2024-3-29 16:12:28 Author: securityboulevard.com(查看原文) 阅读量:13 收藏
NSFOCUS CERT has detected that details and a proof-of-concept (PoC) tool for a Linux kernel privilege escalation vulnerability CVE-2024-1086, have been publicly disclosed recently.
Due to a use-after-free vulnerability in the netfilter: nf_tables component of the Linux kernel, the nft_verdict_init() function allows the use of positive values as a drop error in the hook verdict. When NF_DROP issues a drop error similar to NF_ACCEPT, the nf_hook_slow() function could lead to a double-free vulnerability. Local attackers could exploit this flaw to elevate privileges from a regular user to root. As a PoC has been made public, affected users are urged to take protective measures promptly.
Netfilter is a framework provided by the Linux kernel that allows the implementation of various network-related operations in the form of custom handlers. Netfilter offers various functionalities and operations for packet filtering, network address translation, and port translation, which provide the necessary features to guide packets through the network and prevent them from reaching sensitive areas within the network.
Affected Scope
Affected Versions: 3.15 <= Linux kernel <= 6.8-rc1
Note: Known distributions such as Redhat, Ubuntu, Debian, etc., are affected.
Unaffected Versions: Linux kernel >= 6.8-rc2
Vulnerability Detection
Version Detection
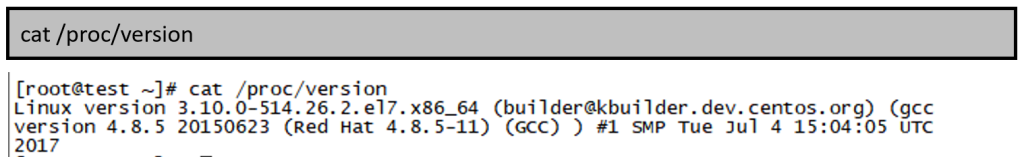
Linux system users can determine if their current system is within the affected range by checking the version. The command to view the operating system version information is as follows:
Mitigation Methods
The kernel version has been upgraded officially to fix this vulnerability. Affected users are advised to update their versions as soon as possible for protection. Download link: https://kernel.org/.
- Redhat: https://access.redhat.com/security/cve/CVE-2024-1086
- Ubuntu: https://ubuntu.com/security/CVE-2024-1086
- Debian: https://security-tracker.debian.org/tracker/CVE-2022-0847
For Redhat, the following temporary protective measures can be taken:
If not required by the business service, mitigate by preventing the loading of the affected netfilter (nf_tables) kernel module. For instructions on how to blacklist a kernel module, please refer to https://access.redhat.com/solutions/41278.
If disabling the module is not feasible, restrict user namespaces in non-containerized deployments of Red Hat Enterprise Linux.
Statement
This advisory is only used to describe a potential risk. NSFOCUS does not provide any commitment or promise on this advisory. NSFOCUS and the author will not bear any liability for any direct and/or indirect consequences and losses caused by transmitting and/or using this advisory. NSFOCUS reserves all the rights to modify and interpret this advisory. Please include this statement paragraph when reproducing or transferring this advisory. Do not modify this advisory, add/delete any information to/from it, or use this advisory for commercial purposes without permission from NSFOCUS.
About NSFOCUS
NSFOCUS, a pioneering leader in cybersecurity, is dedicated to safeguarding telecommunications, Internet service providers, hosting providers, and enterprises from sophisticated cyberattacks.
Founded in 2000, NSFOCUS operates globally with over 4000 employees at two headquarters in Beijing, China, and Santa Clara, CA, USA, and over 50 offices worldwide. It has a proven track record of protecting over 25% of the Fortune Global 500 companies, including four of the five largest banks and six of the world’s top ten telecommunications companies.
Leveraging technical prowess and innovation, NSFOCUS delivers a comprehensive suite of security solutions, including the Intelligent Security Operations Platform (ISOP) for modern SOC, DDoS Protection, Continuous Threat Exposure Management (CTEM) Service and Web Application and API Protection (WAAP). All the solutions and services are augmented by the Security Large Language Model (SecLLM), ML, patented algorithms and other cutting-edge research achievements developed by NSFOCUS.
The post Linux Kernel Privilege Escalation Vulnerability (CVE-2024-1086) Alert appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/linux-kernel-privilege-escalation-vulnerability-cve-2024-1086-alert/
如有侵权请联系:admin#unsafe.sh
