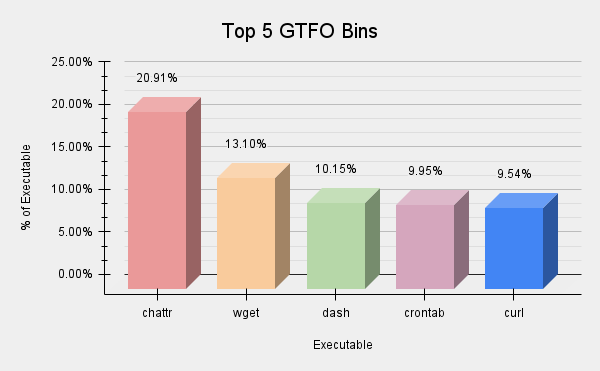
The Uptycs quarterly cyber threat bulletin provides insights into the current threat landscape. This intel is derived from our threat intelligence systems, sources, and a world-class threat research team, which builds and proactively monitors the latest hybrid cloud security TTPs (Tactics, Techniques, and Procedures). Organizations can use this cyber threat bulletin to evaluate and develop a more robust detection and protection posture against the latest Linux and container-based threats. CVE-2024-1086 - Use-After-Free Vulnerability in the Linux kernel's Netfilter The vulnerability identified as CVE-2024-1086 affects various major enterprise Linux distributions, including Debian, Ubuntu, Red Hat, Fedora, Amazon Linux, Oracle Linux, Rocky Linux, and others, depending on their specific configurations and patch levels. As of now, most major Linux distributions have released updates addressing this vulnerability. The issue originates from a flaw in the nf_tables component within the Linux kernel's netfilter packet-filtering framework. Netfilter chains multiple rules for packet processing, using a verdict value after each rule to decide whether to continue processing or drop the packet. A reverted commit in the netfilter code caused the nf_hook_slow function (in core.c) to mistakenly assume that the upper 16 bits of NF_DROP verdicts contain a valid error number (such as -EPERM or -EHOSTUNREACH) or 0. Contrarily, the nft_verdict_init() function interprets the verdict as NF_DROP, leading to packet deallocation in the nf_hook_slow() function. This results in the verdict appearing as NF_ACCEPT later on, causing the packet to undergo further processing and ultimately leading to a double-free vulnerability. This vulnerability enables attackers with initial access to a system to escalate their privileges, potentially gaining root access, which can result in unauthorized data access, service interruptions, and even complete system takeovers. The US Cybersecurity and Infrastructure Security Agency (CISA) has added this vulnerability to the Known Exploited Vulnerabilities (KEV) catalog. This clearly underscores the severity of CVE-2024-1086. Utilizing Uptycs EDR, equipped with YARA process scanning, we have identified the most prevalent malware families across Linux and Docker-based targeting platforms. The top techniques/tactics triggered by malware samples, aligned with the MITRE ATT&CK framework, are Ingress Tool Transfer (T1105), Hide Artifacts (T1564), Unix Shell (T1059.004), Cron (T1053.003), Disable or Modify Tools (T1562.001) Figure 1 depicts the prevalence of these observed ATT&CK technique IDs. Figure 1 – Observed ATT&CK technique IDs "Living off the Land" is a detection evasion technique. Malicious samples often utilize built-in target operating systems utilities in their attack sequences. Across Linux and Docker based platforms, these utilities correspond to our replication systems' tactics. This quarter, we focused more on Linux Utilities also known as GTFOBins, with Chattr being the most abused Linux utility, frequently observed in Mirai malware attacks. Figure 2 shows the top five Linux utilities misused by malware, including their prevalence. Figure 2 – Top five Linux utilities abused by malware Utilizing Uptycs EDR, equipped with YARA process scanning, we have identified the most prevalent malware families across Linux and Docker-based targeting platforms. Our research team has enhanced our platform with comprehensive TTPs and YARA coverage for these malware processes. Uptycs customers can now access detailed toolkit profiles of this malware when detections are triggered. For this cyber threat bulletin, ere are the top malware identified across Linux and Docker-based targeting platforms: Mirai Mirai is a piece of malware that infects IoT devices and is used as a launch platform for DDoS attacks. Two recently disclosed security flaws in Ivanti Connect Secure (ICS) devices are being exploited to deploy Mirai malware. The first vulnerability is an CVE-2023-46805 is an authentication bypass flaw, while the other CVE-2024-21887 is a command injection vulnerability, thereby allowing an attacker to chain the two into an exploit chain to execute arbitrary code and take over susceptible instances. Figure 3 – Uptycs XDR detection of Mirai malware Gafgyt Gafgyt, also known as BASHLITE, is malware that infects Linux architecture operating systems to launch a DDoS (distributed denial of service) attack. In the latest variants of Gafgyt, it downloads and executes the script file from an attacker-controlled server website. Later, it gets the compromised target IP and architecture information, which it concatenates into a string that is part of its initial connection message. Then, the Gafgyt establishes a connection with its C2 server, the malware receives a continuous 'PING' command from the server to ensure persistence on the compromised target. Figure 4 – Uptycs XDR detection of Gafgyt malware Linux systems run many of the most critical operations behind organization servers. Consequently, ransomware operators have intensified their focus on targeting Linux systems. In this quarterly cyber threat bulletin, we have included several new and emerging ransomware trends. A new Linux variant of the "TargetCompany" ransomware family has started targeting VMware ESXi environments using a custom shell script to deliver and execute payloads. This ransomware variant makes sure that it has administrative privileges before continuing the malicious routine. To download and execute the ransomware payload, the threat actor uses a custom script that can also exfiltrate data to two separate servers, likely for redundancy in case of technical issues with the machine or if it gets compromised. Once on the target system, the payload checks if it runs in a VMware ESXi environment by executing the 'uname' command and looking for 'vmkernel'. Next, a 'TargetInfo.txt' file is created and sent to the C2 server. It contains victim information such as hostname, IP address, OS details, logged-in users and privileges, unique identifiers, and details about the encrypted files and directories. RansomHub ransomware operation is using a Linux encryptor designed specifically to encrypt VMware ESXi environments in corporate attacks. RansomHub is a ransomware-as-a-service (RaaS) operation launched in February 2024, featuring code overlaps and member associations with ALPHV/BlackCat and Knight ransomware, having claimed over 45 victims across 18 countries. Unlike RansomHub's Windows and Linux versions that are written in Go, the ESXi version is a C++ program likely derived from the now-defunct Knight ransomware. The cyber criminals are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber, also known as C3RB3R ransomware. The attacks leverage CVE-2023-22518, a critical security vulnerability impacting the Atlassian Confluence Data Center and Server that allows an unauthenticated attacker to reset Confluence and create an administrator account. Cerber Ransomware consists of three highly obfuscated C++ payloads, compiled as a 64-bit Executable and Linkable Format (ELF) and packed with UPX. Akira emerged in March 2023 and quickly gained notoriety after targeting victims across various industry verticals worldwide. The group's ransomware developers had also created and deployed a Linux encryptor to target VMware ESXi virtual machines widely used in enterprise organizations. Akira operators obtain initial access to organizations through a virtual private network (VPN) service without multifactor authentication (MFA) configured, mostly using known Cisco vulnerabilities CVE-2020-3259 and CVE-2023-20269. Akira also uses a double-extortion model and encrypts systems after exfiltrating data. New Threat Detected: Inside Our Discovery of the Log4j Campaign and Its XMRig Malware Central to this cyber threat bulletin is that the Uptycs Threat Research Team has uncovered a large-scale, ongoing operation within the Log4j campaign. Initially detected within our honeypot collection, upon discovery, the team promptly initiated an in-depth analysis to delve into the complexities of this dynamic campaign. The threat research team has ascertained that this campaign is active, with over 1700+ dedicated IPs implicated in its operations. Upon analysis, it has been determined that the ultimate objective of the campaign is to deploy an XMRig cryptominer malware onto the targeted systems. Read more about ongoing Log4j attack Beware of Fake PoC Repositories on GitHub: A Pay4PoC Campaign A recent encounter with a supposed Proof of Concept (PoC) on GitHub for CVE-2024-3094 (a newly disclosed XZ library vulnerability) serves as a stark reminder of the dark side of open-source contributions. The repository claimed to offer a PoC for the XZ vulnerability. It also directed users to a link within the README.md file to download exploit files. Further in the blog, it explains the impact of the exploiting vulnerability. Read more about Pay4PoC Campaign Navigating the XZ Utils Vulnerability (CVE-2024-3094): A Comprehensive Guide The Uptycs research team shared an awareness report on the emergence of four new container vulnerabilities collectively dubbed Leaky Vessels. These vulnerabilities exploit the runC and BuiltKit components of Docker container environments. In the blog, researchers said that Uptycs' enhanced detection and response capabilities allow users to catch privilege escapes and use remediation actions to kill any container process that is running with these vulnerabilities. Details about XZ vulnerability "Transparent Tribe", a Pakistan-based actor has been linked to a new set of attacks targeting Indian government, defense, and aerospace sectors using cross-platform malware written in Python, Golang, and Rust. The group employed cross-platform programming languages, open-source tools, and abused web services for command-and-control and exfiltration. Attack chains mounted by the group involve the use of spear-phishing emails to deliver payloads using malicious links or ZIP archives, particularly focusing their efforts on distributing ELF binaries due to the Indian government's heavy reliance on Linux-based operating