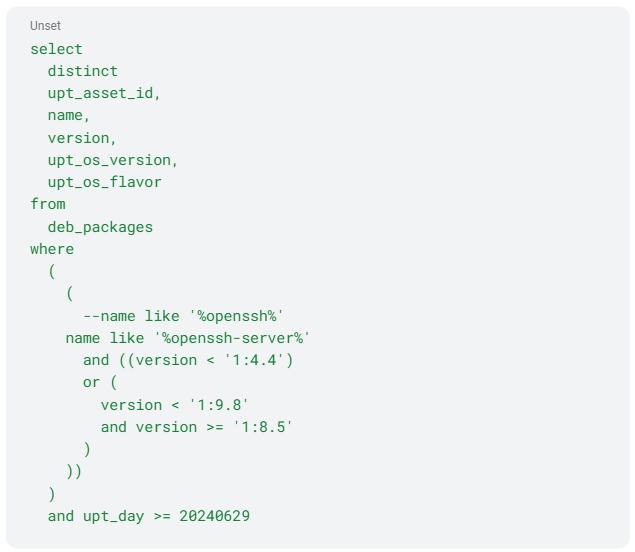
A new OpenSSH vulnerability has been detected. Customers running Uptycs can use these queries to identify all impacted assets immediately. Uptycs has already pushed automated vulnerability indicators to our customers, however, the sync process can take 24 hours for some customers, depending on their specific configuration. Once the vulnerability indicators are in place, the impacted assets will show up in the Uptycs vulnerability dashboards and reports. For identifying Debian packages (Global Query): For identifying RPM packages (Global Query): CVE-2024-6387, known as the “RegreSSHion” vulnerability, is a critical security flaw and OpenSSH vulnerability affecting various OS platforms and OpenSSH versions. This vulnerability poses a significant threat to secure communications, emphasizing the need for immediate attention and remediation by affected users and administrators. This OpenSSH vulnerability is already assumed to be affecting a significant number of computer systems running the affected OpenSSH software version. The vulnerability has been present since October 2020 (OpenSSH 8.5p1) and was patched as of version 9.8p1 of OpenSSH. Systems that are impacted and directly connected to the internet with SSH publicly exposed should be prioritized for patching, while internal systems that are impacted should be secondary to public-facing systems for patching. The researchers who reported this vulnerability have also indicated that successfully exploiting these vulnerabilities requires a significant level of complexity, exploitation can take about 10,000 attempts on x86 (32-bit) before a successful compromise occurs. Uptycs notes that they have not yet been published in CISA’s KEV list, we are urging all our customers, and the wider community, to proactively patch this vulnerability given the threat it could present to allow threat actors to compromise organizations. The RegreSSHion OpenSSH vulnerability impacts multiple operating systems that utilize OpenSSH for secure shell (SSH) operations. The affected platforms include: Specifically, the vulnerability has been identified in OpenSSH versions 8.5p1 and prior to 9.8p1. Version 9.8p1 is not considered vulnerable. Users running these versions should prioritize upgrading to the latest patched release provided by OpenSSH maintainers. To manually determine if your system is vulnerable to CVE-2024-6387, follow these steps: To mitigate the risk posed by CVE-2024-6387, take the following actions: By promptly addressing CVE-2024-6387, organizations can safeguard their systems against potential exploits and maintain the integrity of their secure communications. For more detailed information and updates, refer to official security advisories from OpenSSH and your OS vendor. Ubuntu has released patches for the following affected systems. Source: https://ubuntu.com/security/CVE-2024-6387 RedHat have indicated that OpenSSH on Red Hat Enterprise Linux 9 is impacted and requires patching, while Red Hat Enterprise Linux 6, 7 and 8, are not affected. Source: https://access.redhat.com/security/cve/CVE-2024-6387 Debian has provided a Security Advisory for Debian Bookmark and Debian Trixie that are impacted by the vulnerability. Source: https://security-tracker.debian.org/tracker/CVE-2024-6387 Amazon had indicated that Amazon Linux 2023 systems running OpenSSH are impacted, Amazon Linux-1 and Amazon Linux-2 Core are not affected. Source: https://explore.alas.aws.amazon.com/CVE-2024-6387.html SUSE have indicated that OpenSuse Leap 15.6 systems running OpenSSH are impacted, while other OpenSuse versions are still being investigated for any impact. Source: https://www.suse.com/security/cve/CVE-2024-6387.htmlVulnerability Detection


Understanding CVE-2024-6387: The RegreSSHion Vulnerability
Affected OS Platforms and OpenSSH Versions
Identifying the RegreSSHion Vulnerability Manually
Mitigation and Remediation
OS Vendor Updates
Updates from Ubuntu Security Advisory

Update from RedHat Security Advisory

Update from Debian Security Advisory

Updates from Amazon Linux

Updates from OpenSuse Linux
OpenSSH Vulnerability: CVE-2024-6387 Explained
2024-7-2 20:28:17 Author: www.uptycs.com(查看原文) 阅读量:65 收藏
2024-7-2 20:28:17 Author: www.uptycs.com(查看原文) 阅读量:65 收藏
文章来源: https://www.uptycs.com/blog/openssh-vulnerability-cve-2024-6387-details
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh