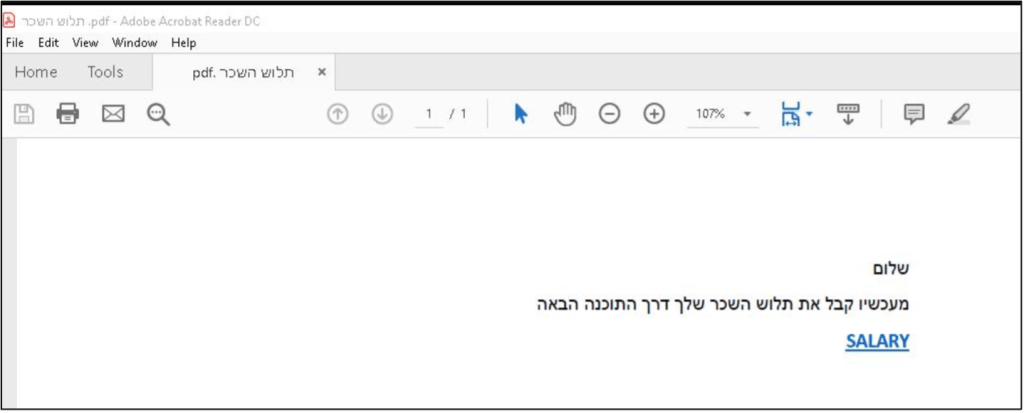
The phishing campaign started on March 7 and continued through the week of March 11, 2024. The TA450 group sent spear-phishing messages with PDF attachments containing malicious links.
The threat actors sent multiple phishing emails with PDF attachments with slightly different embedded links to the same recipients.
The links employed in the campaign were related to several file-sharing sites, including Egnyte, Onehub, Sync and TeraBox. Some of the messages were also sent using a likely a compromised .IL sender account.

Upon clicking on the link that is included in the PDF, a ZIP archive containing a compressed MSI ise served to the recipient.
The installer would install the remote administration software named AteraAgent, which was used by the TA450 APT in other campaigns.
Proofpoint attributes this campaign to TA450 based on the observation of tactics, techniques, and procedures associated with the cyberespionage group, campaign targeting, and malware employed in the attack.
“This activity is notable for several reasons, including that it marks a turn in TA450’s tactics. While this campaign is not the first observed instance of TA450 using attachments with malicious links as part of the threat actor’s attack chain, it is the first time Proofpoint researchers have observed TA450 attempt to deliver a malicious URL in a PDF attachment rather than directly linking the file in an email.” reads the report published by Proofpoint. “Additionally, this campaign is the first time Proofpoint has observed TA450 using a sender email account that matches the lure content. For example, this campaign used an email account of salary[@]<compromisedorg>co[.]il, which is in alignment with the various pay-themed subject lines.”
The report includes Indicators of compromise (IOCs) for this campaign.
The first MuddyWater campaign was observed in late 2017, when the APT group targeted entities in the Middle East.
The experts called the campaign ‘MuddyWater’ due to the confusion in attributing a wave of attacks that took place between February and October 2017 targeting entities in Saudi Arabia, Iraq, Israel, United Arab Emirates, Georgia, India, Pakistan, Turkey, and the United States to date. The group evolved over the years by adding new attack techniques to its arsenal. Over the years the APT group also has also targeted European and North American nations.
The group’s victims are mainly in the telecommunications, government (IT services), and oil sectors.
In January 2022, US Cyber Command (USCYBERCOM) officially linked the MuddyWater APT group to Iran’s Ministry of Intelligence and Security (MOIS).
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, TA450)
如有侵权请联系:admin#unsafe.sh