
2024-5-31 17:2:3 Author: www.netcraft.com(查看原文) 阅读量:6 收藏
Fake pharmacies sell prescription-only drugs without a license and without requiring a valid prescription from a doctor. The storefronts are advertised to consumers through web searches, social media, and unsolicited spam emails. As you might expect, many of these platforms attempt to block known fake pharmacies.
Netcraft analysts have observed evidence of a 12-month spike in fake pharmacy campaigns using page.link (Firebase Dynamic Links), more than doubling since last year. Many of these campaigns bounce visitors through a series of redirects to disguise the eventual destination, inadvertently making it easy for fraudsters to hide malicious links in shortened URLs.
What are fake pharmacies?
Fake pharmacies are a type of counterfeit online shopping website that market prescription drugs, often advertising them as well-known products from established pharmaceutical companies.
Usually operating outside the countries to which they’re selling, these stores are unlicensed and unregulated and will often include false accreditations and phony endorsements from reputable organizations to build perceived credibility.
The majority of fake pharmacies accept standard credit cards and PayPal, with some accepting cryptocurrency for a discount.

Figure 1 Extract from a fake pharmacy site, with spoofed endorsements
Some sites will simply steal payment details. However, unlike other fake online shopping websites, most fake pharmacies will deliver drugs to victims. These could be counterfeit, diluted, or expired drugs and may contain unexpected, potentially fatal ingredients.
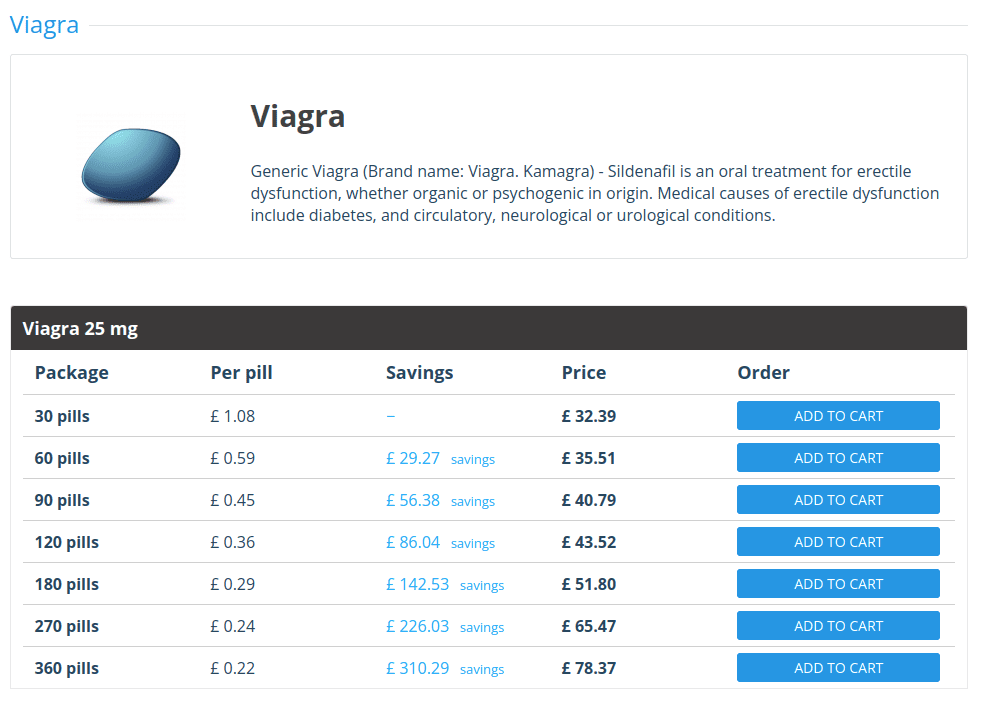
Figure 2 Fake pharmacies sell unlicensed drugs without a prescription, often in very high quantities
Low-quality counterfeits can pose a serious threat to consumers’ health and legitimate pharmaceutical products, with buyers being driven away from real retailers by the lure of large savings and no prescription requirements.
As well as the risks to public health, fake pharmacies have a significant financial impact, with the World Health Organization estimating that $431 billion in drugs are counterfeited worldwide every year.
A growing threat – What Netcraft has detected
During March 2024, Netcraft detected over 37,000 page.link URLs that directed users to fake pharmacy sites, which is more than twice the number detected at the same time last year and indicative of the large increase in the volume of attacks of this type over the last 12 months.
Although the success of fake online pharmacy threats is the underlying driver of the increase in criminal behavior, additional factors for the increases may include:
- Increased cost of living challenges across much of the world, with inflation rising a reported 6.8% globally in 2023
- Shortages in key medications, as reported by the European Medicines Agency (EMA), including very popular prescription-only drugs like Ozempic, continue to trigger warnings from government agencies
- Post-pandemic shifts of counterfeit goods almost entirely to online markets
These, along with other factors, present serious public health concerns.
Why criminals use Firebase Dynamic Links
The cybercriminals behind these campaigns need to hide from law enforcement and from cybercrime disruption organizations like Netcraft. Criminals use link shorteners (such as Firebase Dynamic Links ) to disguise the true destination of their links, making the common suspicious indicators harder to detect. Furthermore, it’s not practical to block a malicious shortened link based on the domain name, as many URL shorteners (such as page.link or bit.ly) are used legitimately by companies all over the world, as was shown in a recent review of attacks leveraging SendGrid’s link shortener capabilities.
A recent full spam to storefront link redirect chain looks like:
- Spam email from Pharmacy 24×7 Discounter (Pharmacy-24×[email protected])
- Contains a link to hxxps[:]//fywg[.]page[.]link/coKa
- Which ultimately redirects to hxxps://saledelivery[.]zone/?cp=fmlcqhob
By appending d=1 to a Firebase Dynamic Link you can review the configuration workflow:
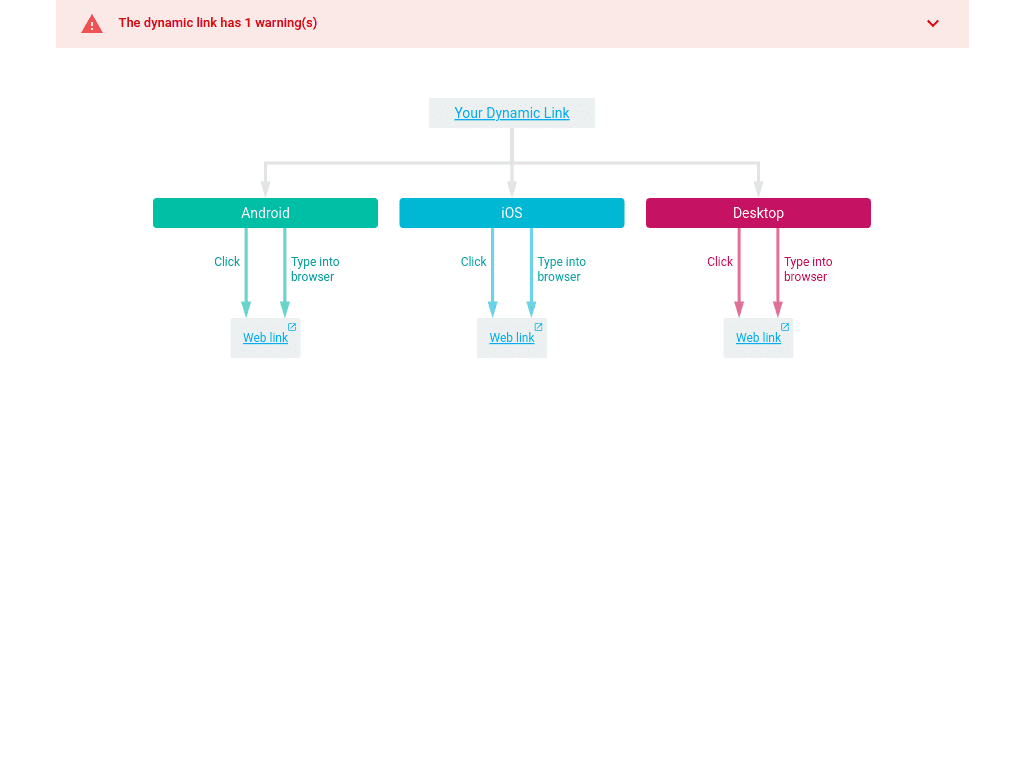
Campaigns commonly use unpredictably named sub-domains of page.link combined with seemingly random URL paths, making their discovery more challenging. Netcraft processes circumvent this deceptive tactic by examining and following millions of links in spam emails received and analyzed by our systems.
Using Firebase Dynamic Links allows criminals to direct victims to different locations. For example, based on the platform they are using, the OS version, or whether they have a specific app installed. Combined with an easy-to-use API to generate many URLs in bulk, it creates additional layers of complexity for cyber criminals to construct complex hiding mechanisms and evade detection.
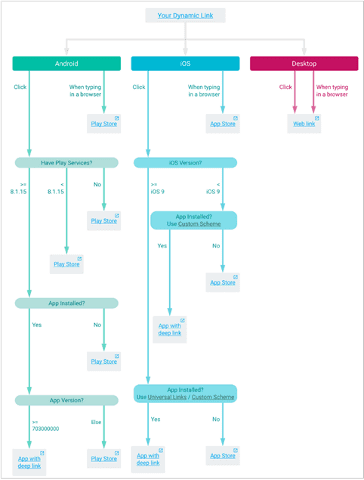
Figure 3 Dynamic links flowchart (from https://firebase.google.com/docs/dynamic-links/debug )
Firebase Dynamic Links is scheduled to be shut down in August 2025, taking all these links with it, but these deceptive campaigns will continue to spread until then. Once Firebase Dynamic Links are no longer an option, criminals will simply move on to another link-shortening platform. We already see the use of other common URL shorteners, including bit.ly, is.gd, and through various email providers, as previously mentioned.
Protecting users – and your brand – from fake pharmacies
There is a public health responsibility for regulators, payment providers, URL-shortening providers, and pharmaceutical companies to work proactively disrupting criminal behavior in respecting fake online pharmacies. With Netcraft, leaders around the world are able to deploy countermeasures against criminal infrastructure that exploit redirection techniques and malicious fake pharmacy websites.
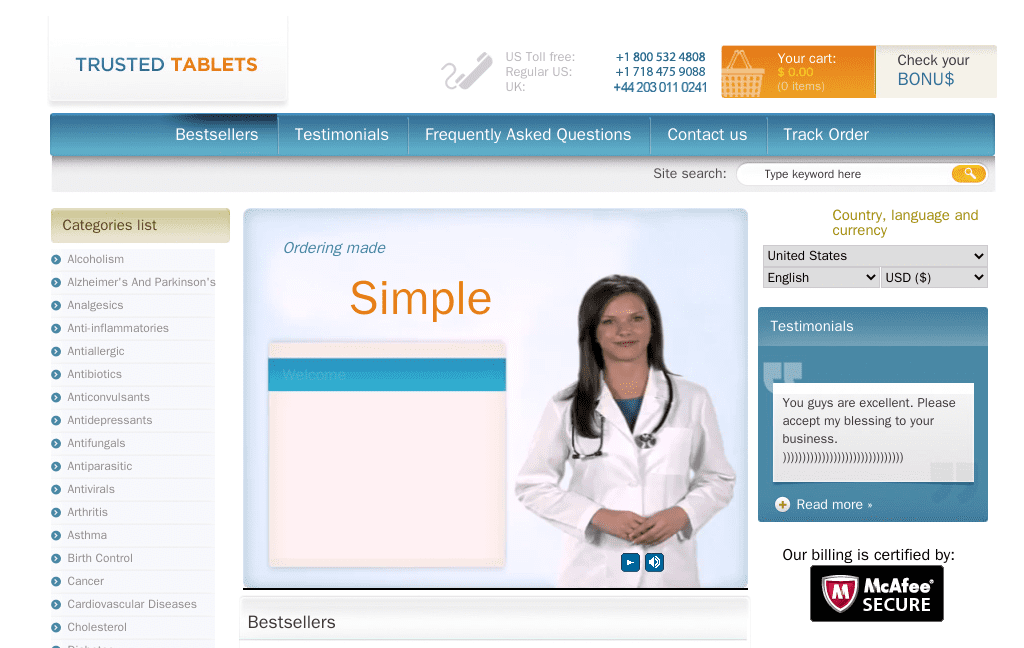
Figure 4 A typical ‘fake pharmacy’ store complete with bogus testimonies and endorsements
Netcraft’s sophisticated cybercrime platform is able to trace malicious links and follow complex redirect chains in order to disrupt these campaigns and take down malicious sites. Our in-depth analysis of the criminal’s entire advertising and distribution mechanism means we can disrupt as much of the criminal’s infrastructure as possible. This broad approach covers the entire threat lifecycle, from mail servers sending advertising emails, link shorteners, redirecting websites, fake pharmacy storefronts, and their checkout infrastructure.
To find out how we can protect your customers – and your brand – from the threat of fake pharmacies and other malicious stores, you can request a demo by visiting https://www.netcraft.com/book-a-demo/.
如有侵权请联系:admin#unsafe.sh