2024-4-17 02:8:47 Author: securityboulevard.com(查看原文) 阅读量:13 收藏
 Widespread spam targets carrier employees, as scrotes try harder to evade two-factor authentication.
Widespread spam targets carrier employees, as scrotes try harder to evade two-factor authentication.
It’s no secret that cellular carrier reps are subject to bribery. Here’s a great example. Yes, again with the SIM swapping—where a fraudster convinces a representative to move a target’s line to a new SIM because they “lost” their phone.
Someone seems to have stolen a contact list of T-Mobile employees and is texting them offers of bribes to execute SIM swaps. But T-Mobile denies it’s been hacked… again.
Here’s the soft underbelly of the insider threat model. In today’s SB Blogwatch, we balk at the three-Benjamin bribes.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: Andre again.
Not OK: SMS 2FA
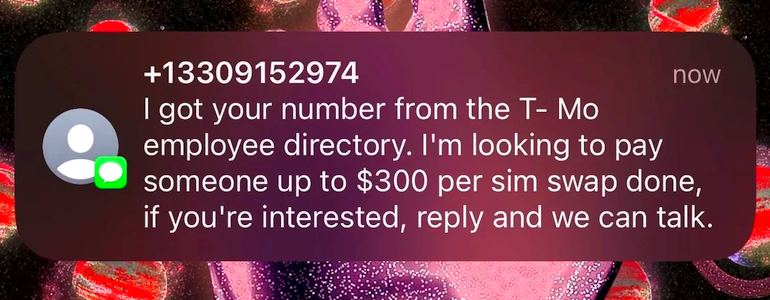
What’s the craic? Ryan McNeal reports, T-Mobile employees report being lured into scamming customers
“T-Mobile’s employee directory”
The news surrounding T-Mobile lately hasn’t exactly been great. Adding fuel to the fire, there’s now a new report that current and former employees are being offered money to perform SIM swaps on user’s phone lines. … It’s a technique bad actors use to gain access to someone’s phone line … by switching the SIM card registered for the line. [Then] that bad actor can intercept verification codes sent to the victim to gain access to accounts protected by two-factor authentication (2FA).
…
T-Mobile’s employee directory … may have leaked somewhere. [But] a T-Mobile spokesperson [said], “We did not have a systems breach. We continue to investigate these messages that are being sent to solicit illegal activity.”
How might McNeal know? The mysterious Jman100 broke the story: T-Mobile Employees Across The Country Receive Cash Offers To Illegally Swap SIMs
“Companies haven’t done enough”
According to multiple posts on Reddit, as well as separate individuals sending us tips, … employees from all over the country are receiving texts offering them … $300 per SIM swap. … This news isn’t exactly comforting to customers.
…
The fact that criminals still see SIM swapping as a viable way to make lots of money means companies haven’t done enough to help prevent them from happening. … If you use any services online that have two-factor authentication, be sure it is not SMS-based. Use an app like Google Authenticator or Authy for this purpose instead. … You should also enable SIM protection on your T-Mobile account.
Reddit posts, you say? Here are a few, from u/LowkyRep, u/rodolfoperezzz, u/kilgor3, u/chaos_recorded, u/RequirementThick1990, u/Ok-Primary5105, u/Enok_Reinli, u/ebkbk and u/2Adude:
Former TMO employee here. … Feeling curious about how they even have my number. …
Just got a message too. And as well, I’m a former employee. …
My coworker got a text too. He’s been with TMO … close to a decade. …
They hit dealer operations people as well. We’ll be able to weed out the bad apples pretty quick. I just read someone went to jail for 8 years for sim swapping. …
Myself and a group of former employees all got the same message—all from different numbers and with different verbiage. …
It’s scary how they got our numbers. …
I was hoping I wasn’t the only one. …
A bunch of [Corporate] employees are getting it too. …
Verizon employees getting this too.
Okay, upgrade your 2FA to avoid SMS: Check. Unfortunately, as TimJRobinson discovered, many services still need SMS as a fallback:
The other big problem … is you can have your account taken over even if you use non-SMS 2FA! If you have your phone number on your account it can be used for recovery, completely bypassing 2FA. [Twitter has] had this security flaw for years and still haven’t fixed it.
Wait! What‽ Why? Ed Tice explains:
Almost every authentication system around has a way to let you replace your second factor and those tend to be a big security hole. But … there’s not much that can be done.
…
I’ve had it happen when I moved to a new device and thought I had updated all 2FA but found out there was some authentication that I had forgotten about and have had to jump through hoops that were a PITA for me but wouldn’t have stopped an adversary.
Exactly this. And u/Pepparkakan takes the nuclear option:
This is why any service that offers account recovery or MFA via SMS has negated the security benefits gained. If it’s possible I always disable phone-based MFA/recovery.
…
Any service that either forces you to add SMS-based MFA, or simply requires a valid phone number for other reasons, I will immediately assume that the service will hand over access to my account to anyone who possesses my phone number. I’ll then try to avoid making that service essential to me in any way.
But what about this scam spam targeting employees? Perhaps there’s a prevention angle, wonders avidiax:
Couldn’t T-Mobile send their own SMSs to their employees pretending to increase the payout to $600? Then fire any employee that replies.
Interesting idea. SigIO takes it and runs with it:
If T-Mobile really cares to stop this, they will text phish their own employees and publicize the busts. Most of the disgruntled will find a better way to make a buck rather than risk getting caught.
Meanwhile, u/night_filter sees the funny side:
Comically, T-Mobile uses SMS for their own MFA.
And Finally:
You have been reading SB Blogwatch by Richi Jennings. Richi curates the best bloggy bits, finest forums, and weirdest websites—so you don’t have to. Hate mail may be directed to @RiCHi, @richij, @[email protected], @richi.bsky.social or [email protected]. Ask your doctor before reading. Your mileage may vary. Past performance is no guarantee of future results. Do not stare into laser with remaining eye. E&OE. 30.
Image sauce: u/LowkyRep
Recent Articles By Author
如有侵权请联系:admin#unsafe.sh