
2024-5-24 21:0:0 Author: www.tenable.com(查看原文) 阅读量:10 收藏

Check out the EPA’s call for water plants to beef up their cyber defenses. Plus, open source developers have a new platform to share threat intelligence. Moreover, business email compromise attacks prompt alert from U.K.’s cyber agency. And CISA tackles DNS encryption best practices. And much more!
Dive into six things that are top of mind for the week ending May 24.
1 - EPA to dial up enforcement of cyber requirements for water systems
The U.S. government is urging water plants to boost their cybersecurity in accordance with federal law, as hackers increasingly target these critical infrastructure organizations.
More than 70% of U.S. water systems don’t fully comply with the cybersecurity requirements of the Safe Drinking Water Act, according to recent inspections by the U.S. Environmental Protection Agency (EPA). This prompted the EPA to issue an “enforcement alert” this week.
“Protecting our nation’s drinking water is a cornerstone of EPA’s mission, and we are committed to using every tool, including our enforcement authorities, to ensure that our nation’s drinking water is protected from cyberattacks,” EPA Deputy Administrator Janet McCabe said in a statement.
Among the actions the EPA is urging water plants to take immediately are:
- Reduce exposure to vulnerabilities
- Make regular cybersecurity assessments
- Change default passwords
- Inventory all operational technology (OT) and IT assets and back them up
- Provide cybersecurity training to the staff
To get more details, read:
- The announcement “EPA Outlines Enforcement Measures to Help Prevent Cybersecurity Attacks and Protect the Nation’s Drinking Water”
- The enforcement alert “Drinking Water Systems to Address Cybersecurity Vulnerabilities”
- The fact sheet “Top Cyber Actions for Securing Water Systems”
To learn more about the threat to water systems and how to address it, check out these Tenable resources:
- “Shoring Up Water Security: Industry Leaders Testify Before Congress” (blog)
- “Protecting Public Water Systems from Cyberattacks” (solution brief)
- “Keep the Water Flowing for the DoD: Securing Operational Technology from Cyberattacks” (blog)
- “Tech Perspectives: What is the State of Cyber Risk in the Water Sector? A Q&A with Tenable’s Marty Edwards” (news article on WaterFM)
- “Enhancing Critical Infrastructure Cybersecurity for Water Utilities” (Infographic)
VIDEOS
Tenable Homeland Security Testimony 2024: Marty Edwards Opening statement
The Constant Drip: EPA Water Regulations, Funding Sources, And How Tenable Can Help (on demand webinar)
2 - New threat intel platform launched for OSS
Developers and maintainers of open source software (OSS) have a new centralized platform to share threat intelligence information and help each other boost the security of their projects.
Called Siren, the platform is hosted by the Open Source Security Foundation (OpenSSF) and aims to provide visibility into the tactics, techniques and procedures, as well as into the indicators of compromise associated with attacks targeting OSS.
“Siren is intended to be a post-disclosure means of keeping the community informed of threats and activities after the initial sharing and coordination,” OpenSSF said in a blog this week.

OpenSSF is inviting all developers and maintainers of open source projects, as well as cybersecurity enthusiasts, to join Siren.
To get more information, check out:
For more information about OSS security:
- “Open Source Software Security Roadmap” (CISA)
- “White House releases report on securing open-source software” (CyberScoop)
- “Securing open source software: Whose job is it, anyway?” (The Register)
VIDEO
CISA Live! Presents Open Source Software Security
3 - U.K. cyber agency issues tips on preventing BEC attacks
As business email compromise grows, the U.K. National Cyber Security Centre (NCSC) has new guidelines to prevent these attacks, in which scammers impersonate business leaders to dupe employees into transferring them money.

Here are some of the NCSC’s recommendations, aimed specifically at small and medium size businesses:
- Don’t overshare details about your company’s senior management on social media and public websites.
- Train staff to detect BEC email characteristics. Tell-tale signs include emails in which a senior leader, out of the blue, asks for an urgent payment or money transfer.
- Set up multi-factor authentication (MFA), thus reducing the chances that attackers will hijack email accounts.
- Adopt the principle of least privilege, to ensure, for example, that the ability to conduct large-scale financial transactions is limited only to the appropriate staffers.
- Establish a process in which high-value payments and transactions requested via email are also confirmed using other methods, such as a phone call or an in-person meeting.
To get more details, read:
- The NCSC blog “Business email compromise: new guidance to protect your organisation”
- The NCSC guidance “Business email compromise: defending your organisation”
For more information about BEC attacks:
- “5 ways to mitigate the risks of business email compromise attacks” (Deloitte)
- “Business Email Compromise” (FBI)
- “Business Email Compromise: What It Is and How to Prevent It” (National Cybersecurity Alliance)
4 - CISA offers guidance on encrypted DNS traffic
Looking for best practices on how to adopt DNS encryption? You might want to check out new guidelines just published for U.S. federal agencies.
The new guide “Encrypted Domain Name System (DNS) Implementation Guidance” offers DNS encryption recommendations for networks, DNS infrastructure, on-premises endpoints, cloud deployments and mobile endpoints.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) developed the document to help federal agencies understand and implement “key actions and protocols” to start encrypting DNS traffic, CISA official Eric Goldstein said in a statement.
“This guide will help agencies progress further in their zero trust security journey,” Goldstein added.
The guide includes a phased-implementation checklist, detailed implementation recommendations and vendor-specific implementation advice, including for specific web browsers, operating systems and DNS servers.
5 - SocGholish rides wave of fake update attacks
SocGholish continues reigning supreme among malware variants, with a 60% share of malware incidents in the first quarter of 2024, as attackers deploy it in fake software update campaigns.
It’s the third straight quarter in which SocGholish ranks first in the Center for Internet Security’s (CIS) quarterly list of top 10 malware, a sign of the prevalence of fake update attacks.
SocGholish, written in JavaScript, is distributed via malicious or compromised websites that peddle fraudulent software updates.
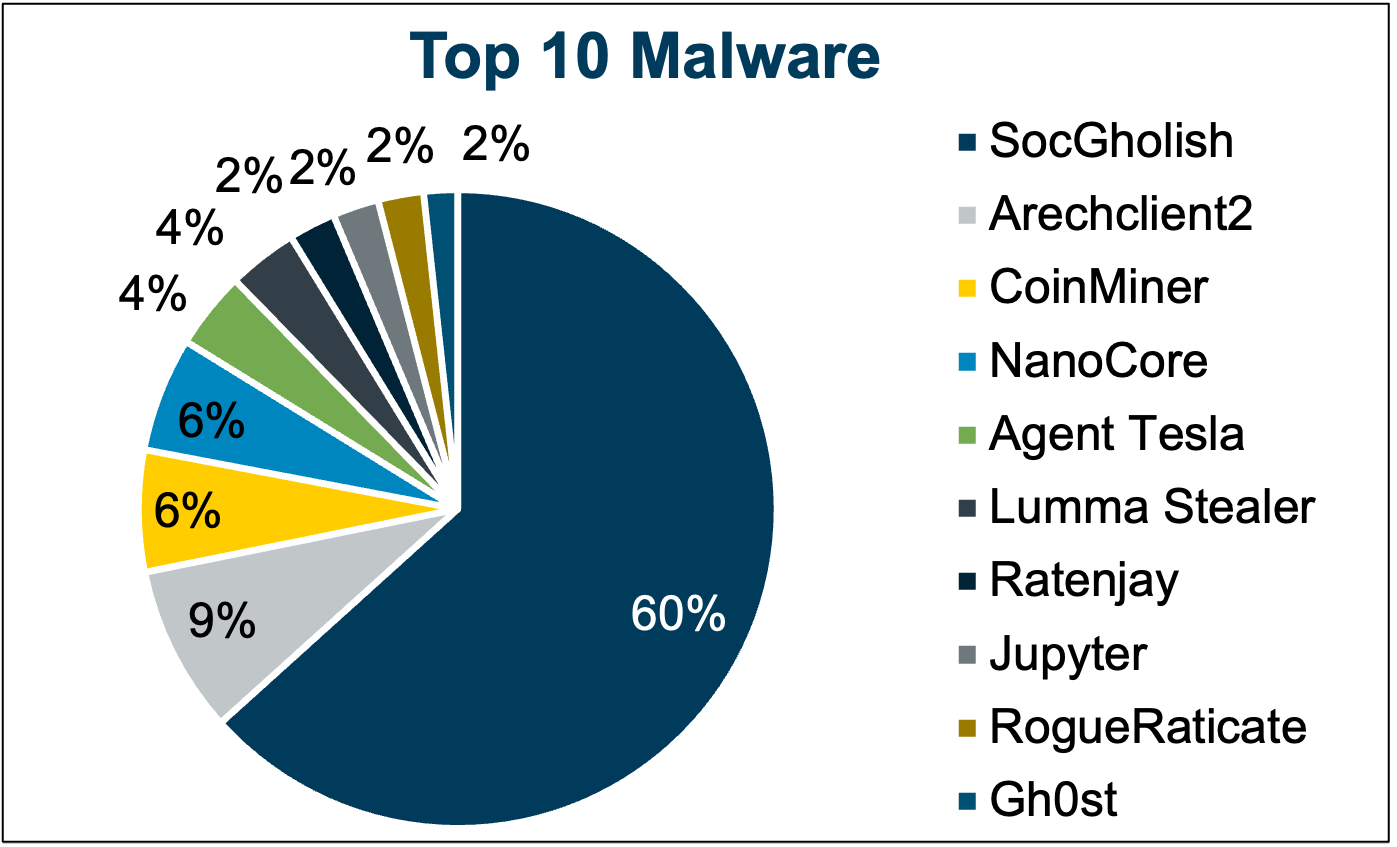
(Source: Center for Internet Security)
Here’s the full list, in descending order:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- Arechclient2, a .NET RAT whose capabilities include multiple stealth functions
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- NanoCore, a remote access trojan (RAT) that spreads via malspam as a malicious Excel spreadsheet
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- Lumma Stealer, an infostealer that focuses on swiping personally identifiable information and features multiple evasion capabilities
- Ratenjay, a RAT that's dropped by other malware, executes remote commands and has keylogging capabilities
- Jupyter, an adaptive .NET infostealer that’s highly evasive
- RogueRaticate, a downloader distributed through malicious or compromised websites using fake browser updates.
