2024-6-14 21:0:41 Author: www.sentinelone.com(查看原文) 阅读量:7 收藏
The Good | Ukrainian Police Arrest Cryptor Specialist Helping Conti & LockBit Ransomware Operations
A Russian national was arrested this week for allegedly working with Conti and LockBit ransomware groups, helping to make their malware undetectable and also conducting at least one attack himself. Ukrainian cyber police apprehended the 28-year-old man in Kyiv during Operation Endgame, a major operation carried out two weeks ago to dismantle an extensive ecosystem of malware droppers.

According to Ukrainian law enforcement, the arrested had expertise in developing custom crypters that encrypted and obfuscated ransomware payloads into what looked like innocuous files. This made them fully undetectable (FUD) to legacy antivirus software. His services were sold to both Conti and LockBit syndicates, which bolstered their success rates in infiltrating networks.
Reports from Dutch police confirm that the man orchestrated at least one of his own attacks using a Conti payload in 2021, indicating his involvement as an affiliate and goals to gain maximum profits from the relationship. His arrest includes seizure of computer equipment, mobile phones, and handwritten notes, all being held for ongoing examination. As it stands, the Russian suspect has already been charged under Part 5 of Article 361 of the Criminal Code of Ukraine for unauthorized interference with information systems. He faces up to 15 years in prison.
This arrest is the latest in a string of actions against LockBit operations, most recently following the distribution of 7000 decryption keys to all affected victims of the Ransomware-as-a-Service (RaaS). Earlier last month, the DoJ unveiled the identity of LockBit’s developer, placing a reward up to $10 million for his arrest or conviction.
The Bad | Hamas-Linked Threat Group Spies on Android Users In Egypt & Palestine
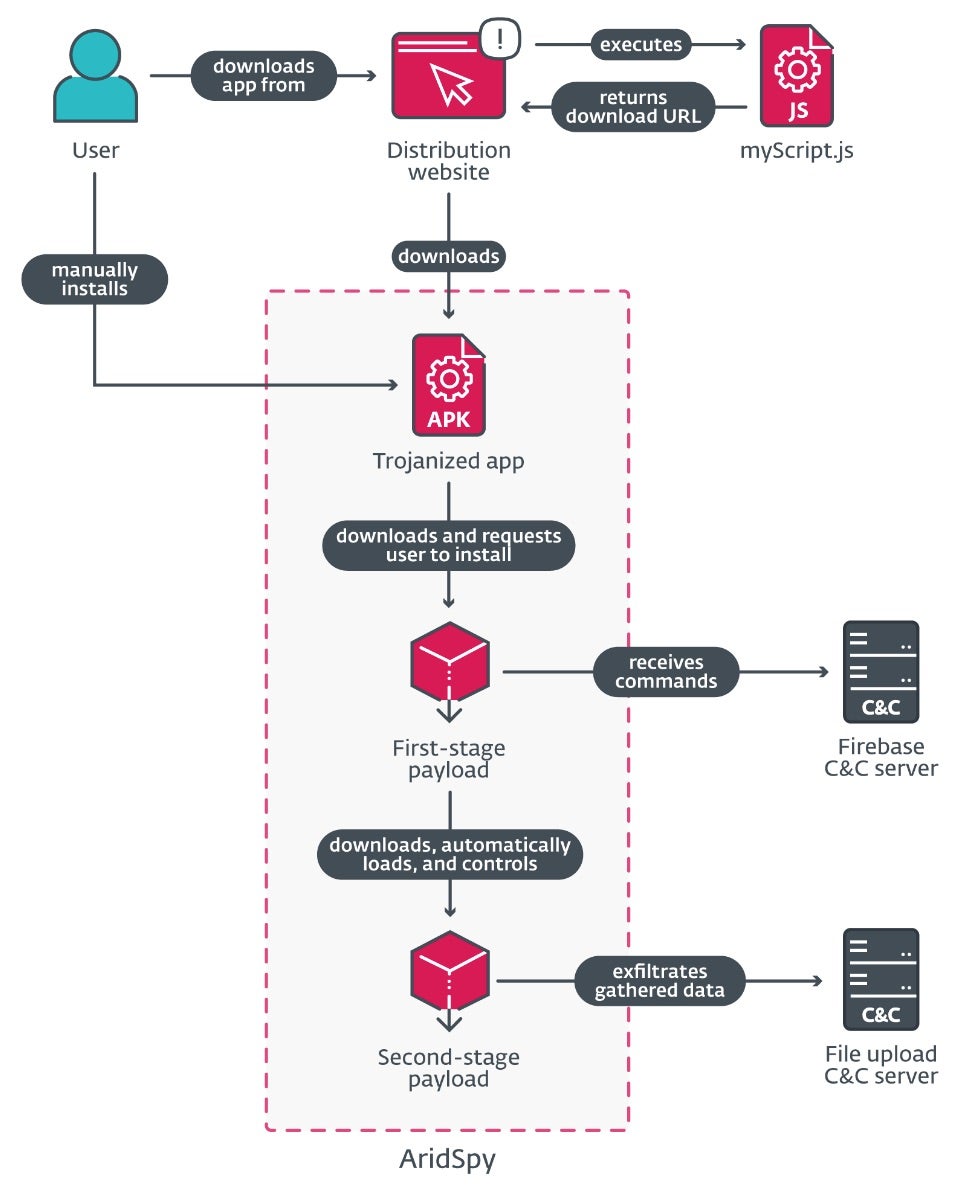
An espionage-focused threat actor known as Arid Viper has been linked to an ongoing mobile-based campaign, involving trojanized Android apps delivering ‘AridSpy’ spyware. Based on a recent report, the Hamas-aligned actor is distributing malware through websites that mimic legitimate messaging, job search, and civil registry applications.
Arid Viper’s latest appearance is marked by a new version of AridSpy – a multi-stage trojan capable of downloading additional payloads from a command-and-control (C2) server. The attacks are primarily targeting users in Palestine and Egypt through websites that distribute the fake (but functional) apps. The apps themselves are clones of legitimate services, but with malicious features.
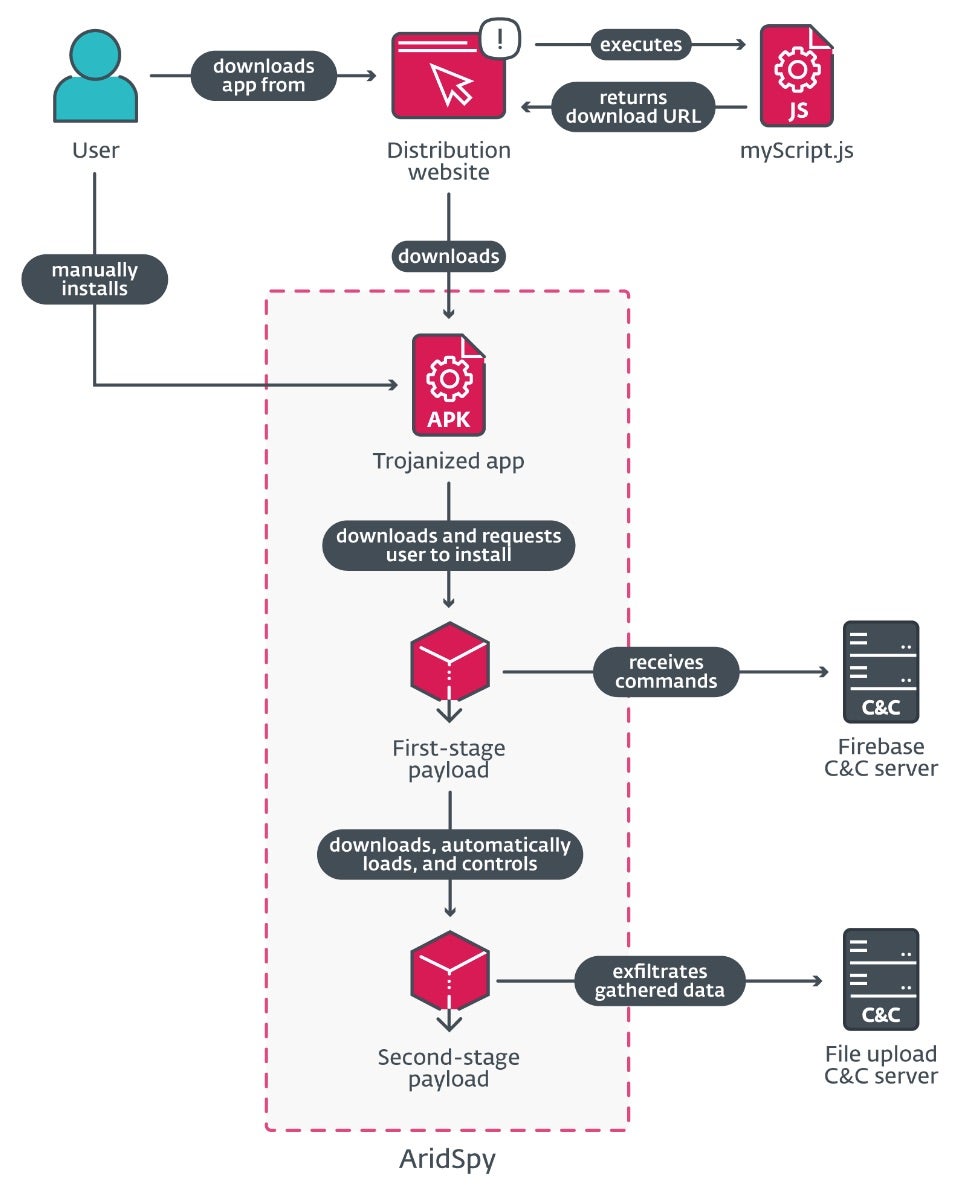
In one case, researchers found a website impersonating a Palestinian Civil Registry which had a nearly 200-person following on its dedicated Facebook page. While the app on this site is not a direct clone of the legitimate version found on Google Play Store, it communicates with its legitimate server, indicating a high level of sophistication by Arid Viper.
The actor is also responsible for registering a fake job opportunity app which, upon install, downloads a first-stage payload posing as a Google Play Services update. The spyware then executes various commands, including taking pictures with the front camera when specific conditions are met and sending the data to the actor’s C2 server.
Arid Viper continues to cause concern due to its consistent use and development of mobile spyware to target military personnel in the Middle East as well as journalists and political dissidents. Organizations in critical infrastructures guarding high-value intel can mitigate the threat of cyber espionage by implementing proactive and AI-enhanced threat detection, advanced response capabilities, and deep visibility across networks.
The Ugly | Multi-Platform Malware Campaign Targets Indian Critical Sectors via RATs
Cyber researchers have uncovered a six-year-long threat campaign, dubbed ‘Operation Celestial Force’, that employs a combination of GravityRAT, an Android-based malware, and HeavyLift, a Windows-based malware loader. Their report ties Pakistani threat group Cosmic Leopard (aka SpaceCobra) to the campaign with high confidence.
While analyzing a sample of #GravityRAT, i came across an interesting binary. It turned out to be the #C2 #panel binary for #GravityRAT and a #Loader dupped #HeavyLift.
Apparently #APT related, i turned to @TalosSecurity for a joint investigation 🧐https://t.co/4wZKgVv2WI— Gi7w0rm (@Gi7w0rm) June 13, 2024
Most recent activity in the operation shows a defined expansion and evolution in the malware suite being used, suggesting ongoing success of the campaign in targeting users in the Indian subcontinent. The operation leverages both Gravity RAT and HeavyLift which are simultaneously managed through another standalone tool called ‘GravityAdmin’.
Though GravityRAT was originally a Windows-based malware deployed via spear phishing emails, it has since been adapted for Android systems as well. The Android version of the tool has now been observed in attacks against the Indian military and Pakistani Air Force personnel by masquerading as cloud storage, entertainment, and chat apps. The HeavyLift malware loader is shipped as an Electron app and targets Windows, macOS and Linux.
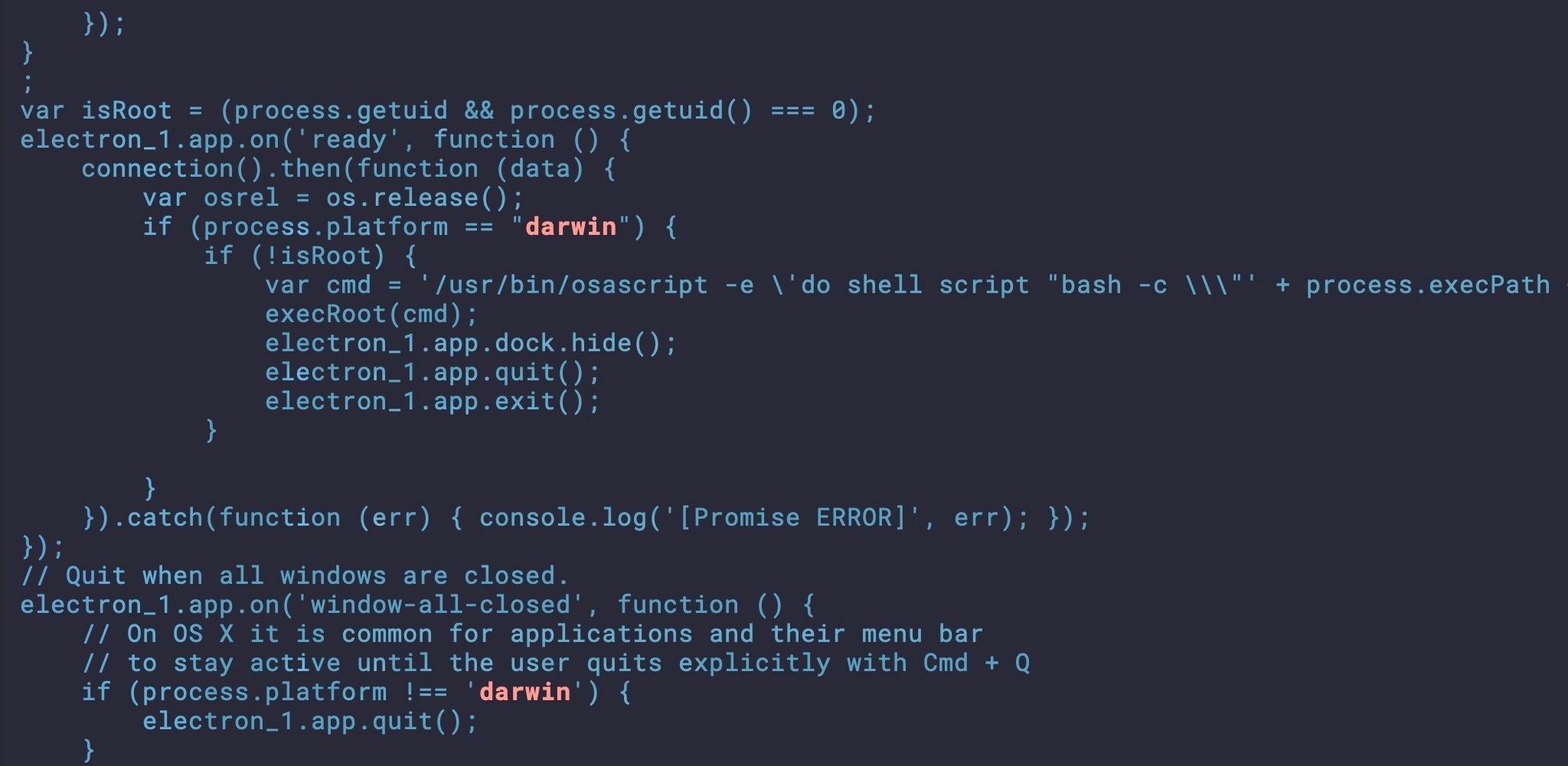
Cosmic Leopard commonly uses spear phishing and social engineering tactics to gain the trust of their victims. After being directed to visit malicious sites, victims are lured into downloading benign-looking programs that then deploy either GravityRAT or HeavyLift depending on the OS in question. The GravityAdmin binary has been used to control the compromised systems since at least August 2021 and works by managing connections with GravityRAT and HeavyLift’s C2 servers.
Researchers posit that the long-running operation will continue to harvest sensitive information from users in the Indian defense, government, and technology sectors, making it crucial for these organizations to shore up their data encryption and monitoring, real-time monitoring, and automated response capabilities.
如有侵权请联系:admin#unsafe.sh