2024-7-10 19:44:40 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
How Horizon3.ai’s Rapid Response Identified and Mitigated a Critical Mirth Connect Vulnerability
A key consideration in cybersecurity is determining whether a known software vulnerability is actually exploitable. This often depends on how and where the at-risk software is deployed in your environment. To address the need to find what’s exploitable, Horizon3.ai developed and recently unveiled its Rapid Response service.
This service provides our customers with proactive notifications about potentially exploitable vulnerabilities existing in their environments. Then using NodeZero, it allows them to test for exploitability for zero-day and N-day vulnerabilities. Once remediations are performed, they then use NodeZero to verify that issues have been resolved.
Let’s look at an example of Rapid Response in action, in the context of a Mirth Connect RCE (Remote Code Execution) vulnerability that our research team discovered last year.
Timeline of Mirth Connect Vulnerability: CVE-2023-43208
As part of our Rapid Response service, Horizon3.ai’s Attack Team performs expert research on popular software applications, this time researching Mirth Connect by NextGen HealthCare. Mirth Connect is an open-source data integration platform widely used by healthcare organizations.
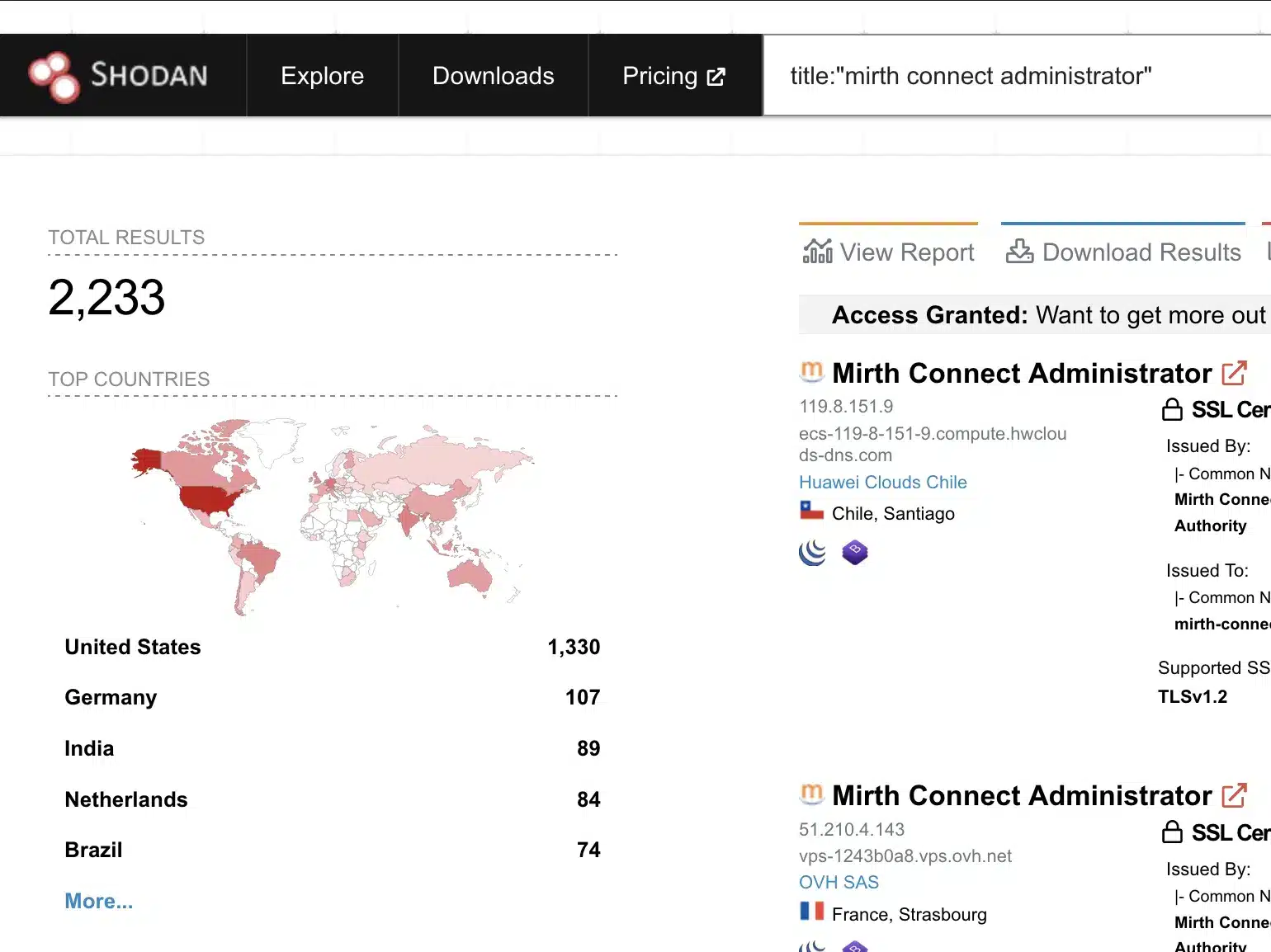
Last August, our Attack Team was tracking a vulnerability in Mirth (CVE-2023-37679) which was reportedly patched in Mirth Connect 4.4.0, released on Aug 2, 2023. In the release notes for 4.4.0., our research team found it odd that this vulnerability was reported to affect only Mirth Connect versions running Java 8. They believed that further investigation needed to be performed. According to Shodan at the time, several thousand instances of Mirth Connect were exposed to the internet.
