2024-6-18 15:47:17 Author: www.netcraft.com(查看原文) 阅读量:10 收藏
Criminals are opportunists, ready to exploit any perceived weakness, from humanitarian efforts to presidential campaigns. Recently, Netcraft has been monitoring a series of attacks surrounding the Trump campaign, particularly following two developments: the May 21st announcement of crypto donations and the May 31st trial verdict that led to a huge surge in real donations, overwhelming the Trump campaign’s actual infrastructure.
Following these events, Netcraft has identified donation scams impersonating the Trump campaign, featuring dozens of malicious domains distributed in phishing and smishing campaigns. With millions of emails and texts sent by the real campaign, scammers are exploiting recent interest to trick would-be donors into visiting a lookalike domain.
Netcraft also used our proprietary peer-to-peer messaging reconnaissance to engage in a direct conversation with a “Trump National Committee” scammer, who revealed various points of actionable threat intelligence, including mule bank accounts, payment app details, email addresses, and more. In addition to collecting critical data that can be utilized to disrupt attacks and dismantle infrastructure, this dialogue with the scammers confirms a popular concern that criminals are leveling up and using AI to create better, faster, and more believable scams.
Let’s examine how quickly criminals deploy these campaigns, adapt to new information, and are getting better while they do.
Legitimate Crypto Support
As announced in late May, the Trump campaign accepts cryptocurrency donations via Coinbase Payments. This technology is provided through Coinbase and is available to any “federally accredited donor” to make payments via Ethereum-based cryptocurrencies or through balances held at Coinbase including Bitcoin and a large variety of more esoteric coins.
When the trial verdict was announced on May 31st, the Trump campaign immediately directed all incoming traffic to its site to the donation pages in order to capitalize on support from donors across the country. The campaign collected more than $50 million in the 24 hours following the verdict, but criminals also took note. Those behind these donation scams also identified the opportunity and immediately pivoted their strategy to mirror what was happening on the legitimate campaign site, with many direct impersonations of campaign resources.
Moving Fast and Smart
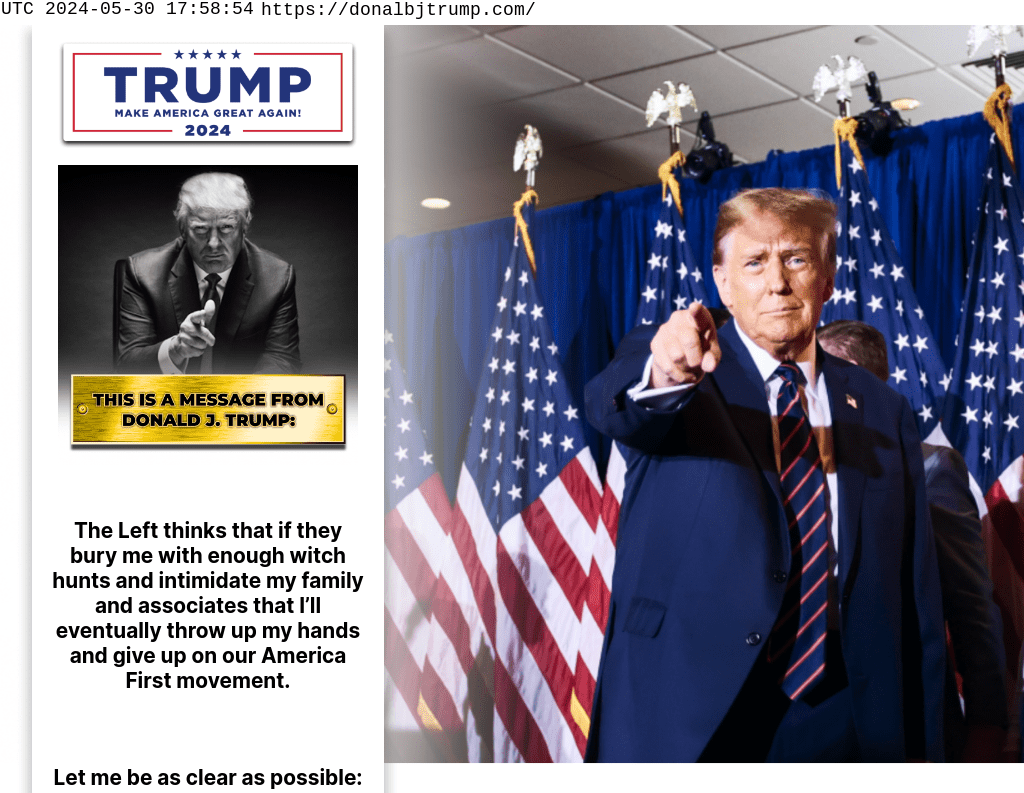
Shortly following the crypto announcement criminals had already taken notice, with various domains being registered the day following the announcement, including: donalbjtrump[.]com and doonaldjtrump[.]com. Among the fastest-acting criminals was the threat actor behind our first example donalbjtrump[.]com, which upon creation mirrored almost exactly the Trump campaign page in content and design.
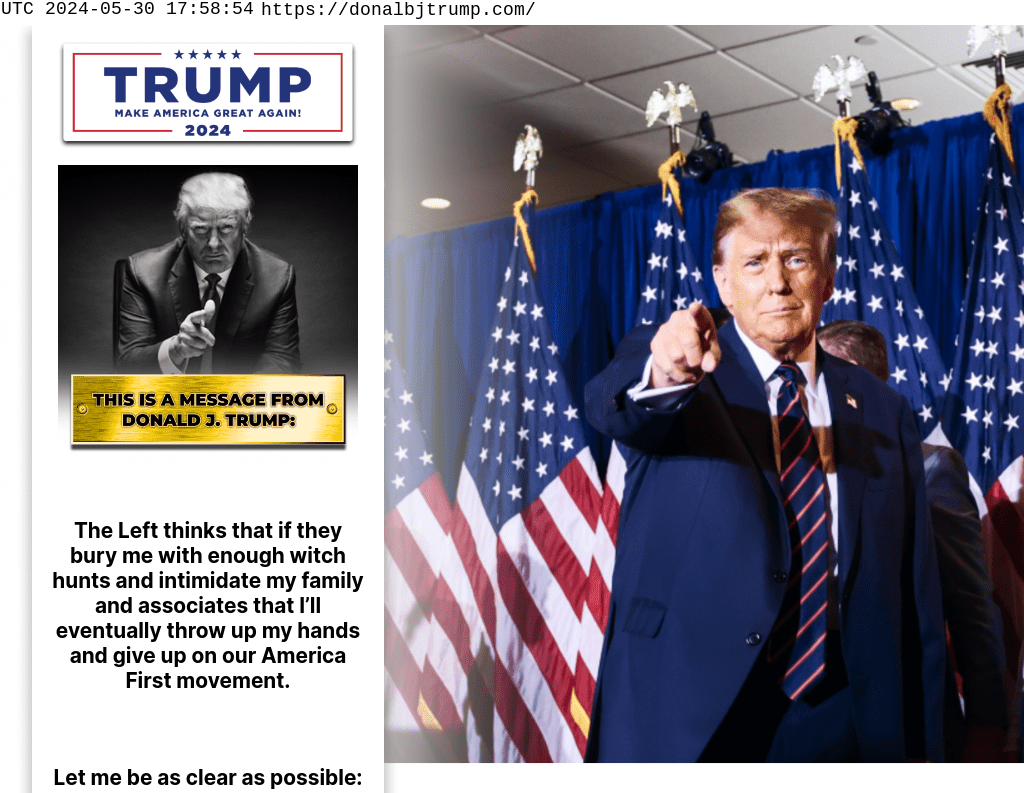
Original page hosted on donalbjtrump[.]com within days of campaign announcements
However, in addition to moving quickly, these scammers are actively monitoring the situation and making strategic adjustments to improve the scam. Initially, the site was created with the content featured in the screenshot above, however on May 31st, the day Trump’s guilty verdict was announced, this scammer adjusted quickly to mirror the “Never Surrender” narrative of the Trump campaign to take advantage of the urgency from Trump supporters and their potential victims. With the Trump campaign collecting more than $50M in a 24-hour period, there’s no telling how much might have been lured away by the criminals behind these scams.
On the left, you’ll see the authentic Trump campaign page, on the right is the fraudulent site that was adapted to match the Trump campaign
Dinner for Donations
Want to meet up with Trump for dinner at Mar-a-lago? This is your chance for just $2,000. Too good to be true? That’s because it is. This scam utilizes the exact layout of the campaign page but obviously steals resources, and in this instance, cash.
The figure on the left showcases the actual donation page, and the image of the fake site to the right adds the introduction to dinner with Trump.
Cashing Out
The donation scams use a variety of different techniques to replace the legitimate Coinbase Payments-based flow used by the Trump campaign, including phishing pages impersonating Coingate, and crypto payment flows using Plisio and Oxapay.
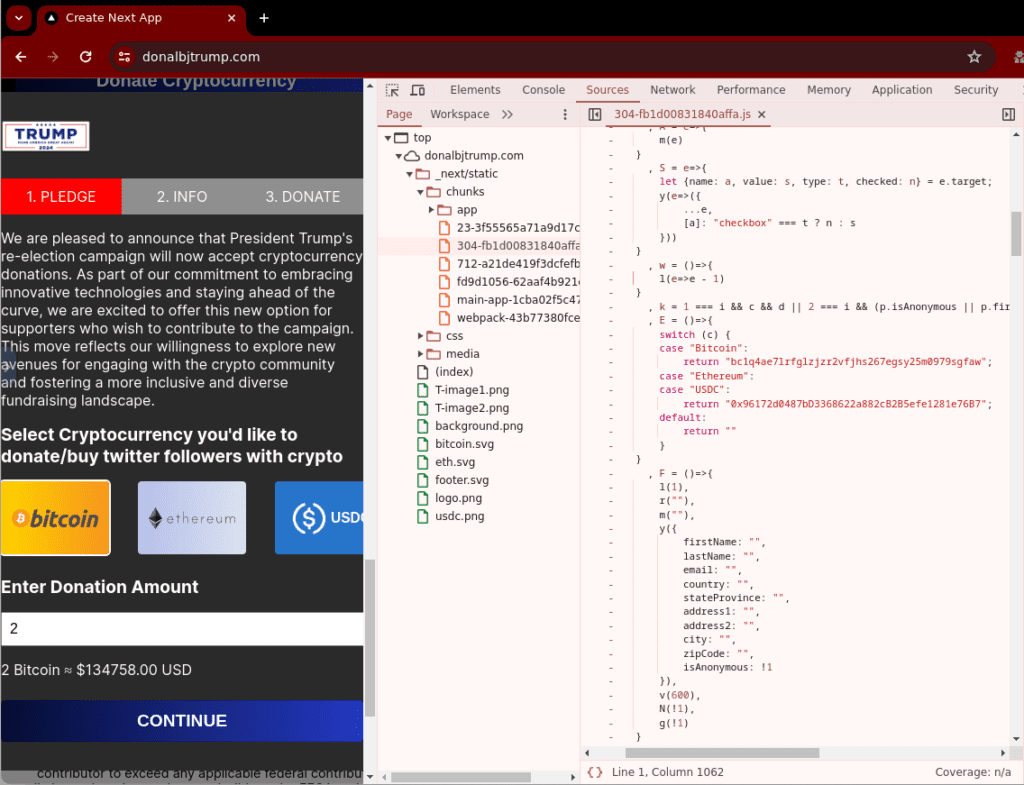
donalbjtrump[.]com contains fixed Bitcoin and USDC wallet addresses. At the time of writing, neither had received any transactions.
Netcraft has also seen donation scams that focus on traditional payment options, including those that selectively redirect back to the legitimate campaign if selecting non-cryptocurrency payment options.
This campaign reinforces the observation that criminals operating donation scams are quick to make use of current affairs to steal money from would-be donors and have no qualms about who or what they impersonate. This recently played out in the Gaza conflict with similar efforts to redirect donations to criminal threat actors, with impersonations playing on sympathies for either Israel or Palestine.
Leveling Up with AI
A common concern within the security landscape is the extent to which AI will level up threats targeting businesses and consumers – improving quality while allowing for increased scale. The peer-to-peer message thread with the Trump campaign scammer appears to confirm what many have feared.
A hallmark of P2P messaging scams is they are often riddled with spelling and grammar errors, at times making them simple to spot. However, in reviewing the back-and-forth dialogue between the scammer and Netcraft systems, these messages break from convention as they are very well structured, use proper English and grammar, contain nuanced language unique to the Trump campaign, as well as repetitive use of some key phrases. Analysis run on the messages reveals there is a very high likelihood the content was created using AI.
**This thread is still ongoing, so to protect the integrity of the data we have chosen to not share screenshots or specific language at this time.
Defending Against Impersonation
As phishing, fraud, and scams continue to increase, along with the added challenges presented by AI, it is critical to stay ahead of criminal innovation by leveraging new technologies to detect, disrupt, and take down threats across the internet. Netcraft’s extensive automation and impactful AI work around the clock to identify threats and deploy automated countermeasures on behalf of our customers – including some of the world’s largest and most trusted brands and governments.
To learn more about how Netcraft can help defend against attacks actively targeting your business, just like the one targeting the Trump campaign, please reach out. Learn more
如有侵权请联系:admin#unsafe.sh