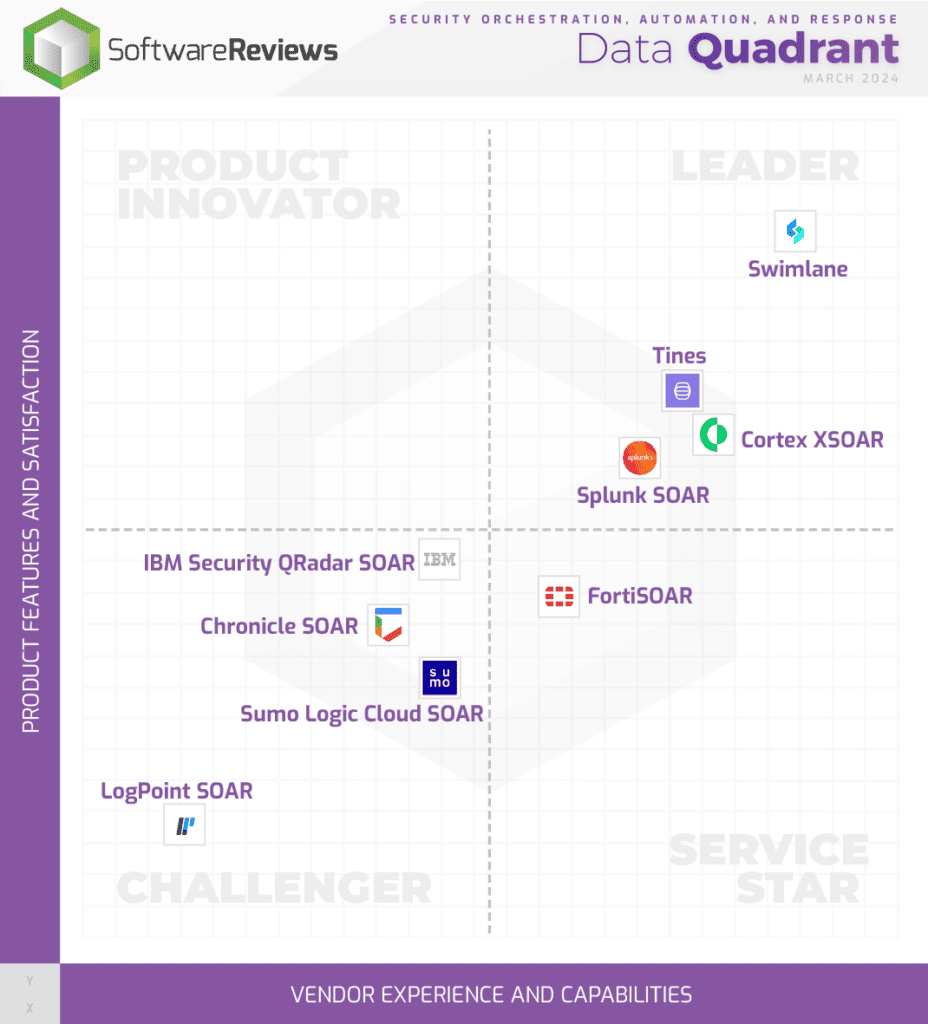
2024-4-4 22:0:0 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
As organizations continue to face increasingly sophisticated cyber threats, the need for a well-equipped and proactive Security Operations Center (SOC) cannot be overstated. Fortunately, SOC vendors offer a wide range of solutions that can help organizations create a robust security infrastructure, from threat intelligence and incident response to network monitoring and vulnerability management.
Whether you’re looking to build a modern SOC from scratch or simply looking to enhance your existing security infrastructure, we’re going to explain why we here at Swimlane should be your next SOC vendor. Let’s get into it.