On September 8, 2023, due to looking closer at the Mirth patch and CVE noted above, the Attack Team privately disclosed a new, unauthenticated remote code execution (RCE) vulnerability they had discovered in Mirth Connect 4.4.0. that was the result of an incomplete patch for CVE-2023-37679.
On October 2, after privately disclosing our discovery of the RCE vulnerability in Mirth, our researchers developed an exploit that was fully capable of exploiting vulnerable versions of Mirth. The exploit was added to NodeZero at that time. After adding the exploit to NodeZero, our customers were able to launch a Rapid Response test for the Mirth vulnerability we discovered to quickly confirm if their instances of Mirth were exploitable. In fact, many of them were.
Through our Rapid Response test for Mirth, our customers had a 15-day window to test for Mirth exploitability before a patch for the RCE vulnerability was even available from NextGen. The Rapid Response zero-day test allowed our customers to take action to protect their exploitable Mirth implementations while they waited for a patch from NextGen.
On October 17, after working closely with NextGen, who provided a test build to our researchers, they released a patched version to remedy the vulnerability our researchers discovered. You can learn more about our public disclosure here.
On October 26, the vulnerability our researchers discovered (CVE-2023-43208) was officially published on the NVD (National Vulnerability Database). According to our disclosure, “Mirth Connect is an interesting application for us at Horizon3.ai because a number of our clients are in the healthcare space and use this application. Healthcare companies are commonly targeted by ransomware threat actors, and this application has decent exposure on the Internet.”
On January 12, 2024, after giving those in the healthcare industry plenty of time to update any vulnerable Mirth instances, our researchers publicly disclosed an exploit for the Mirth vulnerability. According to our public disclosure, “If you’re a user of Mirth Connect and haven’t patched yet, we strongly encourage you to upgrade to the 4.4.1 patch release or later. This is an easily exploitable vulnerability that our own pentesting product, NodeZero, has exploited successfully against a number of healthcare organizations [customers].”
As part of our Rapid Response service, all customers of Horizon3.ai who had previously run NodeZero in their environments were already notified that their Mirth Connect implementations were likely exploitable. We also recommended that they should run the zero-day test for Mirth to identify all systems running the exploitable Mirth version. Since Mirth is an open-source platform, other systems who use Mirth could be exploitable as well.
On February 29, Bayer Radiology Solutions released an important update on Mirth Connect. This update showed that other systems in healthcare environments could be exploitable too. Here is an excerpt from that update: “Bayer has performed an initial assessment of the recently disclosed remote code execution vulnerabilities affecting Mirth Connect versions prior to 4.4.1 (CVE-2023-37679 and CVE-2023-43208).
After conducting a thorough analysis, we have determined that the following Bayer devices contain a vulnerable version of Mirth Connect:
- MEDRAD® Stellant FLEX CT Injection System
- MEDRAD® Stellant CT Injection System with Certegra® Workstation
- MEDRAD® MRXperion MR Injection System”
On March 7, our researchers then learned via a discussion on GitHub that attackers were actively trying to exploit the vulnerability. At that time, NodeZero was updated with information about the vulnerability being exploited in the wild to further warn organizations about the critical need to update to Mirth 4.4.1.
On April 19, Microsoft Threat Intelligence posted on X (formally Twitter) said that they were tracking several ransomware threat actors who were exploiting both CVE-2023-37679 and CVE-2023-43208.
On May 20, CISA added CVE-2023-43208 to the CISA Known Exploited Vulnerabilities (KEV) Catalog – meaning, the vulnerability was reported as being widely exploited, seven months after NextGen issued a patch on October 17, 2023.
Why Rapid Response Matters in the Context of Exploitability
Even before a patch was available from NextGen, our customers were testing their environments with the NodeZero Rapid Response test to determine if their instances of Mirth Connect were exploitable – many of them were. Once a patch was issued, our customers patched their Mirth instances and launched the NodeZero Rapid Response test again to confirm that the patch was effective and that their systems were no longer exploitable.
More importantly, our customers who ran the Mirth Rapid Response test and found they were exploitable were patching all instances of Mirth for nearly nine months before the vulnerability was added to the CISA KEV.
(Here is a screen shot of the NextGen Mirth Connect test on NodeZero with information about the CVE, links to resources to learn more about the issue, and a corresponding timeline of notable events.)
More About Rapid Response
With the latest improvements to NodeZero, both new and existing customers now have a dedicated center for all Rapid Response activities. This includes self-service tests, threat details, and alerts from Horizon3.ai about the exploitability of specific assets in their environments.
In today’s dynamic threat landscape, speed is paramount, followed closely by prioritizing impact on business. By emphasizing velocity and providing tailored, actionable threat intelligence, Horizon3.ai’s Rapid Response service uses offensive security principles to inform defenders about the targets that matter most when protecting critical infrastructure.
Learn More About Rapid Response. Download our Rapid Response White Paper Today.
The post Ensuring Cybersecurity: Horizon3.ai’s Rapid Response Service in Action appeared first on Horizon3.ai.
*** This is a Security Bloggers Network syndicated blog from Horizon3.ai authored by Stephen Gates. Read the original post at: https://www.horizon3.ai/insights/blogs/ensuring-cybersecurity-horizon3-ais-rapid-response-service-in-action/
如有侵权请联系:admin#unsafe.sh


