
2024-6-18 22:11:0 Author: securityboulevard.com(查看原文) 阅读量:8 收藏
Earlier this month our expert takedown team responded to a bad actor that used link shortener services to obfuscate a link to a phishing page that impersonated one of our financial institution customers. The destination was a sign-in webpage presenting malicious content including our customer’s logo and log-in fields for harvesting the institution’s customers’ online banking credentials.
What’s notable in this case is that scammers did not use a well-known URL shortening service such as Bit.ly or TinyURL but either used “fraud-as-a-service-like” link shorteners purpose-built for deceptive activity or that they built themselves. With this article we hope to shed light on the continuing threat posed by URL shorteners, explain what some shortening service providers do to prevent abuse of their services, and provide additional information about this particular incident.
Shortened Phishing URLs Harvesting Banking Credentials
In this case, a fraudster targeted this financial institution’s customers via SMS messages in May and June of 2024. Those messages included short links such as kn8[.]site/n/FHaFb and vt7[.]site/e/QyWyu. In total so far, our team has facilitated the take down of five different domains used for link shortening used in this campaign.
Each of the shortened links redirected to either thforum-bo6visit[.]li or visi1-hnrs3[.]li. Both of those domains presented a fake log-in page impersonating our customer and using their logo. The destination domain did not in any way resemble our customer’s official domain name.
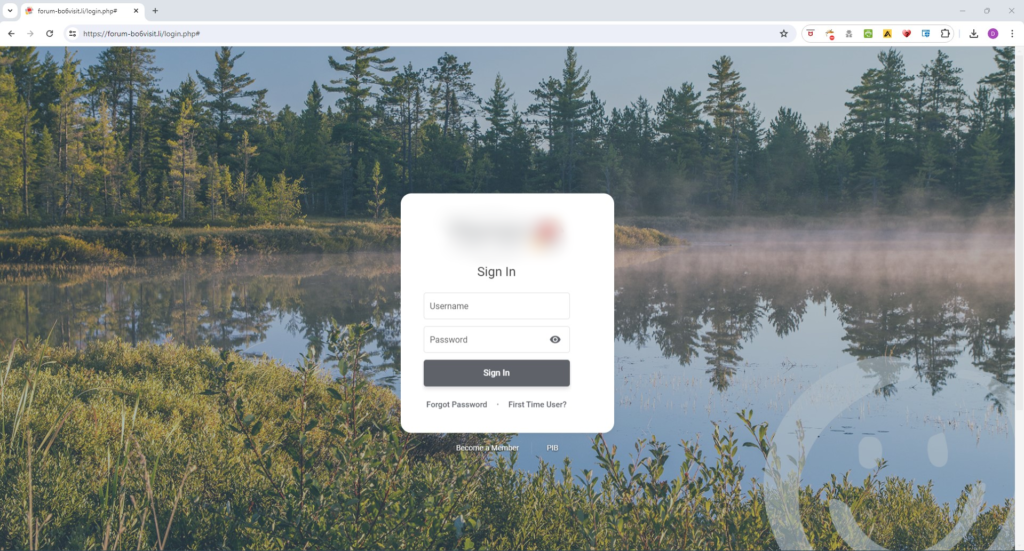
Link Shortener and Credential Harvesting Site Takedown
Originally, the domain registrar and reseller were slow to respond to our takedown team’s requests. Once they did reply, they claimed the domain names were deactivated. Unfortunately, despite these claims our team confirmed that the URLs remained accessible.
Because our mission-driven takedown services team prides themselves on their diligence, they also got in touch with the Switzerland Federal Council National Cyber Security Centre (NCSC) and the domain registry responsible for the .li (Liechtenstein) and .ch (Switzerland) country codes. After our team submitted reports to these organizations, the credential harvesting sites were completely deactivated in the domain name system. At this time DNS records no longer exist for thforum-bo6visit[.]li or visi1-hnrs3[.]li.
URL Shorteners Used as Part of this Incident
Each of these three-character URL-shortening domains exhibited similar patterns:
-
- Domain registered with Hostinger
-
- Domains registered on May 27, 2024, and updated on June 1, 2024
-
- Domains registered using a domain registration privacy service
-
- Followed a similar design template
-
- Websites lacked social media links
Upon additional investigation, we found other link shortening services with websites that also seemed to use the same design template. Those domains are:
-
- shortener[.]space
-
- shorter[.]gg
-
- tli[.]su
As of June 17, 2024, tli[.]su has been blocklisted by some wi-fi routers and Google Safe Browsing classifies it as “Some pages on this site are unsafe.” As of the same date, Google Safe Browsing classifies shortener.space and shorter[.]gg as “No unsafe content found.” Last week Google Safe Browsing listed both tli[.]su and shorter[.]gg as “Some pages on this site are unsafe” and contain “harmful content, including pages that try to trick visitors into sharing personal info or downloading software.”
Each of these URL shortening services looks a lot like another service found at amlink[.]pro. The Amlink site includes a link to a Facebook profile for Ainka Media and a link to a LinkedIn profile for Ainka Technology Solutions – a creative and software agency based in Vietnam. The LinkedIn profile lists the company as having 11-50 employees and a number of individuals’ profiles list Ainka as their employer. Ainka Technology Solutions also has a listing in Dun and Bradstreet’s Business Directory.
Ainka Technology Solutions does appear to be a legitimate business, but some inconsistencies and misspellings in links to their social media profiles do give us some pause. In addition, we could not find any reference to the Amlink shortening service on Ainka’s website, Facebook profile, or LinkedIn profile. Other than a robot mascot on both pages, there’s not a lot linking them.
The amlink[.]pro and what seems to be Ainka’s official website, ainkamedia[.]com, are registered under the same registrar (P.A. Viet Nam Company Limited). Ainkamedia[.]com was registered in March 2014 whereas amlink[.]pro was registered in September 2023. The Amlink domain redacts registrant information whereas the Ainka Media domain does not.
While we wouldn’t vouch for the legitimacy of Ainka Media or the Amlink service without additional research, it’s possible this is a legitimate business and service that the owners of shortener[.]space, shorter[.]gg, and tli[.]su simply cloned for their own purposes.
Abuse of Link Shortening Services
Bad actors have used URL shorteners to disguise malicious URLs for a long time. One of the first link shortening services was TinyURL launched in 2002, and it’s likely threat actors have been abusing such services for just as long.
Many popular link shortening services including TinyURL, RadiumOne Po.st, Ow.ly and Bitly put safety and security controls in place to stop abuse of their technology. For example, The Bitly Trust Center explains that their trust and safety team is dedicated to enforcing “…our policies through a combination of internal technologies, third-party vendors who specialize in abuse detection, trusted tech partners and NGOs.” This also includes an abuse reporting form and a link checker to view a shortened link’s destination.
Because such services have instituted controls to stop malicious activity, fraudsters explore other options – including building their own link shortening services.
The developer of an originally free URL shortening service, explained the challenges of fighting off bad actors and said the experience “…made me appreciate how quickly and diligently cybercriminals will look for new solutions. Because they keep getting banned everywhere else, they will be the first users to find your new solution. And they will try their best to exploit it — and usually a new project is easy to exploit because the founder hasn’t done all the anti-abuse work that mature solutions have.”
Last year, the Infoblox Threat Intelligence team reported on a threat actor they dubbed “Prolific Puma” operating a shadowy link shortening service for 18 or more months. The team believes Prolific Puma provides their link shortening service to other fraudsters and does not oversee the destination scams.
Tips for Combating Phishing URL Shortening
The most crucial thing to keep in mind is that you can’t trust that URL shortening services vet the destination of each and every URL shortened using their services. You should educate your employees and customers to approach shortened links with caution and default to distrust. They can easily lead to credential harvesting pages, malware, and other dangerous content.
You should also think hard about your organization’s use of shortened links. You don’t want to help train customers to click on them. If your marketing team absolutely must use shortened links, consider a service that allows you to brand those links with your domain name rather than the domains of the shortening service.
Fraudsters use short links to purposely obfuscate their scam pages. In some cases, phishing content is only displayed when the page is accessed via specific shortened links, otherwise the content appears to be benign. Because of this, detecting these scams can be a challenge. Even so, expanding daily internet monitoring to quickly identify phishing pages (including those behind shortened links) and catching them early, before anyone falls victim, is a crucial step forward.
This is where Allure Security in particular excels. Our AI-powered detection engine looks at more of the internet by analyzing tens-of-millions of websites each day. That consists of rendering any content in a browser and analyzing all of the components of that page with computer vision and natural language processing to identify impersonating content as a human would.
To see for yourself why Allure Security is so successful with this approach, request a demo today.
如有侵权请联系:admin#unsafe.sh