systems. The infections culminated in the deployment of three different versions of GLOBSHELL, a Python-based information-gathering utility that was reported in connection with attacks targeting the Linux environment within Indian government organizations. Also deployed is PYSHELLFOX to exfiltrate data from Mozilla Firefox. UNC3886, a suspected China-nexus cyber espionage actor that has targeted prominent strategic organizations on a global scale. UNC3886 has employed several layers of organized persistence for redundancy to maintain access to compromised environments over time. The threat actor makes use of publicly available rootkits like REPTILE, MEDUSA and SEAELF for long-term persistence. A suspected Pakistan-based threat actor named UTA0137 has been linked to a cyber espionage campaign targeting Indian government entities in 2024. UTA0137 actors make use of exclusive malware called DISGOMOJI that's written in Golang and is designed to infect Linux systems. It is a modified version of the public project Discord-C2, which uses the messaging service Discord for C2, making use of emojis for its C2 communication. The attack chains commence with spear-phishing emails bearing a Golang ELF binary delivered within a ZIP archive file. The binary then downloads a benign lure document while also stealthily downloading the DISGOMOJI payload from a remote server. North Korea-aligned state-sponsored actors known as the Lazarus Group have been attributed to a new campaign aimed at Linux users. The attack chain is initiated by delivering a fake HSBC job offer as a decoy within a ZIP archive file that's then used to launch a Linux backdoor named SimplexTea distributed via an OpenDrive cloud storage account. The backdoor, written in C++, bears similarities to BADCALL, a Windows trojan previously attributed to the group. ExCobalt cyber threat actors which target Russian organizations by using a Golang-based backdoor known as GoRed. ExCobalt focuses on cyber espionage and includes several members active since at least 2016 and presumably once part of the notorious Cobalt Gang. Initial access to environments is facilitated by taking advantage of a previously compromised contractor and a supply chain attack, wherein the adversary infected a component used to build the target company's legitimate software, suggesting a high degree of sophistication. The modus operandi entails the use of various tools like Metasploit, Mimikatz, ProcDump, SMBExec, Spark RAT for executing commands on the infected hosts, and Linux privilege escalation exploits. For this cyber threat bulletin, the key vulnerabilities/exploits seen across Linux and container-based platforms are as follows. Incident response teams should rigorously investigate the parent processes responsible for triggering the execution of key utilities across different operating systems: To enhance security against malware attacks, organizations are recommended to follow these cyber hygiene best practices: Implementing these practices can significantly strengthen an organization’s defense against various cyber threats. As we wrap up the Uptycs quarterly cyber threat bulletin for Q2 2024, it's clear the sophistication of cyber threats continues to increase, highlighting a critical need for advanced cybersecurity tools and strategies. This quarter has demonstrated the ingenuity of malware evolution and the emergence of new vulnerabilities and brought to light the relentless and innovative tactics employed by threat actors. Our in-depth analysis throughout this cyber threat bulletin underscores the indispensable role of sophisticated cybersecurity solutions in today’s digital landscape. To counter these threats effectively, organizations must understand the latest adversarial trends and equip themselves with the most advanced defenses. At Uptycs, our commitment to empowering organizations with cutting-edge security insights and solutions is unwavering. We strive to ensure that our clients are well-prepared and resilient against the multifaceted cyber threats they face. We remain at the forefront of threat intelligence, offering actionable insights and robust tools to help secure the digital frontier. We encourage our readers to stay informed and proactive, making cybersecurity an integral part of their operational ethos. Thank you for placing your trust in Uptycs. Together, we are building a more secure and resilient digital future.Q2 2024 Cybersecurity Insights: In-depth Threat Analysis and Trends
Critical Alerts
Techniques Used in Malware Samples

Commonly Abused Commands and Utilities
Linux Utilities Abused By Malware

Top Prevalent Malware Families in the Wild
Linux Malware


Trending Linux Ransomware
Q2 Threat Research Articles
Q2 Focus on Top Threat Actors
Key Vulnerabilities/exploits
General Recommendations
Conclusion
Uptycs Quarterly Cyber Threat Bulletin Q2 2024: Key Insights
2024-7-2 20:57:59 Author: www.uptycs.com(查看原文) 阅读量:7 收藏
2024-7-2 20:57:59 Author: www.uptycs.com(查看原文) 阅读量:7 收藏
文章来源: https://www.uptycs.com/blog/uptycs-quarterly-cyber-threat-bulletin-q2-2024
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh