Authors: Gabriele Pippi, Luca Testoni, Mayank Malik, Tommaso Palma, Matteo Ferrari, Federico Totaro, Marco Giovanetti.
Summary
- Premises
- Malware Analysis and Triage Report: RuntimeBroker.exe
- IOCs - Indicator of Compromises
- Variants
1. Premises
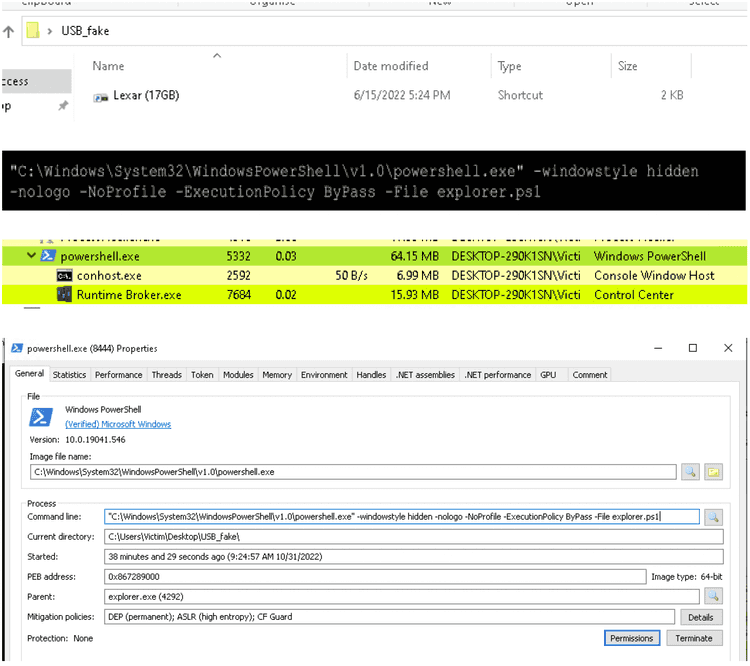
This document contains the analysis about a Windows binary file found on several customers during the last year and from the PanOptikon platform. The alerts were about suspicious traffic generated from the machine after the users inserted and opened the USB key. First analysis revealed that the usb icon is a fake image. In reality, it is a .lnk file (used in Windows as a shortcut used to open another file, folder, orapplication) containing a PowerShell string:
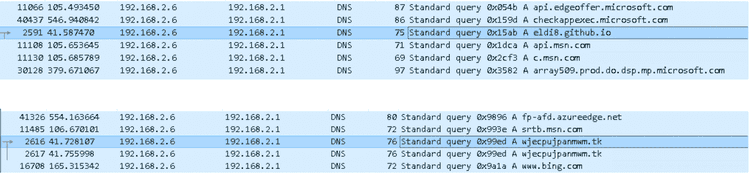
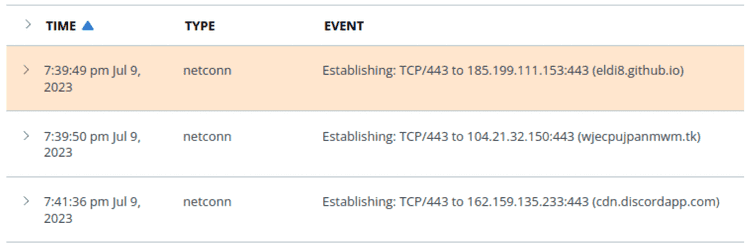
The PowerShell script, when launched, performs some network traffic, like some DNS queries and HTTP connections to some malicious urls reported below:
- eldi8.github.io
- wjecpujpanmwm.tk
- vimeo.com
- evinfeoptasw.dedyn.io
- cdn.discordapp.com
- bobsmith.apiworld.cf
- cdn.goodfilehosting.it
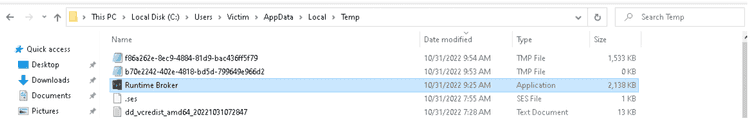
The resulting connections download and execute an executable called “Runtime Broker.exe” in the following path: C:\Users\Victim\AppData\Local\Temp
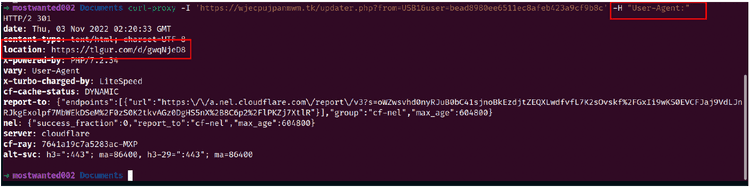
The download of the malware could be reproduced using curl, removing the User-Agent value:
2. Malware Analysis and Triage Report: RuntimeBroker.exe
2.1 Executive Summary
2.1.1 Fingerprinting
1_ MD5: 730f84805b3b815bf5f11b4ef0e60ee2
2_ SHA256: 8a492973b12f84f49c52216d8c29755597f0b92a02311286b1f75ef5c265c30d
3_ VirusTotal Report: https://www.virustotal.com/gui/file/8a492973b12f84f49c52216d8c29755597f0b92a02311286b1f75ef5c265c30d
2.1.2 Classification
The classification as of the report writing time is still under investigation. Our Threat Intel Platform identified the urls contacted as a C2 of “TheHive” ransomware group. The Virustotal platform still identifies the binary as a generic malware.
2.1.3 Behavioral Summary
The execution of the binary in a controlled sandbox results into an execution of a fake audio control center.
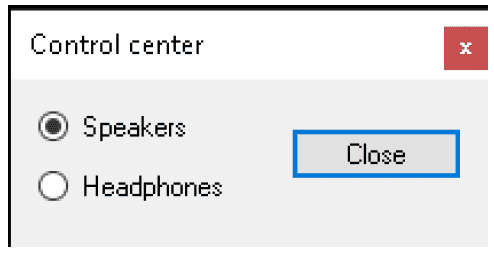
This behavior is generally related to some sandbox checks by the malware or some missing files that are needed by the malware itself to execute the malicious code. In this particular case our analysis suggests that some files are missing in order to see the real effects of the malware execution. Some more details are included in the static analysis chapter (chapter 2.2).
2.2 Static Analysis
Starting from the VirusTotal analysis, two very suspicious points were observed: the first one is that the Creation date is in the future, and the second one is that the binary is packed using .NET 4.0 framework.
These two techniques are commonly used to confuse the Antivirus (AV) static analysis and to bypass checks.
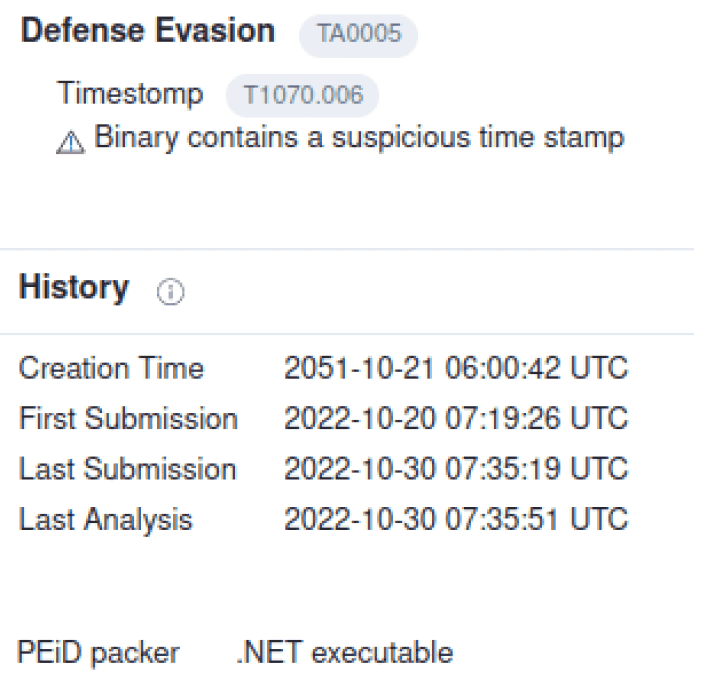
A packer is a tool often used to obfuscate the function names and references to avoid static analysis not only by AVs, but also by human malware analysts.
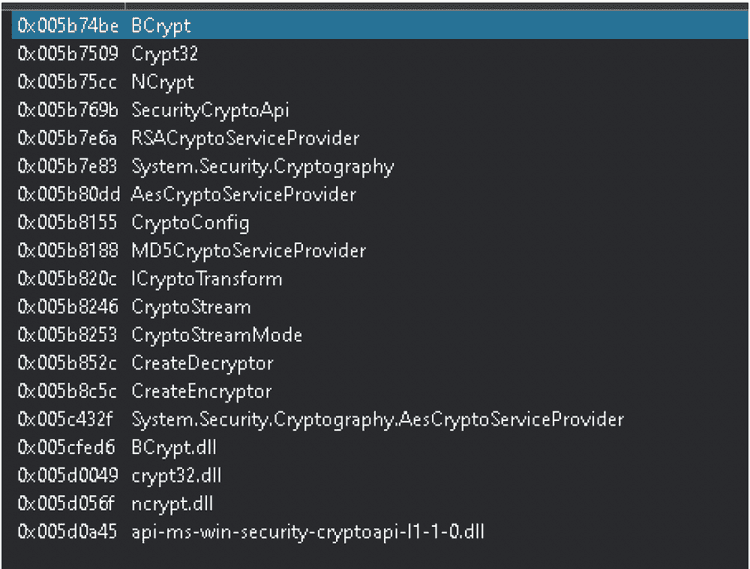
The strings contained in the binary could be related to ransomware behavior: there are some Windows API calls to cryptographic DLLs and also some calls to custom functions names, like CreateEncryptor and CreateDecryptor.
There are also references to custom functions related to encryption algorithms, like AES and RSA, and to one way hash functions like MD5.
The stream reference is another clue of the malicious behavior, because ransomware usually encrypts victims files byte-by-byte, increasing the efficiency of the encryption process.
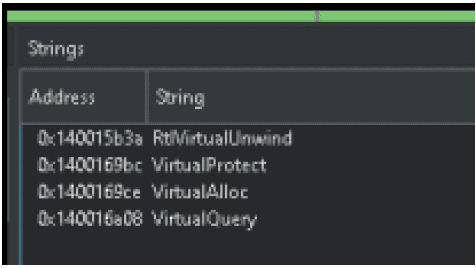
There are also some strings that refer to the Windows API calls used in common code injection techniques:
An interesting thing about the metadata of the packer is that they are in Italian language, which is pretty uncommon for these types of malware.
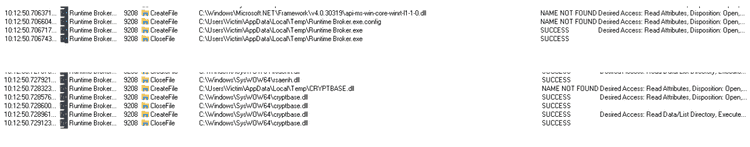
This is the list of files the binary modifies or looks for, it seems it is searching for a config file called “Runtime Broker.exe.config”.
It also loads some dll related to crypto functions or API calls.
Measuring the entropy of the binary is another way to find clues about the scope.
In this case the entropy is high and constant, that’s a confirmation of obfuscation and malicious behavior.
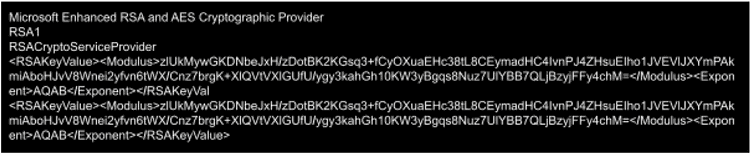
An analysis of the memory dump of the process detected some RSA strings related to a public key:
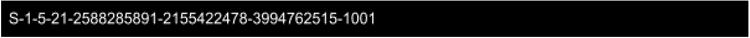
A SID was also found, which means that the binary looks also to the privileges with which it runs.
2.3 Dynamic Analysis
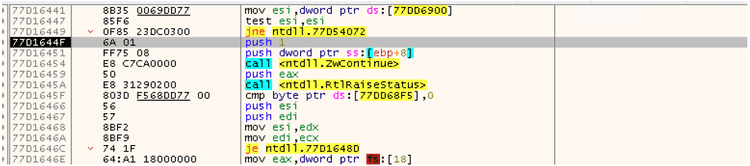
The execution of the binary in a debugger detected a code injection technique called “Heaven’s gate”.
This technique consists in a binary compiled for a 32-bit system that contains a 64-bit payload. The 64-bit payload is another binary that is injected and executed using the WOW64 environment. A migration from 32 to 64 bit, bypasses most of the AV engines that are not able to track this behavior. The injection itself is done creating a new thread of the victim process in suspended mode; when the payload injection is done, the thread is resumed using a specific API call and the payload is executed. In this case the API call is NTTestAlert.
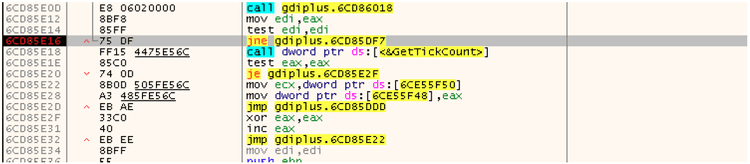
Several anti-debugging techniques were also found. The first one is based on a function called GetTickCount(): it counts the seconds between 2 points inside the binary execution and if the time is too high the program is running in a debugger and the original behavior is modified:
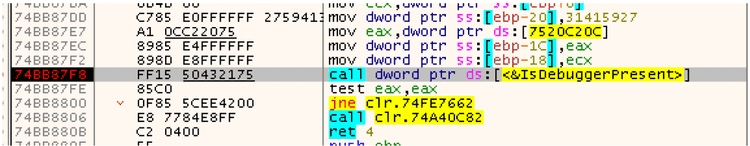
Another API call used in the binary is the IsDebuggerPresent(), a function used to know if the binary is running in a debugger environment. If true, the original behavior is modified:
3. IOCs - Indicator of Compromises
| IOC | Value |
|---|---|
| sha256 | 8a492973b12f84f49c52216d8c29755597f0b92a02311286b1f75ef5c265c30d |
| md5 | 730f84805b3b815bf5f11b4ef0e60ee2 |
| url | eldi8.github.io |
| url | wjecpujpanmwm.tk |
| url | vimeo.com |
| url | evinfeoptasw.dedyn.io |
| url | cdn.discordapp.com |
| url | bobsmith.apiworld.cf |
| url | cdn.goodfilehosting.it |
4. Variants
4.1 Variant v.3 (july 11th 2023)
We observed some variants during last year, here we attach the differences between the behavior described above and the new versions of the malware:
-
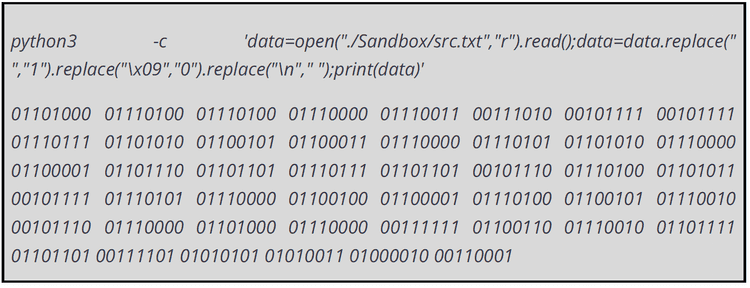
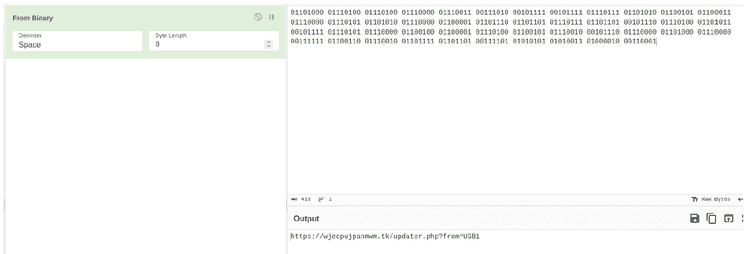
Powershell explorer.ps1 script loads and requests obfuscated binary data from eldi8.github.io/src.txt
-
It then, converts the spaces tabs to 1 and 0 and new-lines to
to get the .tk domain -
then the powershell script makes the request to .tk domain with from=USB&user=
-
In return, the .tk responds with Dropzone URL for Runtime Broker.exe which in this case is the Discord CDN
-
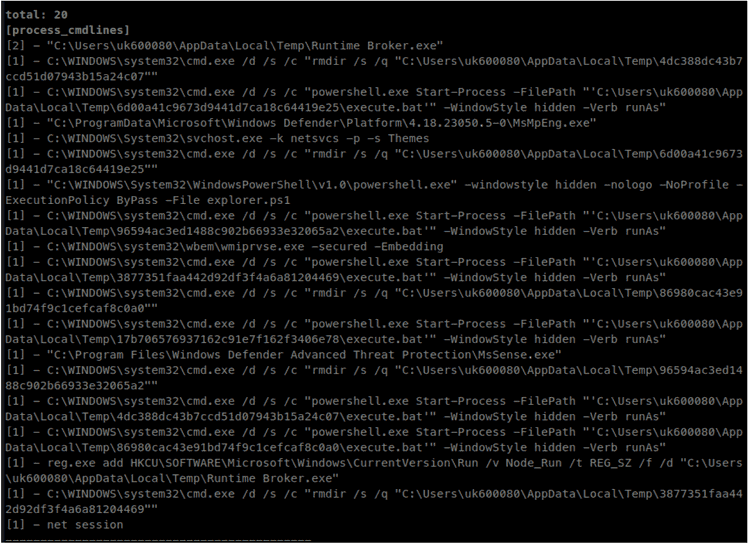
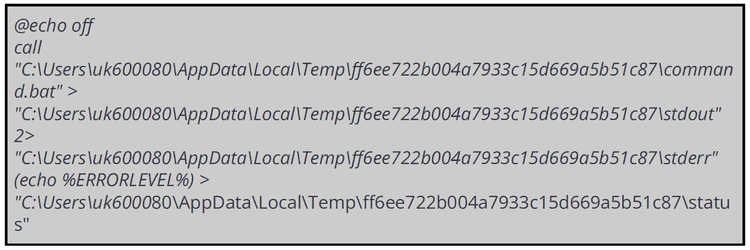
the Runtime Broker.exe create a random Temp folder and save inside command.bat and execute.bat
- execute execute.bat saved in the previous folder
- delete the random temp folder
- run net session
- create the persistence via reg.exe
The wjecpujpanmwm.tk domain is offline due to the expired DNS registration, so we probably will see a new version with new domains and features.
Here’s resumed, the changes from the previous version:
- Using Discord domain instead of Vimeo to download the Runtime Broker.exe
- The eldi8.github.io isn’t offline and is currently used to obfuscate the first stage
- Two scripts command.bat and execute.bat are currently created
The file index.js was not found during the analysis.
4.2 Variant v.4 (september 4th 2023)
Another variant of the RunTime Broker.exe malware emerged in the previous days.
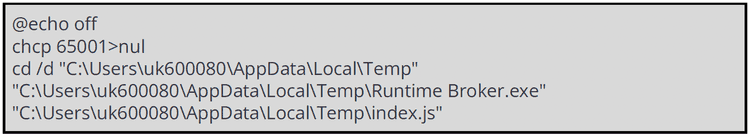
As the previous version, also the last one we have observed is using a batch file present in a directory with a random name in the AppData\Local\Temp parent folder. The batch file is named execute.bat.
Once the cmd.exe execute the batch file two processes are spawned:
- runtime brocker.exe
- chcp.com
The last process would change the Code page in the active console to a UTF-8 encoding (chcp 65001).
Then the process RunTime Broker.exe spawns a JS file named index.js (the file is located in the AppData\Local\Temp directory).
The JS file is a sort of config file used by the Runtime Broker to executes the following:
- C:\program files (x86)\winsoft update service\pythonw.exe "C:\Program Files (x86)\WinSoft Update Service\bootstrap.pyc"
- Netconns to luke.compeyson.eu.org and cdn.goodfilehosting.it (both malicious)
- Child: C:\Program Files (x86)\WinSoft Update Service\pythonw.exe -mpip install -U pytweening==1.0.7 pyscreeze==0.1.29 PyAutoGUI==0.9.54
psutil==5.8.0 playsound==1.2.2 WMI==1.5.1 mouse==0.7.1 keyboard==0.13.5 pyperclip==1.8.2 pycryptodome==3.15.0
- appdata\local\temp\py_installer.exe /VERYSILENT /SUPPRESSMSGBOXES/dir=expand:{pf}\pyt37
- programdata\adobe\creative cloud experience node\node.exe -e
"require(require('path').dirname(process.execPath) + '/node_modules/loader-module').inst()"
- appdata\local\temp\screendim_inst.exe /VERYSILENT /SUPPRESSMSGBOXES
- appdata\local\temp\museum_installer.exe /VERYSILENT
/SUPPRESSMSGBOXES /dir="expand:{pf}\WinSoft Update Service"
- appdata\local\temp\adob_cinst.exe /VERYSILENT /SUPPRESSMSGBOXES
The Runtime Broker.exe also spawns some Windows legit process, some used to get persistence on system, other to perform recognition:
-
c:\windows\syswow64\schtasks.exe /RUN /TN ScreenBrightnessRestore [to ensure persistence on the system, ndr]
-
c:\windows\syswow64\schtasks.exe /create /F /XML "C:\Program Files (x86)\ScreenDim\ScreenBrightnessRestore.xml" /TN ScreenBrightnessRestore [to ensure persistence on the system, ndr]
-
c:\windows\syswow64\net session
-
c:\windows\syswow64\reg.exe delete HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v Node_Run /f
We also detected the execution of "C:\Program Files (x86)\ScreenDim\ScreenDim.exe" restore with parent process C:\Windows\system32\svchost.exe -k netsvcs -p -s Schedule . ScreenDim.exe then spawns "C:\Program Files (x86)\pyt37\python.exe" -m updater. This last process then makes several netconns to the following malicious domains:
- paul.microvortexus.it
- cdn.goodfilehosting.it
After the connections Screendim.exe is uninstalled.