- Gh0st, a RAT designed to control infected endpoint devices
To get more information, check out CIS’ “Top 10 Malware Q1 2024” blog report, which provides details, context and indicators of compromise for each malware strain.
For more information about fake update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Atomic Stealer malware strikes macOS via fake browser updates” (Bleeping Computer)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “Malware crooks find an in with fake browser updates, in case real ones weren't bad enough” (The Register)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
VIDEO
Fake Chrome Update Malware (The PC Security Channel)
6 - 2023 was a banner year for phishers with nearly 5M attacks
Cyber scammers unleashed almost five million phishing attacks in 2023, the most ever recorded in a year, as phishers ramped up their abuse of social media platforms and voice phone calls to carry out their crimes.
That’s according to the Anti Phishing Working Group’s (APWG) “Phishing Activity Trends Report” for the fourth quarter of 2023.
Phishing actually dipped at one point in 2023, after the shutdown of the Freenom free domain-name program, which was heavily used by phishers for many years. But even with that dip, 2023 ended up being the worst on record for phishing victims.
Industries Most Targeted By Phishers, Q4 2023
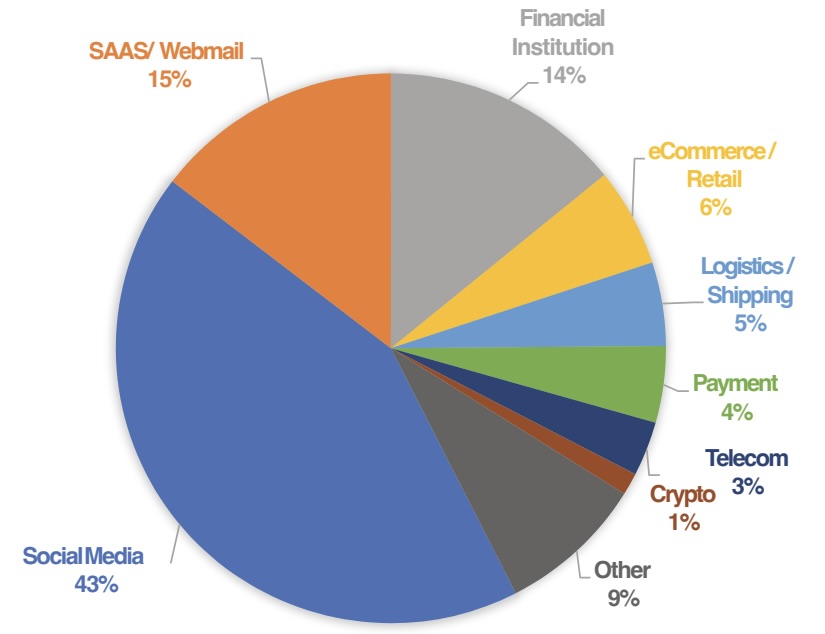
(Source: Anti Phishing Working Group’s “Phishing Activity Trends Report” for Q4 2023)
In the fourth quarter, phishers turned up the heat on social media platforms, which got hit with almost 43% of phishing attacks. Meanwhile, voice phishing, or “vishing,” is becoming popular with scammers, as they use deep-fake tools to imitate voices of people the victims know.
To get more details, read:
- The statement “APWG Q4 Report Finds 2023 Was Record Year For Phishing”
- The “Phishing Activity Trends Report” for Q4

Juan Perez
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
Related Articles
- Center for Internet Security (CIS)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government
- Threat hunting
- Threat Intelligence
- Vulnerability Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose Your Subscription Option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a Sales Representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank You
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology Security You Need.
Reduce the Risk You Don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a Demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
In Action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management In Action
Know the exposure of every asset on any platform.
Thank You
Thank you for your interest in Tenable Attack Surface Management. A representative will be in touch soon.
Try Tenable Nessus Professional Free
FREE FOR 7 DAYS
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
Now Available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro Trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert Free
FREE FOR 7 DAYS
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh