
2024-4-25 13:32:4 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Understanding ITDR and ISPM
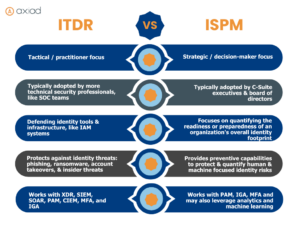
In the cybersecurity world, two emerging identity-centric categories promise to provide a fundamental shift in how identities are secured in modern networks. Those two categories are Identity Threat Detection and Response (ITDR) and Identity Security Posture Management (ISPM). Because these categories are relatively new, it can be hard to distinguish between the two. However, from our perspective, the difference between them comes down to “who drives” and the fundamental positioning of each product. At a high level, ITDR defends identity tools and infrastructure against attack, while ISPM provides preventive capabilities that aim to protect and quantify human- and machine-focused identity risks.
As Axiad helps its customers move toward an identity-first security outlook, it’s important to look at these two categories and where vendors fit in. But first, let’s further define both ITDR and ISPM.
What is ITDR?
According to the analyst community, ITDR narrowly focuses on threats to the identity management stack, including identity tools and infrastructure used by the enterprise. At the most basic level, ITDR can detect, respond, and then block cybersecurity identity threats, including phishing, ransomware, account takeovers, insider threats, and more. Specifically, ITDR can do this by a set of “contain and eradicate”, “recover”, and “remediate” features and functionality.
In fact, ITDR can add a second layer of security to identity and access management (IAM) systems by helping to verify, for example, administrator credentials, as well as by adding detection and response capabilities. It also works in conjunction with many cybersecurity tools, including extended detection and response (XDR), security information and event management (SIEM), security orchestration, automation, and response (SOAR), privileged access management (PAM) systems, cloud infrastructure entitlement management (CIEM), multi-factor authentication (MFA), identity governance and administration (IGA), and many others. And, in many cases, ITDR is incorporated into a zero-trust security model.
What is ISPM?
ISPM hasn’t been as formally defined, but, in general, we view it as an approach that focuses on quantifying the readiness or preparedness of an organization’s overall identity footprint, including identity protection and access security, within the IT environment. ISPM is about accessing overall security posture from a higher level in terms of user identities, access controls, authentication methods, security policies, and more – all to reduce cyber risk.
Key features of this approach include identity discovery and inventory, access control and authorization, and an assessment of IGA and MFA tools. It also works with PAM systems and identity governance for cloud environments. Additionally, ISPM may be able to use analytics and machine learning (ML) to detect anomalies and suspicious behavior to proactively identify and address potential threats.
The Difference Between ITDR and ISPM
The difference between ITDR and ISPM really depends on:
- Who you ask (which analyst or advisor)
- Who is driving the category development
- You and your organization’s unique perspective
If someone is looking at cybersecurity from an identity perspective and protecting infrastructure such as Microsoft or Okta implementations, for example, then they are going to gravitate toward ITDR. This person tends to be a technical security professional.
But, if someone is looking at cybersecurity more broadly in terms of identity risk across the organization and not just through the identity stack – including machine identities, bring your own device (BYOD), etc., as well as compliance and reporting – then they are likely going to lean more toward ISPM. This person is usually a senior executive with a “risk” orientation, like a chief information security officer (CISO). So, ITDR revolves more around threat detection and response and has a heavy focus on the security operations center (SOC) team, while ISPM looks at risk from a higher level in terms of preparedness and readiness from the perspective of the executive team.
However, as mentioned, it really depends on how people define these two segments, how they view them, and the specific identity needs and challenges they are looking at and hoping to solve. Many organizations are actively shifting to a more “risk-aware” posture on their various identity attack surfaces and looking to continually quantify that risk.
We’d love to hear the perspective of our readers that are championing these categories – how do you define each of them and what is your reasoning or approach to using one or the other?
What the Future Holds and Where Axiad Fits
In the analyst community, we already see that ISPM characteristics are sometimes being folded within ITDR, which indicates that ITDR will be the dominant and overarching category of the two. Within the next three years, we think that ITDR will be the predominant category and that ISPM and the preparedness/overall posture management aspects will be completely melded into ITDR as a distinct differentiator.
In our view, though, that doesn’t make ISPM any less important. At the end of the day, we believe identity has been overlooked for too long by the highest level of risk management at organizations, including positions like the CEO and the chief risk officer or CFO. This is one of the key areas in which ISPM is trying to drive risk awareness. It takes a higher-level approach to the overall security posture, which can be just as important as detecting existing threats.
So, if you’re a company seeking to solve the problem of “identity risk insight,” where do you start? ITDR or ISPM? You may want to do both. One gears to executives and risk, while the other focuses on security practitioners. It all starts with looking at your organization’s identity fabric: the various controls, permissions, and attack signals that interweave between every cybersecurity risk and every user experience. And, while identity fabric has turned into a bit of a marketing buzzword recently, from our point of view, it’s looking at evolving your IAM infrastructure to meet a set of specific characteristics and requirements.
In an upcoming blog post, we will discuss identity fabrics, how they work, and how your organization can move even closer toward an identity-first, zero trust future.
If you’d like to learn more about how Axiad can help with your identity journey, contact us today.
The post ITDR vs ISPM: Which Identity-first Product Should You Explore? appeared first on Axiad.
*** This is a Security Bloggers Network syndicated blog from Axiad Cybersecurity Blog authored by Axiad. Read the original post at: https://www.axiad.com/blog/itdr-vs-ispm-which-identity-first-product-should-you-explore/
如有侵权请联系:admin#unsafe.sh
