We Love What’s Broken … Yes, This Of Course Means SIEM!
SIEM challenges never stopped me from loving this technology, but I am very cognizant of YMMV. Anyhow, CardinalOps released their annual “state of SIEM” report, and here are some fun highlights.
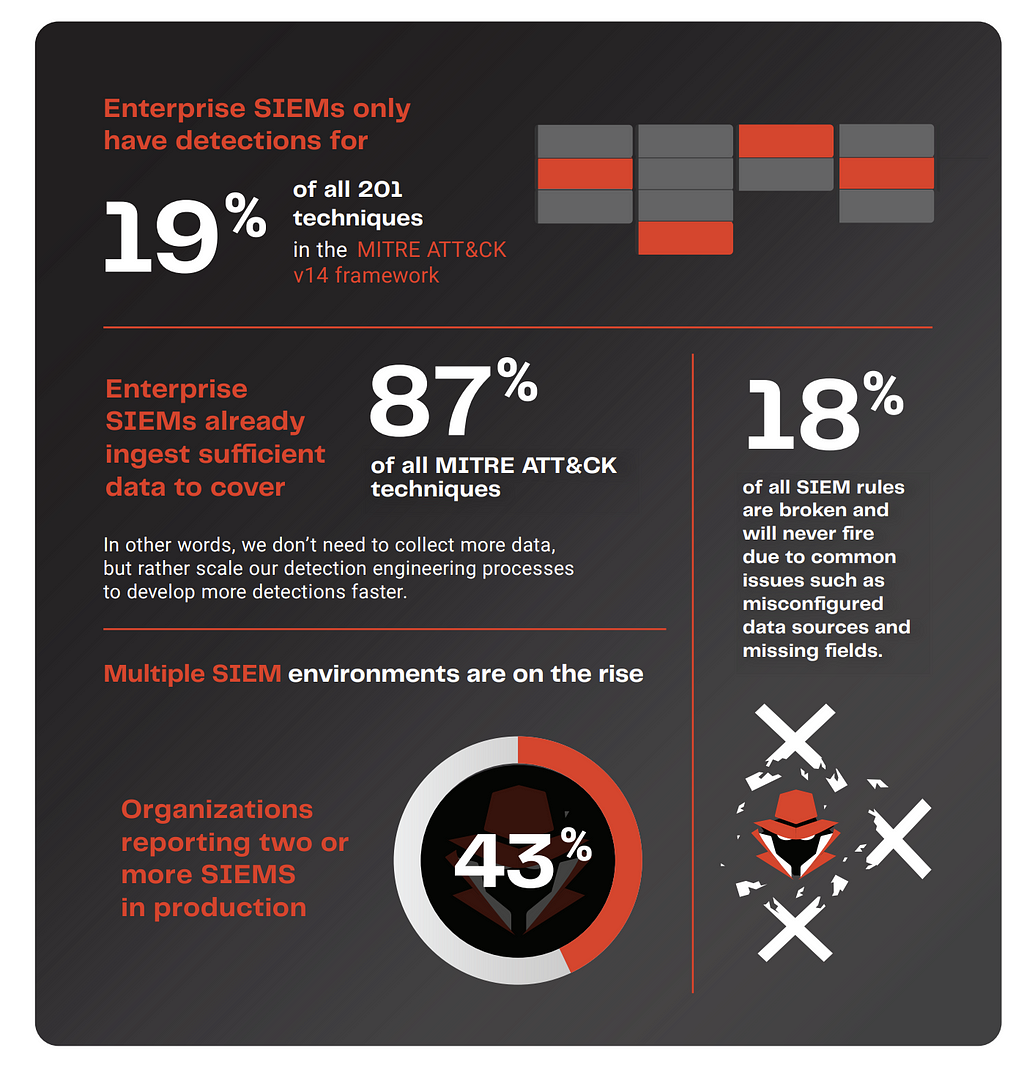
- “Can potentially cover 87% of ATT&CK with existing data sources they’re already ingesting — but are currently only covering less than 19%.“ [A.C. — in my fairly informed opinion, the “security data lakers” are possibly making this particular one worse and definitely not better]
- ”Have more than 18% of their rules that are broken and will never fire an alert due to common issues such as misconfigured data sources, missing fields, and parsing errors.”
- Why so broken?
“Complexity: The average enterprise has more than 130 distinct security tools (endpoint, network, cloud, email, IAM, etc.).
Constant change in infrastructures, security tools, attack surfaces, adversary techniques, and business priorities (e.g., cloud). In fact, over the next 5 years, Gartner Research projects that over 60% of security incidents will be traced to misconfigured security controls.1
No “one-size-fits-all” — every enterprise is unique, making it impractical to copy/paste generic content from SIEM vendors, MSSPs, open source communities, and marketplaces.
Manual and error-prone processes that are highly dependent on individual “ninjas” with specialized expertise, making it difficult to effectively scale and maintain high-quality detections.
Challenges in hiring and retaining skilled personnel who can develop detections across diverse scenarios and log source types.”
- “If you’re like most detection engineering teams, you’re continuously adding new detection rules to your SIEM. But over time, your environment has changed in different ways. [..] So you must continuously identify and fix broken rules!” [A.C. — You have a process to make rules? Good! You actually make rules? Great! Now, get a process for fixing the rules that decayed over time…]
- ”Researchers found that 20–30% of all alerts are simply ignored or not investigated in a timely manner. ” [A.C. — depressing take of the day, but likely true. Don’t create ‘always-ignore’ alerts, and if they are created, destroy them!]
P.S. Free Gemini / LLM tip: don’t ask to summarize, or for insights, ask for surprises!
Related blogs:
- SOC Threat Coverage Analysis — Why/How?
- 20 Years of SIEM Webinar Q&A
- 20 Years of SIEM: Celebrating My Dubious Anniversary
- Security Correlation Then and Now: A Sad Truth About SIEM
We Love What’s Broken … Yes, This Of Course Means SIEM! was originally published in Anton on Security on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Stories by Anton Chuvakin on Medium authored by Anton Chuvakin. Read the original post at: https://medium.com/anton-on-security/we-love-whats-broken-yes-this-of-course-means-siem-adcc9112bd64?source=rss-11065c9e943e------2


