2024-7-17 23:0:31 Author: securityboulevard.com(查看原文) 阅读量:10 收藏

Recent studies have shown that half of the security breaches involve secrets, either to gain initial access or move laterally from one system to another. Attackers are looking for this valuable information to reach their objectives. This has led attackers to expand the scope of their targets, as they're no longer only looking for vulnerabilities in systems and software architectures but everywhere they might appear.
While working on projects, developers collaborate through various mediums, such as project management platforms, messaging tools, ticketing systems, and documentation. However, when developers take quicker routes, they might mistakenly reveal secrets in tools that are not designed to protect this kind of information.
That's why GitGuardian has expanded its automated secrets detection capabilities to the tools developers use the most frequently to collaborate: Slack, Jira, Confluence, Microsoft Teams, and more.
Let's be honest: who has never sent an API key in a Slack or Teams message? Even in well-informed and advanced organizations, developers may sometimes favor the path of least resistance and hardcode secrets in tools that they presume are out of the reach of attackers. Several examples of such incidents have been seen in the past few months.
In June 2024, Snowflake suffered a major breach that exposed hundreds of customers' data: terabytes of stolen data, including millions of bank account details. The point of failure? A Jira instance hosting credentials giving access to unprotected Snowflake accounts.
Through a spear-phishing attack, hackers infected a laptop belonging to one employee of a Snowflake partner with info-stealer malware. Once inside the worker's machine, attackers accessed Jira and found the crown jewels. They gained initial access to Snowflake customers' data and kept increasing their privileges, leading to this gigantic data breach with new incidents surfacing every day.
In even more recent news, a group of activists exposed thousands of Disney's internal Slack messages. Among these messages, they found secrets, source code, information about unreleased projects, and even discussions about AI usage, which partly initiated the Screen Actors Guild and the Writers Guild of America strikes.
At GitGuardian, we launched a study to assess the magnitude of the problem.
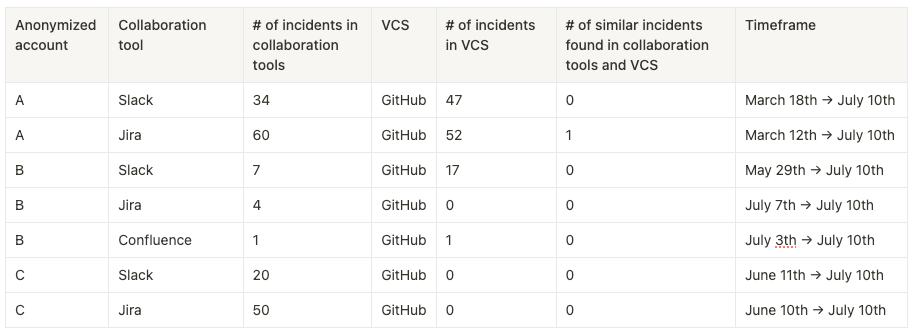
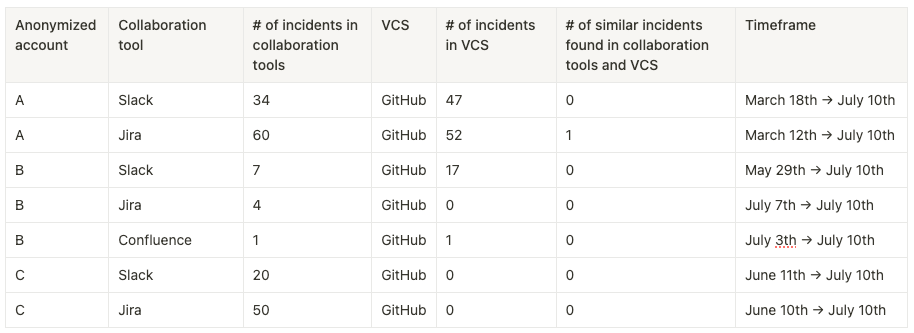
We were surprised to find out that some users leak more secrets within their collaboration tools than into their source code.
So, what does mitigation look like here? While many users use ggshield to shift-left and drastically cut off the number of new hardcoded secrets within their VCS, preventing leaks in collaboration tools is more complex or even impossible. Eventually, they could become the locations where most secrets are found.
Our study did not only focus on the quantity of exposed secrets. We also assessed their severity to see how this would compare with secrets exposed in the VCS.
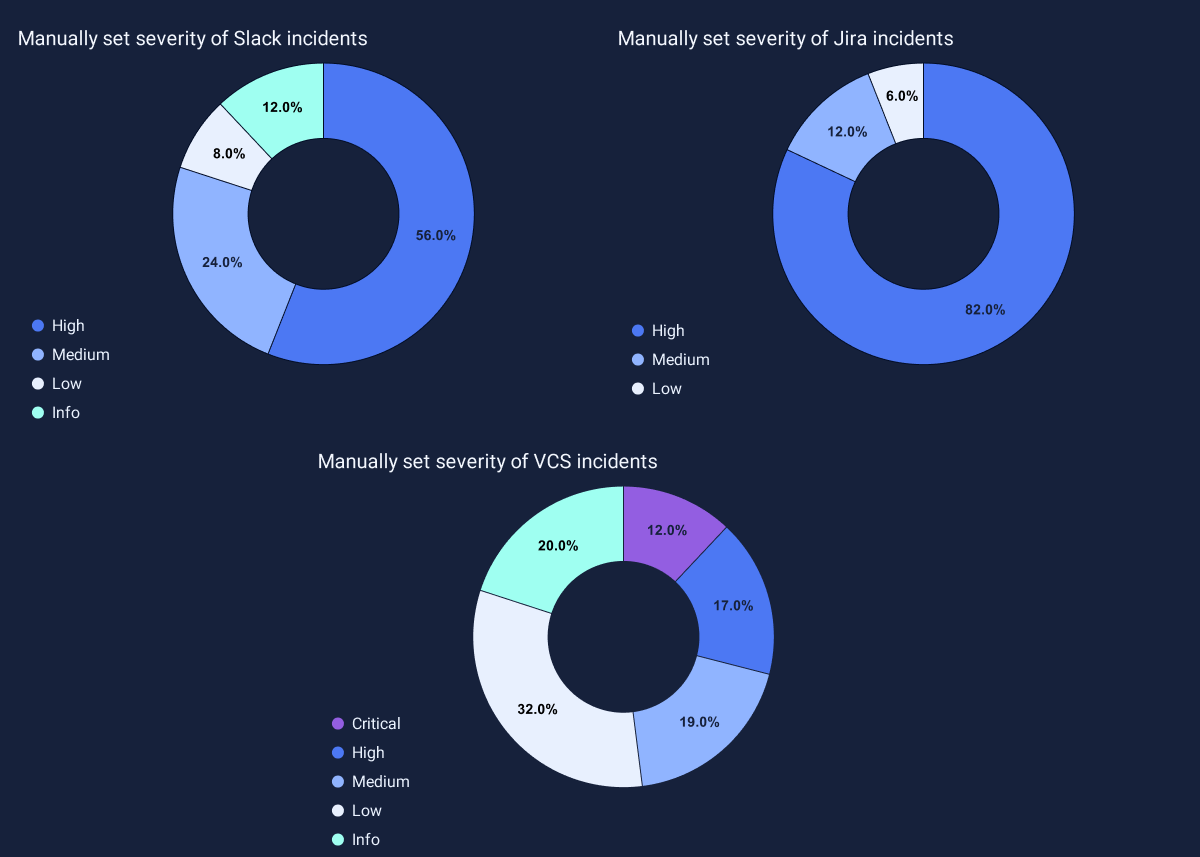
We only considered the severity levels set manually by users. No incidents with critical severity were exposed on our users' Slack workspaces or Jira sites, but the average severity is much higher than in their VCS. More than half of the exposed secrets have a high severity, indicating that teams are less cautious when using collaboration tools than when using VCS for secrets of important services with potentially broad impacts in case of attacks.
With more than 65,000 companies relying on Jira Software to manage their projects, Jira and other collaboration tools have become liabilities in organizations' attack surfaces.
This was confirmed by cybernews researchers, who discovered that hundreds of thousands of vulnerable Atlassian Confluence instances are at risk of being remotely accessed and manipulated by attackers.
You know where this is going: you will need to extend your monitored perimeter to collaborative tools used by your developers. However, to be effective, the key is to be reactive. Secrets detection must be implemented in real-time to ensure timely remediation in case of a leak.
Yet scanning high-frequency assets such as chat messages or project management tickets can seem daunting, especially when monitoring thousands of channels or instances.
Fortunately, GitGuardian integrates with Slack workspaces, Microsoft Teams tenants, Jira or Confluence sites. This means you can almost instantaneously expand your protected perimeter with all the benefits of the GitGuardian platform.
You can include as many workplaces or sites as you would like to monitor. Once set up, detected vulnerabilities will naturally fit within your dashboard. GitGuardian will notify you if the secret still exists in the source and is still valid.
GitGuardian consolidates multiple occurrences of the same secret across source code and productivity tools into a single incident to reduce alert fatigue.
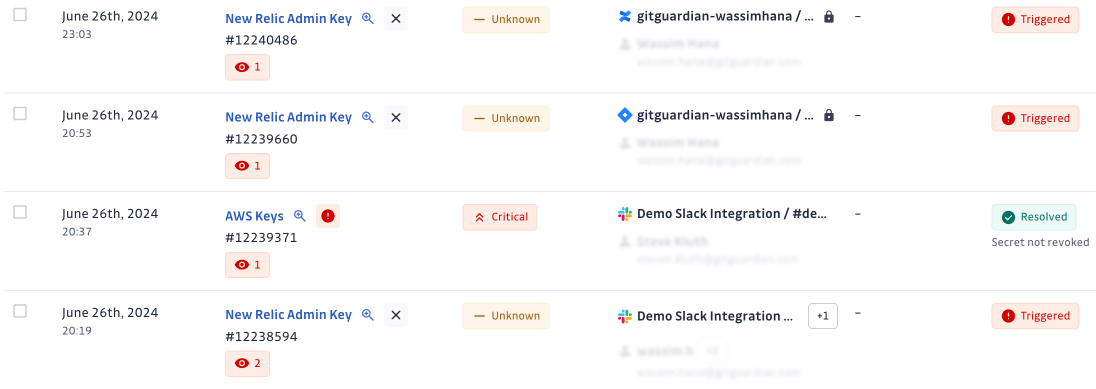
As always, you can never be too fast to be completely safe from all attackers, but taking quick action to address the issue will reduce your exposure to attacks.
Quick focus on secrets detection for Microsoft Teams

In an effort to continue minimizing the attack surface, we just released Microsoft Teams integration, which allows users to monitor their Microsoft Teams channels. These are often used by development and infrastructure teams to:
- Collaborate with each other through channels or direct messages.
- Run ChatOps workflows to receive alerts, for instance, in case a server goes down or to obtain a summary after running a job in a CI pipeline.
In both cases, secrets can be accidentally revealed.GitGuardian will automatically monitor all channels, including standard, private, or shared, to ensure no blind spots are left uncovered.
Read more about integrating Microsoft Teams in our documentation.
Reducing your attack surface
GitGuardian coverage has never been so extensive, yet our teams are continuously working on finding solutions that can detect secrets in the broader range of tools used within organizations and reduce their attack surface.
We always discuss with our users to prioritize our efforts where they would be the most useful to them. Your voice matters! If there are any tools that your teams use for collaboration that could potentially lead to secret leaks, please let us know.
And remember, the best way to prevent the exposure of secrets is always to adopt best practices!
*** This is a Security Bloggers Network syndicated blog from GitGuardian Blog - Code Security for the DevOps generation authored by Ferdinand Boas. Read the original post at: https://blog.gitguardian.com/secrets-detection-collaboration-tools/
如有侵权请联系:admin#unsafe.sh