2024-5-21 21:35:0 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
Article
Security teams face an uphill battle in securing a budget. Leaders are now leveraging company culture and employee collaboration to change perceptions of security as a cost center.

Securing a budget is a significant challenge for many leaders; those charged with security efforts often doubly so. Leaders need to demonstrate the results of their security programs, which are only sometimes immediately visible. Additionally, most organizations view these programs as a necessary cost center — making it even harder to gain the necessary support and investment.
Security operations encompass reactive and proactive measures, producing tangible and intangible outcomes. The challenge lies in conveying these subtle results to decision-makers who may need to fully understand the importance of preventing physical security incidents before they escalate. This gap hinders the allocation and management of resources.
“I’ve experienced that other members and executives on the team gravitate to the reactionary [metrics] and to the ones that show we’re doing work,” Wendy Bashnan, Director of Security & Fire at Scout Motors, said. “I came into it thinking a little broader and asking, ‘Are we effective? How are we going to show we’re effective?’”
Using cybersecurity teams to help illustrate her point that people’s behavior must change, Bashnan noted that it’s common for IT teams to define cybersecurity policies, such as regular backups or security training, that employees rarely follow.
Altering behavior is a gradual process, but momentum can be built to shift mindsets to see intangible benefits as tangible.
This article explores three strategies to cultivate momentum and consensus for your security program:
01
Integrate an always-on security mindset into the company’s culture with the help of Human Resources (HR).
02
Develop a security departmental “pitch” that explains what the department does, why it does it, and how it helps the business’s bottom line.
03
Mimic the strategies of other departments that are typically considered cost centers, too, such as HR.
Integrating an always-on security mindset into company culture
The safety and security of the organization should not be the sole responsibility of one department. Instead, it should embody an innovative vision that fosters a unified culture centered on a comprehensive and empowered security organization — a concept called “shared risk consciousness.”
According to Ontic’s Chief Security Officer Chuck Randolph, the concept removes age-old departmental silos, allowing all security professionals to work together toward a common goal.
“Shared risk consciousness empowers all interdependent security roles throughout an organization — whether corporate, physical, cyber, and others — to thrive. This woven approach involves awareness and collaborative engagement in risk management,” Randolph said.
The concept can be best illustrated by increasing cooperation between security and HR departments. HR’s role in enhancing workplace security is growing, but it’s not a takeover; it’s a buy-in.
