Protecting AI applications and infrastructure should involve an end-to-end approach across every stage of the AI lifecycle including but not limited to data input operations, building and training the models, output and deployment of the trained models, developing applications and more. Uptycs takes this holistic approach of protecting your AI’s entire lifecycle beginning with: Improve time to remediate through better summarization of detections (Fig 1 below) - One challenge Security Operations teams have is lack of personnel to understand and triage huge volumes of alerts. The teams are measured based on how quickly (response time) a potential threat is remediated. Often security teams do not grasp the true criticality of the threat and don’t see the forest for the trees. This can lead to focusing on low risk issues, instead of timely mitigation of the risks that truly matter. One of the most powerful capabilities of GenAI and large language models is to solve such fundamental problems by summarizing large bodies of text and associated context in a meaningful human understandable format. At Uptycs, we leverage GenAI to summarize alerts and detections across your cloud infrastructure and hybrid cloud workloads. We help users understand the nature of the detected behavior as well as explain in natural language the specific behaviors that led to the alert. Faster comprehension by the security teams leads to faster response. Figure 1 - Uptycs GenAI for detection and alert summarization Boost your cyber asset discovery through AI augmented ASK UPTYCS (Fig 2 below) - Most of the cyber security tools for the SecOps team depend on some form of query language to find a needle in the haystack when faced with huge volumes of data. This impedes the tools’ usage due to know-how that the team needs to develop around a specific query language. Ask Uptycs’ purpose is to overcome such challenges and enable teams to ask questions in plain English. This helps them to focus more on solving actual security problems rather than learning new tools. Figure 2 - Ask Uptycs AI Workload monitoring - Uptycs collects telemetry from GPU processors purpose-built for running AI models through a partnership with an increasing number of hardware manufacturers. The telemetry collected here feeds into our unified data pipeline. This deep telemetry can span any AI workload running on purpose-built GPU processors. AI pipeline Cloud Infrastructure monitoring - Uptycs helps customers maintain a better security posture across their key AI infrastructure services from cloud providers such as AWS and Azure. The security posture improvement can be achieved through customizable, out-of-the-box policies and rules based on security best practices recommended by the cloud providers and AI risk management frameworks, including:
Uptycs helps organizations to adapt AI more securely to meet their business needs through the following ways
Using Generative AI (GenAI) to improve your security and security processes
.png?width=874&height=396&name=Screenshot%202024-05-03%20at%202.26.11%20PM%20(1).png)
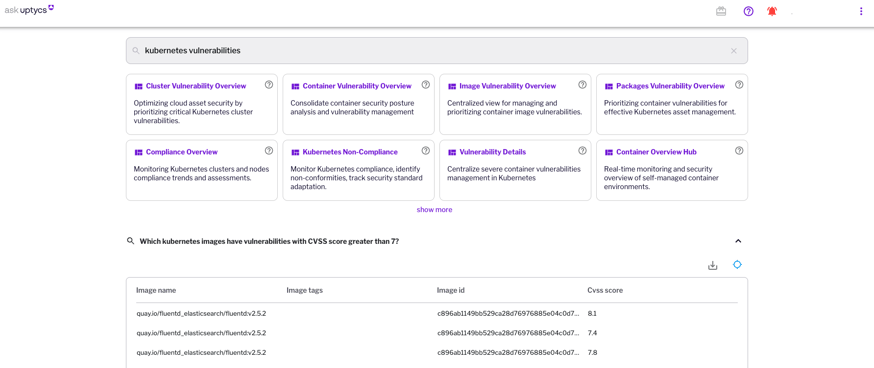
At Uptycs, Ask Uptycs leverages GenAI-based knowledge retrieval to assist with the navigation and discovery of cyber assets across your hybrid cloud infrastructure. It helps to get answers to basic cyber security questions quickly thereby reducing your time to investigate or triage any issues around that asset. The search interface also helps customers pivot between related dashboards and suggests questions that are related to each other. This improves the security team’s investigatory workflows for any specific triaging and remediation of these alerts.
Protecting your AI workloads and infrastructure with enhanced telemetry and guardrails
With this new capability, customers can now extend their anomaly and threat detection frameworks to detect malware, exploitation attempts, model tampering, and unexpected usage of expensive GPU resources running their AI models. This helps customers to protect their AI workloads during different phases of their lifecycle such as modeling, deployment, or running applications on top of those AI models.
Manage Security Risks Across Your AI’s Entire Lifecycle
2024-5-6 21:1:0 Author: www.uptycs.com(查看原文) 阅读量:8 收藏
2024-5-6 21:1:0 Author: www.uptycs.com(查看原文) 阅读量:8 收藏
文章来源: https://www.uptycs.com/blog/manage-security-risks-across-your-ais-entire-lifecycle
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh