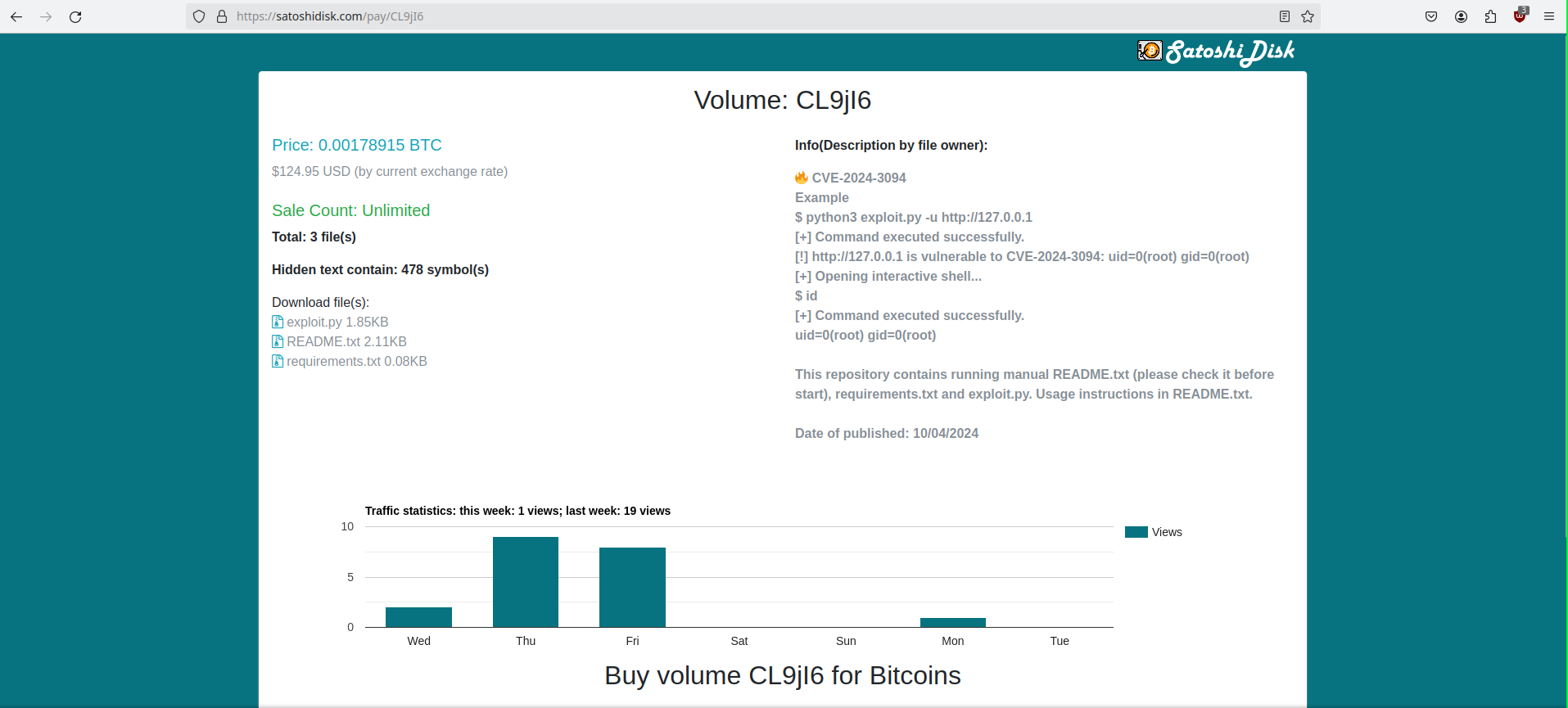
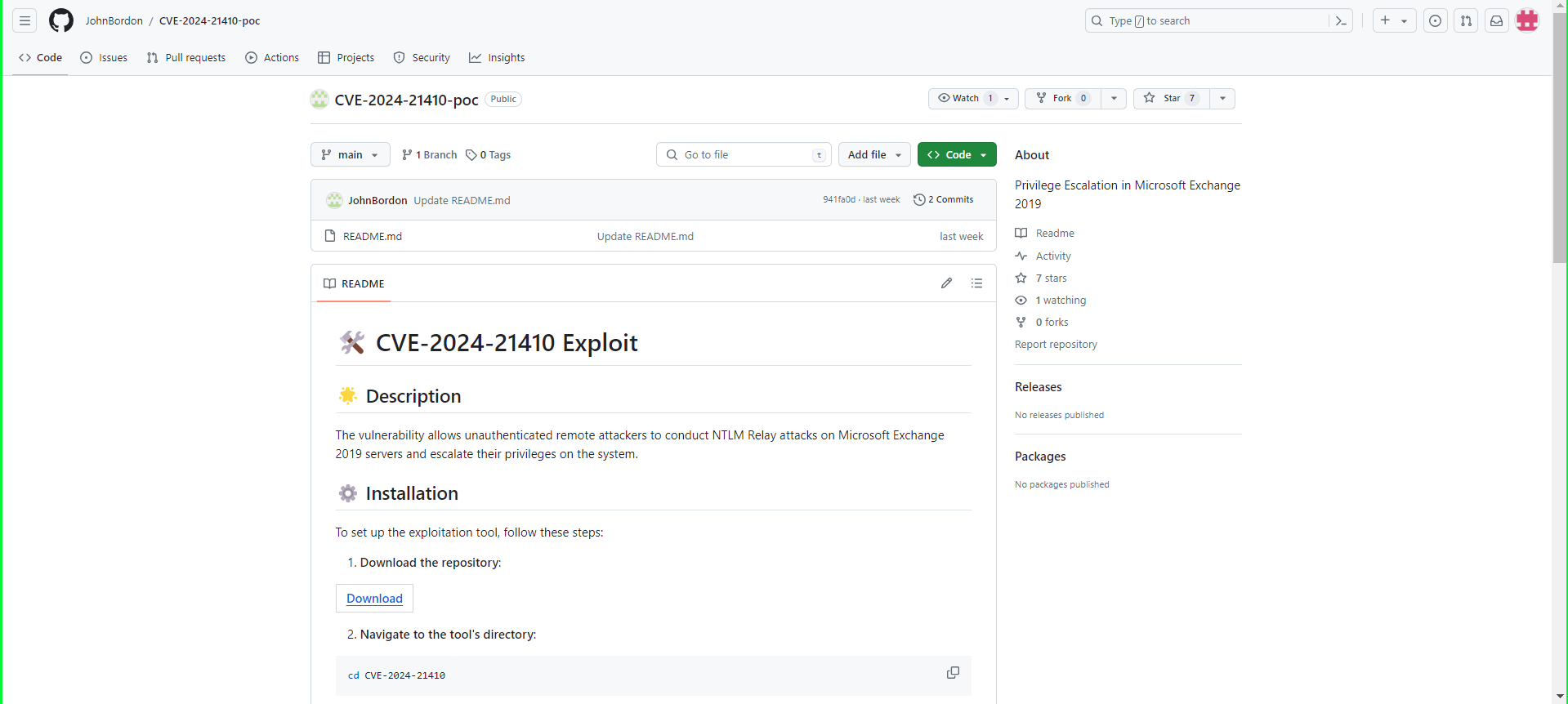
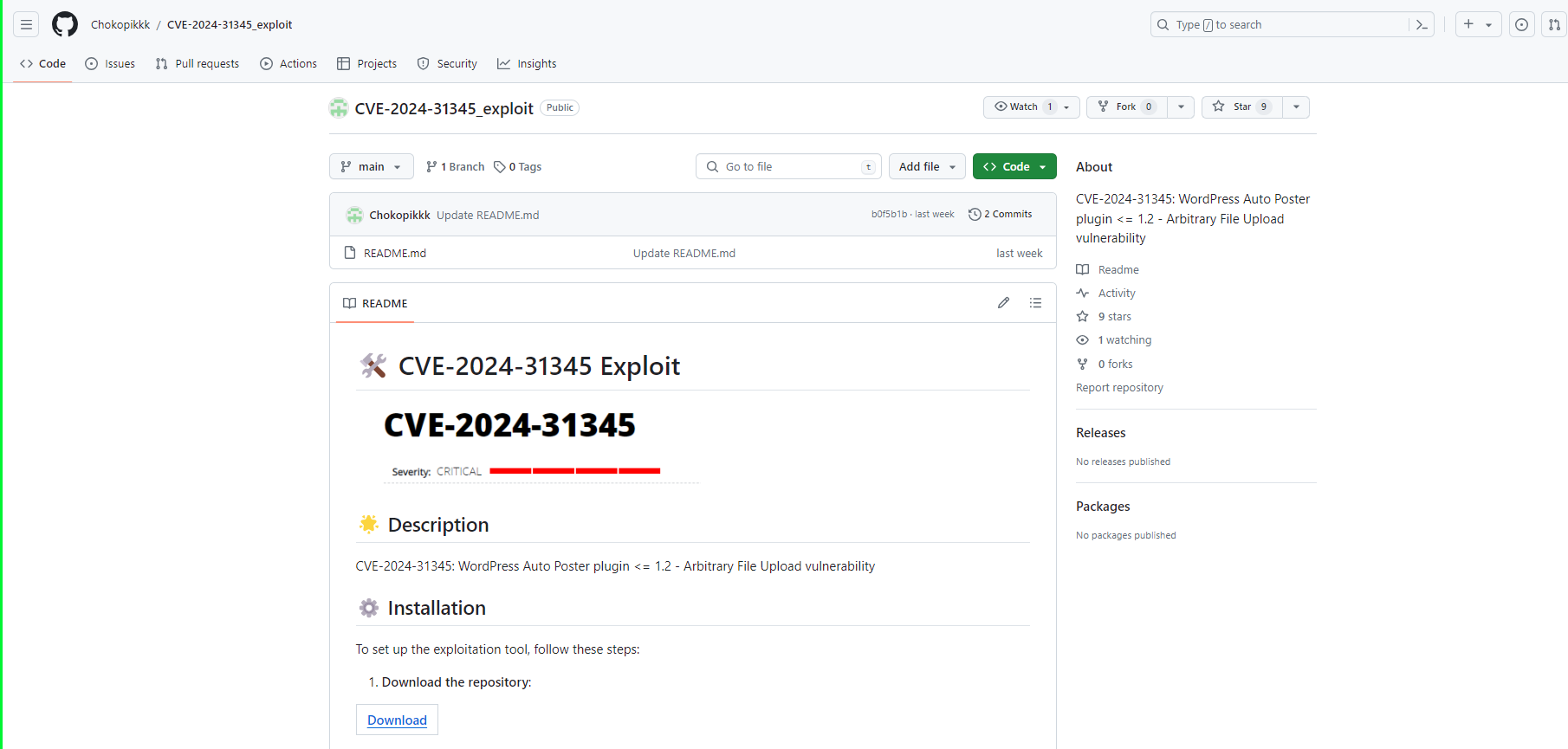
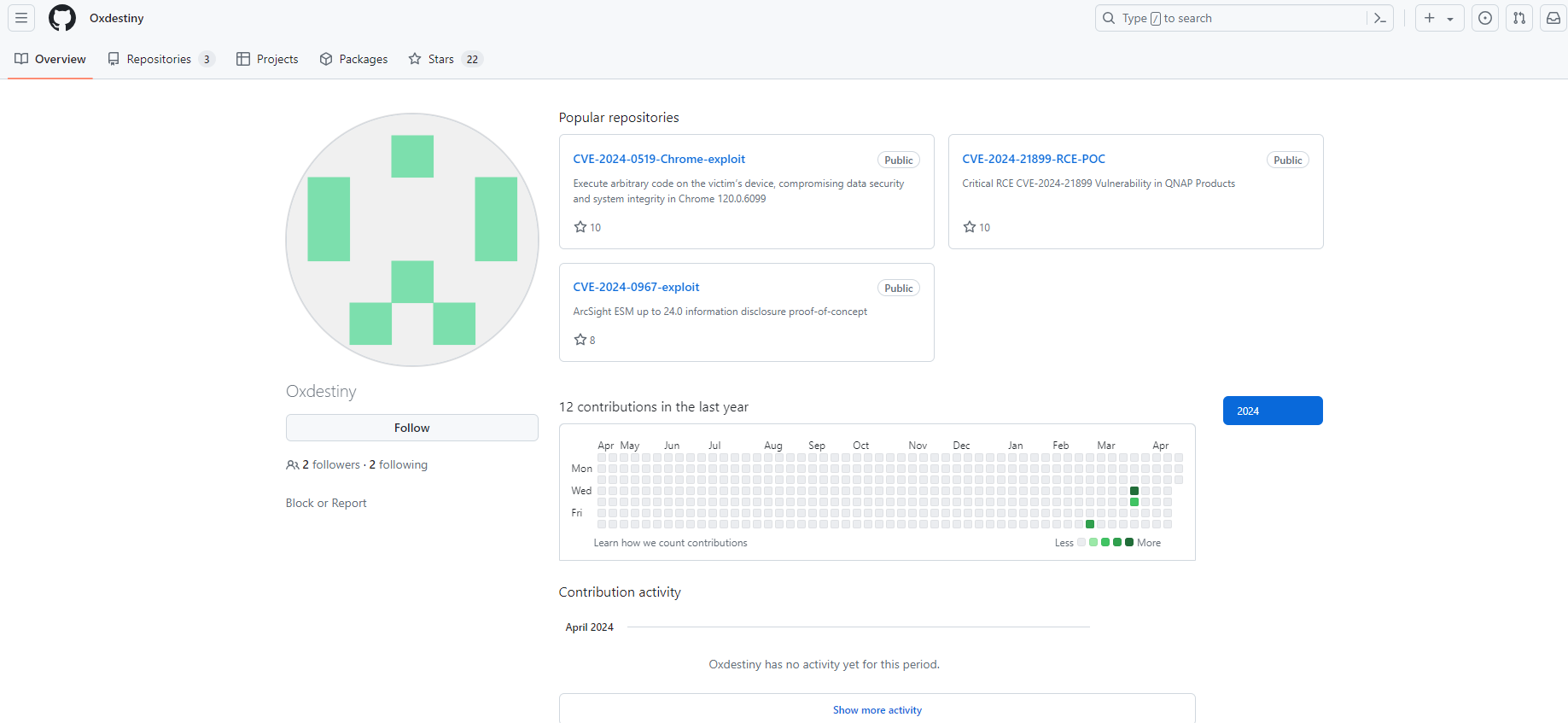
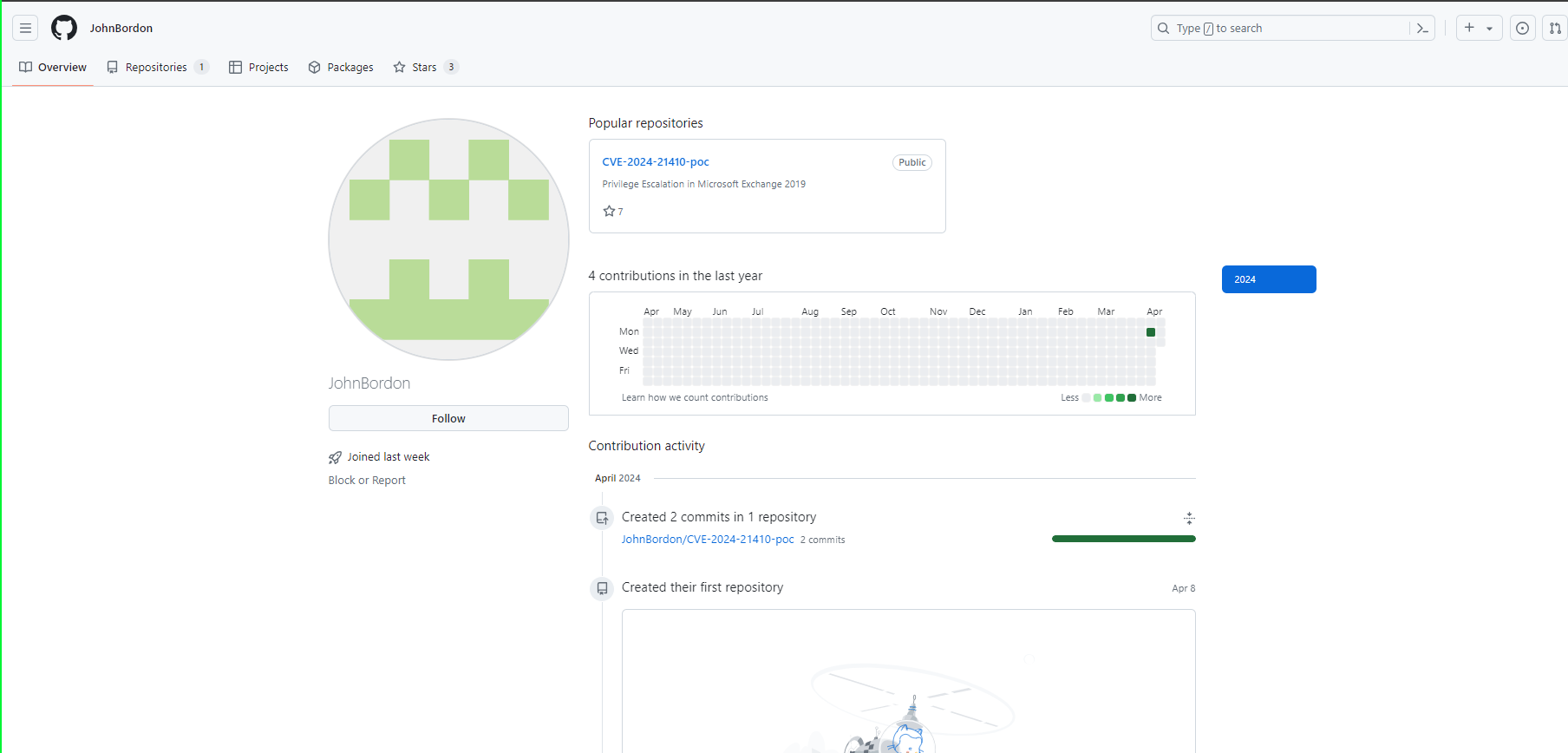
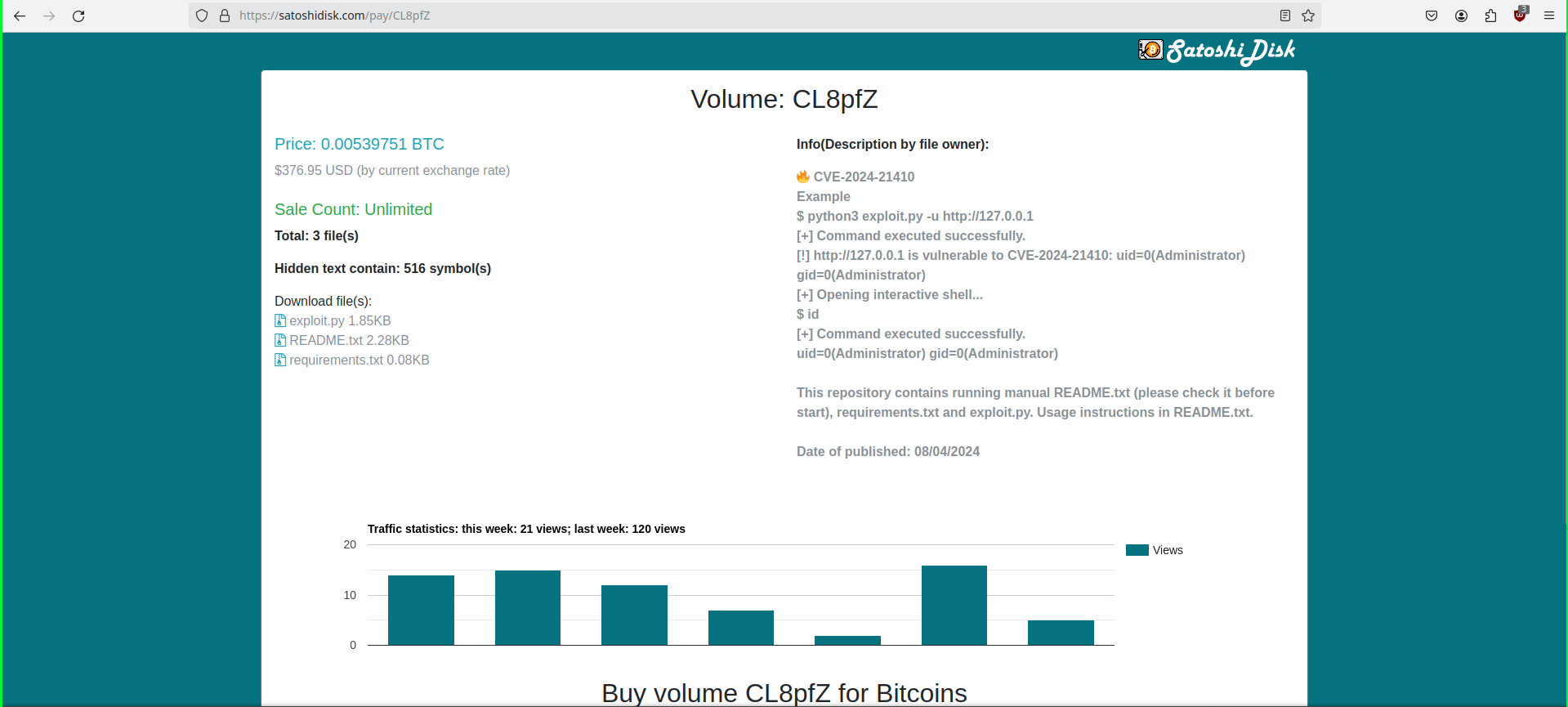
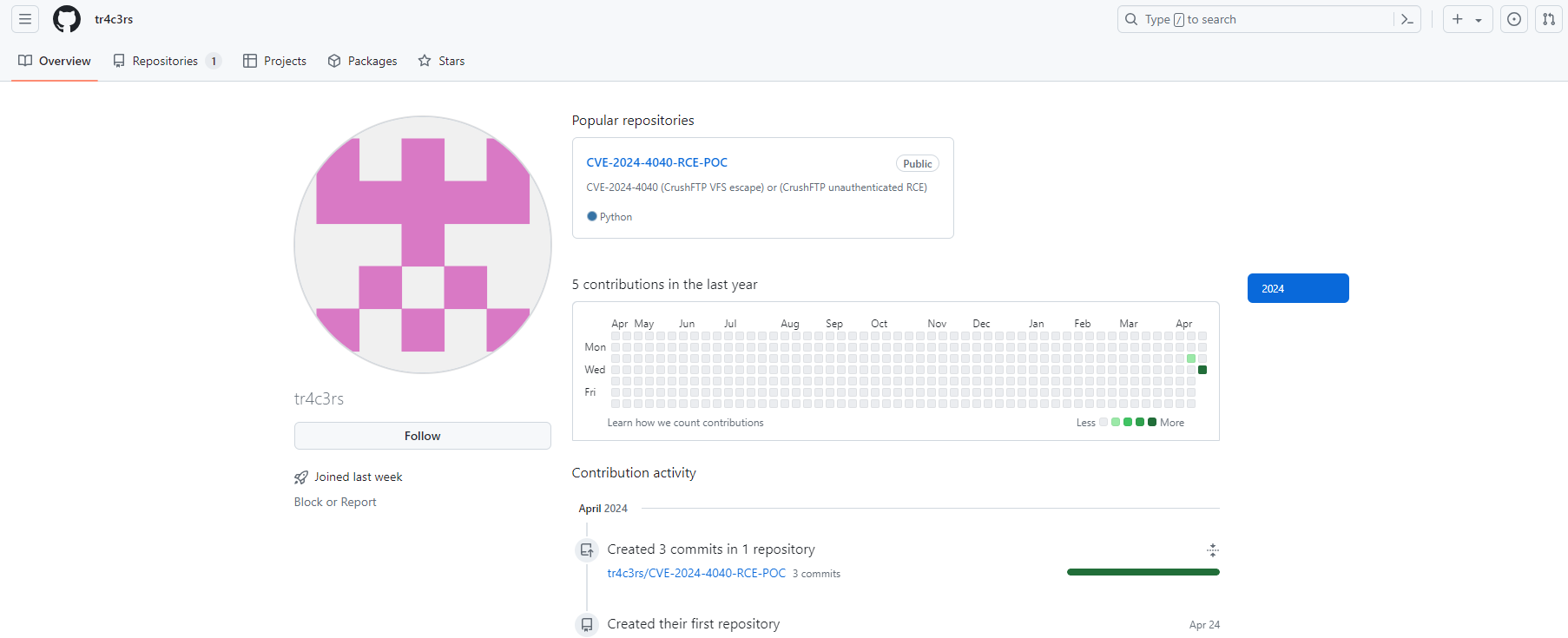
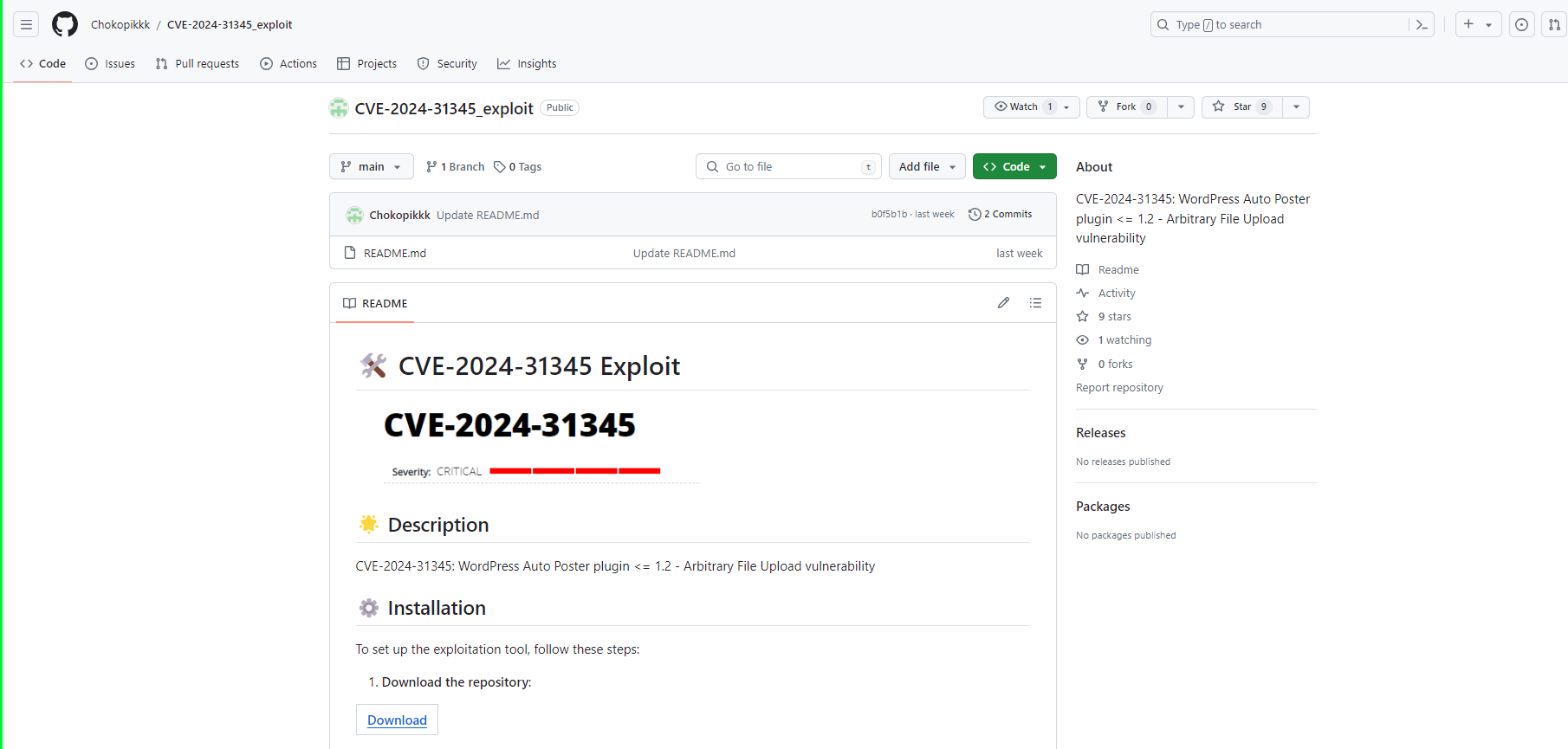
A recent encounter with a supposed Proof of Concept (PoC) on GitHub for CVE-2024-3094 (a newly disclosed XZ library vulnerability) serves as a stark reminder of the dark side of open-source contributions. The repository claimed to offer a PoC for the XZ vulnerability. It also directed users to a link within the README.md file to download exploit files. This link led to satoshidisk.com, a file host known for exchanging files for Bitcoin. This was the first red flag. Genuine security research and legitimate PoCs typically do not involve monetary transactions, especially not through obscure platforms dealing in cryptocurrency. Figure 1 - Satoshidisk.com holds exploit files for sale Further scrutiny of the README revealed the inaccuracy of the explanation of the exploit. In fact, it did not even pertain to the described vulnerability. This mismatch between the stated vulnerability and the explanation is a critical warning sign of the repository's untrustworthiness. Figure 2 - Suspicious PoC of CVE-2024-21410 with similar README Figure 3 - Suspicious PoC of CVE-2024-31345 with similar README The creator of the repository had only recently joined GitHub. Also, they limited activity to this repository and another similar one. Both repositories contained similar README files and directed users to the same website. Further, the website offered files with identical names and sizes for purchase. Such patterns indicate a likely fraudulent scheme, exploiting the trust within the cybersecurity community. Figure 4 - GitHub profile with multiple such repositories which follow similar patterns Figure 5 - Another example of a fake GitHub Profile In both Figure 1 and Figure 6, it’s evident that the descriptions, file names, and sizes are identical, except for the CVE ID. Figure 6 - Exploit files of different CVEs for sale that have the same name and size Further investigation demonstrated this situation was in no way unique. Repositories with similar characteristics were identified, including the latest vulnerability on CrushFTP- CVE-2024-4040. As such, it is clear these were not genuine PoC repositories. Instead, they constitute attempts to capitalize on recent vulnerability disclosures. Thankfully, GitHub is good at taking these down quickly once identified. When multiple repositories for unrelated vulnerabilities feature the same file names and sizes, it suggests no actual relationship between the code and the vulnerability. Figure 7 - GitHub Repository for PoC of CVE-2024-4040 Verify Before Trusting: Always verify the authenticity of a repository before downloading files or executing code. Check the user’s profile for their contribution history and credibility. Look for Official Sources: For vulnerabilities, refer to official sources like NIST’s National Vulnerability Database or trusted security advisories from recognized organizations. Be Skeptical of Monetary Requests: Look for legitimate security research on recognized platforms sharing it for free. Be cautious of any source that asks for payment, especially via cryptocurrency. Report Suspicious Activity: If you encounter repositories that seem dubious, report them. Platforms like GitHub have mechanisms to handle fraudulent activity, and reporting them helps protect the entire community. The attacker(s) invested significant effort creating multiple fake GitHub profiles to distribute suspicious exploit files. These most likely contained malware. Although the success of their efforts remains unclear, their persistence suggests confidence in their strategy. Whether this is the work of an individual or part of a sophisticated campaign remains unclear. Regardless, security researchers need to recognize what attractive targets they represent for malicious actors. When accessing code on platforms like GitHub, it is key to exercise caution. Reviewing any and all code thoroughly before execution is an imperative. Also, avoid using unfamiliar code to mitigate potential compromises. Last year, we discovered a fake PoC that distributed a backdoor, and thus predicted malware delivery through such Fake PoCs constituted a growing trend. This trend appears to have continued well into this year.A Suspicious File Host
Patterns of Deception
The Bigger Picture
Recommendations for the Community
Conclusion
Suggestions for further reading:
Beware of Fake PoC Repositories & Malicious Code on GitHub
2024-4-26 00:41:9 Author: www.uptycs.com(查看原文) 阅读量:37 收藏
2024-4-26 00:41:9 Author: www.uptycs.com(查看原文) 阅读量:37 收藏
文章来源: https://www.uptycs.com/blog/fake-poc-repositories-malicious-code-github
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh