- Data breaches have become one of the most crucial threats to organizations across the globe, and they’ve only become more prevalent and serious over time.
- A data breach occurs when unauthorized individuals gain access to sensitive, protected or confidential data. This stolen data can include personal information, financial records, intellectual property, and other critical information.
- Stolen data is a valuable commodity in the cybercriminal world and, once acquired through data breaches, is often sold on underground markets.
- A recent cryptocurrency-related scam Cisco Talos discovered highlights how data breaches are being increasingly leveraged in these types of campaigns, preying on targets’ fears around their information being out in the wild.
Over the years, data breaches have played a pivotal role in facilitating various forms of cyber-attacks. Adversaries are leveraging on stolen data to execute more sophisticated and damaging attacks to materialize their malicious intents. The significance of data breaches extends far beyond the immediate loss of data with the implications for security, reputation and financial stability of individuals and organizations.
Cisco Talos observed an ongoing cryptocurrency heist scam since as early as January 2024, leveraging hybrid social engineering techniques such as vishing and spear phishing, impersonating individuals and legitimate authorities to compromise the victims by psychologically manipulating their trust with social skills.
Impersonating investigation officers of CySEC (Cyprus Securities and Exchange Commission), the scammers in this campaign are using a lure theme of refunding a fake seized amount from a fraudulent trading activity in Opteck trading platform to compromise the victims.
Opteck is a trading platform founded in 2011 and provides binary options trading solutions for its customers. In 2017, Opteck’s database was sold on raidforums by adversaries and even today, we still see users’ Opteck login credentials being sold on Russian dark markets, indicating the likelihood of a data breach. That same year, CySEC (Cyprus Securities and Exchange Commission) flagged Opteck as non-complaint and had suspended its license until they took action to rectify the issues. The scammers are likely leveraging the stolen data in the dark web and the news to create a more convincing lure for this campaign.
CySEC issued other warnings in November 2022 that fraudsters are impersonating their officers and making fake offers to assist investors with compensation claims for the dealings that they may have had with the sanctioned firms.
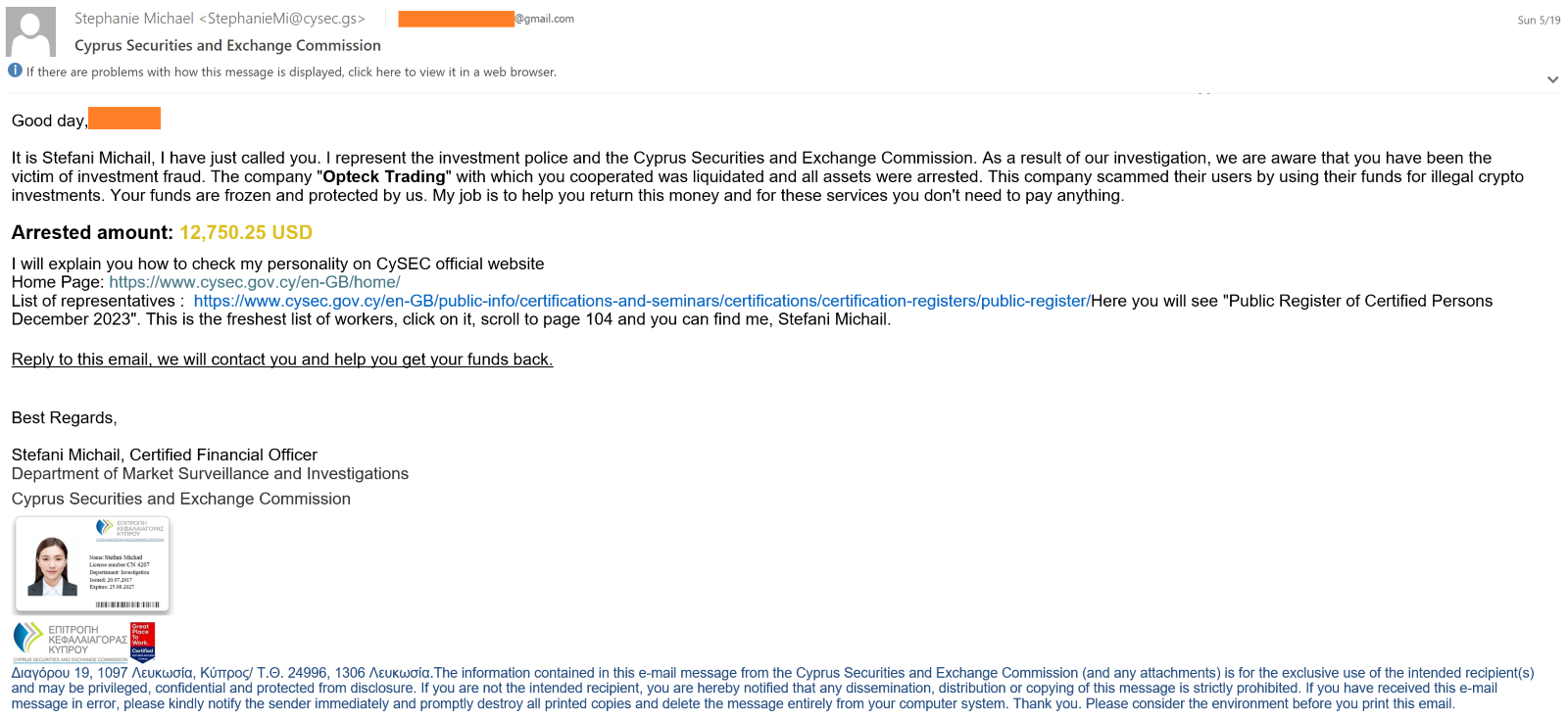
Since January 2024, Talos has been observing that the scammer, impersonating certified investigation officers of CySEC, is attempting to contact a potential victim who is or was once a user of the Opteck trading platform. The scammers, after getting connected to a potential victim over the phone, introduces them as the investigation officers of CySEC, confirming that the potential victim was once an Opteck trading platform user. Then, they attempt to get the potential victim into a conversation, explaining a fake story of a fraudulent activity that Opteck was involved in and misusing potential victim’s cryptocurrency investments. The scammer also tried to assure the potential victims that their phone call was for refunding an amount they had seized, claiming that the amount belongs to the potential victim.
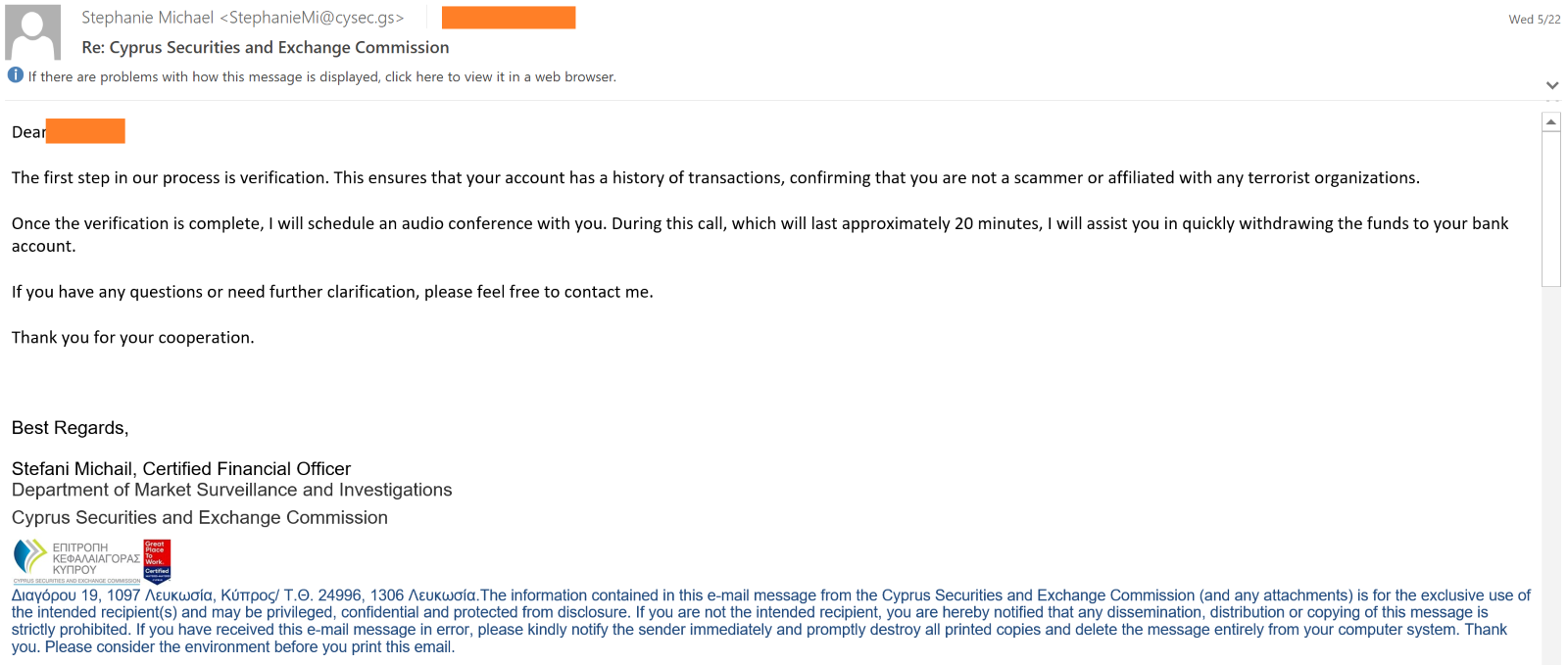
To convince the victims, scammers send an email impersonating the identities of the CySEC officers by misusing the CySEC investigating officers’ names in the CySEC’s Public Register of Certified Persons documentation from CySEC official website. In one instance, the scammer had created a fake business card and embedded it in the phishing email to make the phishing email appear legitimate.
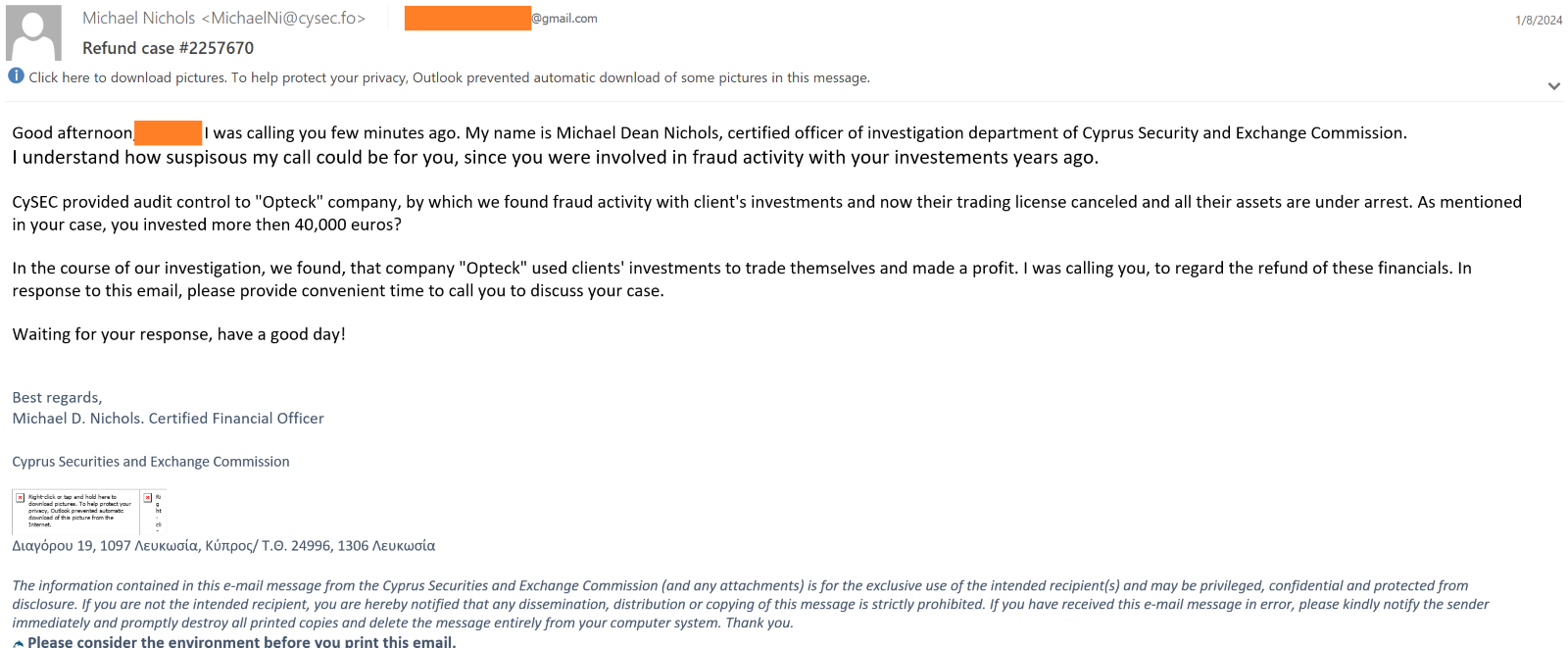
Upon compromising the victim and gaining their confidence, the scammer sends another email asking the victims’ bank statement as part of regulatory compliance verifications.
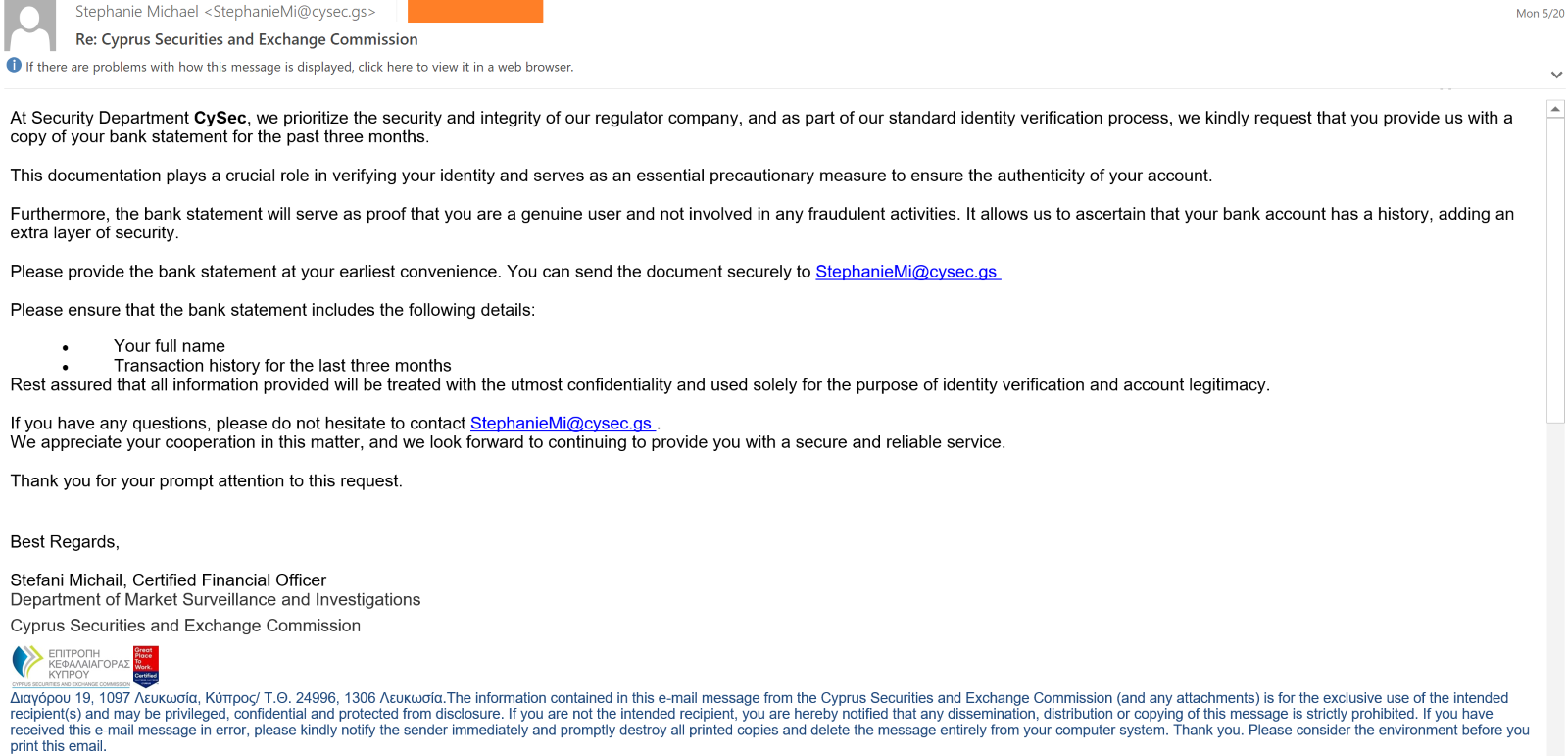
They will also send a follow-up email to the victim, explaining the fake refund process that includes an identity verification stage and after that they will engage the victims in a 20-minute telephonic conversation and assisting them in withdrawing funds.
We observed that when a victim engages in a phone conversation with the scammer, first they will create a cryptocurrency wallet in the Coinbase platform and send the wallet ID to the victim, assuring that they will give him 816 USDT as a wallet activation amount, which will be available 12 hours after activation.
In case of any errors performed by a victim, the scammer demands the victim transfer some specified ETH to another cryptocurrency wallet ID belonging to the scammer, which they are calling an AML wallet in this campaign. They also advise the victims that a representative from Coinbase would contact them.
By impersonating a Coinbase representative, the scammer advises the victim to pay them 10% of the fake refund amount as Coinbase legal insurance fees to their so-called AML wallet in USDT or ETH. When a victim agrees and pays the insurance fees, the scammer again demands the victim pay another amount as part of a negotiation process for another wallet ID in ETH, assuring that the victims will get 50% of the fake refund amount to their Coinbase wallet.
Finally, when a victim agrees and pays the negotiation amount with an intention to get the fake refund into the Coinbase wallet, the scammer continues the conversation by advising the victims to wait for the funds get transferred, which never actually happens, leading to the theft of victim's cryptocurrencies.
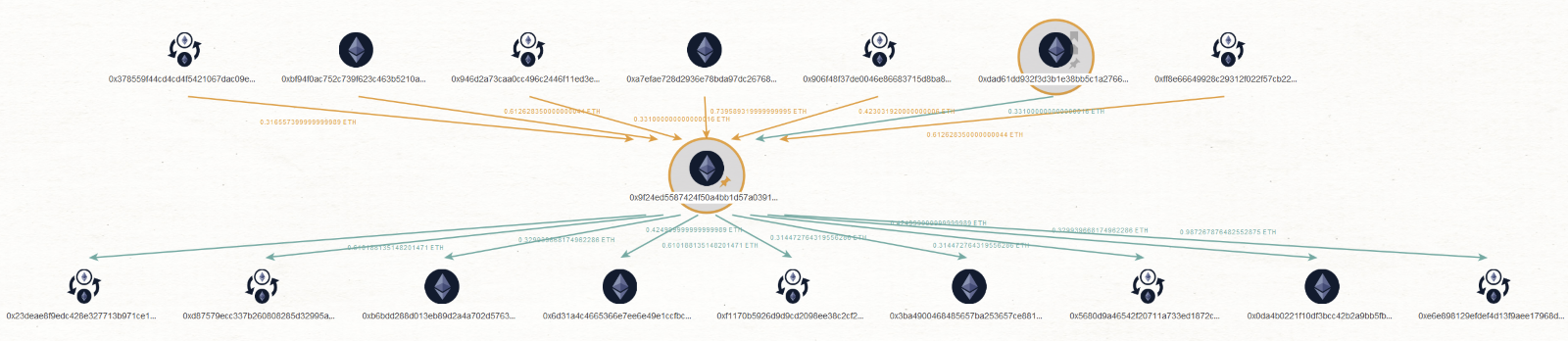
The campaign seemed lucrative till date according to the scammer's cryptocurrency wallets transactions and balances. We found four Ethereum wallets addresses that they have used to steal the victim’s cryptocurrency based on our analysis of the phishing emails.
Analyzing the transactions of scammer’s wallets in blockchain we discovered that the transaction volume and Ethereum received during the campaign period is equivalent to several thousands of USD.
Approximate ETH equivalent in USD | |
0xdAd61Dd932f3D3B1E38BB5c1a2766901487B6B1e | |
0x9f24ed5587424f50a4bb1d57a03914c2b5215ae2 | |
0xdAD9C378Bc0Eb7Ee17F92770a64eC80eef32caE2 | |
0xdC9060786AA19977Aa0AdbDa247437682B324D2a |
Talos also observed that scammers have multi-chain portfolios that allow them to spread their stolen cryptocurrency assets across multiple blockchain networks.
Scammer’s phishing infrastructure
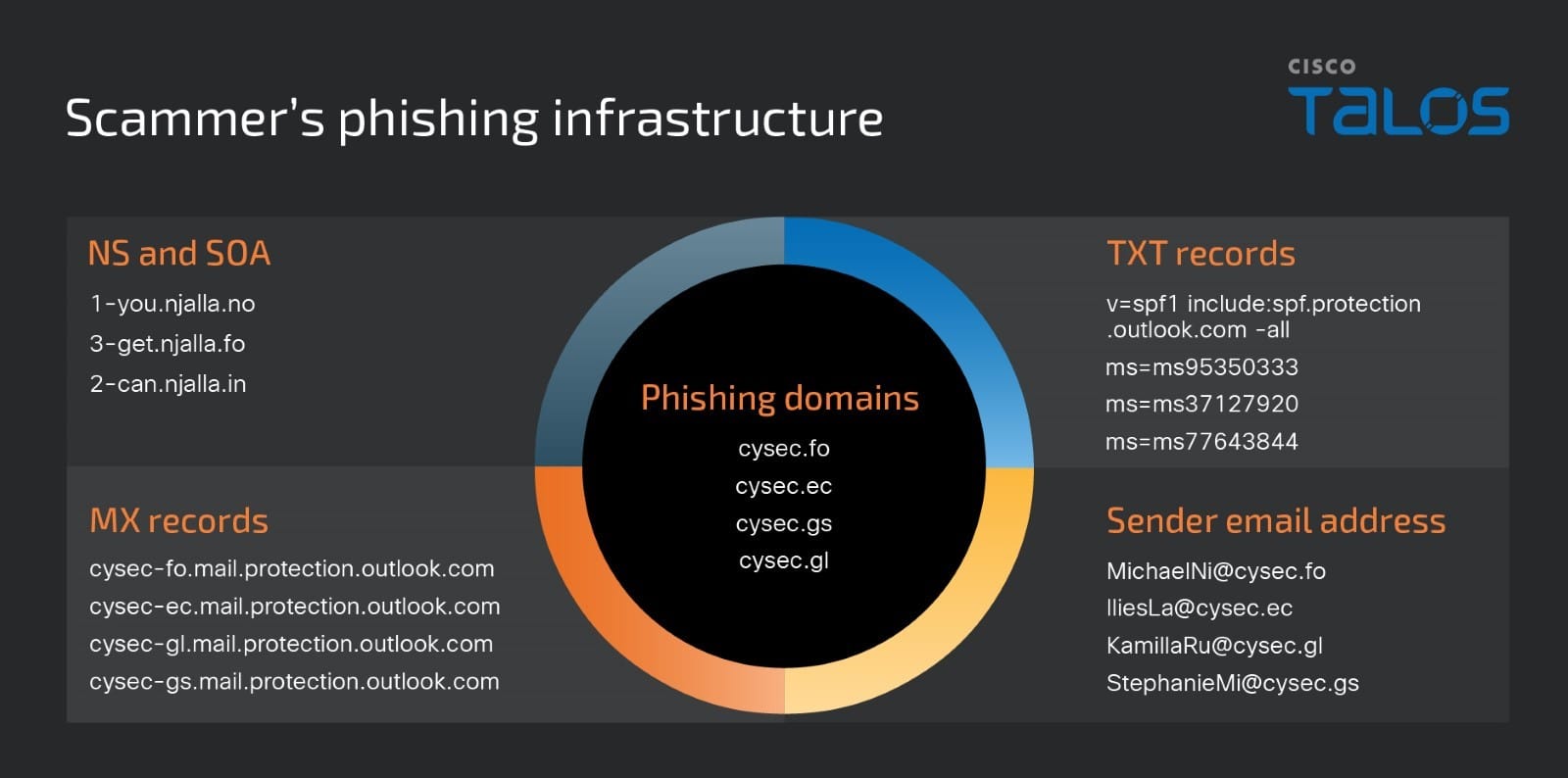
The scammer in this campaign has used several domains that resemble the legitimate domain of CySEC “cysec.gov.cy” as the phishing domains created in Sarek, a domain registration service provider.
The phishing domains’ name server (NS) and start of authority (SOA) records were configured to point to the domain name servers of njalla, a “privacy as a service” provider.
The mail exchange (MX) records of the domains were configured with the mail servers on mail.protection.outlook.com, indicating that the phishing emails are routed through Microsoft’s email protection services.
The text records for the domains indicates that the actor’s mail server includes the SPF (Sender Policy Framework) rules defined by “spf.protection.outlook.com,” meaning that any IP addresses allowed by Microsoft’s Outlook protection service are also allowed to send emails on behalf of the actor’s domain. We also observed a few ms=msXXXXXXXX values defined in the TXT records. The ms record is usually used for the domain validation procedure by Microsoft Office 365 and its existence indicates a rightful owner of the domain. The actor is using these values to likely validate their phishing domains in Microsoft office 365.
Security awareness, a mainstay in effective cybersecurity
Humans are considered as the weakest link or a low hanging fruit by the adversaries, as they attempt to trick them with various social engineering techniques, very often to gain access to their environment or perform fraudulent financial activities. And the significance of data breaches is facilitating the adversaries in their scam campaigns providing them the information needed to execute fraudulent activities, causing extensive financial, reputational, and psychological damage to individuals and organizations.
So, creating security awareness in public is a preliminary responsibility of the organizations and security community. It empowers individuals to protect themselves and supports organizational security efforts. By fostering a culture of security awareness, the risks associated with data breaches and scam campaigns can be reduced.