Ontic commissioned a study, in partnership with the Clarity Factory, on managing threats and risks with a unified model. According to the report, 80% of HR executives surveyed believe that they are directly responsible for protecting their company from hostile, harmful, or aggressive employee behavior.
“Culture plays a major role,” Nick Saroka, Director of Operations at Exlog Global, said. “Because if you have people that are going against the culture that you’re trying to implement, then it’ll naturally revert back to whatever that culture was before.”
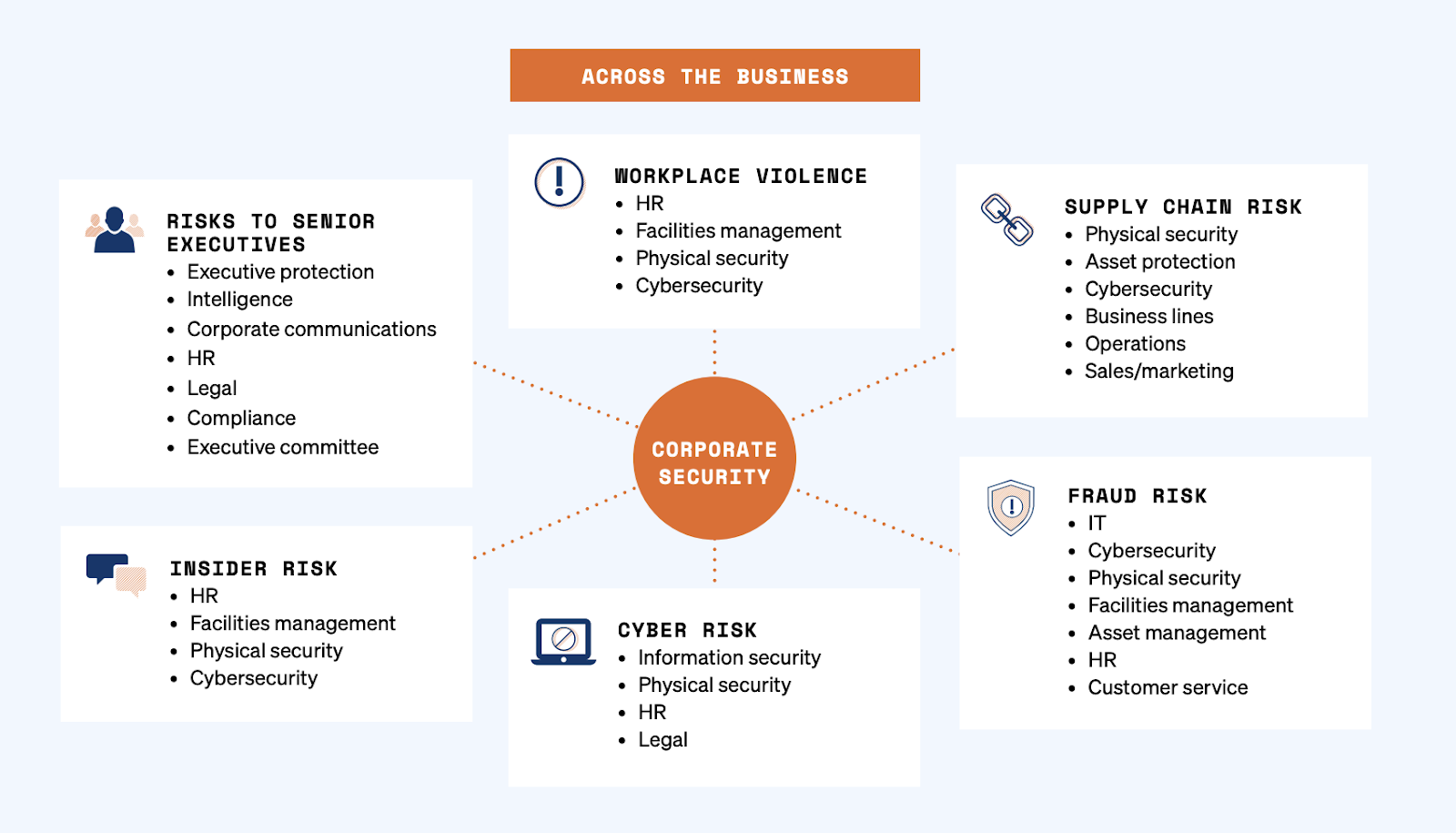
Non-security professionals can significantly contribute to a company’s safety and security culture. Given the wide range of responsibilities that corporate security teams manage, involving non-security staff is crucial to any strategy.
However, to effectively manage and mitigate interconnected risks, corporate security needs to understand where each department can play a role and work seamlessly across teams. The following highlights the functions that a corporate security program needs to collaborate with across the business concerning a range of different risks:
As part of a people, process, and technology strategy, the above-referenced survey suggested that technology’s role is crucial in implementing shared corporate security at scale.
The average confidence level for those who use basic technology is 63%, compared to 69% for those who are advanced and 74% for those deemed cutting-edge. The vast majority of CSOs (90%) said technology improves the overall effectiveness of security operations, enabling security staff to be more productive and efficient, and around the same proportion (88%) recognize that technology is changing the skills required for security professionals.
This data indicates that using advanced technology in security operations is linked to higher user confidence levels, which grow as the technology becomes more sophisticated. Moreover, technology not only enhances the effectiveness of security operations but also necessitates a shift in the skills required for security practitioners.
“[Corporate security] should no longer be thought of as ‘This is security’s budget,” Bashnan said. “I’m not saying that I want to pull all of our money in together and kind of have a commune. But I think there’s an element where if we get other people saying the message, then we can get, at least we can protect what we have and potentially, as things evolve, get additional money for the elements that support the business.”
Create an elevator pitch for your program
Gloria Mark, PhD is a professor of informatics at the University of California, Irvine. During a podcast with the American Psychological Association, she suggested the average human attention span is 47 seconds. With this in mind, ask yourself, “How can I convince an executive to invest in my security program in less than 60 seconds?”
Doing so requires a well-constructed verbal argument for an idea, better known as a pitch, to gain approval and budget for your security program.
For Matthew Spangenberg, an executive security leader at JP Morgan Chase & Company, having his pitch ready proved crucial during an unexpected run-in with a company executive.
“Every time a new senior leader would [join the company], I would put together my own customized elevator pitch for that leader if I had the opportunity to talk with them,” Spangenberg said. “And four and a half years ago, I had that opportunity. It was literally in the elevator lobby. And for that individual, you have to have something compelling because that 60 seconds might be all that you get.”
Begin constructing your business case by focusing on a security-related organizational pain point that is widely recognized within the company. Avoid centering on future capabilities, as this can weaken your argument. When developing your business case, remember to:
- Have all relevant documentation in an appendix. You don’t need to get bogged down in the details, but those who want more background can review the appendix after your pitch.
- Clearly present tangible costs, potential cost savings, and the financial risks of lack of action. Consider the right language for your audience when discussing cost. Clients have different opinions about calling this a “cost-benefit analysis” or “ROI assessment.”
SCIPAB is a framework commonly used as a template for a persuasive business case. SCIPBAB stands for:
Situation: What is the current problem or opportunity? This should be something that already has broad agreement among your audience. Getting agreement at this stage increases the likelihood of a yes at the end of the presentation.
Complication: What are the pressures or demands that impact the situation? Here, briefly explain any challenges related to the situation.
Implication: What are the consequences of failing to act on the problem identified in the Complication?
Make this point compelling by estimating the potential financial risks associated with a security breach should subsequent legal actions and negative public relations coverage occur.
Position: What solution are you proposing to the problem?
Action: What action do you need from your audience? Make a statement about how your audience
can act to support your position, whether by approving the budget, sharing resources, or something else.
Benefit: What are the benefits of taking the desired action and adopting the solution proposed in the Position? Back up the benefits with supporting documentation like a cost-benefit analysis.
Mimic HR and Legal’s evolutions from cost centers to profit centers
The journey from cost center to profit center, while rugged, is a worn pathway. For example, once considered money pits, many HR departments have shifted companies’ mindsets.
Through her research, Rachel Briggs, CEO and Founder of The Clarity Factory, reveals a paradigm shift where security departments must evolve from “corporate cop” to C-suite executive. The shift is similar to the one human resources began years earlier.
“In my research, HR was referred to commonly within the company as the corporate cop,” Briggs said. “It was referred to in this way because it spent its time enforcing policies, telling managers what they could and couldn’t do, and administering a number of fairly technical administrative programs like payroll, performance appraisal, and so on and so forth. Now we know where the HR journey ended. It ended squarely in the C-suite.”
A study by CareerBuilder revealed that 74% of companies that made a poor hire lost an average of $14,900 per poor hire. Bad hires can also decrease employee morale, negatively impacting productivity. Consider this: How would a company’s average financial loss from a security breach affect employee morale and productivity?
Recognizing security as a value driver rather than just a cost center involves shifting from measuring performance (MOP) to assessing effectiveness (MOE).
“We’re focused on the activities (MOPs) and often overlook the MOE, which assesses whether our actions are effectively advancing our objectives,” Randolph said.” The MOE represents a behavioral change towards a stated goal, while performance encompasses all the actions we undertake. However, the key question is whether these actions are truly driving behaviors towards positive outcomes (green) or negative ones (red).”
Shifting the narrative
Security is not a cost center, yet that’s not the story told within many organizations today. Before they were considered value centers, HR, Legal, and Compliance were considered cost centers. It’s time to learn from their playbooks.
First, adopt the principle of shared risk consciousness. This approach moves away from the notion that only a select few are responsible for corporate security and toward cultivating a culture that supports a robust and empowered security organization.
Second, security professionals must also excel in communication. It’s essential that employees and company leaders quickly grasp who you are, what you do, and why it’s important to them — all within 60 seconds. Without their support, advancing your security program will be challenging.
Finally, adjust how you view security. See it as a value center, not just a cost center. Security enhances value by protecting the supply chain, creating a safe work environment to retain staff, safeguarding assets, and using advanced technology to predict and mitigate threats, thereby conserving substantial company resources.
The post Three Ways to Build Momentum and Consensus for Your Security Program appeared first on Ontic.
*** This is a Security Bloggers Network syndicated blog from Articles - Ontic authored by Ontic. Read the original post at: https://ontic.co/resources/article/three-ways-to-build-momentum-and-consensus-for-your-security-program/
如有侵权请联系:admin#unsafe.sh