2024-3-27 18:44:33 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
TL;DR
- The NIST Cybersecurity Framework (CSF) offers a structured approach to organizations in need of assessing their cyber posture and cyber risk management practices.
- The framework comprises three main components: Functions, Implementation Tiers, and Business Profiles. The core functions include Identify, Protect, Detect, Respond, Recover, and, per the newly released NIST 2.0, Govern.
- The Implementation Tiers, of which there are four, give CISOs the language to express the maturity regarding the practices they’ve implemented for each of the core functions.
- The Business Profiles serve as a means for organizations to align their desired implementation levels according to specific characteristics.
- A major con of the NIST CSF is that the outcomes are ambiguous, i.e., non-technical business leaders don’t understand how achieving Tier 3 tangibly affects the business and bolsters growth.
- By enhancing NIST maturity levels with cyber risk quantification (CRQ), the results are transformed into actionable figures that can be used for high-level decision-making.
- CRQ platforms like Kovrr’s can demonstrate the financial impact of a security control upgrade, helping CISOs prioritize mitigation initiatives according to broader business objectives and communicate progress to the board in a language they understand.
What Is the NIST Cybersecurity Framework
Cybersecurity maturity assessments play a fundamental role in helping chief information security officers (CISOs) determine the level of risk their organizations face due to cyber activity. By illuminating the various areas that are exposed to exploitation, these evaluations serve as a blueprint for cybersecurity leaders tasked with making the business secure amid an increasingly risky operational landscape.
Recognizing the market’s pressing need for a structured approach to cyber risk management more than a decade ago, the National Institute of Standards and Technology (NIST) established its Cybersecurity Framework (CSF), providing organizations with a standardized approach to track their cybersecurity posture based on high-level outcomes.
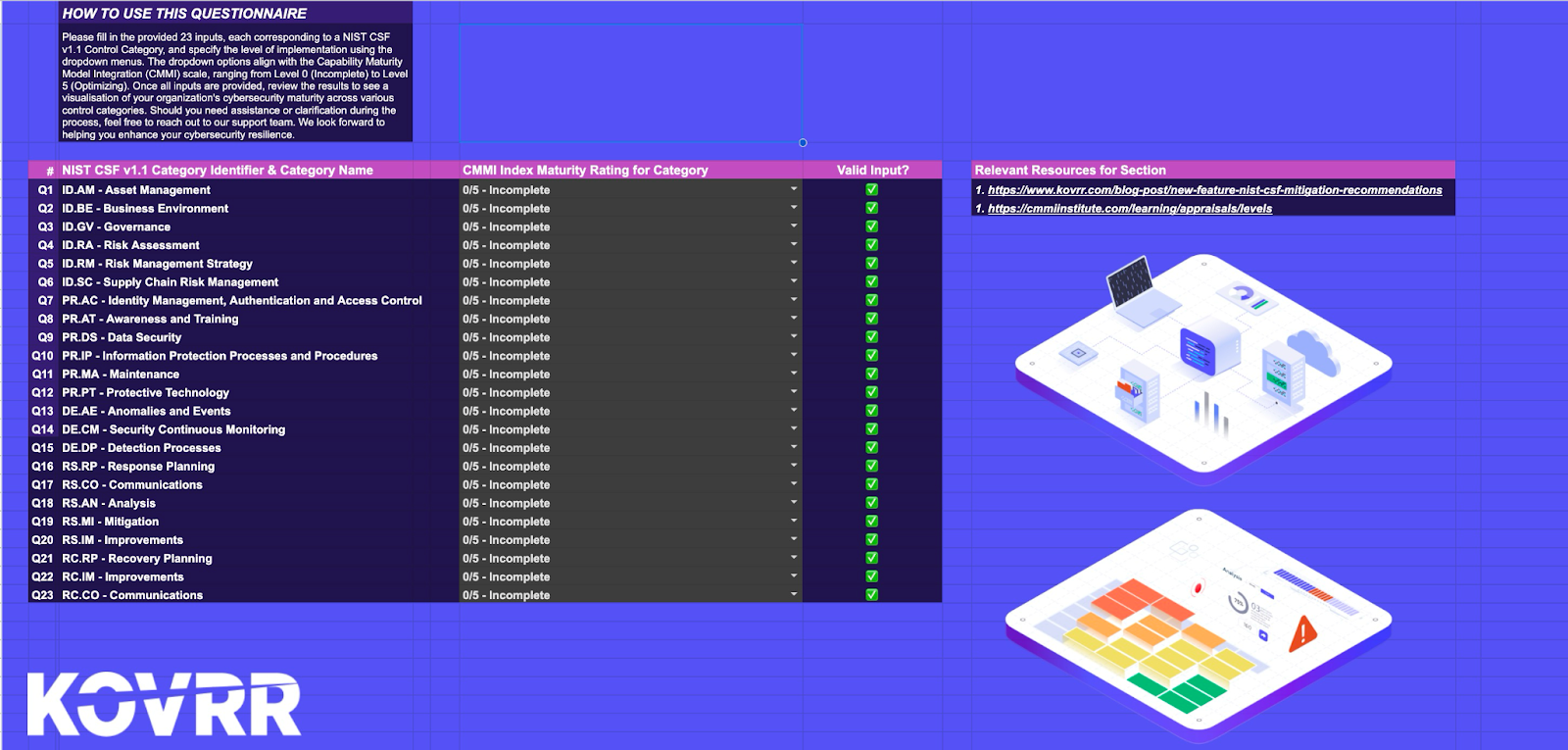
Download Kovrr’s free NIST assessment tool today to review your organization’s maturity in terms of the NIST framework.

