2024-7-5 22:0:0 Author: securityboulevard.com(查看原文) 阅读量:5 收藏

The Network and Information Systems Directive 2 (NIS2) is sweeping legislation designed to improve the cybersecurity of network and information systems in the European Union (EU). The new directive was released to keep up with an increasingly complex cybersecurity threat landscape. NIS2 builds upon its predecessor, NIS1, but with an expanded scope and more stringent requirements for member states and organizations.
With NIS2’s October 17, 2024 implementation date approaching fast, businesses and institutions need to understand the implications of the directive and take proactive steps to ensure compliance.
In this article, we’ll explain what steps you should take to get ready for the NIS2 deadline, so you can prepare for most of the NIS2 requirements. Along the way, we’ll also show you how to make NIS2 preparation faster and easier.
Key differences between NIS1 and NIS2
One way to better understand NIS2 is to compare it to its predecessor, NIS1. Some key differences between NIS1 and NIS2 include:
Broadened scope
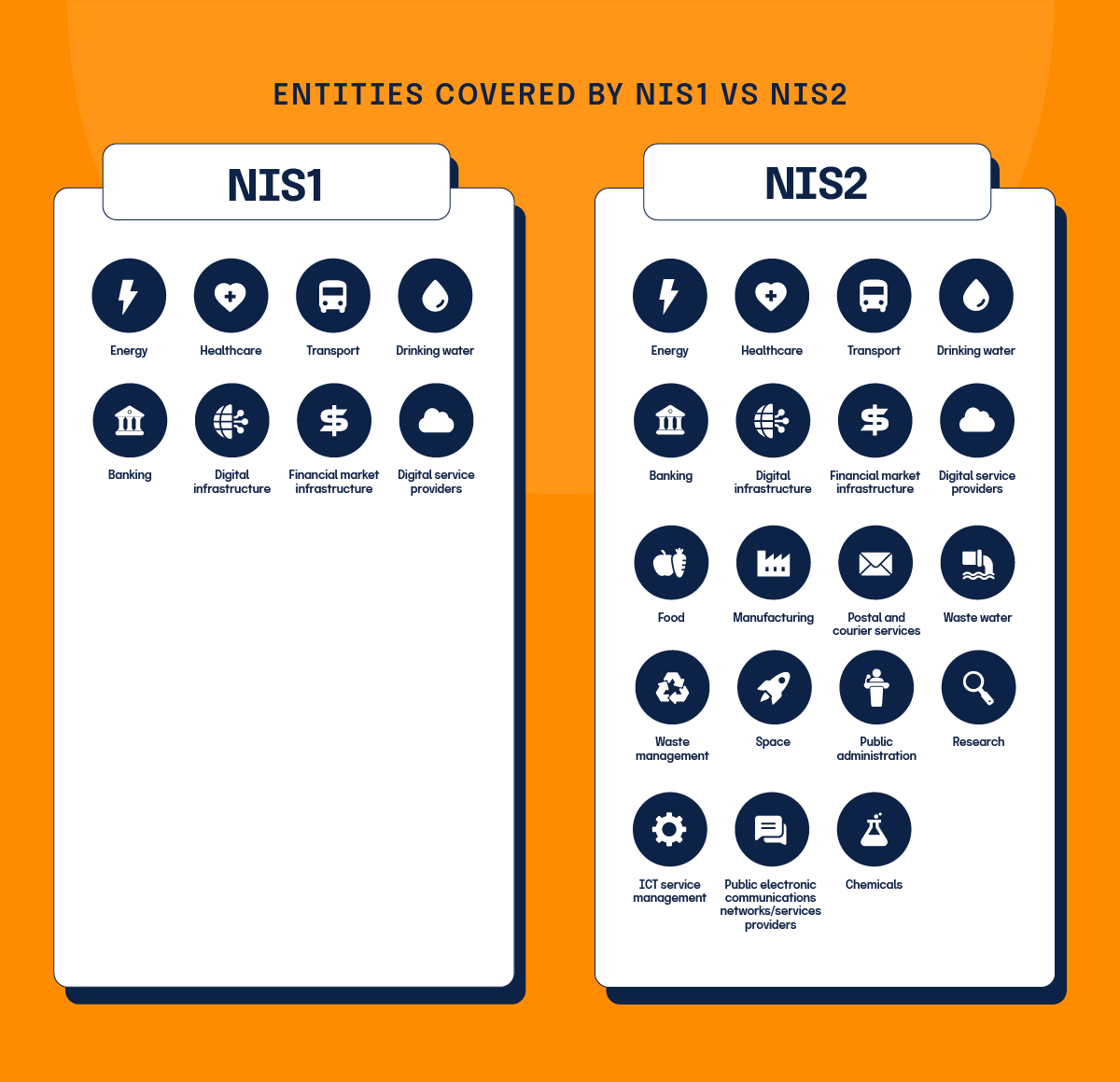
NIS2 expands the list of sectors and services that fall under its purview. While NIS1 focused primarily on essential services such as energy, transport, and healthcare, NIS2 includes additional sectors such as public administration, space, and digital infrastructure.
Enhanced obligations
NIS2 introduces more stringent security requirements for organizations, including mandatory risk management measures, incident reporting, and supply chain security.
Increased accountability
The directive places greater emphasis on accountability, requiring senior management to be directly involved in cybersecurity governance and decision-making.
Stronger enforcement
NIS2 provides for more robust enforcement mechanisms, including higher penalties for non-compliance and the establishment of a new European Cybersecurity Competence Centre to coordinate efforts.
What sectors are included in NIS2?
As mentioned, the scope of NIS2 is much broader than that of NIS1. The industries called to compliance include ‘essential’ and ‘important’ entities.
Essential entities
Essential entities provide services which are considered crucial for societal functions, economy, public health, and safety. Any disruption in their services would have significant negative consequences. Essential entities are subject to more stringent cybersecurity and reporting requirements compared to important entities. Essential entities include:
- Energy
- Healthcare
- Transport
- Drinking water
- Banking
- Digital infrastructure
- Financial market infrastructure
- Digital service providers
Important entities
Important entities, while still crucial, do not have as high a level of criticality as essential entities. The impact of a disruption in their services would be significant but not as severe as that of essential entities. While important entities still need to comply with NIS2, the requirements are not as strict as those for essential entities. Important entities include:
- Food
- Manufacturing
- Postal and courier services
- Waste water
- Waste management
- Public electronic communications networks/services providers
- Public administration
- Space
- Research
- ICT service management
- Chemicals
How to prepare for NIS2
To comply with NIS2, organizations need to adopt a proactive approach to cybersecurity. Entities are expected to take all the technical, operational, and organizational measures to manage the network and IT risks. The 10 core measures outlined in the NIS2 Directive include:
1. Risk analysis and information system security
Create policies to regularly check and manage risks in your IT systems. It’s important to keep these policies updated to stay ahead of new threats and tech changes.
2. Incident handling
Set up plans for dealing with security breaches, including how to detect, report, analyze, and fix them. Having a good incident response plan helps minimize damage and speeds up recovery.
3. Business continuity
Include plans for backups, disaster recovery, and managing crises to keep things running during and after disruptions. Regularly testing and updating these plans ensures they’re effective when needed.
4. Supply chain security
Focus on securing relationships with your suppliers and service providers to prevent risks from third-party connections. Regularly checking and auditing suppliers’ security practices helps keep things safe.
5. Security in network and information systems
Make sure your security covers buying, developing, maintaining, and handling vulnerabilities in your systems. Building security into the design phase helps reduce future risks.
6. Cybersecurity risk management measures
Create policies and procedures to regularly check how well your cybersecurity efforts are working. Frequent risk assessments and adopting new tech can boost overall security.
7. Cyber hygiene and cybersecurity training
Teach good cybersecurity habits and knowledge to protect digital assets, and foster a culture of security awareness. Ongoing training keeps everyone up-to-date on the latest threats and best practices.
8. Cryptography and encryption
Set policies for using encryption to protect sensitive data and communications. Properly managing encryption keys is crucial for keeping data secure.
9. Human resources security
Implement access control policies and manage assets to ensure only authorized people can access critical systems and info. Background checks and regular security training for employees can enhance security further.
10. Authentication
Use multi-factor authentication and other methods to verify user identities and prevent unauthorized access. Strong authentication reduces the risk of unauthorized access and data breaches.
Action 1: Conduct a comprehensive risk assessment
Next, we’ll dive deeper into some of these measures and look at five specific lines of action that are central to achieving NIS2 compliance.
A thorough risk assessment is the foundation of any effective cybersecurity strategy. In preparation for NIS2, organizations should:
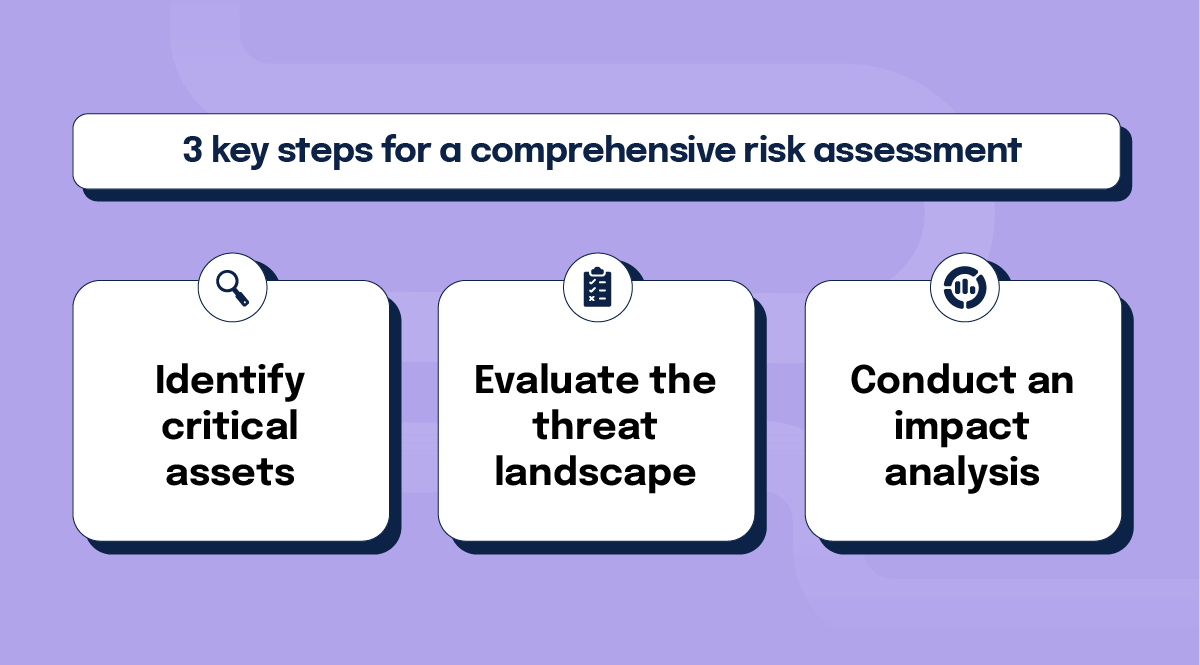
1. Identify critical assets
Determine which systems, data, and services are essential to your operations and could be targeted by cyber threats.
2. Evaluate the threat landscape
Assess the potential threats and vulnerabilities specific to your organization and industry.
3. Conduct an impact analysis
Understand the potential impact of various cyber incidents on your operations, reputation, and regulatory compliance.
It’s also best to track your risk posture over time since your risk constantly evolves. Plus, you’ll not only want to register your own risks, but also evaluate your risks inherent to relationships with vendors (see more about this in Action 3 below).
Action 2: Develop and maintain an incident response plan
Incident handling also deserves some added attention when it comes to NIS2 compliance. Not only is it one of the core risk management measures, but how you respond to an incident can affect any subsequent regulatory action against your organization. Here are four key components that make up an effective incident response plan:
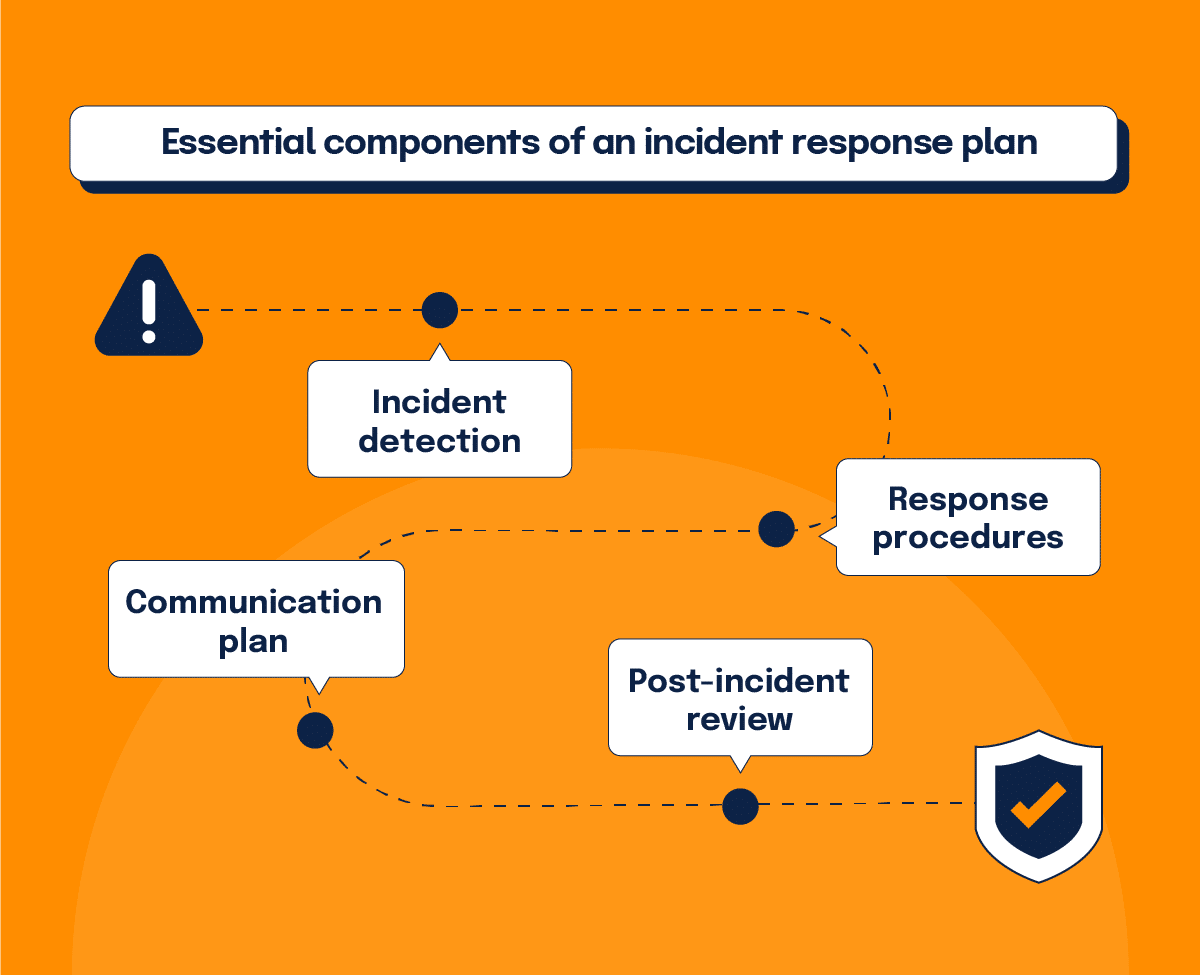
1. Incident detection
Implement monitoring tools and processes to detect security incidents in real-time, such as intrusion detection systems and log analysis tools to swiftly identify any unauthorized activities or anomalies within the network.
2. Response procedures
Establish clear procedures for responding to different types of incidents, including containment, eradication, and recovery steps. Outline roles and responsibilities of team members to ensure a coordinated effort during a crisis.
3. Communication plan
Develop a communication plan to inform stakeholders, including regulators, customers, and employees in the event of a cyber incident. Specify channels of communication, key messaging, and designated spokespersons to maintain transparency and trust.
4. Post-incident review
Conduct a thorough review after each incident to identify lessons learned and improve your incident response capabilities. This includes evaluating the effectiveness of response procedures, updating documentation, and implementing necessary adjustments to prevent similar incidents in the future.
Action 3: Enhance supply chain security
Increasingly, perpetrators compromise the security of an entity’s network and information systems by exploiting vulnerabilities affecting third-party products. As per NIS2, organizations should secure their supply chains through:
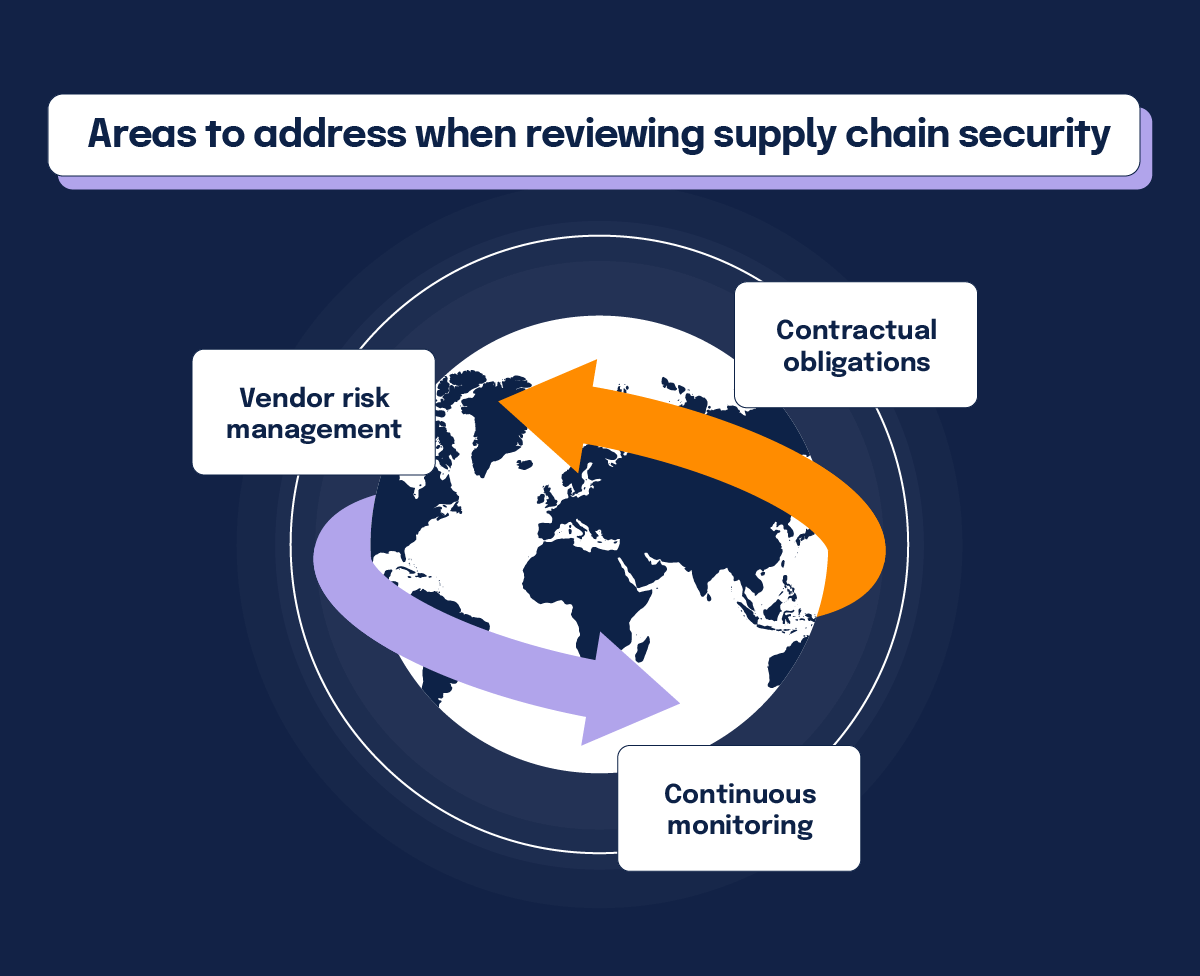
Vendor risk management
Assess the cybersecurity posture of your vendors and third-party service providers. Require them to adhere to your security standards.
Contractual obligations
Include cybersecurity requirements in contracts with suppliers and partners to ensure they are accountable for their security practices.
Continuous monitoring
Regularly monitor and audit the security practices of your supply chain to identify and address potential vulnerabilities.
For most companies today, their SaaS tech stacks are fairly large (or even massive) which means the risk is significant. The average small business with 500 or fewer employees has 172 apps in their stack; mid-market companies between 501 and 2,500 employees have 255 apps on average; and large enterprises have an average of 664 apps.
Hyperproof can help you streamline your vendor risk assessment significantly with risk assessment templates. Hyperproof even lets you automate your vendor risk assessment. With continuous updates of your list of vendors, secure vendor questionnaires, vendor monitoring, and proof of vendor risk management, we can accelerate the process to achieve robust supply chain security.
Action 4: Foster a culture of cybersecurity
According to the latest Verizon Data Breach Investigations Report (DBIR), 74% of all breaches include the human element, with people being involved either via error, privilege misuse, use of stolen credentials, or social engineering. That makes a strong case for good cyber hygiene. Creating a culture of cybersecurity awareness and accountability within your organization is essential. Steps to achieve this include:
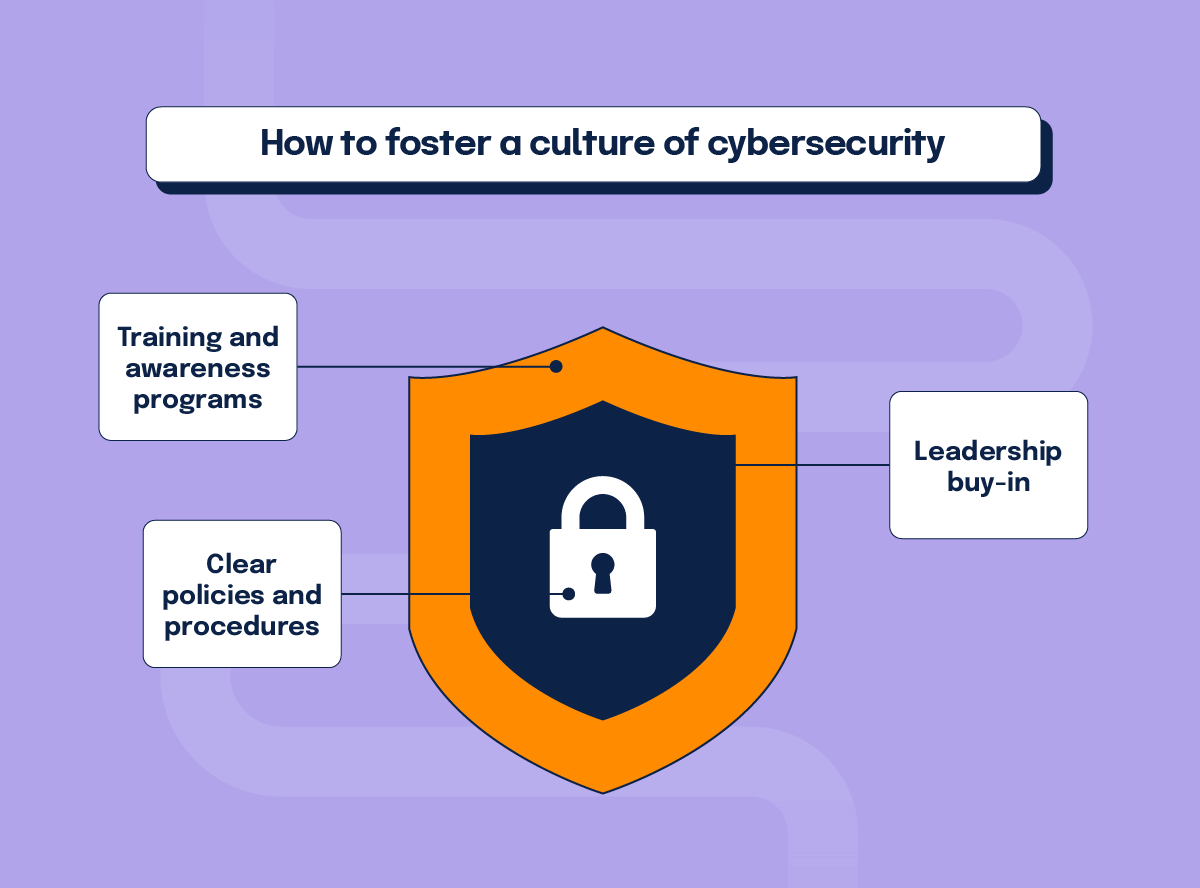
Training and awareness programs
Conduct regular cybersecurity training sessions for all employees to ensure they understand the importance of cybersecurity and their role in maintaining it.
Clear policies and procedures
Develop and enforce clear cybersecurity policies and procedures that all employees must follow.
Leadership buy-in
Ensure that senior management is actively involved in cybersecurity governance and decision-making.
Action 5: Ensure compliance with reporting requirements
Compared to its predecessor, NIS2 introduces stricter reporting requirements for cybersecurity incidents. Organizations must comply with:

Timely reporting
Report significant cybersecurity incidents to the relevant national authorities within the required timeframe.
Comprehensive documentation
Maintain detailed records of all cybersecurity incidents, including the nature of the incident, the response measures taken, and the impact on your operations.
Collaboration with authorities
Cooperate with national authorities during incident investigations and follow their guidance on incident management and mitigation.
Organizations must notify the relevant national authorities within 24 hours of becoming aware of a significant incident. If the initial notification was incomplete, an intermediate report providing additional information must be submitted within 72 hours of the initial notification. A final report providing comprehensive information about the incident, including its impact and the remedial actions taken, should be submitted no later than one month after the initial notification.
The role of national authorities and NIS2
Under NIS2, national authorities play a crucial role in ensuring compliance and enhancing cybersecurity across the EU. This reality underpins the entire legislation and establishes the authority, and responsibility, required to achieve widespread compliance. National authorities’ responsibilities include:
Regulatory oversight
National authorities are responsible for overseeing the implementation of NIS2 within their jurisdictions, ensuring that organizations comply with the directive’s requirements.
Guidance and support
Authorities provide guidance and support to organizations, helping them understand their obligations and implement effective cybersecurity measures.
Incident handling
National authorities coordinate the response to significant cybersecurity incidents, working with affected organizations to manage and mitigate the impact.
Cross-boarder cooperation
Authorities collaborate with their counterparts in other EU member states to address cross-border cyber threats and incidents.
Additional considerations for NIS2 compliance
International considerations
For multinational organizations, NIS2 compliance can be particularly challenging due to varying regulations across different countries. Some key ways to address cross-border issues include:
Harmonize compliance efforts
Develop a unified approach to compliance that aligns with NIS2 and other international cybersecurity standards, such as the General Data Protection Regulation (GDPR), the Cybersecurity Maturity Model Certification (CMMC), and ISO/IEC 27001. If you already have evidence for compliance with these schemes, it can accelerate your compliance with NIS2. By mapping controls across frameworks, you can satisfy requirements from multiple standards. This saves you a lot of time when implementing new frameworks, adapting to new regulations, and staying up to date with existing frameworks.
Cross-boarder incident response
Establish cross-border incident response protocols to ensure coordinated efforts in the event of a cyber incident that affects multiple jurisdictions.
2. Monitoring regulatory updates
Be sure to stay informed about updates to NIS2 and other relevant regulations. Regularly review and update your cybersecurity policies to reflect changes in the regulatory environment. Hyperproof can make this process easier with automated evidence collection to streamline keeping up with compliance updates.
Build a stronger, more secure future with NIS2
Preparing for the EU’s NIS2 Directive requires a comprehensive and proactive approach to cybersecurity. By conducting thorough risk assessments, implementing robust technical measures, fostering a culture of cybersecurity awareness, and collaborating with national authorities, organizations can ensure compliance and enhance their overall security posture.
Achieving NIS2 compliance not only helps avoid regulatory penalties but also provides significant benefits, including enhanced security, improved resilience, increased trust, and a competitive advantage. By taking these steps, organizations can navigate the complexities of NIS2 and build a stronger, more secure future.
The post How to Prepare for the EU’s NIS2 Directive appeared first on Hyperproof.
*** This is a Security Bloggers Network syndicated blog from Hyperproof authored by Erin Nelson. Read the original post at: https://hyperproof.io/resource/nis2-directive/
如有侵权请联系:admin#unsafe.sh