2024-6-18 03:54:5 Author: securityboulevard.com(查看原文) 阅读量:7 收藏
In June 2023, a critical vulnerability (CVE-2023-34362) in the MOVEit Transfer file transfer software was exploited by adversaries, resulting in a series of high-profile data breaches. Despite the availability of patches, and the vulnerability being publicly known and actively exploited, many organizations failed to prioritize its remediation. This lapse allowed attackers to gain unauthorized access to sensitive data, causing substantial financial and reputational damage. This incident, amongst others, starkly highlights the urgent need to address Known Exploited Vulnerabilities (KEV) swiftly and effectively.
KEVs are an essential element of the cybersecurity framework, offering a prioritized list of vulnerabilities that are actively exploited in the wild. This critical information guides organizations to allocate their resources effectively, addressing the most imminent threats first. However, relying solely on KEV can present challenges, and a multifaceted approach is essential for comprehensive security.
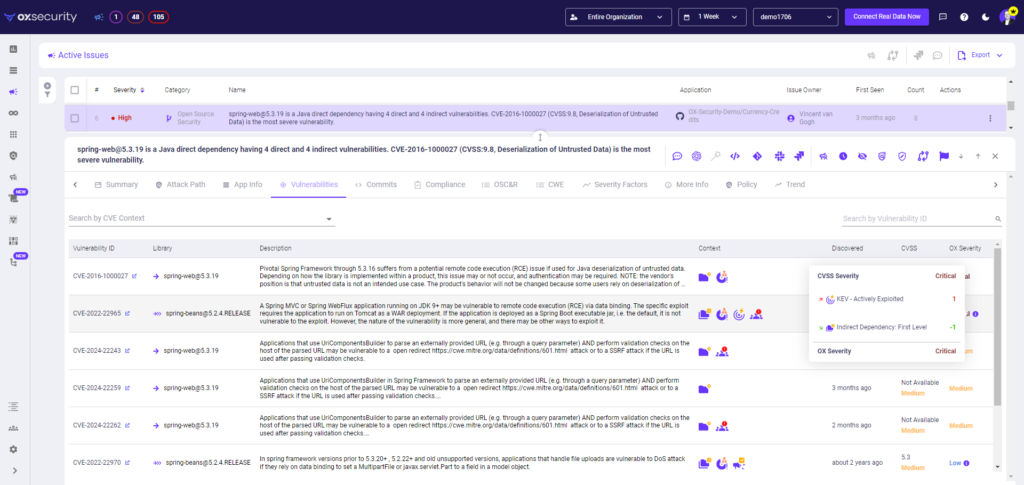
To navigate security complexities effectively, organizations need a multifaceted defense strategy. OX Security latest update integrates KEV with the Exploit Prediction Scoring System (EPSS) and enhanced CVSS matching. By merging KEV insights with predictive exploit data and detailed vulnerability assessments, the OX platform equips security teams with the tools to pinpoint and remediate the most pressing threats, ensuring robust defenses against vulnerabilities that are being actively being exploited in the wild.
Known Exploited Vulnerabilities: An Example
Imagine your organization is dealing with a backlog of vulnerabilities, each with varying degrees of severity. It’s challenging to know which to tackle first. This is where KEV comes into play. KEV focuses on vulnerabilities that are being actively exploited, offering a clear priority list based on real-world threat data.
Example in Action: During 2022, a critical vulnerability in Zoho’s ManageEngine (CVE-2022-47966) was identified as being actively exploited. This flaw allowed attackers to execute remote code due to improper input validation, leading to ransomware attacks and data theft in several organizations. Despite the availability of patches, many failed to prioritize this KEV, resulting in significant damage. By integrating KEV, OX Security ensures that such actively exploited vulnerabilities are prioritized, helping you avoid similar oversight and mitigate risks more effectively.
Key Benefits of Known Exploited Vulnerabilities (KVE) Integration:
-
- Immediate Threat Focus: With OX’s integration, you can quickly identify and address vulnerabilities that are currently being exploited in the wild.
- Resource Optimization: Allocate your security resources to tackle the most urgent threats, reducing the window of exposure.

What is Exploit Prediction Scoring System (EPSS)and It’s Advantages
While KEV helps address current threats, the EPSS adds a predictive layer, estimating the likelihood of future exploitation. EPSS uses historical data and machine learning to forecast which vulnerabilities are most likely to be targeted next, allowing you to get ahead of potential attacks.
Example in Action: Consider the “ProxyNotShell” vulnerabilities (CVE-2022-41040 & CVE-2022-41082) in Microsoft Exchange Server. In late 2022, these flaws allowed attackers to install web shells and exfiltrate data. Despite available mitigations, the lack of prioritization based on predicted exploitation led to widespread breaches. EPSS would have highlighted the high likelihood of these vulnerabilities being exploited, prompting earlier action. Integrating EPSS with KEV in OX Security provides a dual approach to managing current and future threats.
Advantages of EPSS Integration:
-
- Proactive Mitigation: Anticipate which vulnerabilities are likely to be exploited, enabling preemptive measures.
- Informed Decision-Making: Combine predictive analytics with real-time data for a comprehensive risk management strategy.

Enhanced CVSS Matching: Contextual Precision in Risk Assessment
CVSS scores provide a baseline for understanding the severity of vulnerabilities. However, traditional scoring often lacks the contextual relevance needed for effective prioritization. Our improved CVSS matching incorporates KEV and EPSS data, enhancing the precision of risk assessments.
Example in Action: In May 2023, a zero-day vulnerability in Fortinet’s FortiOS SSL-VPN (CVE-2023-27997) was exploited, leading to unauthorized network access through buffer overflow attacks. Despite advisories and patches, many organizations failed to recognize the immediate threat posed by this CVSS-rated vulnerability. By integrating KEV and EPSS data, OX Security’s enhanced CVSS matching provides a more accurate assessment, ensuring critical vulnerabilities are addressed swiftly.
Benefits of Enhanced CVSS Matching:
- Contextual Relevance: Augment CVSS scores with real-world exploitation data and predictive insights for more effective prioritization.
- Targeted Remediation: Focus on vulnerabilities that pose the greatest risk, streamlining your response efforts.
Discovery: Accurate Identification of Critical Threats
Effective vulnerability management begins with accurate discovery. The OX Security platform’s discovery capabilities now integrate KEV and EPSS data, ensuring precise identification of vulnerabilities that matter most.
Discovery Features:
- Advanced Scanning: Enhanced scanning techniques incorporate KEV and EPSS data, providing a comprehensive and relevant vulnerability discovery process.
- Continuous Updates: Stay informed about emerging threats with real-time updates, keeping your security measures up-to-date.
Analysis: Deep Insights for Effective Prioritization
Once vulnerabilities are discovered, in-depth analysis is essential for effective prioritization. Our platform delivers detailed risk profiles, integrating KEV, EPSS, and improved CVSS matching.
Analysis Highlights:
- Comprehensive Risk Profiles: Understand vulnerabilities from multiple dimensions, including current exploitation status and future risk predictions.
- Clear Prioritization: Receive actionable insights that guide you in addressing the most critical vulnerabilities first.

Response: Efficient and Effective Remediation
The final step in vulnerability management is response. OX Security’s platform offers robust tools to facilitate swift and effective remediation, ensuring vulnerabilities are addressed promptly.
Response Capabilities:
- Automated Remediation: Apply patches and fixes efficiently with automation, reducing time to resolution.
- Customizable Playbooks: Develop and implement response strategies tailored to your organizational needs.
- Seamless Integration: Ensure a unified response strategy with tools that integrate smoothly into your existing security infrastructure.
The Power of KEV: Essential but Not Sufficient
Identifying Known Exploited Vulnerabilities (KEV) is a critical component of any robust cybersecurity strategy. KEV highlights vulnerabilities that are being currently exploited in the wild, helping security teams prioritize immediate threats. However, focusing exclusively on KEV can lead to gaps in your security posture, as not all vulnerabilities listed may be equally critical to your specific environment, and some threats to your organization might not yet be recognized in the KEV system.
Example in Action: Using the “ProxyNotShell” example from above, if we consider how to integrate data from KEV into the vulnerability prioritization process, you can achieve a balanced approach and context-specific analysis.
A Nuanced Approach to KEV:
- Tailored Prioritization: While KEV repository provides a valuable list of actively exploited vulnerabilities, it’s essential to assess these against your specific environment. Some vulnerabilities flagged as KEVs might not pose a significant risk to your organization based on your infrastructure and threat landscape.
- Beyond the KEV List: Conversely, vulnerabilities not currently on the KEV list might be critical for your organization due to unique configurations, dependencies, or operational impacts. For instance, CVE-2022-47966 in Zoho’s ManageEngine may not be globally prioritized but could be critical for organizations deeply integrated with this tool.
Integrated Solution with OX Security
OX Security’s platform goes beyond merely identifying KEVs. By integrating the EPSS and improved CVSS matching, OX provides a more comprehensive risk assessment. This approach helps you prioritize vulnerabilities not only based on their exploitation status in the wild but also on their relevance and potential impact within your specific context.
Key Benefits:
- Context-Aware Prioritization: Combine KEV data with an understanding of your unique environment to prioritize vulnerabilities that truly matter to your organization.
- Balanced Risk Management: Address both actively exploited vulnerabilities and those that may not yet be exploited but are critical to your operations.
By adopting a nuanced view of KEV, supported by EPSS and enhanced CVSS matching, OX Security ensures you’re not just reacting to threats but proactively managing risk in a way that aligns with your organization’s specific needs.
Want to see how to enhance your AppSec strategy? Schedule a consultation with our team to see live data in action.
The post From Risk to Resolution: OX Security’s Integrations with KEV and EPSS Drive Smarter Vulnerability Prioritization appeared first on OX Security.
*** This is a Security Bloggers Network syndicated blog from OX Security authored by Boaz Barzel. Read the original post at: https://www.ox.security/kev-and-epss/
如有侵权请联系:admin#unsafe.sh

