2024-7-4 19:19:6 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
Let’s discuss passwords and identity security. By entering a password that only you know, you are in theory “proving” to a system that you are who you claim to be. They have been widely used in the IT/OT world for a very long time – arguably too long.
To make passwords a little more secure, some organizations have a policy regarding the complexity and frequency of password changes. This is why there are solutions that focus on detecting password hygiene issues or similar alerts.
What Are the Different Password Hygiene Issues?
Password hygiene refers to the practice of creating, managing and protecting passwords. It consists of guidelines and best practices designed to reduce the risk of unauthorized access or compromised credentials. The following are some common password hygiene issues:
- Weak Passwords: The use of simple, easily guessable passwords; for example, “123456” or “password”. These passwords are easy to crack as they are short and lack the complexity of mixing letters, numbers, and special characters.
- Duplicate or shared passwords: Using the same password across multiple systems/accounts increases the risk if one system/account is compromised.
- Old passwords: Not regularly updating passwords might allow an attacker enough time to guess the password, or lead to prolonged exposure if a password is compromised.
Is Detecting Bad Password Hygiene the Right Approach?
Both yes and no. In theory, alerts are a good thing, but organizations should not solely focus on detection and reacting to alerts. Having more alerts to review every day is not always valuable, and retrospective detection alone could be too little too late, as the attacker might have already taken advantage of them.
Additionally, even with great password hygiene, malicious actors can still obtain credentials without your knowledge. Even a strong password that has not been shared nor found on the dark web could be compromised through phishing or tools like Mimikatz.
Assume passwords will be compromised and take a different approach to protecting identities – one that prioritizes protection. The key is to ensure that even if an attacker has obtained valid credentials, they won’t be able to use them for malicious activity like performing lateral movement. In short, don’t just focus on detection – focus on protection.
Protection is Better
Your identity security strategy should be built around focusing on the protection of your identities, rather than simply adding more alerts.
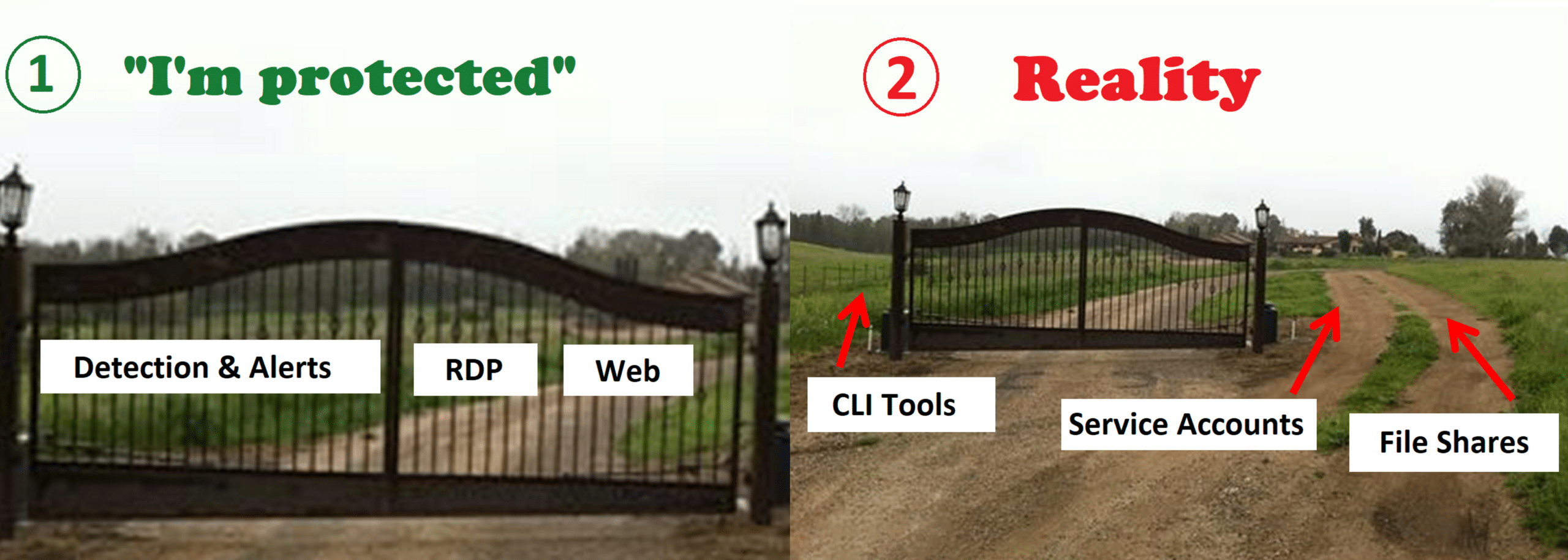
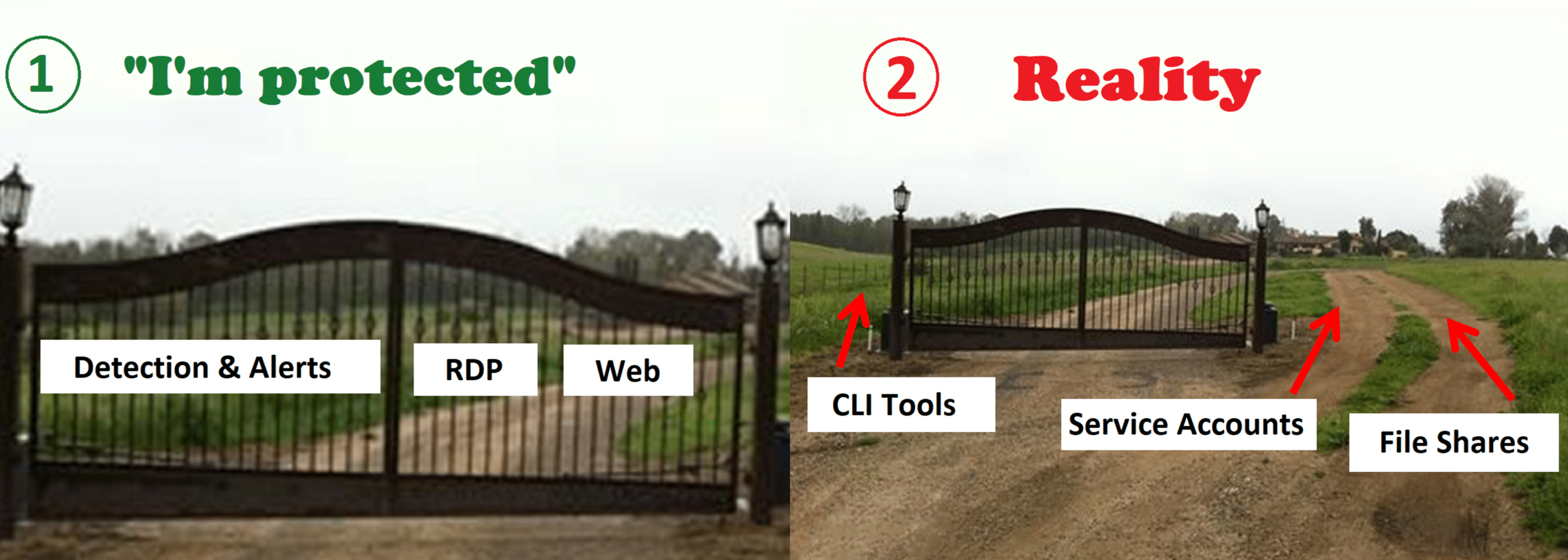
For human accounts, this could be strong MFA and conditional access controls, even for interfaces that were considered “unprotected” like CLI tools or file shares. So even if an attacker attempts to use compromised credentials with these interfaces, they will face another layer of security.
Don’t forget about Non-Human Identities (NHI)
NHI and Active Directory service accounts must also be protected. Their activity is usually automated and based on machine-to-machine communication. It is common for non-human identities to have elevated privileges or even administrative access depending on each vendor’s requirements. At scale, this could be a lot. Compromised service accounts can be used to perform a variety of malicious activities, such as running lateral movement for the purpose of deploying ransomware.
Some organizations are trying different ways to secure service accounts, their passwords, and their activity in the network. Even so, an attacker could gain service account credentials using other methods or tools.
How Can You Protect Service Accounts?
Organizations should implement proactive protection methods based on security controls tailored for service accounts at scale.
When choosing a solution for service account management and protection, the following features should be considered:
- Full visibility – You should be able to map all your service accounts based on their actual behavior on the network. This will allow admins to automatically identify them – even those you didn’t know existed – and provide complete visibility into their behavior patterns.
- Behavior analysis- You should be able to analyze their dependencies and their repetitive authentication activities within the domain, as well as synchronize with your CMDB to enrich knowledge.
- Proactive protection- Most importantly you should be able to create policies to place a “virtual fence” around your service accounts at scale, so even a compromised service account won’t be able to move laterally within the network. It’s important to only allow it to do what it is supposed to do for its functionality. For example, a database service account should only be used to authenticate to the DB app servers.
From Detection to Protection: Enhancing Identity Security
An identity security strategy with protection as the primary focus is the recommended approach to ensure the security of your users and service accounts against malicious actors. Implementing strong MFA (such as number-matching or phishing-resistant methods like FIDO2) for human accounts to access even traditionally “unprotectable” interfaces will significantly enhance security. For service accounts, virtual fencing techniques offer robust protection at scale by tightly controlling and monitoring machine-to-machine activities.
The bottom line is that you should focus more on protective security controls and not solely on retrospective detection alerts. To learn how Silverfort can help you focus on protection and meet your identity security needs, request a demo here: https://www.silverfort.com/request-a-demo/
The post Beyond Passwords: Why Trusting Password Hygiene Isn’t Enough appeared first on Silverfort.
*** This is a Security Bloggers Network syndicated blog from Silverfort Blog - Cyber Security News authored by Zev Brodsky. Read the original post at: https://www.silverfort.com/blog/beyond-passwords-why-trusting-password-hygiene-isnt-enough/
如有侵权请联系:admin#unsafe.sh