Harnessing Quantification for Deeper NIST Insights
While NIST CSF is one of the most widely used cybersecurity frameworks by organizations across industries, it nevertheless falls short in providing CISOs and other cybersecurity leaders a deeper understanding of how their progress and upgrades concretely affect the organization’s cyber risk posture. For instance, even if a business elevates its maturity levels, it remains unclear how much less likely it is to experience a cyber attack.
This limitation of the NIST Cybersecurity Framework does not render it obsolete; rather, it merely demands that results be quantified. On top of transforming assessment results into objective results that can be used to prioritize risk mitigation initiatives, cyber risk quantification (CRQ) also translates NIST maturity into a broader business language, providing CISOs with a means of fostering high-level collaboration.
When combined, the NIST cyber assessment and CRQ offer organizations objective insights that guide strategic decision-making, ensuring cybersecurity programs focus on those security upgrades that produce the overall biggest effect on minimizing cyber risk.
How Is the NIST Cybersecurity Framework Structured?
The NIST CSF has three primary elements. First is the core, which is broken down into functions, followed by categories, and then subcategories. Second, are implementation tiers, created to describe the maturity of an organization’s program within each category. Third and last, there are business profiles that offer the ability to align unique objectives to the all-purpose framework.
The NIST CSF’s Core Functions
Within the original NIST framework (v.1.1), there were five core functions: Identify, Protect, Detect, Respond, and Recover. These functions, also referred to sometimes as pillars, are considered the spine of the core, upon which all of the other elements are situated. The initial five functions were selected by NIST experts because, when invested in, they demonstrate an organization’s “successful and holistic” cybersecurity risk management program.
In February 2024, NIST released an updated version of its cybersecurity framework, NIST 2.0., which, among other changes, added a sixth overarching function: Govern. This new pillar was added to better reflect the evolving cyber risk landscape and will be discussed more in-depth later in this blog.

Identify (ID)
“Identify” helps organizations to understand their unique cyber posture and, thus, their risk landscape. This process includes mapping system structures and information flows, discovering where the most valuable assets are located, and documenting relationships with third-party services. Only with this baseline knowledge can CISOs know which business areas require the most attention. Ultimately, you can’t manage the risk of what you haven’t identified.
The categories within the “Identify” function, as per NIST 2.0, include:
- Asset Management
- Risk Assessment
- Improvement
Protect (PR)
The “Protect” function serves as a means for organizations to assess various safeguards that can protect the system. Under this pillar, cybersecurity teams can demonstrate progress by, among other activities, managing access permissions, conducting employee training sessions, adopting various vulnerability management services, and maintaining the most up-to-date software. This pillar’s underlying aim is to proactively limit and contain potential attacks.
The categories within the “Protect” function, as per NIST 2.0, include:
- Identity Management, Authentication, and Access Control
- Awareness and Training
- Data Security
- Platform Security
- Technology Infrastructure Resilience
Detect (DE)
The third pillar, “Detect,” measures how quickly companies can discover unauthorized activity. “Detect” prescribes that CISOs monitor networks and develop procedures for detecting potential events. It also involves collecting log information and searching for patterns that can optimize this process. The “Detect” function is also a part of the NIST framework to help organizations determine potential impacts of and provide additional information regarding a threat.
The categories within the “Detect” function, as per NIST 2.0, include:
- Continuous Monitoring
- Adverse Event Analysis
Respond (RS)
In today’s cyber risk landscape, an attack is a matter of when rather than if. Within NIST CSF 2.0, “Respond” is an evaluation of the actions taken after a cybersecurity incident has been detected and the organization’s ability to contain it. This pillar requires CISOs to document incident response plans according to the expected severity of the event and ensure everyone knows their subsequent responsibilities.
The categories within the Respond function, as per NIST 2.0, include:
- Incident Management
- Incident Analysis
- Incident Response Reporting and Communication
- Incident Mitigation
Recover
Once the cyber attack has been effectively contained and employees have executed their initial reactive duties, the “Recover” function assesses how efficiently and effectively the affected assets and operations were restored. The categories and subcategories of “Recover” are in place to support timely recovery. After an event, many organizations feel stuck, but the “Recover” pillar is there to help organizations rebound and regain operational momentum.
The categories within the “Recover” function, as per NIST 2.0, include:
- Incident Recovery Plan Execution
- Incident Recovery Communication
The NIST CSF’s Implementation Tiers

The NIST Implementation Tiers represent the level to which an organization’s cyber risk management and governance practices adhere to the six functions (more specifically outlined in the categories and subcategories). They are defined by how well such practices are documented, formalized, and embedded within the organizational structure.
- Tier 1 (Partial): At this level, organizations have an ad-hoc approach to the function. There is likely a limited investment in this particular pillar, and if there are any relevant initiatives, they lack a formalized or documented approach.
- Tier 2 (Risk Informed): At this level, there is at least some formalization to the risk management process and some documentation regarding how the organization approaches the various categories. Efforts are definitely more proactive than in Tier 1, and there is a baseline level of cybersecurity awareness.
- Tier 3 (Repeatable): Organizational practices at this level are systematic and repeatable. Cyber risk management practices regarding the function are continuously improved upon. The policies focus on proactive mitigation and are adaptable to the evolving risk landscape.
- Tier 4 (Adaptive): The highest tier indicates that cybersecurity and cyber risk management practices in the relevant core function are embedded within the company culture. Respective cybersecurity measures are specifically created to adapt to the dynamic landscape, allowing the organization to maintain a proactive risk mitigation mindset.
The NIST CSF’s Business Profiles
Business, or framework, profiles serve as a means for organizations to align their unique missions, objectives, and risk appetites with the proper implementation levels within each of the core functions. The profiles illuminate in which cyber risk mitigation areas, according to their specific profile, the cybersecurity team should invest in.
For example, a logistics business profile may have very different ideal outcomes than those of a transportation company. This final component of the NIST Cybersecurity Framework is there to help organizations contextualize their current cyber posture and have a better understanding of how to allocate limited resources.
The Significance of the NIST 2.0 and the Govern (GV) Function
Recognizing the need to update the framework to reflect the evolving cybersecurity and cyber risk landscape, NIST officially released the updated 2.0 version of the framework in late February 2024. The previous version, 1.1., had been published 6 six years. While the Institute made several tweaks throughout the documentation, the most significant change was the addition of a sixth core function: Govern.
Cyber risk governance encompasses how key business stakeholders incorporate cybersecurity matters into the overall mission and use relative insights to make informed, data-driven decisions that foster growth. Nowadays, amid the increasing cost of cyber events, the volatile economy, and the growing number of global cybersecurity regulations, it’s never been more apparent that robust cybersecurity programs depend on high-level executive engagement.”
The categories within the Govern function include:
- Organizational Context
- Risk Management Strategy
- Roles, Responsibilities, and Authorities
- Policy
- Oversight
- Cybersecurity Supply Chain Risk Management
The Pros and Cons of the NIST CSF
The Pros: NIST provides a structured, comprehensive approach to assessing an organization’s cyber risk. The core functions, categories, and subcategories provide solid guidance on the type of practices and areas a cybersecurity team should invest in to build a more robust cyber posture. The framework is also widely used across the US and Europe, so it’s relatively easy for other organizations to establish benchmarks according to their industry peers.
Discover where your organization’s NIST cybersecurity framework maturity stands today with Kovrr’s free NIST assessment tool.
The Cons: When it comes to strategic planning and determining which implementation tier upgrades to prioritize, the NIST framework offers very little insight, leaving questions like “By how much will this investment reduce the likelihood of my organization experiencing a cyber event?” unanswered.
Additionally, although written less technically than some other cybersecurity maturity frameworks, NIST outcomes are rather ambiguous and still leave C-suite and board members confused about their tangible implications on the business. This ambiguity also renders it difficult for them to determine the amount of resources necessary to ensure cyber risk aligns with overall risk appetite levels and can remain resilient in the wake of an attack.
Making Meaning Out of NIST Implementation Tiers With Cyber Risk Quantification
To truly capitalize on all of the information NIST CSF can offer, organizations have to transform subjective implementation levels into objective figures that can be used for higher-level strategic decision-making. By enhancing NIST outcomes using an on-demand cyber risk quantification platform, CISOs become equipped with actionable insights that can guide cost-effective risk mitigation initiative planning.

Moreover, the translation of NIST maturity levels into terms like event likelihoods and potential financial damages enables cybersecurity leaders to elevate these crucial discussions into the C-suite and boardroom, helping to ensure that cyber programs align with the broader business strategy.
The underlying purpose of the NIST assessment framework is to provide organizations with the details necessary for creating the most robust cyber programs that ensure high-end resilience. With cyber risk quantification, NIST can finally deliver.
To quantify your NIST cybersecurity framework implementation tiers and explore your organization’s relative cybersecurity maturity, check our free NIST assessment tool.
If you’d like access to the full range of insights our CRQ platform can provide regarding your organization’s threat landscape and potential financial consequences, schedule a free demo with one of Kovrr’s cyber risk management experts today.
如有侵权请联系:admin#unsafe.sh