Eight Reasons to Choose Swimlane as Your SOC Vendor
1. Our Low-Code Approach is the Sweet Spot
With our low-code security automation platform, you can strike a balance between power and ease of use, automating complex processes and creating sophisticated applications without needing to write code from scratch. At the same time, Swimlane platforms are designed to be user-friendly and accessible to anyone, regardless of their technical background. This means that you can create custom solutions tailored to your organization’s specific needs without having to rely on expensive IT resources or outside developers. So, in short, our low-code approach empowers businesses and individuals to unlock their full potential and achieve their goals faster and more efficiently than ever before.
2. A Modern Approach to Security Automation
Swimlane’s low-code security automation approach is a modern solution that empowers security teams with an approachable way to implement automation in and beyond the SOC. It offers unmatched flexibility, autonomous integrations, adaptable playbooks, and actionable insights that revolutionize automation. With Swimlane, SecOps teams can easily automate repetitive and time-consuming tasks, which frees up their time to focus on more critical security issues. Additionally, automation with Swimlane allows security teams to analyze security metrics and respond to security incidents quickly and efficiently, reducing the risk of cyber attacks.
3. We’re Always Launching New Technologies
The next benefit of choosing us as your Security Operations Center vendor is our commitment to launching new technologies and staying at the forefront of the industry. For example, to keep up with the evolving landscape and push towards AI, we recently released two new capabilities:
- Turbine Canvas is the industry’s first and only ultra-simple automation builder. This innovative technology uses intuitive human-centric interfaces and modular, reusable components to redefine SecOps and make automation fast and simple.
- Hero AI (private LLM) is a collection of AI-enabled innovations that allow you to work faster and more effectively than ever before. You can quickly craft AI prompts and case summarization, generate complex Python in seconds and keep your data fully private and secure.
Our team at Swimlane are experts in their field, always on the lookout for the latest innovations and advancements, striving to stay ahead of the curve. These two technologies are just the beginning of what’s to come.
4. We Provide Non-Resource Intensive Solutions
Legacy SOAR solutions are often criticized for being complex and resource-intensive. Such full-code automation products require a dedicated team of developers to build integrations and customize playbooks to meet the specific needs of an organization’s SOC. This means that only the most mature SOC teams have the skills and resources necessary to handle legacy SOARs. Additionally, the high resource requirements of this legacy platform can put a significant strain on an organization’s IT infrastructure.
However, Swimlane’s low code security automation platform, Swimlane Turbine, is non-resource intensive. Built with SecOps in mind, Turbine is the world’s fastest and most scalable security automation platform that allows for unparalleled control and flexibility, integrates with anything and provides huge ROI and scalability.
5. No Vendor Lock-in
One of the major drawbacks associated with legacy SOAR solutions on the market is the issue of vendor lock-in. This can be particularly problematic as it limits the ability to automate beyond SOC use cases and may restrict innovation in automation due to the vendor’s competitive considerations. Many legacy SOAR tools have been consolidated into larger security companies’ technology stacks, limiting integrations and stifling the development of more effective automation solutions. Therefore, it’s essential to carefully consider the potential for vendor lock-in when evaluating SOAR solutions. But luckily, with Swimlane, there’s no vendor lock-in and you’re free to integrate and innovate as much as your organization requires.
6. Human-First Case Management and Reporting
No-code automation tools lack robust features like case management, dashboards and reporting, which are essential for effectively bringing human SOC analysts into the loop of automation. Swimlane knows that this human interaction is vital for applying business logic, extending security automation beyond the SOC, and improving the organization’s risk posture over time.
7. Access to Unlimited Use Cases
No-code automation restrains security teams to a limited number of use cases without the opportunity to have customized operations that fit your unique business needs. As companies grow, their needs for security automation evolve and extend to less common use cases inside and beyond the SOC. This is where Swimlane’s low-code approach shines.
With Swimlane as your SOC vendor, you have access to some of the most advanced use cases:
| Inside the SOC | Outside the SOC |
| Phishing Triage helps with the high volume of alerts, false positive alerts and the time-sensitive nature of one of the world’s most common types of threats. | Insider Threat: automates the detection of malicious behavior and ensures water-tight employee offboarding. |
| Incident Response: identify and address cyber threats before they cause more significant damage. | Secure Employee Offboarding: ensures credentials and data do not walk out the door with the individual. |
| SIEM Triage: assists with the overwhelming number of alerts from SIEM tools. | Fraud Prevention: unites SecOps and fraud teams to prevent the top security challenge financial organizations face. |
| Threat Hunting: proactively searches for cyber threats that are lurking undetected in the network. | Anti-Cheat Automation: prevents players in online gaming and betting companies from exploiting their platforms. |
| EDR Alert Triage deals with the thousands of endpoints generating alerts from EDR tools when manually researching and executing endpoint actions that are too slow. | Physical Security: prepares both individuals and businesses for potential outcomes of physical threats. |
8. Easy Implementation and Constant Support
Security teams are increasingly looking to integrate with tools that are typically siloed from a SecOps perspective, like cloud applications, IoT, and data center edge computing. Turbine’s Autonomous Integrations make it possible to connect to any API without the dependency on developer resources to build or maintain the integration. From conventional SOC tools like SIEM, EDR, XDR, and firewalls to HR systems, compliance software, and physical security cameras, if it has an API, Swimlane can integrate with it.
As organizations continue to face increasingly sophisticated cyber threats, the need for a well-equipped and proactive Security Operations Center (SOC) cannot be overstated. Fortunately, SOC vendors offer a wide range of solutions that can help organizations create a robust security infrastructure, from threat intelligence and incident response to network monitoring and vulnerability management.
Whether you’re looking to build a modern SOC from scratch or simply looking to enhance your existing security infrastructure, we’re going to explain why we here at Swimlane should be your next SOC vendor. Let’s get into it.
Our Customer’s Success
Don’t just take our word for it; hear it from our customers that trusted us as their SOC vendor:
Patrick Schraut, Senior Vice President of Cybersecurity NTT DATA
“The flexibility of the Swimlane platform makes it the ideal solution for both our company and our customers to harness the power of low-code security automation, allowing every team member to create response processes that align with unique business processes.”
Jonathan Kennedy, Chief Information Security Officer, INCOMM PAYMENTS
“What makes Swimlane different is the ability to customize exactly what you need to get out of a SOAR platform. You’re not limited to prebuilt toolsets and your engineers can really create what they need to based upon your specific attack surface for your organization.”
Matt Helling, Head of Cybersecurity Softcat
“With Swimlane, we didn’t have to try and fit our outcome into a preconceived box that had already been developed. Swimlane allowed us to build something that worked for us and how we operate.”
Vice President of Cybersecurity and Chief Information Security Officer, Tanajak Watanakij, RV CONNEX
“We saw the sincere support that Swimlane could give us from the first call we had with Swimlane. They even bring in the CTO or higher up management support team to make sure the platform is providing optimal value for our organization. I think this unyielding support from Swimlane and the product, which is extremely intuitive and meets all the requirements of our entire company, is the most important deciding factor of why I chose Swimlane over every other vendor.”
Vice President of Cybersecurity and Chief Information Security Officer, Tanajak Watanakij, RV CONNEX
Vendor Agnostic With No Extra Cost: “Swimlane isn’t vendor specific and has so many integrations available. If an integration is not available, we can always ask Swimlane support to build it for us without any cost!”
Choose Swimlane as Your SOC Vendor Today
Selecting the right SOC vendor is crucial for the security and success of your organization. And Swimlane stands out as a top choice for SOC vendors, offering comprehensive platforms that streamline incident response and automate routine security tasks. By choosing us, your organization will always be at the forefront of cybersecurity and have the tools and support you need to stay one step ahead of cyber threats.
So why wait? Choose Swimlane as your SOC vendor today and take the first step towards a more secure and resilient organization.
如有侵权请联系:admin#unsafe.sh