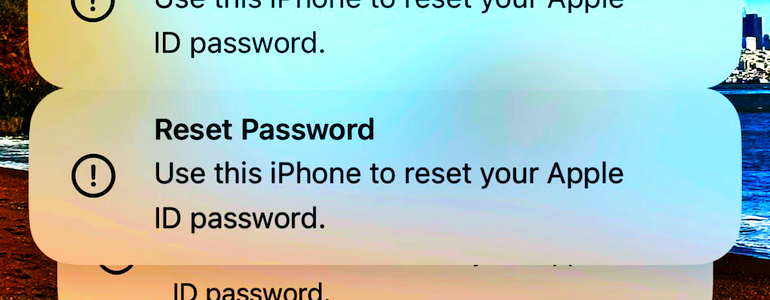
 First, fatigue frightened users with multiple modal nighttime notifications. Next, call and pretend to be Apple support.
First, fatigue frightened users with multiple modal nighttime notifications. Next, call and pretend to be Apple support.
Apple is under fire for not rate limiting its unskippable password-reset prompts. And for having iDevices go BLOOP in the wee small hours—even if on silent. Scrotes are exploiting the flaw, trying to steal your accounts.
The idea is to wear down your defenses, so when the phishers call you, you’re ready to fall for their con. In today’s SB Blogwatch, forewarned is forearmed.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: NESrecursion.
Rethink Different
What’s the craic? All aboard the Brian Krebs cycle—“‘MFA Bombing’ Attacks Targeting Apple Users”:
“Apple has not yet responded”
Several Apple customers recently reported being targeted in elaborate phishing attacks that involve what appears to be a bug in Apple’s password reset feature. … Devices are forced to display dozens of system-level prompts that prevent the devices from being used until the recipient responds “Allow” or “Don’t Allow” to each.
…
Scammers will then call the victim … saying the user’s account is under attack and that Apple support needs to “verify” a one-time code. … The goal of the voice phishers is to trigger an Apple ID reset code to be sent. … If the user supplies that one-time code, the attackers can then reset the password … and lock the user out.
…
What sanely designed authentication system would send dozens of requests for a password change in the span of a few moments, when the first requests haven’t even been acted on by the user? … Apple has not yet responded to requests for comment.
MFA bombing again? Why is this news? Usama Jawad explains—“Apple customers are being targeted”:
“Flaws in Apple’s authentication”
This attack is slightly more sophisticated than a typical MFA Bombing attack. If the victim keeps rejecting password reset requests, the attacker calls the victim. … They spoof Apple’s actual support line and also share details about the victim’s personal data in an attempt to convince the victim that they are legitimate.
…
This attack also highlights the flaws in Apple’s authentication system, which apparently has no rate limits. [Apple] doesn’t send outbound calls to customers unless they are explicitly requested so be wary.
How can I protect myself against aggressive MFA-bomb phishing attacks? Asma Hussain counts the ways—“How to protect your device against phishing attacks”:
“Adopt proactive measures”
Stay cautious. … If a user mistakenly clicks “Allow,” the attacker gains control. … Hackers capitalize on users’ exhaustion or confusion. … Users must adopt proactive measures to safeguard their Apple accounts against phishing attacks:
- Question unexpected password change requests or phone calls, especially if they request … OTPs. …
- Contact Apple directly through official channels rather than responding to unsolicited calls. …
- 2FA adds an extra layer of security, requiring both a password and a secondary verification method.
Sensible advice. But fortran77 cuts to the chase:
Wow! You’d think they’d rate limit these. Once you’ve done it twice, go to once every 15 minutes, then hour, then 4 hours, than day, etc. — like bad logins.
Perhaps the code is only limiting a single origin? It could be a distributed denial of service attack, thinks dgatwood:
The problem is that any jack*** … can hit Apple’s servers and issue a password reset request, and all your machines will get a password reset confirmation. And if that jack*** happens to have a few thousand/million compromised bots in a botnet that can all issue password reset requests against the same account, one every few seconds, the resulting DDoS attack can potentially prevent its victims from using their devices.
“It just works.” hambone isn’t impressed:
It’s just too easy to trick people into handing over their digital keys to the thief at the door. … This stuff is getting really hard for older people and kids to recognize.
…
And it’s just crazy that consumers are dumped on to be their own IT security department. I’m sending spam/scan notices to family members on practically a weekly basis.
It gets worse. Technoguide emits a silent scream:
This has happened to me over the last 6 months at least two dozen times. What’s worse, those push notifications come through even in Do Not Disturb or Sleep Focus, and pings all devices in a home at once (often late at night).
…
The spammers are getting really good. Stay vigilant!
The solution? Stop buying iThings! Here’s Lee D’s rant:
Everyone tells me that Apple products/software are so expensive and different because of the superior “design,” but I have yet to find a single design feature in any Apple device, hardware or software, that I actually even like, let alone prefer. Some of their design is ****ing atrocious.
…
[The] setup dialog … used to let you set up an iTunes account on a new iPad without entering a credit card number. At first it was literally a click, then they got increasingly obfuscated and would only allow you to select the option the first time on that iPad and not ever again. And then it became a running battle of stupendous workarounds where you had to cancel the “Sign in with iTunes” dialog some 50+ times to get into the iPad, change the setting to a particular account that had been set up with no credit card, and then you were able to sort things out. But to get there: System-modal dialogs every few seconds, that take an age to clear and then you had to quickly progress a tiny amount to get into the settings dialogs in between more system-modal dialogs, etc.
…
After setting up 200 iPads that way, I banned iPad purchases from the site and they’ve not added one in 10 years.
What should you do if you get a call? Heed Arul’s advice:
At the end of the day, the success of this attack depends on you handing over the reset code to the caller on the phone, assuming you survive the “MFA bombing” attack. Just hang up the call, though it appears to be a number from Apple: Caller ID spoofing is easy.
Meanwhile, paul_h sounds slightly sarcastic:
If … the hackers called you [and] you responded, “I understand you’re a hacker and are wanting to steal from me in some way, but I am only going to give you incorrect PIN numbers. So please stop with the reset dialogs and update your database not to try it again,” … would they stop?
And Finally:
Hat tip: ****socks
You have been reading SB Blogwatch by Richi Jennings. Richi curates the best bloggy bits, finest forums, and weirdest websites … so you don’t have to. Hate mail may be directed to @RiCHi, @richij or [email protected]. Ask your doctor before reading. Your mileage may vary. Past performance is no guarantee of future results. Do not stare into laser with remaining eye. E&OE. 30.
Image sauce: Parth Patel
Recent Articles By Author
Richi Jennings 2fa, 2FA bypass, 2FA Flaws, 2FA phishing, 2FA solution, 2FA/MFA, Apple, apple bug, Apple Data Security, apple hack, apple hacker, Apple iCloud, Apple ID, Apple ID failure, Apple iOS, Apple iPad, Apple iPhone, bypass 2FA, MFA, MFA Bombing, mfa fatigue, MFA hacks, mfa protection, mfasecurity, Multi-Factor Authentication (MFA), OTP, OTP circumvention bot, OTP interception bot, phishing-resistant MFA, push otp, SB Blogwatch, TOTP, two-factor-authentication.2fa
