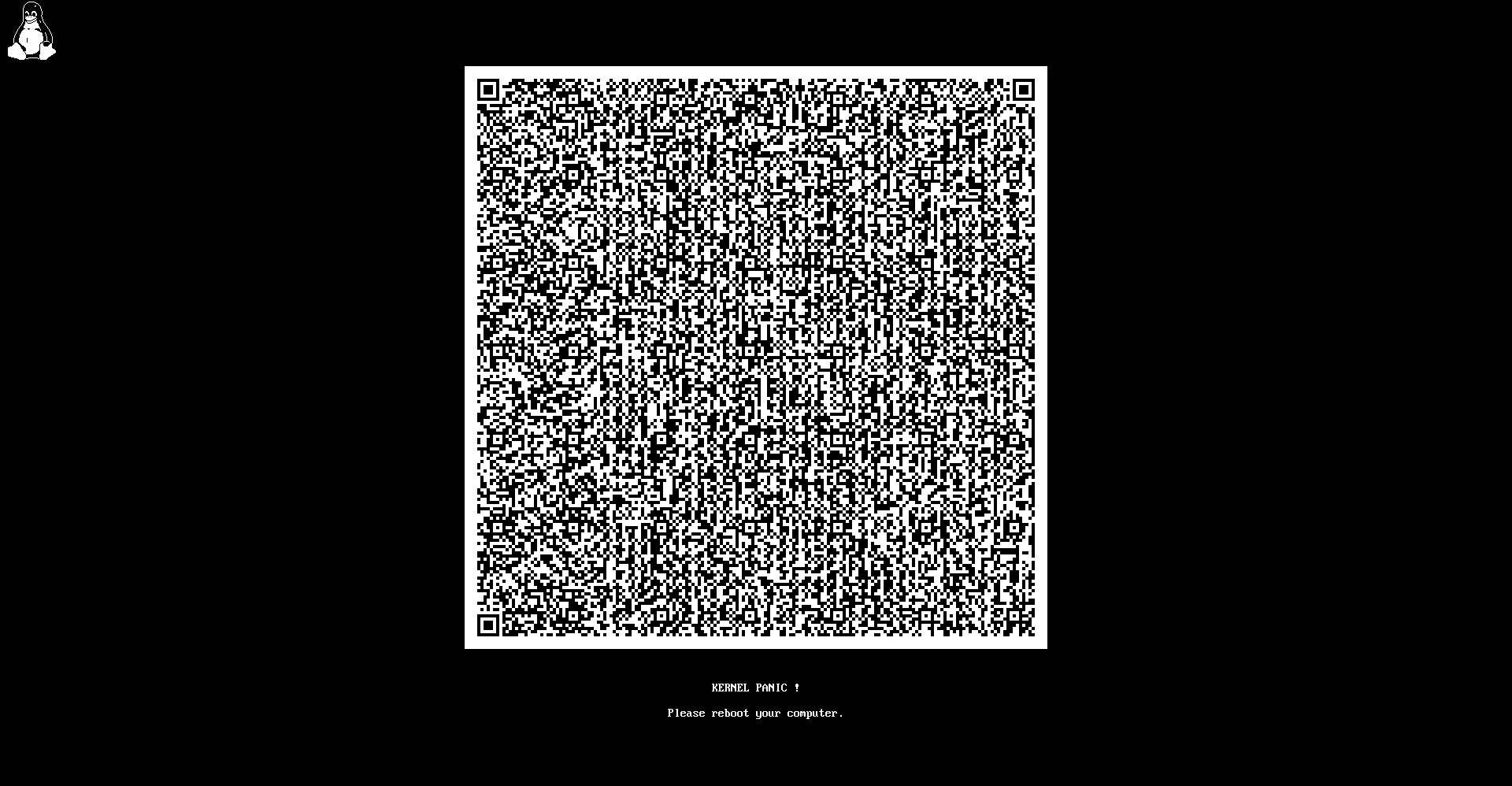
#系统资讯 去年 systemd 255 引入了 BSOD 服务,可以在 Linux 发生死机时使用全屏显示错误内容。那么怎么更好的显示错误内容呢?那就是将其压缩为二维码,只需要拍摄保存二维码即可事后进行分析,这也可以解决有时候错误内容太长屏幕呈现不完的问题。查看全文:https://ourl.co/104834
2023 年 12 月 Linux 系统组件 systemd 255 版发布,此次更新附带了 systemd-bsod 服务,该服务可以在 Linux 上全屏显示错误消息。
BSOD 指的是 Blue Screen of Death,也就是我们常说的蓝屏死机,Linux 增加该功能后也会引入二维码,不过在 Windows BSOD 里二维码内容比较固定,主要是微软制作的一些错误代码对应的链接。
而 Linux 在二维码显示上会有所区别,有时候内核级别的错误消息非常长,可能整个屏幕都无法容纳完整的错误信息,如果能将这些信息压缩为二维码的话,也是个解决方案。
引入二维码的好处是将非常长的内核错误放在二维码里,用户可以通过拍照的方式保存内核错误,方便未来需要进行排查或将二维码发送给专业用户进行分析。
日前红帽工程师发布了一组用于实现 Linux BSOD 二维码的四个补丁,这些补丁使用 Rust 语言进行编写,可以将错误消息转换为完整的二维码。
从示例来看二维码确实可以压缩足够多的信息,这种情况下用户可能需要专业的解码工具才能识别全部内容,直接使用手机扫码解码可能有一定的困难。
不过这些只是目前的实现示例,具体未来会变成什么样子还需要 Linux 社区继续讨论,下面是两个示例对应的解码内容。
示例一:将错误信息编码的错误报告中再通过 Github 呈现
该二维码内容是:
https://kdj0c.github.io/panic_report/?a=x86_64&v=6.9.0-rc2&d=fc38&zl=23211526274253735776105615355975449444773432468760857542427925690077558347731802432825010712715135500903315678882545762970007010034124540664402866476969005541133176227228004395748660976276702927587832641336897975280630406751639006951363122856892870490366276003338524932577228006372333266878370765644344345550356742622824123134131785182771236468702953991363612226051279477367280684727309412232789447316068538467362073790921197786609608236465602171740167276428494801545749797401238601205562655303486556396856852714551505747576367345970308281624536073352867324445581802377510415354690689290176304380094557331825332136421360355832808107785469053427497000851562143419398022236654912164497179816990437473314918482444941627418653724508074715151719238620912731729051684189435371454438308629225520525405224450404974461364519366666670412663004832630743045580125780726160816657503106309150654397174720812884721540064455630433718028249716991356540762434629347757855106552560907254285817486152562571678064222438610284737040658098418562746974452771764482096304837041684329600837709431364550436408941223175651242072566175604675715611030256683164140698118812193189122022641991688477255967011018962280708467672630529479727975639643595316808042420125020743687553336150663176419237370385090416785683746862735317783102663334770046653705110331250921003823462490121905303595757317195213676672137319109161935220571045492866451725081869187637000549013451661368242729197374258937016175267206805358668573724876541430720369118137205281326307570635743858941490525461765747419831137872197249002947509907271421575119955685320054096593499537960489193140668014250101872358265846971465607062291992337028982672512309695690300957750002723420403405144114823245254804594961395057864834142872413152715155956037000656627154564760170804009051867171592159787115701236021285006417230004231057937456196650431545093303603633704730775107463265616056374801515532536704781312114400324228312722323622631739121231748411220876020745142483786044621940222868697104179545740999506164507702765042227711590545094041398223666045096722411373614837030363111819632305780555612178396333633927509802623808696337541452472129490439018756691288149970054227064918451987537473265285480468182544546129645254611852817774259505873016041822811514239911002861401817950978113633140766270239257337480102755458772222195680220600687077787145807338244539523262391481542923356873927132203767153755369640928026079403798031080749156291688264645297277412191353809766640727550320395100397919372814
呈现的错误报告是:
Panic Report Arch: x86_64 Version: 6.9.0-rc2 Distribution: fc38 [ 5.003159] NET: Registered PF_QIPCRTR protocol family [ 5.749751] systemd-journald[675]: /var/log/journal/3fd49adc611f4a67ad8ca32dd9d374dd/user-1000.journal: Journal file uses a different sequence number ID, rotating. [ 7.160218] rfkill: input handler disabled [ 8.261932] input: spice vdagent tablet as /devices/virtual/input/input7 [ 1332.704223] sysrq: Trigger a crash [ 1332.705499] Kernel panic - not syncing: sysrq triggered crash [ 1332.710397] CPU: 6 PID: 2454 Comm: bash Not tainted 6.9.0-rc2+ #7 [ 1332.712751] Hardware name: QEMU Standard PC (Q35 + ICH9, 2009), BIOS edk2-20230524-3.fc38 05/24/2023 [ 1332.715600] Call Trace: [ 1332.715778] <TASK> [ 1332.715932] dump_stack_lvl+0x2d/0x90 [ 1332.716204] panic+0x118/0x310 [ 1332.716422] sysrq_handle_crash+0x1a/0x20 [ 1332.716724] __handle_sysrq+0x130/0x140 [ 1332.716990] write_sysrq_trigger+0x4c/0x80 [ 1332.717279] proc_reg_write+0x4a/0xa0 [ 1332.717559] vfs_write+0x110/0x3d0 [ 1332.717800] ksys_write+0x72/0xe0 [ 1332.718047] do_syscall_64+0x99/0x180 [ 1332.718303] ? exc_page_fault+0x7b/0x1b0 [ 1332.718591] entry_SYSCALL_64_after_hwframe+0x71/0x79 [ 1332.718938] RIP: 0033:0x7f1967c17c74 [ 1332.719218] Code: c7 00 16 00 00 00 b8 ff ff ff ff c3 66 2e 0f 1f 84 00 00 00 00 00 f3 0f 1e fa 80 3d f5 76 0d 00 00 74 13 b8 01 00 00 00 0f 05 <48> 3d 00 f0 ff ff 77 54 c3 0f 1f 00 55 48 89 e5 48 83 ec 20 48 89 [ 1332.720487] RSP: 002b:00007fffb7518348 EFLAGS: 00000202 ORIG_RAX: 0000000000000001 [ 1332.721032] RAX: ffffffffffffffda RBX: 0000000000000002 RCX: 00007f1967c17c74 [ 1332.721502] RDX: 0000000000000002 RSI: 000055f9365fb510 RDI: 0000000000000001 [ 1332.722100] RBP: 00007fffb7518370 R08: 0000000000000073 R09: 0000000000000001 [ 1332.722564] R10: 0000000000000000 R11: 0000000000000202 R12: 0000000000000002 [ 1332.724053] R13: 000055f9365fb510 R14: 00007f1967ce85c0 R15: 00007f1967ce5f20 [ 1332.724532] </TASK> [ 1332.724867] Kernel Offset: 0x22000000 from 0xffffffff81000000 (relocation range: 0xffffffff80000000-0xffffffffbfffffff)
示例二:不经过Github中转而是直接将完整的错误信息压缩到二维码中
该二维码的内容是:
[ 3.319019] RPC: Registered tcp-with-tls transport module. [ 3.319019] RPC: Registered tcp NFSv4.1 backchannel transport module. [ 3.606789] NET: Registered PF_QIPCRTR protocol family [ 6.181205] rfkill: input handler disabled [ 7.416796] input: spice vdagent tablet as /devices/virtual/input/input7 [ 61.830264] sysrq: Trigger a crash [ 61.830271] Kernel panic - not syncing: sysrq triggered crash [ 61.830276] CPU: 6 PID: 2354 Comm: bash Not tainted 6.10.0-rc1+ #88 [ 61.830278] Hardware name: QEMU Standard PC (Q35 + ICH9, 2009), BIOS edk2-20240524-2.fc39 05/24/2024 [ 61.830280] Call Trace: [ 61.830282] <TASK> [ 61.830285] dump_stack_lvl+0x2d/0x90 [ 61.830294] panic+0x118/0x300 [ 61.830297] sysrq_handle_crash+0x1a/0x20 [ 61.830299] __handle_sysrq+0x130/0x140 [ 61.830302] write_sysrq_trigger+0x4c/0x80 [ 61.830304] proc_reg_write+0x68/0xb0 [ 61.830306] vfs_write+0x111/0x3e0 [ 61.830308] ? do_syscall_64+0x9a/0x170 [ 61.830310] ksys_write+0x72/0xe0 [ 61.830312] do_syscall_64+0x8e/0x170 [ 61.830314] ? do_syscall_64+0x9a/0x170 [ 61.830315] ? filp_close+0x5c/0x80 [ 61.830317] ? do_dup2+0xae/0x110 [ 61.830319] ? syscall_exit_to_user_mode+0xb0/0xd0 [ 61.830321] ? do_syscall_64+0x9a/0x170 [ 61.830323] ? __se_sys_fcntl+0x64/0xb0 [ 61.830324] ? syscall_exit_to_user_mode+0xb0/0xd0 [ 61.830326] ? do_syscall_64+0x9a/0x170 [ 61.830328] ? ptep_set_access_flags+0x27/0x40 [ 61.830330] ? _raw_spin_unlock+0xe/0x30 [ 61.830332] ? do_wp_page+0x7f4/0x1100 [ 61.830334] ? __se_sys_fcntl+0x64/0xb0 [ 61.830335] ? syscall_exit_to_user_mode+0xb0/0xd0 [ 61.830337] ? __count_memcg_events+0x6e/0x100 [ 61.830338] ? handle_mm_fault+0xa18/0x13e0 [ 61.830340] ? kmem_cache_free+0x2d/0x2e0 [ 61.830344] ? do_user_addr_fault+0x212/0x750 [ 61.830346] ? clear_bhb_loop+0x25/0x80 [ 61.830348] ? clear_bhb_loop+0x25/0x80 [ 61.830350] ? clear_bhb_loop+0x25/0x80 [ 61.830352] entry_SYSCALL_64_after_hwframe+0x76/0x7e [ 61.830356] RIP: 0033:0x7f11316cb834 [ 61.830360] Code: c7 00 16 00 00 00 b8 ff ff ff ff c3 66 2e 0f 1f 84 00 00 00 00 00 f3 0f 1e fa 80 3d 15 f8 0d 00 00 74 13 b8 01 00 00 00 0f 05 <48> 3d 00 f0 ff ff 77 54 c3 0f 1f 00 55 48 89 e5 48 83 ec 20 48 89 [ 61.830361] RSP: 002b:00007ffc1b0593c8 EFLAGS: 00000202 ORIG_RAX: 0000000000000001 [ 61.830364] RAX: ffffffffffffffda RBX: 0000000000000002 RCX: 00007f11316cb834 [ 61.830365] RDX: 0000000000000002 RSI: 00005566aa3202e0 RDI: 0000000000000001 [ 61.830366] RBP: 00007ffc1b0593f0 R08: 0000000000000073 R09: 00000000ffffffff [ 61.830367] R10: 0000000000000000 R11: 0000000000000202 R12: 0000000000000002 [ 61.830368] R13: 00005566aa3202e0 R14: 00007f11317a45c0 R15: 00007f11317a1f00 [ 61.830371] </TASK> [ 61.830543] Kernel Offset: 0x3a000000 from 0xffffffff81000000 (relocation range: 0xffffffff80000000-0xffffffffbfffffff)
版权声明:
感谢您的阅读,本文由 @山外的鸭子哥 转载或编译,如您需要继续转载此内容请务必以超链接(而非纯文本链接)标注原始来源。原始内容来源:Phoronix