Hacking APIs is an art; like any artist, the right tools make all the difference.
While curl has long been my trusty companion, HTTPie has become my go-to for API exploration and testing.
At least from the command line.
Its simplicity and power make it a joy to use, especially when diving deep into the intricacies of API vulnerabilities.
In this article, I’ll take you on a journey through the world of HTTPie, showcasing its strengths and demonstrating why it should be an essential part of your API hacking toolkit.
Get ready to discover a tool that will transform how you interact with APIs.
Let’s dive in!
WTF is HTTPie?
HTTPie is a command-line HTTP client designed for simplicity and ease of use. It allows developers and testers to interact with APIs in a human-friendly way.
What does that mean?
This means the CLI is designed to be intuitive, easy to use, and have readable syntax. It can automatically format and colorize JSON responses. It can save and reuse session data, such as cookies and auth tokens, across multiple requests. And it supports proxying so you can use it along with the BurpSuite Attack Proxy.
Installing HTTPie
Before we can start hacking APIs with HTTPie, we must install it on our system.
Whether you’re using Windows, macOS, or Linux, HTTPie offers a straightforward installation process. Follow the steps below to get HTTPie up and running on your machine.
Installing on macOS
For macOS users, the easiest way to install HTTPie is through Homebrew. If you don’t have Homebrew installed, you can get it from brew.sh.
1. Open your terminal.
2. Install HTTPie with the following command: brew install httpie
Installing on Linux
Linux users can install HTTPie using their package manager. Here are the commands for some popular distributions:
- Debian/Ubuntu:
sudo apt install httpie - Fedora:
sudo dnf install httpie - Arch Linux:
sudo pacman -S httpie
Installing on Windows
Windows users can install HTTPie via Chocolatey or Scoop. If you don’t have either of these package managers, you can install them from chocolatey.org or scoop.sh.
Using Chocolatey:
- Open Command Prompt or PowerShell as Administrator.
- Install HTTPie with the following command:
choco install httpie
Using Scoop:
- Open PowerShell.
- Install HTTPie with the following command:
scoop install httpie
Trying HTTPie Online
You aren’t forced to install HTTPie locally.
If you would rather try it out first, you can do so at https://httpie.io/cli/run.
HTTPie Basics
To get started, let’s look at some of the basic syntax.
Basic GET request
http GET httpbin.org/get
Basic POST request with JSON data
http POST httpbin.org/post name=Bob age=42
HTTPie also includes a CLI called https that can be used for TLS/SSL requests.
Setting query parameters
If you wish to add query parameters to a request, you use double equals (==) as a separator between a key/value pair:
http GET httpbin.org/get some-key==some-value
Setting headers
If you wish to add a header to a request, you use a colon (:) as a separator between a key/value pair:
http GET httpbin.org/get X-Some-Header:Some-Value
Setting JSON fields
HTTPie defaults to sending JSON in its requests. There are several ways to set properties. Consider this example:
http PUT httpbin.org/put \
name=Bob \ # String (default)
age:=42 \ # Raw JSON — Number
active:=true \ # Raw JSON — Boolean
roles:='["admin", "user"]' \ # Raw JSON — Array
tools:='{"HTTPie": "Yummy"}' # Raw JSON — Object
Controlling response output
One of the standout features of HTTPie is its ability to control and format the output, making it easier to read and analyze responses from APIs.
By default, HTTPie provides a beautifully formatted and colorized output highlighting different parts of the response, such as headers and body content. You can further control this output with various flags.
For instance, the --pretty flag allows you to specify how you want the output to be formatted, while the --print option lets you dictate exactly what parts of the HTTP exchange should be printed (e.g., request headers, response body, etc.).
Additionally, HTTPie supports JSON pretty-printing by default, making it a breeze to work with API responses.
This level of control ensures that you get precisely the information you need in the most readable format, enhancing your efficiency and effectiveness in API testing.
Output flags
The --print option (or -p for short) has several options you can use to control output:
- ‘H’ request headers
- ‘B’ request body
- ‘h’ response headers
- ‘b’ response body
- ‘m’ response metadata
You can combine them to tailor your output exactly as you want it. As an example, if you wanted to show only the request body, but also the response headers and body, you could use -pBhb.
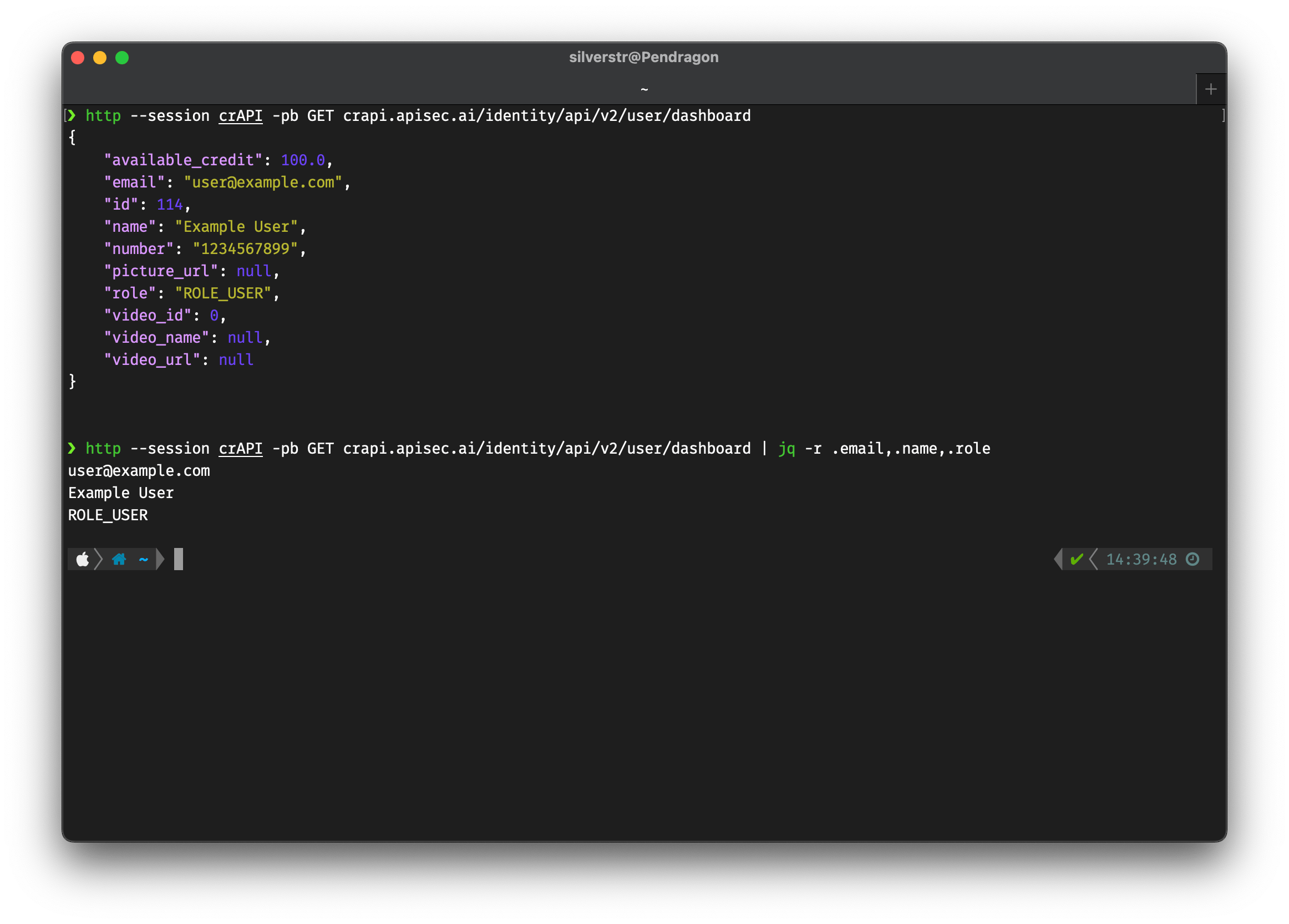
Using jq
You can further parse the JSON in a response with the use of jq.
Here is an example of extracting just the name, email, and role from the dashboard of OWASP crAPI:
http GET crapi.apisec.ai/identity/api/v2/user/dashboard | jq -r .name,.email,.role
Using sessions
HTTPie offers a powerful feature called sessions, which allows you to persist certain aspects of your HTTP interactions across multiple requests.
This is particularly useful for maintaining authentication tokens, headers, or other data that needs to be reused without manually including them in every request.
You can use the --session flag followed by a session name to create a session. For example, http --session=my_session POST https://api.example.com/login username=user password=pass will save the session details.
Subsequent requests can use this session with http --session=my_session GET https://api.example.com/profile, automatically including the stored cookies, tokens, and headers.
This feature streamlines repetitive tasks, reduces manual errors, and enhances your productivity by maintaining a seamless interaction flow with the API.

Constructing requests with offline mode
HTTPie also provides an offline mode, which is incredibly useful for constructing and testing requests without actually sending them.
This allows you to perfect your request syntax and structure before making live calls to the API.
To use offline mode, simply add the --offline flag to your command.
For example, http --offline POST https://api.example.com/resource name=example will display the constructed request without sending it.
This feature is convenient for debugging and ensuring your request is correctly formatted, including headers, JSON payloads, and query parameters.
By leveraging offline mode, you can confidently build and tweak your requests in a controlled environment, ultimately saving time and reducing potential errors when you go live.

Using HTTPie with Burp’s Attack Proxy
HTTPie makes it easy to route your requests through a proxy, which is particularly useful for capturing and analyzing traffic with tools like Burp Suite.
To use proxy mode, you can add the --proxy flag followed by the proxy URL.
For instance, if you’re running Burp Suite on your local machine with the default settings, you can proxy your HTTPie requests through it by running this:
http --proxy=http:http://127.0.0.1:8080 GET https://api.example.com/resource
This command will send the request through Burp Suite, allowing you to intercept, modify, and analyze the traffic.
By integrating HTTPie with Burp’s attack proxy, you can leverage Burp’s extensive suite of tools to perform security testing, identify vulnerabilities, and refine your API hacking techniques with greater precision and control.
If you wish to use this with SSL/TLS, you can ignore certificate errors with Burp’s self-signed cert with the following command:
https --proxy=https:https://localhost:8080 --verify no api.example.com/resource
Leveraging environment variables
If you do not wish to enter the proxy configuration for each request, you can set up environment variables for it.
export HTTP_PROXY=http://localhost:8080
export HTTPS_PROXY=https://localhost:8080
export NO_PROXY=localhost,example.comTIP: Be careful when using these variables. They are common names that are also used in other tools supporting proxying.
Conclusion
Hacking with HTTPie is a game-changer for developers and testers aiming to streamline their API exploration and testing processes. Its intuitive design, powerful features, and user-friendly command-line interface make it an invaluable tool for anyone working with APIs.
From simple installation across various platforms to advanced capabilities like session management, offline mode, and proxy support, HTTPie offers everything you need to interact with APIs efficiently and effectively.
Whether you’re constructing complex requests, parsing JSON responses, or leveraging tools like Burp Suite for deeper analysis, HTTPie provides the flexibility and control required for thorough API testing. By incorporating it into your toolkit, you’ll enhance your productivity, reduce manual errors, and ultimately become more adept at identifying and addressing API vulnerabilities.
So, what are you waiting for? Dive in and start hacking APIs with HTTPie today. It’s time to elevate your API testing game and make your interactions with APIs as smooth and efficient as possible.

Happy hacking!
One last thing…

Have you joined The API Hacker Inner Circle yet? It’s my FREE weekly newsletter where I share articles like this, along with pro tips, industry insights, and community news that I don’t tend to share publicly. If you haven’t, subscribe today at https://apihacker.blog.
The post Hacking APIs with HTTPie appeared first on Dana Epp's Blog.
*** This is a Security Bloggers Network syndicated blog from Dana Epp's Blog authored by Dana Epp. Read the original post at: https://danaepp.com/hacking-apis-with-httpie
如有侵权请联系:admin#unsafe.sh