2024-5-20 22:44:6 Author: lab.wallarm.com(查看原文) 阅读量:9 收藏
Dell recently issued a notice regarding a data breach that occurred on May 9, which has reportedly affected over 49 million customers across the globe.
According to a report by BleepingComputer, Dell initiated the distribution of notifications cautioning its customers that their personally identifiable information (PII) had been compromised in a data breach. This breach encompassed customer order details, such as warranty specifics, service tags, names of customers, installation addresses, customer IDs, and order references.
Via email communication, the computer and IT product manufacturer alerted users that it is currently probing an occurrence involving a Dell platform housing restricted categories of customer data linked to purchases made by the company.

On April 28th, an individual identified as Menelik posted the data for sale on the Breached hacking forum, but moderators swiftly removed the post. The image below shows the post by the malicious threat actor on the forum.

How did API abuse lead to the Dell data leakage?
In an exclusive conversation with BleepingComputer, threat actor Menelik disclosed that they were able to access and steal the data after coming across a portal that was used by resellers, partners, and retailers to access order information.
Menelik claimed to have gained entry into the portal by registering multiple accounts using fabricated company names, successfully obtaining access within just two days without any verification.
Speaking to BleepingComputer, Menelik stated, "Registering as a partner is quite straightforward. You simply complete an application form, providing company details and your reason for partnership."
The process leads to instant approval with unrestricted access to the 'authorized' portal.
Following their successful access to the portal, Menelik disclosed that they had devised a software capable of generating 7-digit service tags. These tags were subsequently entered into the portal's page starting in March to retrieve the associated information. Due to the absence of rate limiting on the portal, the hackers were able to extract data from 49 million customer records by sending 5,000 requests per minute for three consecutive weeks.
Customer records regarding the following hardware were lifted from the portal:
- Monitors: 22,406,133
- Alienware Notebooks: 447,315
- Chromebooks: 198,713
- Inspiron Notebooks: 11,257,567
- Inspiron Desktops: 1,731,767
- Latitude Laptops: 4,130,510
- Optiplex: 5,177,626
- Poweredge: 783,575
- Precision Desktops: 798,018
- Precision Notebooks: 486,244
- Vostro Notebooks: 148,087
- Vostro Desktops: 37,427
- Xps Notebooks: 1,045,302
- XPS/Alienware desktops: 399,695
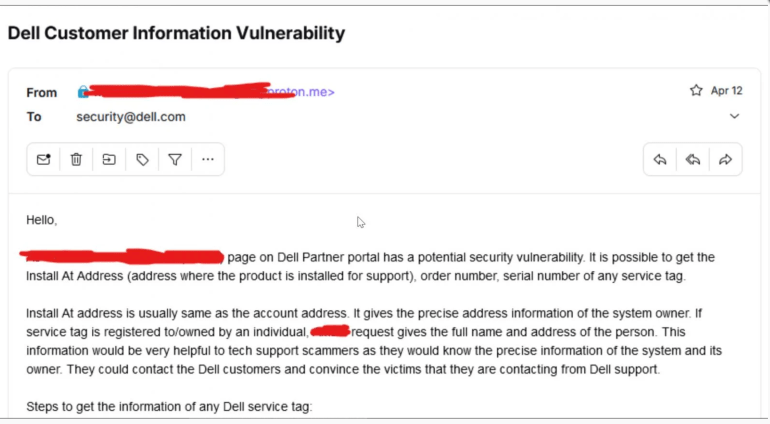
The individuals behind the exposure indicated that they sent emails to Dell's security team on April 12th and 14th to report the vulnerability. With the email probably falling into a backlog of unread emails, Dell failed to intervene on time.
However, it’s important to note that the malicious actors admitted to BleepingComputer that they harvested data of 49 million records before reaching out to the team at Dell.
Email sent to Dell from Menelik

The individual(s) behind the threat asserted that Dell did not respond to the emails or address the vulnerability until about two weeks later, which coincides with the initial posting of the stolen data on Breach Forums hacking forum.
Dell acknowledged that they had received the emails from the hackers but declined to provide additional details, citing an ongoing law enforcement investigation. Nevertheless, the company stated that they had already detected the suspicious activity before receiving the emails from the threat actor.
Rise in API vulnerabilities leading to critical exposures
Dell isn’t alone in being impacted by API exploits. In recent years, easily accessible APIs have emerged as a significant vulnerability for companies, as threat actors exploit them to extract sensitive data for resale to other malicious entities.
Recently, a highly concerning security loophole was discovered in a WordPress plugin. Officially designated as CVE-2024-2876, the vulnerability represented a significant threat as it exposed numerous websites to potential attacks. Wallarm’s Integrated API and Application Security Platform has detected thousands of malicious requests associated with this exploit in just the past two months.
In another instance of an API vulnerability leading to a significant breach, a severe command injection vulnerability within Palo Alto Networks’ GlobalProtect Gateway feature of certain PAN-OS versions was actively exploited to install backdoors on Palo Alto firewalls. Identified as CVE-2024-3400, the exposure allowed unauthorized users to execute commands as the system administrator, significantly threatening the security of critical infrastructure.
To know how Wallarm, a leader in API Security, helps organizations detect and block such vulnerabilities, visit our official website.
如有侵权请联系:admin#unsafe.sh