
2024-3-25 23:30:40 Author: www.sentinelone.com(查看原文) 阅读量:11 收藏
Last week, PinnacleOne flagged the ongoing SVR exploitation of their breach of Microsoft.
This week, we examine the geopolitical dynamics and risks facing firms that do business or have key dependencies in China and highlight principles to frame a China-for-China strategy given firm-specific threat models.
Please subscribe to read future issues — and forward this newsletter to your colleagues to get them to sign up as well.
Feel free to contact us directly with any comments or questions: [email protected]

Insight Focus | Enterprise Risk Management in China
China’s civilian intelligence service, the Ministry of State Security (MSS), ventured into public policy analysis when it posted on WeChat this Monday. In its post, the MSS underlined how important private sector cooperation with the security services is to safeguarding national security under the country’s Cybersecurity Law. Some sections even highlighted the need for security assessments for businesses transferring data overseas. An English-language state media outlet went so far as to put out an accompanying piece.
We don’t know what motivated the MSS and state media to highlight the PRC’s Cybersecurity Law – but we do know what they said and its implications.
Despite other parts of state media posting videos of Apple’s CEO Tim Cook walking around Shanghai and saying that China is open for business, the experience of executives trying to navigate the expanding labyrinth of PRC regulations is not so sanguine.
In the course of our advisory work, we have walked alongside a number of key leaders making decisions about how to approach their operations in the PRC. We find that, as China convinces other countries to join its “Community with Shared Future in Cyberspace” initiative, the risks below, the questions they raise, and resulting business decisions will become more pressing and may soon extend to other countries as well.
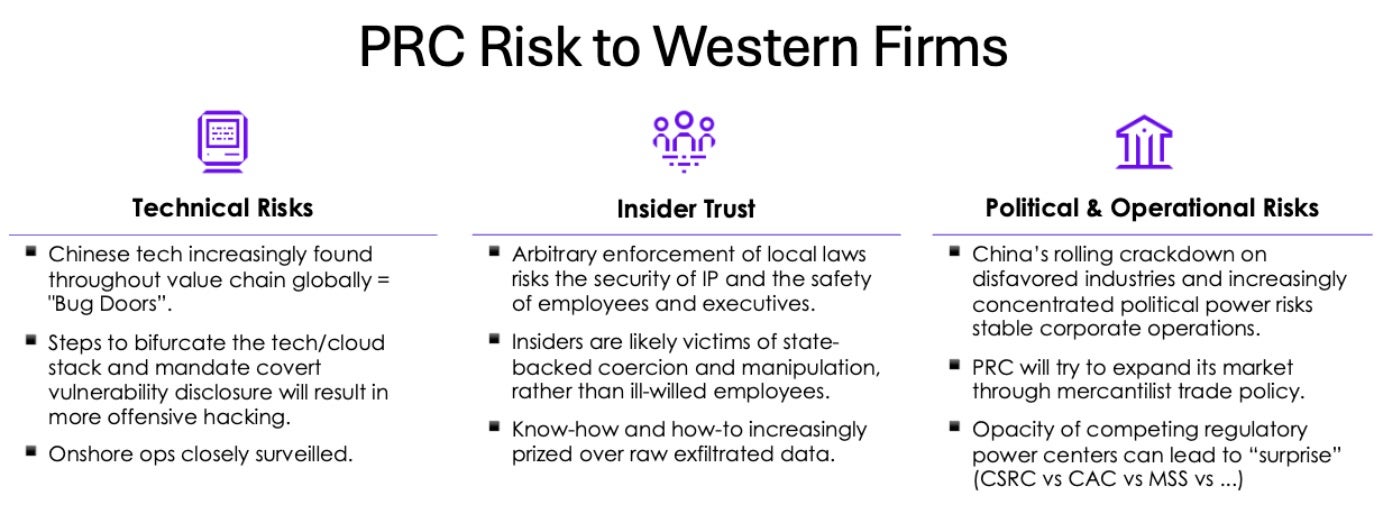
Business Risks Facing MNC Operations in China
- Technical Risks: Chinese tech increasingly found throughout the global value chain will create “Bug Doors.” Moves to bifurcate tech stacks will result in more offensive hacking between the PRC and the rest and onshore operations are closely scrutinized.
- Insider Trust: Arbitrary enforcement of local laws risks the security of IP and the safety of employees and executives — the PRC is sliding back to join other autocracies.
- Insiders are likely victims of state-backed coercion and manipulation, rather than ill-willed employees.
- The MSS offers cash payouts to anyone who reports unpatriotic behavior or actions that “endanger national security.” It’s unclear if disgruntled employees reporting employers for perceived actions against China’s interest will be accepted.
- Know-how and how-to are increasingly prized over raw exfiltrated data, aligned to key strategic industries and political requirements, and in support of China’s geopolitical objectives.
- Political & Operational Risks: China’s crackdown on capital and increasingly concentrated political power risks stable corporate operations.
Key Principles That Should Frame Any China-for-China Strategy
- Navigate the Political Landscape: Each industry’s threat profile is different, and each requires its own course towards safety and resilience.
- Target Resilience: Ensure you have the flexibility to manage future uncertainties by preserving optionality and limiting irreversible decisions, when possible.
- Evaluate Enterprise Architecture: Determine how to shape the relationship between critical data storage, admin access, business impacts, and network dependencies.
- Prioritize Strictly: Identifying what capabilities to move and duplicate now will reduce implementation risk.
Strategic Threat Modeling Should Drive De-Risking Decisions
Understand what threats are most likely to present a significant impact on your value chain and prioritize enterprise operations accordingly. This assessment should answer three key questions:
- Risks Mitigated: To what extent would localizing a given application, service, or infrastructure element mitigate plausible PRC risks?
- Risks Introduced: To what extent would localizing introduce new risks, and how are those evaluated and controlled?
- Operating Model Impact: What impact would localizing have on your firm’s operating model, customer delivery, and competitive position?
Firms should apply the following decision rule: Prioritize those applications for PRC localization that maximize known risks, minimize new risks, and limit operating model impact given inherent political and geopolitical uncertainty.
Across all related enterprise architecture de-risking decisions, firms should consider the following options:
- Adjusting logical controls to databases, applications, and systems;
- Creating hybrid structures for specific databases or apps with instances inside and outside China; or
- Conducting a full separation of enterprise networks and connectivity.
These decisions are complex, hard to tangibly justify, and costly. They require the input and buy-in across the executive team with a clear, actionable roadmap that reflects priority mitigations. All activities should be tightly managed internally with senior leadership guidance and sound operational security measures. Lastly, since these are multi-month/year initiatives, firms should regularly adjust their strategies given changes in the threat model and security environment.
如有侵权请联系:admin#unsafe.sh