
2024-4-24 00:56:43 Author: www.tenable.com(查看原文) 阅读量:12 收藏


A zero-day vulnerability in CrushFTP was exploited in the wild against multiple U.S. entities prior to fixed versions becoming available as the vendor recommends customers upgrade as soon as possible.
Background
On April 19, CrushFTP published an advisory for a zero-day vulnerability in its file transfer tool which bears the same name.
| CVE | Description | CVSSv3 | Severity |
|---|---|---|---|
| CVE-2024-4040 | CrushFTP VFS Sandbox Escape Vulnerability | 7.7 | High |
No CVE identifier was initially assigned for this vulnerability. However, on April 22, h4sh, a security engineer and founder of DirectCyber, an Australian Cyber Security Incident Response Team (CSIRT), assigned a CVE for this flaw.
Analysis
CVE-2024-4040 is an improper input validation vulnerability in CrushFTP. An authenticated attacker with low privileges could exploit this vulnerability on a vulnerable CrushFTP server to escape the virtual file system (VFS) sandbox. Successful exploitation would allow an attacker to download system files.
Zero-day exploitation of VFS sandbox escape flaw
According to researchers at CrowdStrike, CVE-2024-4040 has been exploited in the wild as a zero-day. Specifically, its report notes that these attacks are targeted in nature and that intrusions have been discovered at “multiple U.S. entities” with a focus on “intelligence-gathering” that is “possibly politically motivated.” No further details about attribution of these targeted attacks are available as of April 23.
Attackers are probing for vulnerable CrushFTP servers
In a statement to The Record, an official from CrushFTP says that they have seen “a customer who was already patched who was probed for the vulnerability” adding that if the patch had not been applied “important config info would have been stolen.” This official stressed that customers “need to update ASAP.”
Over 7,100 CrushFTP servers publicly accessible and potentially vulnerable
Based on a shodan query in a Nuclei template created by h4sh to identify potentially vulnerable CrushFTP servers, there are reportedly over 7,100 CrushFTP servers publicly accessible. It is unclear how many of these systems are potentially vulnerable.
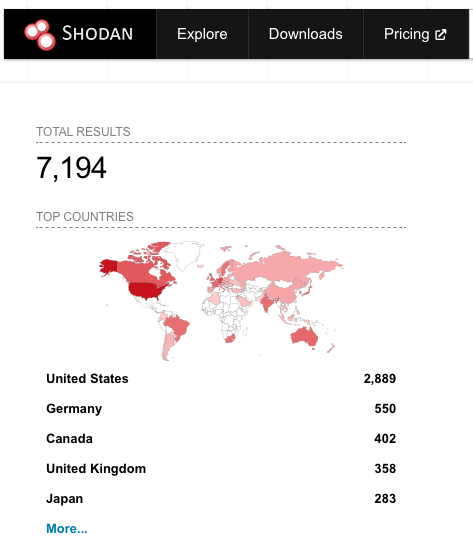
Shodan query results as of April 22 for publicly accessible CrushFTP servers
Proof of concept
On April 23, a public proof-of-concept (PoC) for this vulnerability was posted to GitHub. It was created by Simon Garrelou of Airbus Community Emergency Response Team (CERT), who is credited with discovering and reporting CVE-2024-4040 to CrushFTP.
Additionally, it is important to highlight that it is common practice for attackers to seed fake PoCs on public source code repositories like GitHub in an effort to target both researchers and would-be attackers looking for exploit code. In the case of CVE-2024-4040, we’ve seen a repository published to GitHub directing users to a third-party site called SatoshiDisk that requests a payment of 0.00735 Bitcoin ($513.30 USD as of April 22).
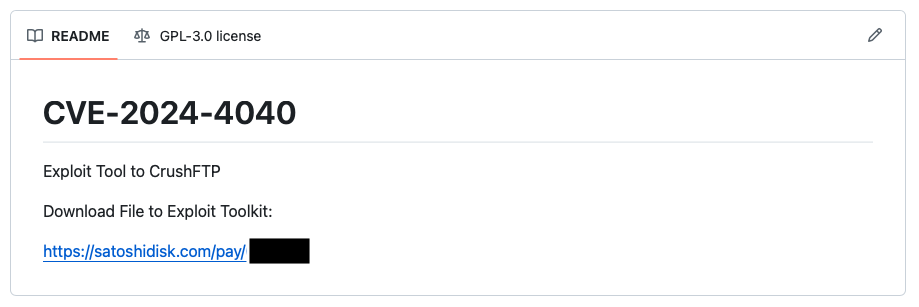
Example repository on GitHub seeking Bitcoin payment for a fake exploit for CVE-2024-4040
It is unlikely that the exploit code will work and we do not expect it to be malicious in nature. Instead, it is more likely that the attackers are seeking to make money from the interest in the exploit code for this vulnerability.
Solution
On April 23, CrushFTP released fixes for version 10 and version 11 of CrushFTP:
| Affected Versions | Fixed Version |
|---|---|
| 11.0.1 | 11.1.0 |
| 10.0.0 through 10.6.1 | 10.7.1 |
| Below 10.0.0 | Upgrade to 11.1.0 |
Previously, reports suggested that if CrushFTP was behind a demilitarized zone (DMZ) then users would be protected against this flaw. However, as of April 22, CrushFTP disputed this claim, noting that a DMZ “does not fully protect you.” Customers using a vulnerable version of CrushFTP are advised to update to a fixed version as soon as possible.
Garrelou also developed a script to scan CrushFTP logs to search for potential indicators of compromise.
Identifying affected systems
A list of Tenable plugins for this vulnerability can be found on the individual CVE page for CVE-2024-4040 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
Get more information
- CrushFTP Wiki Page for CrushFTP 11 (Advisory)
- SITUATIONAL AWARENESS // 2024-04-19 // CrushFTP Virtual Filesystem Escape Vulnerability in the Wild
- The Record News: CrushFTP urges customers to patch file transfer tool ‘ASAP’
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Satnam Narang
Satnam joined Tenable in 2018. He has over 15 years experience in the industry (M86 Security and Symantec). He contributed to the Anti-Phishing Working Group, helped develop a Social Networking Guide for the National Cyber Security Alliance, uncovered a huge spam botnet on Twitter and was the first to report on spam bots on Tinder. He's appeared on NBC Nightly News, Entertainment Tonight, Bloomberg West, and the Why Oh Why podcast.
Interests outside of work: Satnam writes poetry and makes hip-hop music. He enjoys live music, spending time with his three nieces, football and basketball, Bollywood movies and music and Grogu (Baby Yoda).
Related Articles
- Exposure Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh