By Joey Chen, Chetan Raghuprasad and Alex Karkins.
- Cisco Talos discovered a new ongoing campaign since at least February 2024, operated by a threat actor distributing three famous infostealer malware, including Cryptbot, LummaC2 and Rhadamanthys.
- Talos also discovered a new PowerShell command-line argument embedded in the LNK file to bypass anti-virus products and download the final payload into the victims’ host.
- This campaign uses the Content Delivery Network (CDN) cache domain as a download server, hosting the malicious HTA file and payload.
- Talos assesses with moderate confidence that the threat actor CoralRaider operates the campaign. We observed several overlaps in tactics, techniques, and procedures (TTPs) of CoralRaider’s Rotbot campaign, including the initial attack vector of the Windows Shortcut file, intermediate PowerShell decryptor and payload download scripts, the FoDHelper technique used to bypass User Access Controls (UAC) of the victim machine.
The campaign affects victims across multiple countries, including the U.S., Nigeria, Pakistan, Ecuador, Germany, Egypt, the U.K., Poland, the Philippines, Norway, Japan, Syria and Turkey, based on our telemetry data and OSINT information. Our telemetry also disclosed that some affected users were from Japan’s computer service call center organizations and civil defense service organizations in Syria. The affected users were downloading files masquerading as movie files through the browser, indicating the possibility of a widespread attack on users across various business verticals and geographies.
We observe that this threat actor is using a Content Delivery Network (CDN) cache to store the malicious files on their network edge host in this campaign, avoiding request delay. The actor is using the CDN cache as a download server to deceive network defenders.
CDN edge URLs | Information Stealer |
hxxps[://]techsheck[.]b-cdn[.]net/Zen90 | Cryptbot |
hxxps[://]zexodown-2[.]b-cdn[.]net/Peta12 | Cryptbot |
hxxps[://]denv-2[.]b-cdn[.]net/FebL5 | Cryptbot, Rhadamanthys |
hxxps[://]download-main5[.]b-cdn[.]net/BSR_v7IDcc | Rhadamanthys |
hxxps[://]dashdisk-2[.]b-cdn[.]net/XFeb18 | Cryptbot |
hxxps[://]metrodown-3[.]b-cdn[.]net/MebL1 | Cryptbot |
hxxps[://]metrodown-2[.]b-cdn[.]net/MebL1 | Cryptbot, LummaC2 |
hxxps[://]metrodown-2[.]b-cdn[.]net/SAq2 | LummaC2 |
Talos discovered that the actor is using multiple C2 domains in the campaign. The DNS requests for the domains during our analysis period are shown in the graph, indicating the campaign is ongoing.
Talos assesses with moderate confidence that threat actor CoralRaider is likely operating this campaign based on several overlaps in the TTPs used and the targeted victims’ geography of this campaign with that of the CoralRaider’s Rotbot campaign. We spotted that the PowerShell scripts used in the attack chain of this campaign to decrypt the PowerShell scripts of further stages and the downloader PowerShell script are similar to those employed in the Rotbot’s campaign.
PowerShell decryptor script of Rotbot campaign (left) and new unknown campaign (right). | |
String decrypt and download routine of Rotbot campaign (Left) and new unknown campaign (right). | |
The Powershell script did not appear in any public repository or article, indicating the threat actor likely developed these PowerShell scripts. Pivoting on the PowerShell argument embedded in the LNK file showed us that such arguments are not popular and likely specific to the actor and the campaign.
.(gp -pa 'HKLM:\SOF*\Clas*\Applications\msh*e').('PSChildName') |
The infection chain starts when a victim opens the malicious shortcut file from a ZIP file downloaded using the drive-by download technique, according to our telemetry. The threat actor is likely delivering malicious links to victims through phishing emails.
The Windows shortcut file has an embedded PowerShell command running a malicious HTA file on attacker-controlled CDN domains. HTA file executes an embedded Javascript, which decodes and runs a PowerShell decrypter script. PowerShell decrypter script decrypts the embedded PowerShell Loader script and runs it in the victim’s memory. The PowerShell Loader executes multiple functions to evade the detections and bypass UAC, and finally, it downloads and runs one of the payloads, Cryptbot, LummaC2 or Rhadamanthys information stealer.
Windows Shortcut file to execute the malicious HTA file
Windows shortcut file runs a PowerShell command to download and run an HTML application file on the victim’s machine. The threat actor has used “gp,” a PowerShell command alias for Get-ItemProperty, to read the registry contents of the application classes registry key and gets the executable name “mshta.exe.” Using mshta.exe, the PowerShell instance executes the remotely hosted malicious HTA file on the victim’s machine.
Obfuscated HTA runs embedded PowerShell decrypter
The malicious HTML application file is heavily obfuscated and has a Javascript that decodes and executes a function using the String fromCharCode method. The decoded function then executes an embedded PowerShell decryptor script.
The decryptor PowerShell script has a block of AES-encrypted string. Using the AES decryptor function, it generates an AES key of 256 bytes from a base64 encoded string “RVRVd2h4RUJHUWNiTEZpbkN5SXhzUWRHeFN4V053THQ=” and the IV “AAAAAAAAAAAAAAAA.” With the key and IV, it decrypts and executes the next stage of the PowerShell Loader script.
PowerShell loader downloads and runs the payload
The PowerShell loader script is modular and has multiple functions to perform a sequence of activities on the victim’s machine. Initially, it executes a function that drops a batch script in the victim machine’s temporary folder and writes its contents, which includes the PowerShell command to add the folder “ProgramData” of the victim machine to the Windows Defender exclusion list.
The dropped bath script is executed through a living-off-the-land binary (LoLBin) “FoDHelper.exe” and a Programmatic Identifiers (ProgIDs) registry key to bypass the User Access Controls (UAC) in the victim’s machine. Fodhelper is a Windows feature, an on-demand helper binary that runs by default with high integrity. Usually, when the FodHelper is run, it checks for the presence of the registry keys listed below. If the registry keys have commands assigned, the FodHelper will execute them in an elevated context without prompting the user.
HKCU:\Software\Classes\ms-settings\shell\open\command
HKCU:\Software\Classes\ms-settings\shell\open\command\DelegateExecute
HKCU:\Software\Classes\ms-settings\shell\open\command\(default)
Windows Defender, by default, detects if there are attempts to write to the registry keysHKCU:\Software\Classes\ms-settings\shell\open\command and to evade this detection, the threat actor uses the programmatic identifier (ProgID). In Windows machines, a programmatic identifier (ProgID ) is a registry entry that can be associated with a Class ID (CLSID ), which is a globally unique serial number that identifies a COM (Component Object Model) class object. The Windows Shell uses a default ProgID registry key called CurVer, which is used to set the default version of a COM application.
In this campaign, the threat actor abuses the “CurVer” registry key feature by creating a custom ProgID “ServiceHostXGRT” registry key in the software classes registry and assigns the Windows shell to execute a command to run the batch script.
Registry Key | "HKCU\Software\Classes\ServiceHostXGRT\Shell\Open\command" |
Value | %temp%\r.bat |
The script configures the ProgID ServiceHostXGRT in the CurVer registry subkey of HKCU\Software\Classes\ms-settings\CurVer, which will get translated to HKCU:\Software\Classes\ms-settings\shell\open\command. After modifying the registry settings, the PowerShell script runs FoDHelper.exe, executing the command assigned to the registry key HKCU:\Software\Classes\ms-settings\shell\open\command and executing the dropped batch script. Finally, it deletes the configured registry keys to evade detection.
The batch script adds the folder “C:\ProgramData” to the Windows Defender exclusion list. The PowerShell loader script downloads the payload and saves it in the “C:\ProgramData” folder as “X1xDd.exe.”
After downloading the payload to the victim’s machine, the PowerShell loader executes another function that overwrites the previously dropped batch file with the new instructions to run the downloaded payload information stealer through the Windows start command. It again uses the same FoDHelper technique to run the batch script’s second version, which we explained earlier in this section.
Talos discovered that the threat actor delivered three famous information stealer malware as payloads in this campaign, including CryptBot, LummaC2 and Rhadamanthys. These information stealers target victims’ information, such as system and browser data, credentials, cryptocurrency wallets and financial information.
CryptBot
CryptBot is a typical infostealer targeting Windows systems discovered in the wild in 2019 by GDATA. It is designed to steal sensitive information from infected computers, such as credentials from browsers, cryptocurrency wallets, browser cookies and credit cards, and creates screenshots of the infected system.
Talos has discovered a new CryptBot variant distributed in the wild since January 2024. The goal of the new CryptBot is the same, with some new innovative functionalities. The new CryptBot is packed with different techniques to obstruct malware analysis. A few new CryptBot variants are packed with VMProtect V2.0.3-2.13; others also have VMProtect, but with unknown versions. The new CryptBot attempts to steal sensitive information from infected machines and modifies the configuration changes of the stolen applications. The list of targeted browsers, applications and cryptocurrency wallets by the new variant of CryptBot is shown below.
We observed the new CryptBot variant also includes password manager application databases and authenticator application information in its stealing list to steal the cryptocurrency wallets that have two-factor authentication enabled.
CryptBot is aware that the target applications in the victim’s environment will have different versions, and their database files will have different file extensions. It scans the victim’s machine for database files’ extensions of the targeted applications for harvesting credentials.
LummaC2
Talos discovered that the actor is delivering a new variant of LummaC2 malware as an alternative payload in this campaign. LummaC2 is a notorious information stealer that attempts to harvest information from victims’ machines. Based on the report posted by outpost24 and other external security reports, LummaC2 has already been confirmed to be sold on the underground market for years.
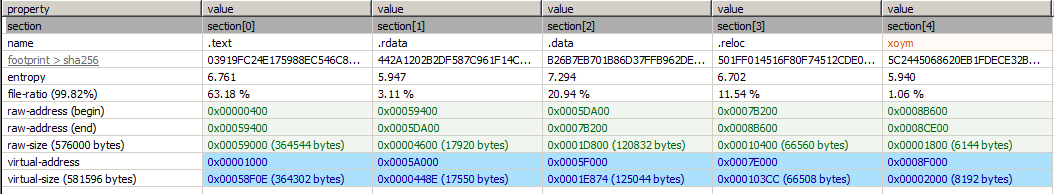
The threat actor has modified LummaC2’s information stealer capability and obfuscated the malware with a custom algorithm. The obfuscation algorithm is saved in another section inside the malware shown below.
The new version of LummaC2 also presents the same signature of the alert message displayed to the user during its execution.
The C2 domains are encrypted with a symmetric algorithm, and we found that the actor has nine C2 servers that the malware will attempt to connect to one by one. Analyzing various samples of the new LummaC2 variant, we spotted that each will use a different key to encrypt the C2.
Talos has compiled the list of nine C2 domains the new LummaC2 variant attempts to connect in this campaign.
Encrypted strings | Decrypted Strings |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphB+VXagKwrRr7BjLA71GNEZ8E8/0K2otQ== | peasanthovecapspll[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphBpVXqwOAHAo75nPQT3Hc4I6EZ+x+u0rVjB | gemcreedarticulateod[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphB9VXShLxDMqLFmPATgC8Ma+U14zKy0oBnC/kf0 | secretionsuitcasenioise[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphBtXHa6JwfKqbxwOh79B8wb+UF0jbavqkc= | claimconcessionrebe[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphBiWXaxIwjMs6Z0Ox/1BsUM8UZ/2qyz60TZ+Vg= | liabilityarrangemenyit[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphBjX3O2ORDAtKx0MAjiDcwE9U9mxq7ptl/e5g== | modestessayevenmilwek[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphB6Qn6yJAPJoqxwKB77BsAM8kB51K/ptl/e5g== | triangleseasonbenchwj[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphBtRXunPxbAtLRwPQ78DssH/U1yyqSrqRnC/kf0 | culturesketchfinanciall[.]shop |
DjAX00pkpcffFUltlGiiaZwjEaPFx8U3sZYohNNzphB9X3GyIhHLs7Z7Lh74AcYM+Ep/xuu0rVjB | sofahuntingslidedine[.]shop |
LummaC2’s first step in its exfiltration phase is its connection to the C2 server. The malware will exit the process if it does not receive the “OK” message as a response from any of the nine C2 servers. The second step will be exfiltrating information from infected machines. The basic stealing functionality is the same as the previous version, with the addition of victims’ discord credentials to exfiltrate.
Rhadamanthys
The last payload we found in this campaign is Rhadamanthys malware, a famous infostealer appearing in the underground forum advertisement in September 2022. The Rhadamanthys malware has been evolving till now, and its authors have released a new version, V0.6.0, on Feb. 15, 2024. However, the Rhadamanthys variant we found in this campaign is still v0.5.0.
The threat actor uses a Python executable file as a loader to execute the Rhadamanthys malware into memory. After decompiling the Python executable file, Python scripts load the Rhadamanthys malware in two stages. The first stage is a simple Python script that replaces the binary code from 0 to 9 and decodes the second stage.
In the second stage, the Python script uses the Windows API to allocate a memory block and inject Rhadamanthys malware into the process. We spotted that the threat actor is developing the Python script with the intention of including the functionality of executing a shellcode.
Analyzing the final executable file showed us that the malware unpacks the loader module with the custom format having the magic header “XS” and performs the process injection. The custom loader module in XS format is similar to that of a Rhadamanthys sample analyzed by the researcher at Check Point. The malware selects one of the listed processes as the target process for process injection from a hardcoded list in the binary:
- "%Systemroot%\\system32\\dialer.exe"
- "%Systemroot%\\system32\\openwith.exe"
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SID for this threat is 63218 - 63225 and 300867 - 300870.
ClamAV detections are also available for this threat:
Lnk.Downloader.CoralRaider-10027128-0
Txt.Tool.CoralRaider-10027140-0
Html.Downloader.CoralRaider-10027220-0
Win.Infostealer.Lumma-10027222-0
Win.Infostealer.Rhadamanthys-10027293-0
Win.Infostealer.Rhadamanthys-10027294-0
Win.Infostealer.Cryptbot-10027295-0
Win.Infostealer.Cryptbot-10027296-0
Win.Infostealer.Cryptbot-10027297-0
Win.Infostealer.Cryptbot-10027298-0
Win.Infostealer.Cryptbot-10027299-0
Win.Infostealer.Cryptbot-10027300-0
Win.Infostealer.Cryptbot-10027301-0
Win.Infostealer.Cryptbot-10027302-0
Win.Infostealer.Cryptbot-10027303-0
Win.Infostealer.Cryptbot-10027305-0
Indicators of Compromise associated with this threat can be found here.